Banking has undergone some huge transformations over the last decade as it becomes more embedded in consumers’ everyday lives. In the last year alone, technology adoption in banking has accelerated at an unprecedented rate due to the COVID-19 pandemic. A testament to this India, where digital payments over the unified payment interface (UPI) increased from 8 trillion Indian rupees (INR) in 2019 to more than INR 21 trillion in 2020.1 Consumers are delighted about making financial decisions without having to visit a bank branch or use a banking application. Buy now, pay later (BNPL) represents a transformation in the payments industry and is experiencing rapid adoption. BNPL empowers consumers by providing a line of credit at the point of sale.
BNPL eases the pressure on consumers by allowing them to pay over a period of time instead of paying the whole amount up front. The fact that most BNPL service providers do not charge interest if payments are made on time, and that BNPL options are available in both e-commerce and traditional retail scenarios, makes this financial instrument more attractive than other products, such as credit cards, payday loans, or financing schemes marred with poor consumer experience.
BNPL service adoption has been steadily growing, benefiting both businesses and consumers. A 2019 case study noted a 33 percent increase in shopping cart size when BNPL options were provided.2 The ability to buy now and pay later helps consumers stretch their dollar during trying financial times, as shown by the 200 percent growth in BNPL adoption in 2020.3 The success of BNPL, a blend of technology and business acumen to address a market segment, depends on keeping the user experience smooth with:
- A simple checkout experience requiring few clicks.
- A consistent user experience across websites.
- No processing fees.
- Instant credit, without a lengthy approval process.
However, the practices that keep the user experience simple and engaging are often the same ones attackers use to commit fraud and make money. Fraudsters take advantage of existing and modified techniques to try to game the BNPL systems and services. In this article, we investigate some of those methods.
How BNPL Systems Work
BNPL services are provided by financial technology (fintech) companies or banks. Retailers subscribe to these services, providing their consumers an alternate mechanism to pay. The payment method is usually triggered at the point of sale both in the digital and physical world. On an e-commerce platform, the consumer is offered BNPL as a payment option after adding items to a shopping cart and checking out. If the shopper selects BNPL, they are directed to a BNPL service provider. After verifying the user, the service provider extends an interest-free line of credit to the consumer. The payment process involves scanning a QR code, using the phone to confirm the transaction, or entering a one-time password sent to the phone. Figure 1 illustrates the flow of control.
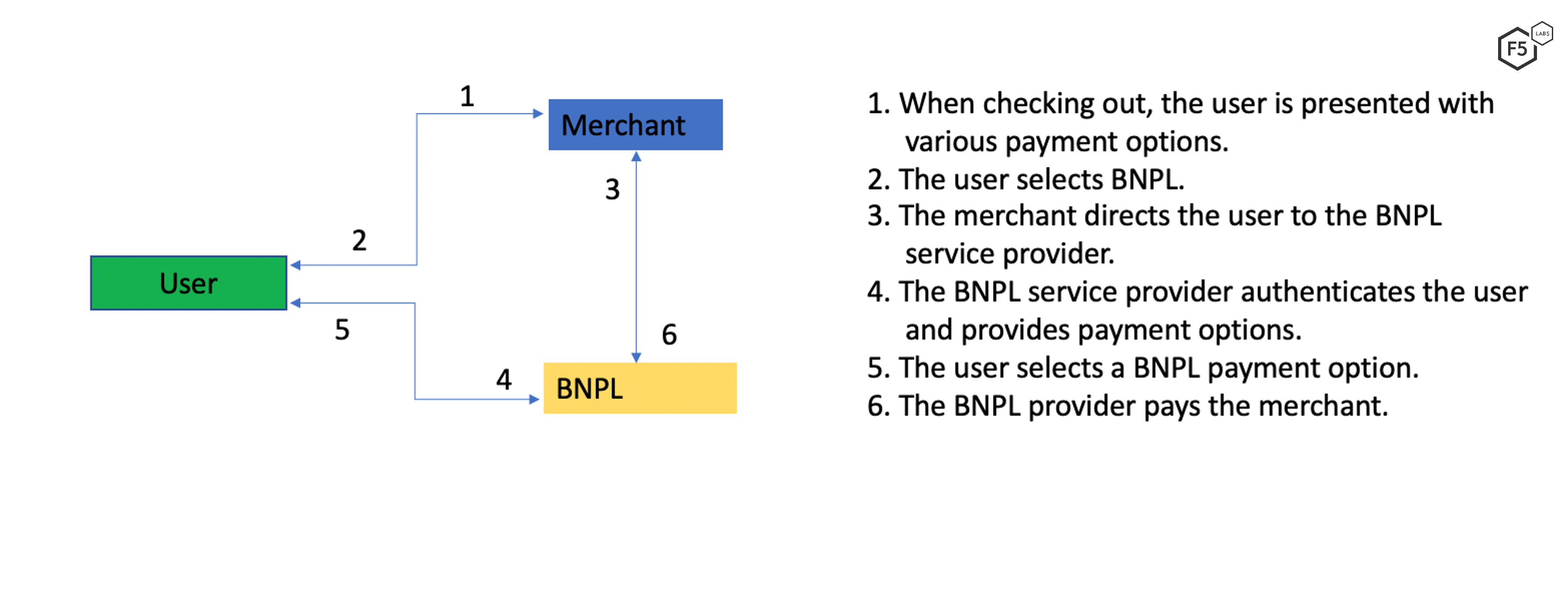
Figure 1. Payment flow using a buy now, pay later system.
Fraud Techniques in Operation
BNPL services are like other digital applications, and attackers utilize various techniques to cheat this system. Coincidently, the banking and financial industry is already familiar with some of the tricks attackers use. Three common techniques fraudsters use include:
- Account takeover: BNPL services usually provide a default line of credit to a new account, and the lending limits usually increase with account age, transactions, and payment history. Fraudsters create fake accounts to capitalize on default credit, but to increase their gain they also target existing accounts. Attackers use a combination of techniques, including phishing, credential stuffing, and SIM card cloning, to make money at someone else’s expense.
- Abusing the default line of credit for new accounts: Most BNPL systems enable consumers to sign up simply by providing copies of documents for proof of identity (such as a driver’s license) and/or a current address (such as utility bills). Using similar documents obtained from stolen mails or data breaches, fraudsters create fake accounts and then use the same simple sign-up requirements and introductory line of credit offered to legitimate consumers. In some cases, fraudsters collude with merchants to convert the default line of credit to cash.
- Repayments with a stolen credit card: Most BNPL services allow consumers to settle loans using credit cards. Fraudsters take advantage of this feature and pay their debts using stolen credit card information. For the merchant, such transactions lead to chargebacks and other expenses toward settlement of the fraud.
Planning a Robust Defense
To meet the onslaught of the various attack mechanisms fraudsters use, BNPL service providers need to include several preventive and detective security controls. These should include mechanisms to identify the user and their intent. Some of the checks necessary for BNPL systems include:
- Validating the user during the sign-up process: Most BNPL systems make the sign-up process effortless, with the user uploading documents to prove their identity. This process needs to be infallible, without adding complexity. BNPL systems should include biometric authentication, liveness checks, and fake-document checks (such as holograms or font mismatch) as part of the sign-up process to counter fake identity creation.
- Detecting and preventing account takeovers: BNPL services need to protect takeovers of valid user accounts. This requires a series of checks that include:
- Detecting automated and manual efforts of credential stuffing and implementing countermeasures, such as rate limits and time-based account freezes.
- Collecting and analyzing additional contextual information, such as user device, location, and time of day, and using that in conjunction with other authentication factors.
- Implementing a robust, risk-based multifactor authentication system.
- Protecting against the use of stolen credit cards: Implement and enforce the 3D Secure protocol for credit cards to improve credit card fraud prevention.
- Detecting anomalies: Collect the necessary telemetry on user transaction data including endpoint information and utilize machine learning algorithms to spot transactional anomalies like buyer-seller collusion.
Conclusion
BNPL systems extend the buying power of consumers with their broad audience appeal and interest-free loans, providing an edge over other lending instruments the financial sector uses. This payment mechanism is novel and suits the current market dynamics, however, fraudsters do not need to pivot much from their existing tricks to gain from the system. Tricks such as account takeover and new account fraud have spoiled user credit ratings with other financial instruments and pose a similar threat to BNPL systems. Regulations for fintech companies differ across regions, but companies need to deploy security controls to protect against system abuse.
Security Controls
To mitigate the challenges discussed in the article we recommend the following security controls to protect BNPL systems:
Recommendations
- Detect and block malicious intent from humans and bots.
- Implement risk-based authentication and authorization systems.
- Develop intelligent user onboarding processes that incorporate artificial intelligence to weed out the use of stolen information, like matching a user selfie with proof of identity.
- Monitor account lifecycles and transactions for anomalous activities.


