Attackers are always on the lookout to compromise digital identities (/content/f5-labs-v2/en/archive-pages/education/digital-identity-is-an-increasingly-popular-attack-vector-for-cybercriminals.html). A successful account takeover allows a cybercriminal to impersonate a genuine user for monetization purposes. Enterprises large and small have utilized various means to secure someone’s digital identity, and credentials are the starting point. F5 Labs 2021 Credential Stuffing Report indicates that 1.8 billion credential sets were spilled in 2020 alone. Such a huge stash of credentials is a massive threat to digital identities. An effective mitigation strategy to this threat that various regulatory bodies and security practitioners recommend is to enforce multifactor authentication (MFA).
MFA, which restricts attackers from capitalizing on the use of compromised credentials, has been on the rise. It requires the user to provide two or more different types of factors. Typically, it’s something the user knows (such as a password) and something the user has. The second factor is usually a code sent via text message, a hardware token, or a dedicated multifactor authentication app. After entering a username and password, the user must enter the code to complete the login. However, it is worth noting that not all authentication systems are created equal, and unsuspecting users can be tricked into providing the second factor. Social engineering is a prevalent way of getting a user the divulge the second factor, but fraudsters have also employed technologically sophisticated ways to bypass MFA. This article evaluates two tricks attackers use to game authentication systems.
Trick 1: Capitalizing on Trusted Sessions
No doubt, the user experience suffers because of MFA. To make this less inconvenient for customers, many websites employ techniques to identify a user device and register the information after the user provides a second authentication factor and consent to trust their device. Once registered, transactions from those devices are deemed safe. For example, an e-commerce website establishes trust with a user device by enforcing MFA on the first logon. It then subsequently allows transactions from this trusted user device, which may include credit card details stored in a user’s profile. This improves the experience for the user, who is not forced to provide a second factor for every transaction. However, any deviation from the user’s stored risk profile, such as a known user logging in from a new device, initiates a multifactor verification.
Typically, once a device is identified, the information is stored in the form of a cookie on the client side, which will be used to identify the device on the server side. A known device is supposedly less risky and does not trigger additional authentication. Fraudsters understand this process, and we have seen a thriving marketplace named Genesis Store that helps enable these bad actors. For example, a fraudster can obtain device fingerprints and associated cookies and credentials with ease, as shown in Figure 1.
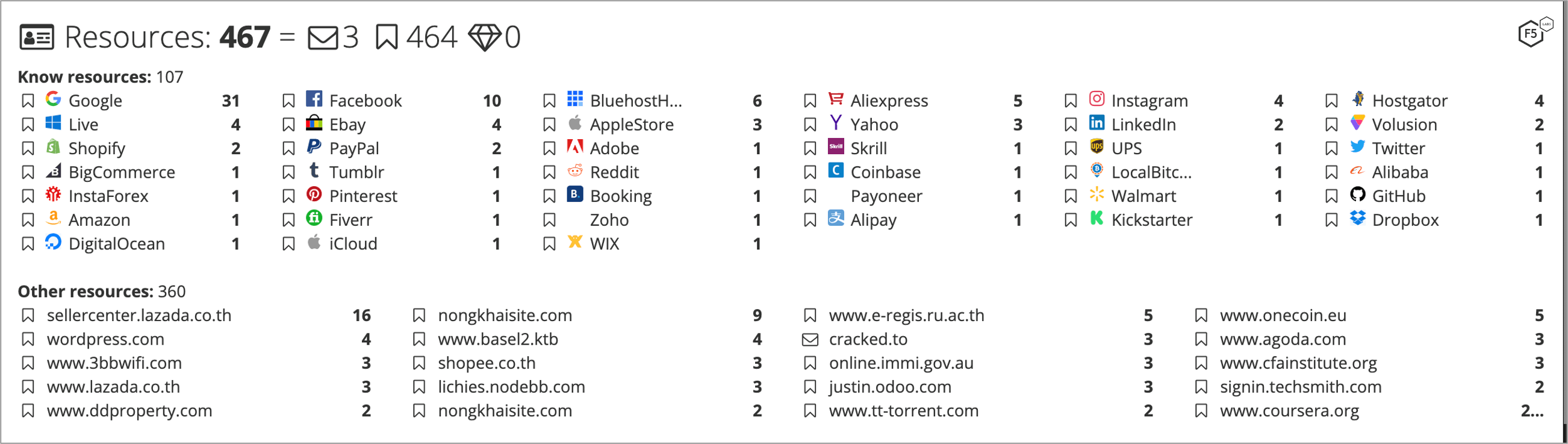
Figure 1. Genesis bot for sale with access to 467 digital resources.
An analysis of data collected from January through May 2021 from a leading financial institution showed fraudsters making targeted attacks using Genesis. About 1,500 requests were aimed at either logons or change password requests using a Genesis plugin that spoofed the attacker’s device as the customer’s device. These requests, which produced around 900 unique browser fingerprints, were crafted to trick the financial institution’s antifraud solution and to potentially prevent triggering multifactor authentication that the attacker might not have access to.
Trick 2: Using Real-Time Phishing Proxies
In the 2020 Phishing and Fraud Report, F5 Labs researchers noted a rise in the use of real-time phishing proxies (RTPP). Simply put, RTPP is a different take on phishing. Instead of setting up fake websites, fraudsters use a person-in-the-middle technique that intercepts users’ transactions on the genuine website. Traditional phishing attacks are asynchronous in nature, as the fraudster’s objective is to collect credentials and utilize them at a different time. MFA-enabled accounts are a dampener to these phishing attempts, as they usually rely on time-sensitive tokens that cannot be reused. RTPPs transform phishing from asynchronous to real-time, enabling attackers to capture of MFA codes or the authenticated session cookies. Armed with these, fraudsters can impersonate a genuine user and complete transactions.
F5 Labs, along with Shape Security researchers, analyzed one such campaign targeting a financial institution. In this attack campaign, cybercriminals set up a spoofed domain and lured customers to access it using various phishing techniques. During the four-week period in which F5 studied the active attack campaign, researchers spotted an interesting anomaly about the devices. This threat actor group was limited to real devices and more than 55,000 attempts were made for 4,127 accounts from a single device. The attackers used a few other devices, but the account-to-device ratio was disproportionate. Table 1 shows the account-related details of five unique devices used in this campaign.
| Device | Unique IDs | Number of Login Attempts |
| 1 | 4,127 | 55,312 |
| 2 | 307 | 1,409 |
| 3 | 225 | 875 |
| 4 | 233 | 399 |
| 5 | 217 | 811 |
Table 1. Analysis of an RTPP attack campaign on a financial institution.
Conclusion
Multifactor authenticationenhances security for online accounts and makes it more difficult to compromise an account. But it diminishes the user experience, and businesses often design easier paths based on risk assessment. Fraudsters and attackers are on the lookout for these easy paths and employ a range of techniques to bypass MFA controls. This makes it essential to understand the threat landscape and implement MFA accordingly.
Recommendations
- Tie MFA to specific transactions and adopt a risk-based approach
- Analyze affinity of account-to-device and device-to-account to spot anomalies
- Deploy controls to check if an endpoint is trying to spoof its fingerprint.
- Detect automated transactions.
- Train users to treat credentials and MFA codes as confidential.


