Introduction
In part one of this two-part series, we define digital identity and explore the attack vectors cybercriminals use at each stage in the identity lifecycle.
Everything that we do as individuals has found its way into the digital world. From communicating with friends to purchasing good or services—even getting an education and managing investments can all be done online today. Consumers wholeheartedly embrace this “digital channel” for the broad reach and convenience it offers.
To provide the right services and maintain appropriate privacy, companies doing business online maintain data about every user in the form of an account. To grant users access to their accounts, proper user identification is a must. However, when you combine the great trail of personal information people voluntarily provide about themselves online with the vast amount of identity data that has been compromised in data breaches, it’s becoming a lot more difficult to identify legitimate users online. Because identities can so easily be stolen and faked, user accounts are put in jeopardy. Even as organizations amplify their defenses, cybercriminals find digital identity and identity fraud too lucrative an attack vector to ignore.
In this article, we look at the different techniques cybercriminals use to commit fraud at different stages in the “identity lifecycle.” But first, we must understand what digital identity is.
What Is Digital Identity?
In the physical world, everyone needs to assert their identity, and trust is established based on something the person is (their physical presence and appearance) combined with something the person has (an identity card, which often includes a photo to validate their identity). Identity in the digital world has some commonalities with the physical world, but user attributes, such as date of birth, age, gender, location, and government-issued identity numbers that are stored in a digital format, also become part of a person’s digital identity. Over time, the activities users perform and the devices they use also contribute to their digital identity. But without a physical document or physical presence to validate identity, the digital world must rely on authentication to validate an identity assertion. This is typically done using a combination of the following factors:
- something the user knows (such as a password, passphrase, or PIN)
- something the user has (such as a token generator)
- something the user is (a biometric factor, such as a fingerprint, voiceprint, or iris scan)
Depending on the confidentiality of data and user tolerance for the inconvenience of the validation process, organizations combine one or more of these factors to enforce identity assertion/authentication. Some factors can be easily faked, so it’s becoming more common to augment these three factors with a contextual factor such as location, time of day, or the device used for a particular transaction. Together, these factors can help detect anomalies and improve the identification process. The sum of these factors that enable organizations to uniquely identify a user constitute digital identity. Usually this association between an account and the required authentication factors is made during the sign-up process for an online service.
How Cybercriminals Weaponize Digital Identity for Fraud Schemes
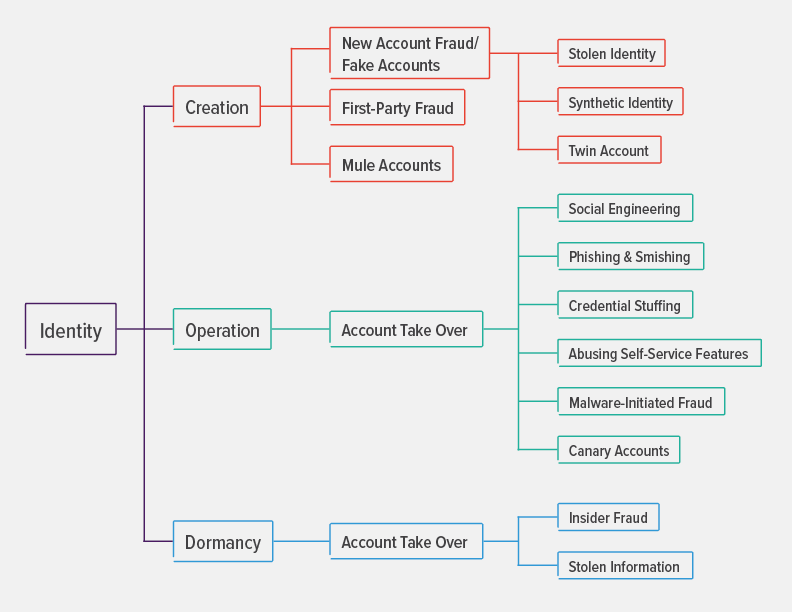
In the rapidly expanding digital universe, identity is a frequent attack focus for abuse. Fraudsters have figured out ways to carry out different malicious schemes at each stage of the identity life cycle (see Figure 1). In most cases, the end goal is to steal data or procure services intended only for the authorized user. Digital identity has a lifecycle that includes three stages: creation, operation, and dormancy. Let’s look more closely at each stage and some specific identity fraud vectors within each.