Report
DDoS
2024 DDoS Attack Trends
Unveiling the rise of Hacktivism in a tense global climate.
Latest Research
Sensor Intel Series
GeoServer Targeting on the Rise
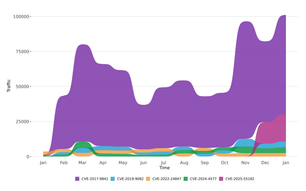
Sensor Intel Series: January 2026 CVE Trends
What is Application Protection?
Application Protection is the range of security options that defenders use to protect apps and their related data from a range of threats. This includes process-based practices such as securing applications during development (DevSecOps), access controls, code obfuscation, and patch management. It also includes active protection in the form of encryption, anomaly detection, and firewalls. The goal is to prevent unauthorized access, data breaches, tampering, or exploitation of vulnerabilities that could compromise the integrity and functionality of the applications.
This stems from a recognition that apps are increasingly the target of choice for malicious actors, for much the same reason that criminals rob banks: that's "where the money is". Given that, it increasingly makes sense for defenders to be app-centric in their protection models and mitigation strategies. Providing robust application security ensures the safety of sensitive information, builds customer trust, ensures regulatory compliance, and minimizes financial and reputational damages.
2019 APR
Top Risks
Application Protection Report 2019, Intro Episode: Why Application Security?
Find out why we care so much about application security, how applications have grown into the weird beasts that they are today, and how our work fits into the bigger picture of securing and running an application.
Sensor Intel Series
Sensor Intel Series
F5 Labs Top CWEs & OWASP Top Ten Analysis
We expand our view to include CWE and OWASP, and we also examine the latest overall trends for June 2025.
Top Risks
The State of the State of Application Exploits in Security Incidents
The title of this report is not a typo. “The State of the State of Application Exploits in Security Incidents” is a meta-analysis of several prominent industry reports, each of which covers the state of application security.
How Do Threat Actors Target Applications?
Threat actors target applications by exploiting vulnerabilities and misconfigurations. Common attack methods include injecting malicious code through techniques like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), as well as abusing APIs to access sensitive data. They also exploit insecure authentication by using stolen credentials (via credential stuffing) or brute force attacks, and conduct malware injections, supply chain attacks, and reverse engineering to compromise the application or its users. Threat actors may also take advantage of misconfigured environments, such as exposed admin dashboards, unencrypted data, or default credentials. Denial-of-service (DoS) attacks can overwhelm applications and degrade their availability, while zero-day exploits leverage undiscovered vulnerabilities before they are patched.
In addition to technical attacks, threat actors use social engineering tactics, such as phishing, to manipulate users into revealing credentials or performing unauthorized actions. They may also target client-side vulnerabilities, such as intercepting unencrypted traffic or injecting malicious scripts into websites via formjacking. These attacks are often automated using tools to scan for application weaknesses or abuse APIs, but can also involve highly targeted, manual exploitation.
How Can You Protect Your Apps?
Because there are so many ways attackers target applications, defenders need to use a variety of approaches to protect those applications. Begin by prioritizing security: implement secure development practices and use robust security tools. Secure coding is essential to minimize vulnerabilities like SQL injection, cross-site scripting (XSS), and other common threats. Use strong authentication and authorization solutions, and rely on the principles of least privilege and zero trust to reinforce those access controls. Keeping software, frameworks, libraries, and APIs up to date with the latest patches is also critical to prevent exploitation of known vulnerabilities. CVSS scores can be helpful in prioritizing your patches, but you should pair this with maintaining a robust inventory of what you're defending, and adding in threat intelligence to stay informed about what attackers are actively exploiting.
Apache Parquet
Canary Exploit Tool for CVE-2025-30065 Apache Parquet Avro Vulnerability
Investigating a schema parsing concern in the parquet-avro module of Apache Parquet Java.
Ready to Learn More?
Application Protection is a particular area of focus for us, and we're always looking to stay on top of the latest attacker trends to better understand where defenders should take action next. Sometimes that means we're conducting broad analyses across billions of data points, sometimes it means we're taking apart a newly discovered malware and building an open-source tool to counter it, and sometimes it means we're explaining different control strategies that you can apply to protect yourself today. Asking questions of the data leads to insights and, inevitably, more questions, so there's always more research to do. Below, you can find a collection of all our research into application protection.