APIs Power Applications—and Pose Security Challenges
Application programming interfaces (APIs) form the chassis for modern applications. They are interfaces to software components that developers use to integrate valuable information into their applications (like Google Maps in a rideshare app or YouTube videos into a webpage) and they are everywhere—even in security products. APIs are key components at every stage in the journey of an application.
Like all things that are created with good intentions, the prominent use of APIs has motivated bad actors with the worst of intentions to exploit them. Gartner has predicted that by 2022, API abuses will be the most frequent attack vector against enterprise web applications, resulting in data breaches.1
Learning via Gamification
F5 Labs is introducing a gamified version of a system that lets you hunt for API vulnerabilities on your own to learn how they work. The system simulates some of the errors that are left intentionally or unintentionally in the system and similar issues that have been exploited and resulted in breaches.
- Hard-Coded Secrets: Many applications exchange user credentials for a hard-coded token or key. This key allows anyone that knows it to gain access to the application. However, many times these keys have no expiry, allowing a user to completely circumvent the authentication process.
- Broken Authorization: Providing blanket access to the API keys has proven detrimental to multiple mobile and web applications. Malicious users have used such blanket access to get ahold of confidential data belonging to others.
- Data Access Control on User Interface (UI): Time and again we have seen implementations where APIs pull more data from a server than an app is authorized to share, so even if the app’s UI filters this information from the user, attackers can access and exploit this data.
- Security Check for User Interface (UI): Over the last few decades, we have learned that no entry made from the client should be blindly trusted. In some instances, checks are built into the UI, but they can be circumvented with man-in-the-middle tools or API tools such as the Google Chrome app, Postman.
- Weak Tokens: JSON Web Token (JWT) has soared in popularity for use within APIs for its ability to provide integrity. However, an implementation of JWT without a proper cryptographic signing mechanism can lead to privilege escalation.
- Credential Stuffing: Bots have automated the process of testing stolen website login credentials; testing credentials against APIs is no different. Bots can be used to scrape APIs for data or used to validate stolen credentials, eventually leading to account takeover (ATO) attacks.
- Version Troubles: APIs are often changed to add functionality or remove unused features. These changes can cause the clients that use them to break, so it is common practice that organizations maintain multiple versions of APIs to ensure compatibility. But sometimes out-of-sight and out-of-mind treatment for older version of APIs has caused breaches, and security controls are not kept up to date for the older versions.
Setting up the Practice Range
Users can set up a practice environment on a personal machine with Docker Runtime Environment or any cloud environment, or they can attend a live event conducted by F5 Labs. We've already run a few successful events, times and locations for additional events and other CTFs will be announced as they are scheduled.
The practice environment consists of two Docker images:
- sbacker/ctfapi: The quiz website describing the scenario that needs to be pwned
- sbacker/witcherportal: The vulnerable portal for challenged
Commands to run the images locally are:
Capture the Flag (CTF) API Portal
- docker pull sbacker/ctfapi
- docker run --name ctfapi1 -p 8000:8000 -it -d sbacker/ctfapi
Witcher Portal
- docker pull sbacker/witcherportal
- docker run -it -d --name witcher10 -p8080:8080 -e PYTHONUNBUFFERED=1 sbacker/witcherportal
The portal will be accessible locally at port 8000 and 8080:
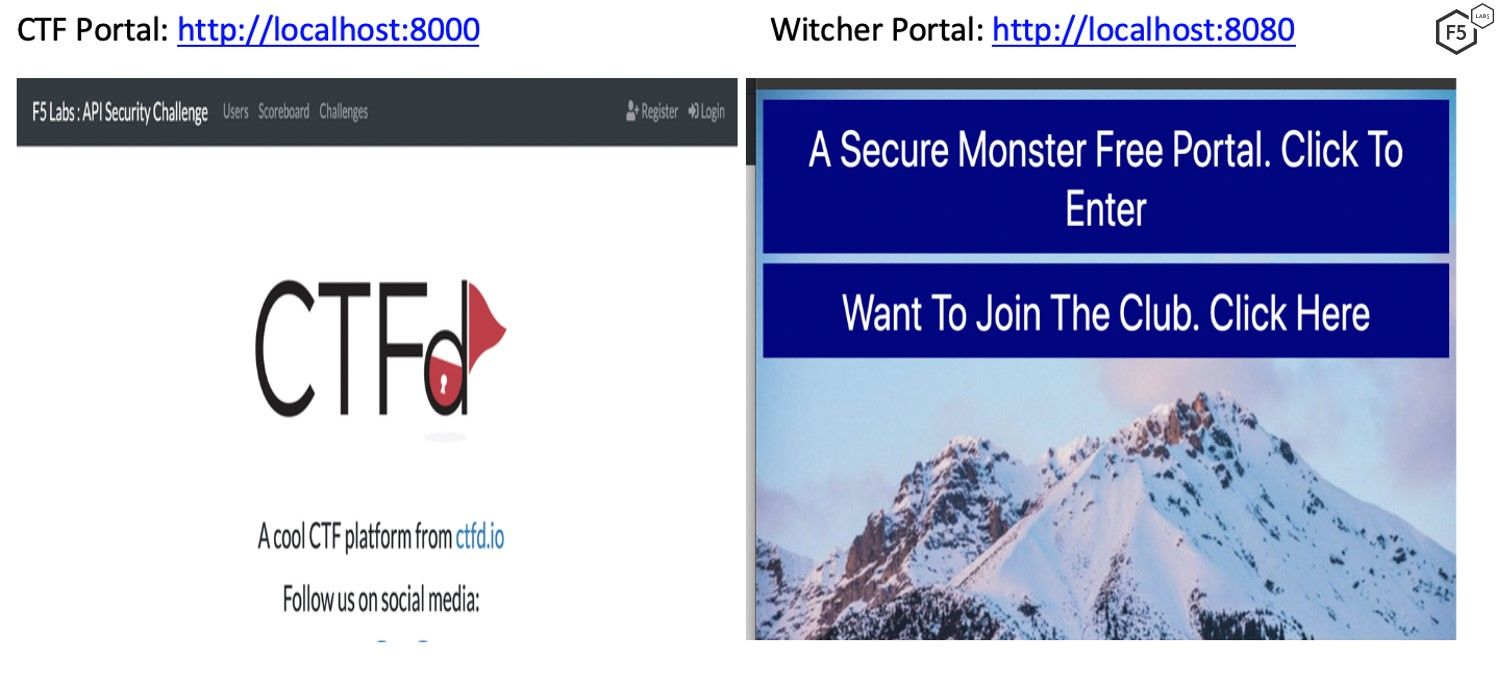
Figure 1. Portals for the API capture-the-flag game
Conclusion
Understanding the tools, tactics, and procedures used by malicious actors help us strengthen our application security stance. The API juggernaut needs the security ecosystem to evolve as our current defenses fall short. Sun Tzu in The Art of War sums it all up with the statement, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.”
Acknowledgments
The CTF portion of the website is built on the popular CTF portal by ctfd.io.


