
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Welcome to the Sensor Intel Series installment for January 2023. The purpose of this recurring monthly brief is to provide security practitioners with vulnerability targeting intelligence so that they can make better-informed decisions about patching and vulnerability remediation. The source of this intelligence is log data from a globally distributed network of passive sensors. While these sensors collect logs on all ports, we primarily focus on HTTP/S traffic on ports 80 and 443. Furthermore, this brief is largely limited to published vulnerabilities with CVE numbers, although there are a handful of non-CVE vulnerabilities that we track as well because they are particularly interesting, easy to spot, or both.
January attack traffic was particularly notable for the continuing growth of interest in CVE-2020-8958. This is an OS command injection vulnerability in several optical routers from Guangzhou VSOL. While attacker interest in this vuln has remained consistently high for most of the past year, the January traffic blew away the previous record (set last month, also by CVE-2020-8958) by nearly 50%. All other vulnerabilities experienced volumes that are more consistent with the baselines we’ve observed in the last year, leaving us to speculate about the reason behind this enormous growth.
January Vulnerabilities by the Numbers
Figure 1 shows the top ten vulnerabilities and their attack traffic in January. This really illustrates the difference between the volume of traffic attempting to exploit CVE-2020-8958 and, well, everything else. However, CVE-2020-8958 shouldn’t obscure the rapid growth of another vulnerability, the CVE-less and roughly-named “2018 JAWS Web Server Vuln.” This is an authentication bypass vulnerability in the JAWS/1.0 web server installed on several digital video recorders (DVRs).1
Table 1 shows traffic volumes for all vulnerabilities that we track. This month we identified seven new vulnerabilities in our logs, bringing the total number of tracked CVEs to 62.
| CVE Number | Count | Change |
| CVE-2020-8958 | 13963 | 4536 |
| 2018 JAWS Web Server Vuln | 3213 | 2283 |
| CVE-2017-9841 | 1948 | -258 |
| CVE-2022-22947 | 1830 | 82 |
| CVE-2022-41040/CVE-2021-34473 | 1700 | 239 |
| CVE-2018-10561 | 869 | 172 |
| CVE-2019-9082 | 545 | 4 |
| CVE-2021-3129 | 517 | 17 |
| CVE-2021-28481 | 466 | -384 |
| CVE-2019-18935 | 448 | 94 |
| CVE-2018-13379 | 422 | -3163 |
| CVE-2017-18368 | 414 | -268 |
| CVE-2021-40539 | 364 | -501 |
| NETGEAR-MOZI | 320 | -57 |
| Citrix XML Buffer Overflow | 310 | 10 |
| CVE-2014-2908 | 304 | -5 |
| CVE-2020-15505 | 233 | 58 |
| CVE-2013-6397 | 219 | -72 |
| CVE-2020-25078 | 200 | 182 |
| CVE-2021-26086 | 185 | -92 |
| CVE-2017-1000226 | 167 | -42 |
| CVE-2021-44228 | 157 | -122 |
| CVE-2022-40684 | 111 | -109 |
| CVE-2019-9670 | 66 | -64 |
| CVE-2021-21985 | 60 | -26 |
| CVE-2021-26855 | 58 | 0 |
| CVE-2021-22986 | 50 | 37 |
| CVE-2021-26084 | 42 | 3 |
| CVE-2020-3452 | 36 | -159 |
| CVE-2022-22965 | 33 | 6 |
| CVE-2019-12725 | 31 | -81 |
| CVE-2020-9757 | 14 | 0 |
| CVE-2020-25506 | 12 | 0 |
| CVE-2021-29203 | 10 | 1 |
| CVE-2021-33564 | 10 | 6 |
| CVE-2022-1388 | 7 | -5 |
| CVE-2007-3010 | 7 | -260 |
| CVE-2018-7600 | 5 | -11 |
| CVE-2015-3897 | 4 | -4 |
| CVE-2018-17246 | 4 | 0 |
| CVE-2020-7796 | 4 | 0 |
| CVE-2021-33357 | 4 | -4 |
| CVE-2022-1040 | 4 | -2 |
| CVE-2019-8982 | 3 | -1 |
| CVE-2021-201667 | 3 | -4 |
| CVE-2021-41277 | 3 | -4 |
| CVE-2022-25369 | 3 | -2 |
| CVE-22020-17506 | 3 | -11 |
| CVE-2008-6668 | 2 | -1 |
| CVE-2017-0929 | 2 | -2 |
| CVE-2018-7700 | 2 | -5 |
| CVE-2020-13167 | 2 | -6 |
| CVE-2020-17505 | 2 | -6 |
| CVE-2018-1000600 | 1 | -4 |
| CVE-2020-28188 | 1 | -7 |
| CVE-2021-21315 | 1 | -8 |
| CVE-2021-32172 | 1 | -2 |
| CVE-2021-3577 | 1 | -6 |
| CVE-2008-2052 | 0 | 0 |
| CVE-2017-9506 | 0 | 0 |
| CVE-2018-18775 | 0 | 0 |
| CVE-2019-2767 | 0 | 0 |
| CVE-2021-31589 | 0 | 0 |
Table 1. CVE targeting volumes for January, along with change from December. This month we added several new vulnerabilities, bringing our total to 62. Note that a handful of vulnerabilities at the bottom experienced no traffic in either month but are still listed here because they’ve seen traffic in the past.
Targeting Trends
To better understand how January contrasts with previous months, Figure 2 shows how the most prominent vulnerabilities have ebbed and flowed in terms of volume over the last year. (To avoid overplotting, Figure 2 shows the top five vulnerabilities per month, grouped and plotted across all months.) The continuing growth of CVE-2020-8958 and the resurgence of the JAWS vulnerability are visible here, as is a precipitous decline in traffic targeting CVE-2018-13379, which dropped 89% from December to January (more on this vulnerability in a moment).
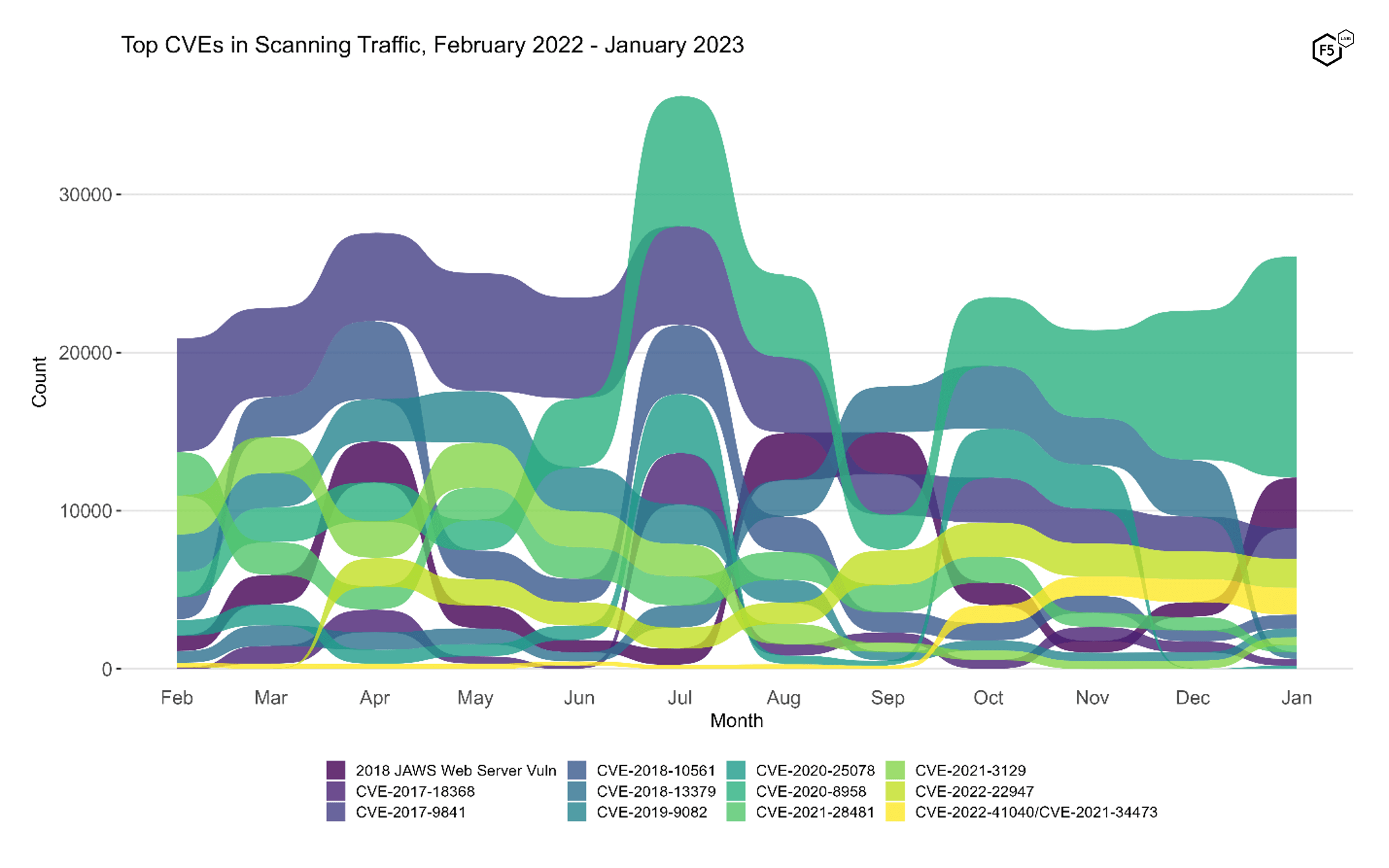
Figure 2. Evolution of vulnerability targeting in the last twelve months. Both the resurgence of the JAWS web server vulnerability and the decline of CVE-2018-13379 are evident here.
Long Term Trends and Sibling Vulnerabilities
Figure 3 shows traffic volume over time for all of the CVEs we track. This provides a little bit more context around the decline in CVE-2018-13379 (fourth column, top row). This is a critical credential disclosure vulnerability in various Fortinet products, and we expected this vulnerability to be superseded by the October 2022 release of CVE-2022-40684, a critical authentication bypass vulnerability affecting the same Fortinet products. However, both CVE-2018-13379 and CVE-2022-40684 (which is plotted in the third column, sixth row of Figure 3) declined in prevalence in January. One potential explanation for this parallel drop is that the release of a new critical vulnerability drove more customers to patch, and so the attack surface for both vulnerabilities declined.
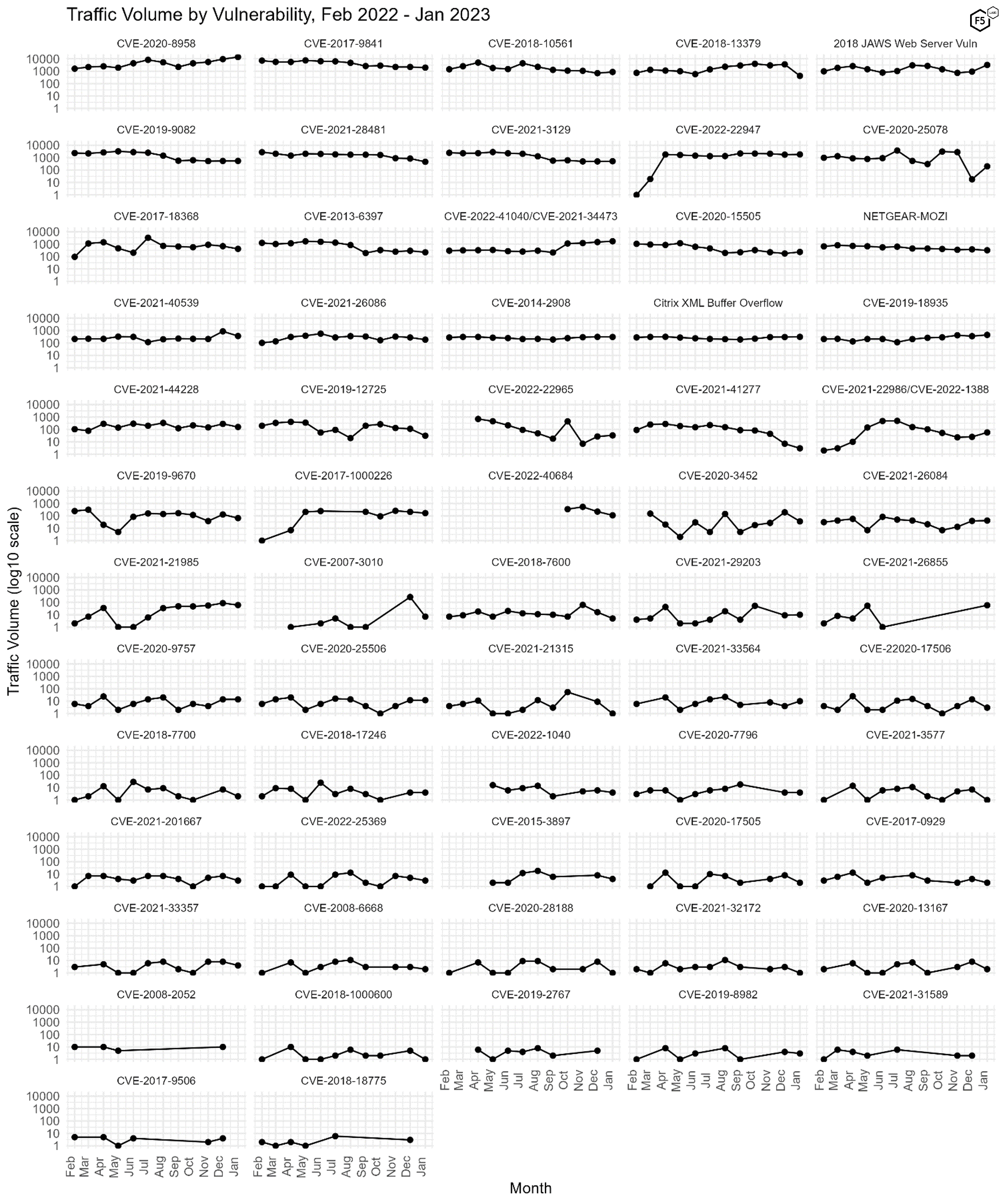
Figure 3. Plot of all 62 tracked CVEs over time. Note the visible decline in CVE-2018-13379, among others. Log10 scale on y axes.
Conclusions
With the same IoT vulnerability that the top of the heap for four months straight (and six of the last seven months), our conclusions are rather predictable: be alert for DDoS attacks, as compromised IoT devices are the modern gold standard for DDoS infrastructure. Furthermore, F5 Labs recently published our 2023 DDoS Attack Trends, which identified a growing trend towards application layer and multi-vector DDoS attacks. Application layer attacks can be significantly more complex to identify and mitigate than simpler volumetric attacks, so paired with these leading indicators about attackers developing attack infrastructure, it appears that both the likelihood and the impact of DDoS are increasing at present. Our recommendation is to prepare ahead of time and be vigilant, particularly with respect to logging and monitoring—the trend toward application DDoS means that the attacks won’t always be as loud and obvious as they used to be.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


