Introduction
Over the past few months, F5 Labs has presented a series of articles on fake account creation. We’ve covered why fraudsters create fake accounts and how automation is used to create fake accounts at scale. These articles have described how these fake accounts can negatively impact businesses, but also how security professionals identify fake accounts and leverage security controls to stop bots running fake accounts.
In this deep dive we worked with engineers from F5’s Bot Defense© service to examine how fraudsters attempted to leverage fake accounts and automation during a promotional contest created by a major restaurant chain.
Promotion Overview
A popular quick-serve restaurant chain offered a promotional contest in which loyalty rewards members could win prizes that included free food and drink items, restaurant gift cards and higher value grand prizes.
The contest was announced via press release on the day the promotion started. To participate, customers needed to be enrolled in the brand’s loyalty rewards program, and they needed to log into their loyalty rewards account to access their daily and weekly contest entries. Within minutes of the official announcement, traffic spiked on the company’s website, but not everyone flocking to the site had the intention to play by the rules. Specifically, some bad actors were hoping to maximize their chances of winning by creating multiple fake accounts. While others were interested in cracking the card numbers for the flood of gift cards that were being won daily by contest participants, this case study focuses on fake account creation associated with this event.
Requirements: One Valid(ish) Email
Each loyalty rewards account required a unique email address. However, like many retail websites, this restaurant did not require that a user validate their email address. This means that almost any combination of characters formatted as a valid email could be used to register an account.
Allowing users to register accounts using any email address without verifying its existence reduces friction in the ordering process, but without an email verification step, fraudsters creating accounts on these systems aren’t limited to email addresses they can readily access, which is a net benefit to fraudsters: it reduces friction within any fraud scheme that requires creating multiple system accounts.
On this retailer’s system, if an account was successfully created, users were immediately logged into their account and could begin accessing menu options such as entering the contest, placing food orders, or updating their account details and payment methods. Once logged in, the user remained logged in until they logged out, cleared their browser data, or reached a maximum session time limit (typically several weeks long).
Logins and Account Creation Spike
The contest began with a surprise press release and ad campaign that announced its start. There were no announcements about the promotion in the days leading up to the event kick-off. From a case study perspective, this was a lucky choice because we can see the immediate impacts of the contest announcement on website login traffic (see Figure 1) and can assume that any account creation activity that occurred in the days prior to the contest’s start were unrelated to the promotion. For this case study, the 14 days leading up to the announcement provided baseline traffic for this restaurant. The promotion provided new chances to win each week, which correlated to higher daily login peaks as those new opportunities rolled out to users.
F5 protected key endpoints for this customer, but not every URL. F5 did not have any visibility into the promotional contest’s web endpoints but did have visibility into account creation and login transactions. The average daily volume of login transactions in the 2 weeks leading up to the promotion was 149,000, and that surged more than 5x to 851,000 during the contest period. At the conclusion of the contest, daily logins returned to baseline levels.
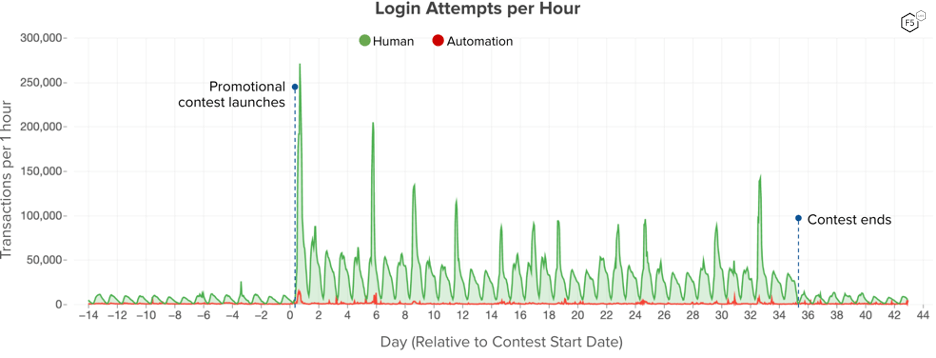
Figure 1: Web login traffic across a period that includes the promotional contest as well as two weeks prior and one week after the contest’s end. The largest login spike corresponds to the press release announcing the event on its first day.
Figure 2 below shows an overview of new account creation traffic. On the first day of the promotion, more customers began to create loyalty rewards accounts so that they could participate, and the fraudsters also wanted to benefit from the promotion and started creating fake accounts. Within hours, a fake account creation attack launched. This attack was highly sophisticated, and the threat actors behind it were able to scale their attack that same day. The speed with which the attack began underscores how sophisticated attackers are both opportunistic and organized. They have a range of tools at their disposal to deploy when an opportunity arises, and they easily pivot to focus on that opportunity.

Figure 2: Web traffic attempting account creation transactions across a period that includes the promotional contest. While a small spike of customers created accounts immediately after the contest was announced, it took a few hours for fake account creation bots to follow suit.
While most of the automation occurred during the contest, careful inspection of Figure 2 reveals very small automation spikes occurring on days on either side of the contest. Those low volumes are typical of the automated traffic blocked from creating fake accounts on this website outside of the contest period. Typical daily account creation automation leading up to the contest was around 700 automated transactions per day. Automated activity averaged 59,000 transactions per day across the contest period, 78x higher than usual. This underscores that interest in creating fraudulent accounts climbs when there’s an incentive, but almost every day someone tries to apply automation towards creating fake loyalty rewards accounts on this site.
The fake account creation seen on a typical day by this retailer happens for various reasons, many of which were described in the first article in the fake account creation series. An additional reason that daily fake account creation may be seen on this site is that the account creation endpoint reveals whether an account already exists for any entered email address. A fraudster can use this feedback to create more focused lists of accounts they can apply to their primary goals, which might include trying to steal account data or stored gift cards from existing users.
Features of Fake Accounts
The contest attracted new users, and while many were legitimate customers excited for a chance to win their favorite menu items as well as the more valuable prizes, we found manual and automated attempts at fake account creation. We saw evidence of individuals trying to max out their potential rewards by creating fake accounts and we saw bots attempting large fake account creation efforts using fake emails or email aliases at scale. In part 3 of the Fake Account Creation Bots series, Tafara described common features that one can use to identify fake accounts, and several of those features were identified within these account creation attempts.
Disposable Emails
A disposable or temporary email refers to an email address that is unique but is typically only used for a limited number of transactions and may be used only to forward incoming messages to a more permanent email address. Some disposable email services allow each inbox to be accessed by all users of the service, with no expectation of privacy, which helps the actual recipient further hide their connection to the activity. These services can be used by fraudsters and other criminals, but they are also sometimes used by individuals who are trying to prevent reduce exposure of their primary email address.
While any free email can be used as a disposable email at the individual-user level, there are thousands of domains owned by services that support disposable email at scale, allowing bots to create limitless fake accounts that cannot be traced back to one person. In this case study, domains used by these services are used to identify disposable emails. Denylisting known disposable email domains is one tool for reducing the creation of accounts that use these domains, but the approach amounts to a game of a whack-a-mole, in which new fake email domains pop up as others disappear.
There wasn’t a significant change in the portion of new accounts being created using disposable domains during the contest. Across the analysis period, both within and outside of the contest period, approximately 0.1% of account creation attempts on any day were made using email domains found in a publicly available list of more than 3000 disposable domains. The vast majority were unsuccessful at registering accounts, likely due to domain controls maintained by the customer’s website. There are two factors that contribute to the very low portion of these domains being used. The first is that there are very few fraud use cases that would require tying an account to a valid email inbox in this web app, and the second reason is that if controls, such as a regularly updated domain denylist, are in place, then fraudsters will use a newer (unlisted) disposable domain or come up with other strategies.
Overall, these disposable domains appeared more often in manual account creation attempts than they did in automation, underscoring their use by lower-tech fraudsters. However, there were several days during the contest where a large share of the daily account creation attempts that used disposable emails were made by bots (See Figure 3). This might mean that the operators of some of the bots that showed up for the contest had not previously tested account creation on this site and had not yet learned they should avoid using well known disposable domains.
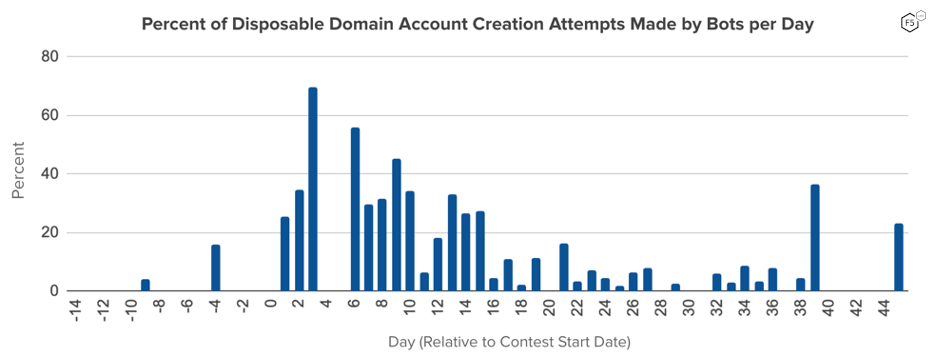
Figure 3: The daily proportion of automated (as opposed to manual) account creation attempts using disposable domain email addresses. While the percent of total new accounts attempted using disposable domain email addresses didn’t change across the contest period, the share of that activity performed by bots increased during the contest and continued for several days after the contest’s end.
Email Fuzzing
One of the features of fake account creation attempts during this promotion was the obvious use of username fuzzing. As previously described in the fake account creation series, this technique abuses certain email platforms’ use of special characters such as “.” or “+”. The technique is also sometimes called “sub-addressing”.
Some email services ignore “.” in any email address, such that “johndoesoap@gmail.com” or “john.doe.soap@gmail.com” will land in the same inbox.
Another fuzzing technique is the use of the “+” character. Gmail ignores anything from “+” forward. This is very useful for power users who want to set up filters based on variations of their username, such as “johndoesoap+school@gmail.com” versus “johndoesoap+sports@gmail.com”. However, this can be leveraged by bad actors to generate unlimited unique usernames tied to a single email inbox.
Not all email providers use these characters the same way. For many providers, they would be treated as any other character, so we should expect that some small portion of legitimate users will have a “.” or “+” in their email address.
The percentage of email addresses containing either of these two special characters that were entered into this site’s account creation form skyrocketed shortly after the contest began, jumping from a daily average of 15.8% of account creation attempts in the two weeks leading up to the contest to a daily high of 93% of attempts on the second day of the promotion.
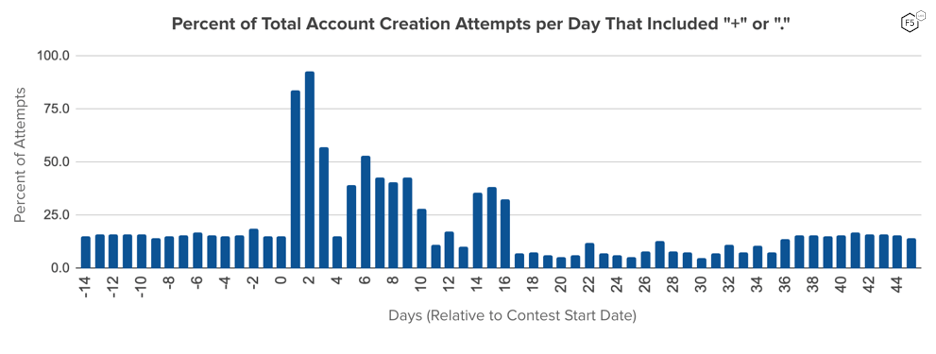
Figure 4: Certain characters ( “+” and “.”) can be used on some popular email domains to create email aliases, but work as standard characters with no special functions on other email domains. The portion of email addresses containing these characters in the username portion spiked in the first days of the promotional contest. We assume this is due to increased use of these aliased accounts for fraudulent account creation purposes by both individuals (manual) and bots (automation).
Fabricated Email Accounts
There were multiple examples of email addresses that were likely to be fabricated, including randomly generated nonsense strings, as described in a previous article. However, there was a novel pattern in the usernames that was also heavily associated with domains that allow their email users to create and delete custom email aliases on demand as an online privacy and spam prevention tool. The pattern was unusual for an email address, but not overly suspicious when seen in isolation. It began with one or two digits and included two randomly generated non-name dictionary words. An example of that patterns is: “06adapt.muddles@example.com”. While digits commonly appear in alphanumeric email usernames, they rarely appear as the starting characters. Emails commonly feature dictionary words but are more likely to be a represent an obviously meaningful phrase. The likelihood of any of these generated usernames being existing email addresses on a domain that allows custom aliasing would be low.
There are two potential benefits for using this specific pattern in conjunction with one of the higher reputation email domains that support custom aliases. First, the accounts are not likely to exist at all, meaning that they won’t conflict with an existing user on the targeted system. Second, the accounts can be made to exist in the future, if ever needed. This might be useful for the fraudster interested in making bulk contest entries. In the case of winning one of the more valuable prizes they would need to be able to access the email associated with the account to coordinate prize delivery. Because of the unusual pattern, they would most likely be able to create the email alias, attached to a legitimate account on that higher-reputation domain to claim a prize. Because the pattern isn’t obviously a fake, they may avoid suspicion of fraud.
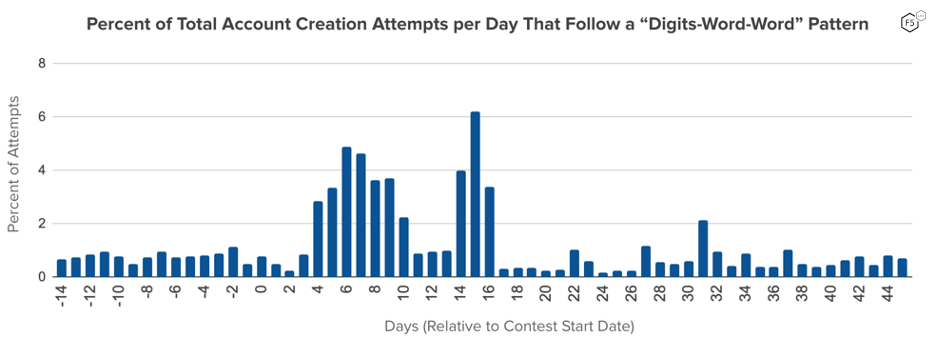
Figure 5: a pattern based on “digits-word-word” was relatively uncommon in account creation outside of the contest period, with fewer than 1% of new account registration attempts per day matching that character pattern. During the contest period the rate of this pattern surged above 4% across multiple days.
Unusual Creation Times
We established that daily account creation volumes increased during the contest and a significant portion of that was due to bots. However, it wasn’t just the daily volume pattern that changed, but there were notable shifts in the time of day that accounts were typically created as well.
Internet use generally follows daily patterns that approximate the schedules of people: lower overnight and higher during the day. In the two weeks prior to the beginning of the contest, account creation was lowest during the early morning hours (midnight to 6 AM) and the average daily share of total account creation attempts for that time of day was lower than 5%. However, during the contest, the proportion of accounts created in the early morning hours increased to approximately 20% of accounts. Evenings (6 PM – 12 AM) saw a modest jump during the contest, from an average daily share of 19% in the baseline period to 24% during the contest. After the contest ends, time of day activity returned to baseline.
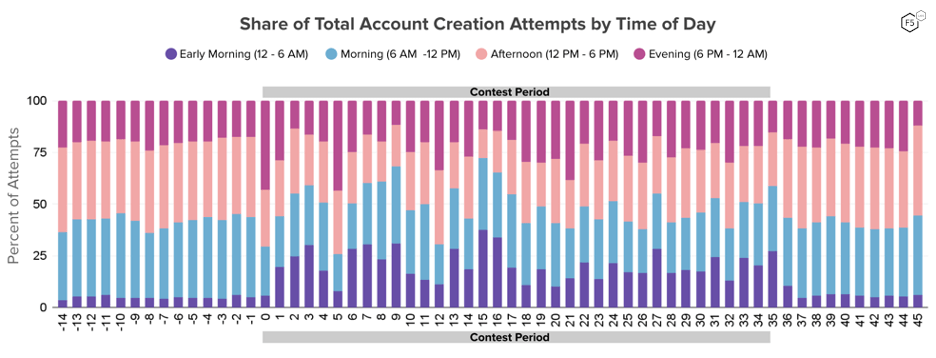
Figure 6: Chart shows the share of account creation attempts made during each time of day. All day/times are adjusted to the user’s location. A large jump in accounts created in the early morning and smaller increase in the evening hours reduced the relative share for morning and afternoon account creation attempts.
Thousands of Suspicious Accounts
The focus of F5 Bot Defense© is to stop unwanted automation, but the signals collected can be used in retrospective analysis to identify suspected manual fraud. We were able to identify several suspicious clusters of manual transactions that had a high likelihood of being related to fraudulent activities. Prior to the contest start, the daily rates of highly suspicious manual account creations were quite low. In the two weeks before the contest began, the median number of suspicious account creation attempts was 11.5 per day and the maximum seen was 41. During the contest, both the median and max increased to almost 3x baseline (median: 32.5 per day, maximum: 119 per day). There was also a particularly noticeable rise in suspicious account creations across the second week of the promotion. One potential explanation for that delay might be that some of the threat actors behind the failed account creation bots during the first days of the contest may have decided to shift to a manual approach.
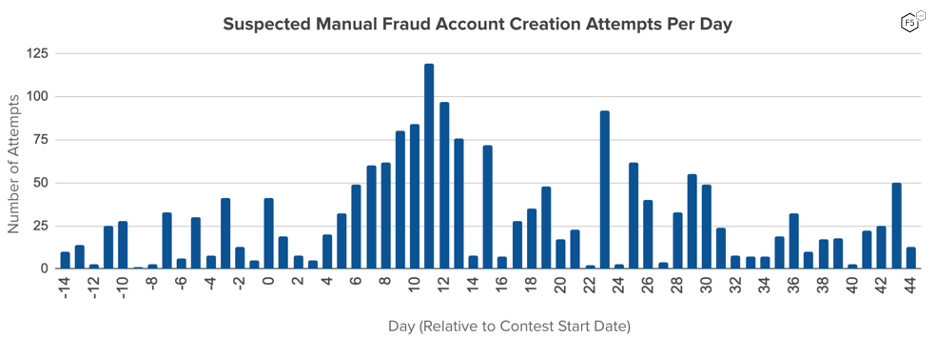
Figure 7: Chart shows the number of suspicious accounts created per day. Accounts are labeled as suspicious due to anomalous behaviors in non-automated transactions.
Some suspicious accounts created manually were later seen engaging in automated activity on the website during the contest. Approximately 84% of transactions by these suspicious accounts occurred on gift card balance endpoints where the user could enter a gift card number into a form, and if the card was valid, they’d see the existing balance. Approximately 93% of attempts from these suspicious accounts were blocked for using automation. This suggests that fake accounts were created manually, but then primarily used in conjunction with automated gift card cracking efforts. Only about 1% of total transactions by these accounts were related to placing orders. The big draw to create these accounts was obviously the gift card endpoints, which makes sense because those fraudsters focus on retailers that they perceive to have a high number of active cards in circulation. Throughout the contest, gift cards were included in the contest prizes. The increased number of active gift cards proved to be an incentive for fraudsters to increase card cracking activity.
Millions of Automated Account Creation Requests
Across the promotion, bots filled and submitted 2.1 million account creation requests. 98% of automated fake account creation attempts during the contest can be described as highly sophisticated. Due to attackers’ investment of time, resources and skill, the behaviors of these bots at a per-transaction scale look very similar to legitimate human transactions, making these bots particularly challenging to identify and mitigate. The automated traffic originated from more than 69,000 different IPs which spanned almost 2,000 different autonomous system numbers (ASNs). This traffic used more than 4,600 different user agent headers. The attackers took considerable effort to hide their activities by accessing distributed infrastructure and randomizing HTTP header information to masquerade as legitimate traffic from diverse sources.
While most bot activity was fully blocked during the promotion, approximately 213,000 new fake bot accounts were successfully created. 34,000 of those accounts collectively made 360,000 gift card cracking attempts prior to being blocked. These accounts also attempted about 7,000 orders before they were blocked. These fraudsters may have merely been redeeming fraudulently won food or drink prizes, or they could have been attempting to pay for orders with stolen payment information.
Because the contest endpoints were not under F5 protection, we don’t know how many of the accounts attempted to engage in fraudulent contest participation, nor do we know exactly how many prizes may have been stolen from legitimate customers. Given the scale of the attack, the actions of these accounts represent a small fraction of the potential damage that could have occurred without a highly sophisticated automation defense in place.
Automated Fraudsters Moved Between Web and Mobile
This restaurant chain has a mobile app that supports the process of ordering and paying for orders. Every single fake account successfully created by bots on the website had at least one login attempt in the mobile app. These login attempts typically occurred within a few seconds of the initial account creation on web. Sophisticated attackers will use approaches that cross platforms to avoid detection and maximize profit. This seamless movement across platforms indicate that the people behind the bots have high levels of technological sophistication, resourcefulness, preparation, and creativity. We do not have visibility into what occurred within this Mobile App after the login, so we can assume that mobile logins were first used to verify the successful creation of the accounts and then those accounts could engage in similar behaviors within the app as was seen on web.
Conclusion
When a popular brand used a contest to engage with new and loyal customers, the fraudsters also crawled out of the woodwork to benefit from the promotion. The fraudsters did not play fair and rushed to create large numbers of fake accounts, with some using manual means and others employing bots. While almost 2 million fake account creation attempts were blocked by the F5 Bot Defense service, some fraudsters and sophisticated bots were able to create fake accounts in the earliest hours of the contest. These fake accounts were used to try to crack gift cards and potentially may have stolen prizes intended for brand-fans who were playing by the rules. Fake accounts created via automation on the web were seen using the native mobile app, indicating that attackers were technologically sophisticated and highly prepared to quickly act across multiple platforms to reach their objectives.
Recommendations
Businesses need to identify how prevalent fake accounts and fake account bot activity are on their platforms to understand the existing risks to their business posed by fake accounts. Marketing promotions that can attract new or repeat customers can also attract fraud and abuse. The design of contests and promotions should also include consideration of design choices or additional technological solutions that may help reduce risks associated with fake accounts abusing promotion terms or stealing prizes from the legitimate winners. Companies launching such campaigns should work closely with their security teams and vendors to ensure that appropriate controls are in place ahead of highly visible promotions and similar events. In this instance, closer collaboration would have reduced the number of successful fake accounts created at the beginning of the contest period.


