Introduction
In part one of this two-part series, we define digital identity and explore the attack vectors cybercriminals use at each stage in the identity lifecycle.
Everything that we do as individuals has found its way into the digital world. From communicating with friends to purchasing good or services—even getting an education and managing investments can all be done online today. Consumers wholeheartedly embrace this “digital channel” for the broad reach and convenience it offers.
To provide the right services and maintain appropriate privacy, companies doing business online maintain data about every user in the form of an account. To grant users access to their accounts, proper user identification is a must. However, when you combine the great trail of personal information people voluntarily provide about themselves online with the vast amount of identity data that has been compromised in data breaches, it’s becoming a lot more difficult to identify legitimate users online. Because identities can so easily be stolen and faked, user accounts are put in jeopardy. Even as organizations amplify their defenses, cybercriminals find digital identity and identity fraud too lucrative an attack vector to ignore.
In this article, we look at the different techniques cybercriminals use to commit fraud at different stages in the “identity lifecycle.” But first, we must understand what digital identity is.
What Is Digital Identity?
In the physical world, everyone needs to assert their identity, and trust is established based on something the person is (their physical presence and appearance) combined with something the person has (an identity card, which often includes a photo to validate their identity). Identity in the digital world has some commonalities with the physical world, but user attributes, such as date of birth, age, gender, location, and government-issued identity numbers that are stored in a digital format, also become part of a person’s digital identity. Over time, the activities users perform and the devices they use also contribute to their digital identity. But without a physical document or physical presence to validate identity, the digital world must rely on authentication to validate an identity assertion. This is typically done using a combination of the following factors:
- something the user knows (such as a password, passphrase, or PIN)
- something the user has (such as a token generator)
- something the user is (a biometric factor, such as a fingerprint, voiceprint, or iris scan)
Depending on the confidentiality of data and user tolerance for the inconvenience of the validation process, organizations combine one or more of these factors to enforce identity assertion/authentication. Some factors can be easily faked, so it’s becoming more common to augment these three factors with a contextual factor such as location, time of day, or the device used for a particular transaction. Together, these factors can help detect anomalies and improve the identification process. The sum of these factors that enable organizations to uniquely identify a user constitute digital identity. Usually this association between an account and the required authentication factors is made during the sign-up process for an online service.
How Cybercriminals Weaponize Digital Identity for Fraud Schemes
In the rapidly expanding digital universe, identity is a frequent attack focus for abuse. Fraudsters have figured out ways to carry out different malicious schemes at each stage of the identity life cycle (see Figure 1). In most cases, the end goal is to steal data or procure services intended only for the authorized user. Digital identity has a lifecycle that includes three stages: creation, operation, and dormancy. Let’s look more closely at each stage and some specific identity fraud vectors within each.
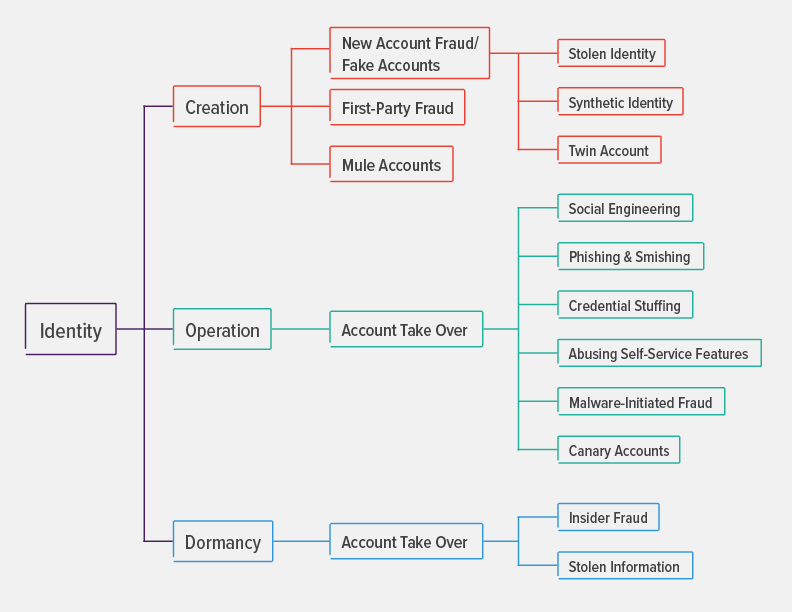
Figure 1. Different types of identity fraud can occur at each stage of the identity lifecycle.
Identity Creation
In this phase, a user identity is created on an online service in the form of an account. This helps the provider to have a record of users and customize the experience to the user’s liking, location, and needs. Data required for the account is typically collected using a web form or it’s pulled from other established services after obtaining the user’s consent.
In this stage, having access to a wealth of data (from previous breaches and other avenues), criminals can scam users, organizations, or both in the following ways:
- New account fraud: The deliberate use of stolen information to impersonate a valid user, typically with the aim of financial gain, such as obtaining credit in their name or gaining other advantages (such as limited free services) at the legitimate user’s or organization’s cost. New account fraud can take the following forms:
- Stolen identity: A cybercriminal uses stolen details (such as a government-issued identification number, photo, date of birth, location, etc.) that can identify a genuine user to create a new account and defraud an online service.
- Synthetic identity: A cybercriminal amalgamates the stolen user details with fake information to create a seemingly genuine identity. The objective is to defraud the system and disappear before anyone spots the anomalies.
- Twin account fraud: A fraudster tries to create an account similar to a genuine, existing online account and defraud the system by providing detailed information and making it seem like both accounts belong to the same user.
- First-party fraud. In this method, a user or group misrepresents their identity data or provides false information to gain an advantage or derive some services for which they are not otherwise eligible.
- Mule accounts: In this method, a user creates an account and passes the information to cybercriminals in exchange for some minor financial payment. This method resembles the steps involved in money laundering.
Identity in Operation
In the operation stage, a user’s digital identity has already been created with an online service and is actively being used to identify the user and provide access to services. At this stage, fraudsters aim to get into the active account to obtain the service for themselves or, in the case of a financial account, make use of the user’s credit or steal funds. This process is known as account takeover (ATO), and fraudsters can trick users and steal their account access in multiple ways, including:
- Social engineering: Fraudsters use a variety of tactics to create an environment of urgency (pretending to need help or making a limited time offer) to deceive users into divulging their personal information, including credentials, one-time passwords, credit card number, and so on.
- Phishing and smishing: Fraudsters use email or mobile channels (text messages) to pose as a genuine entity or website and lure victims into voluntarily providing personal or confidential information so they can then impersonate that user.
- Credential Stuffing: It is a common practice for users to reuse passwords across multiple online accounts, making stolen credentials very valuable. Fraudsters can easily procure huge quantities of credentials from compromised sites or the dark web. Then, using a systematic process, such as bots or manual labor farms, they can validate credentials across multiple websites until they can gain access and take over an account.
- Abuse of self-service features like forgotten password. Most applications provide self-service access for users to get into their accounts in case they forget their current credentials. Typically, the “forgot password” functionality either asks the user to provide answers to security questions (which can easily be guessed) or sends a reset link to a preregistered email address. Fraudsters make use of data acquired either via a data breach or using online sources to gain access to the account.
- Malware-initiated fraud. Fraudsters make use of malware to gain an intermediary position between two communicating parties so they can intercept communications and alter user transactions. With techniques like man-in-the-browser, they can successfully deceive users because they can modify both user input as well as the response from the server without the user realizing what is happening.
- Canary accounts. Fraudsters create genuine accounts on the system to study how the system works. This technique is not used to commit direct crime but rather to understand and assist in creating actual attacks.
Dormant Identity
It is not uncommon for users to lose interest in or completely forget about online accounts they previously created and no longer use. Over time, these accounts become dormant. Cybercriminals can take over these forgotten accounts by reactivating them using the following:
- Stolen information: Fraudsters use stolen credentials to reactivate accounts by calling user helplines or using self-service reactivation mechanisms.
- Insider help: Time and again, criminals have colluded with insiders to circumvent tools and procedures put in place to detect fraud. Malicious insiders can activate dormant accounts for criminals to commit fraud. This mechanism is highly effective because when the fraud is uncovered, law enforcement will focus on tracking down the original account owners, while the fraudsters have already monetized their fraud and moved on.
Conclusion
Digital identity is an important and complex security construct that enables individuals to reap the benefits of the connected world. But fraudsters find it an equally lucrative attack vector and have found countless ways to exploit it. In this article, we reviewed some of the common techniques fraudsters use. Part two will take a deeper dive into individual fraud attack vectors, the tactics and technologies criminals use to conduct fraud at scale, and mitigation techniques.


