
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
---------------------------------------------------------------------------------------------------------------------------------------------
Welcome to our final Sensor Intel Series installment for 2022. The purpose of this series is to provide vulnerability targeting intelligence to practitioners, based on our analysis of telemetry from a globally distributed network of passive sensors. This series is mostly limited to ports 80 and 443, primarily because it allows us to produce timely and actionable analyses. Obviously these are not the only ports that attackers target, nor are they the only ports that run HTTP/TLS, but since architectural trends and consumption models are increasingly moving towards these ports, this is the analysis most practitioners we speak to want. Note also that we generally restrict this analysis to CVEs and not all vulnerabilities, although we have made a few exceptions for important or interesting vulnerabilities, as you’ll see below.
December 2022 was notable mostly for the activity of a single CVE, and it’s one we’ve seen many times before: CVE-2020-8958, an OS command injection vulnerability in a number of V-SOL (aka Guangzhou) GPON routers. Traffic targeting this vulnerability in December exceeded that of any vulnerability we’ve seen in 2022, with nearly 9500 connections. The next vulnerability, CVE-2018-13379, received just over one third as much traffic in comparison.
December Vulnerabilities By the Numbers
Figure 1 shows attack traffic volumes for December for the top ten vulnerabilities, and illustrates the gap in attention between CVE-2020-8958 and everything else.
Table 1 shows traffic volumes for all tracked vulnerabilities. Several CVEs are brand new to the list this month, and can be spotted in this table when the change and count columns are identical, as in the cases of CVE-2018-17246 and CVE-2015-3897.
| CVE Number | Count | Change |
| CVE-2020-8958 | 9427 | 3881 |
| CVE-2018-13379 | 3585 | 624 |
| CVE-2017-9841 | 2206 | 11 |
| CVE-2022-22947 | 1748 | -333 |
| CVE-2022-41040/CVE-2021-34473 | 1405 | 213 |
| 2018 JAWS Web Server Vuln | 930 | 197 |
| CVE-2021-40539 | 865 | 657 |
| CVE-2021-28481 | 850 | -53 |
| CVE-2018-10561 | 697 | -379 |
| CVE-2017-18368 | 682 | -207 |
| CVE-2019-9082 | 541 | 11 |
| CVE-2021-3129 | 500 | 2 |
| NETGEAR-MOZI | 377 | 29 |
| CVE-2019-18935 | 354 | -64 |
| CVE-2014-2908 | 309 | 18 |
| Citrix XML Buffer Overflow | 300 | 3 |
| CVE-2013-6397 | 291 | 44 |
| CVE-2021-44228 | 279 | 133 |
| CVE-2021-26086 | 277 | -50 |
| CVE-2007-3010 | 267 | 267 |
| CVE-2022-40684 | 220 | -312 |
| CVE-2017-1000226 | 209 | -46 |
| CVE-2020-3452 | 195 | 168 |
| CVE-2020-15505 | 175 | -47 |
| CVE-2019-9670 | 130 | 92 |
| CVE-2019-12725 | 112 | -18 |
| CVE-2021-21985 | 86 | 31 |
| CVE-2020-25078 | 18 | -2769 |
| CVE-2018-7600 | 16 | -46 |
| CVE-2020-9757 | 14 | 10 |
| CVE-2021-22986 | 13 | -6 |
| CVE-2022-1388 | 12 | 8 |
| CVE-2008-2052 | 10 | 10 |
| CVE-2021-21315 | 9 | 9 |
| CVE-2021-29203 | 9 | 9 |
| CVE-2015-3897 | 8 | 8 |
| CVE-2020-13167 | 8 | 5 |
| CVE-2020-28188 | 8 | 6 |
| CVE-2021-33357 | 8 | 0 |
| CVE-2022-22965 | 8 | 8 |
| CVE-2018-7700 | 7 | 7 |
| CVE-2021-3577 | 7 | 2 |
| CVE-2021-41277 | 7 | -37 |
| CVE-2018-1000600 | 5 | 5 |
| CVE-2019-2767 | 5 | 5 |
| CVE-2022-25369 | 5 | -2 |
| CVE-2017-0929 | 4 | 2 |
| CVE-2017-9506 | 4 | 2 |
| CVE-2018-17246 | 4 | 4 |
| CVE-2019-8982 | 4 | 4 |
| CVE-2020-7796 | 4 | 4 |
| CVE-2008-6668 | 3 | 0 |
| CVE-2018-18775 | 3 | 3 |
| CVE-2021-32172 | 3 | 1 |
| CVE-2021-31589 | 2 | 0 |
Table 1. CVE targeting volume for December, along with traffic change from November. Note the addition of several CVEs that are novel to this series.
Targeting Trends
To better understand how December contrasts with previous months, Figure 2 shows the evolution of targeting volume and ranking over the course of 2022. (To avoid overplotting, Figure 2 shows the top five vulnerabilities per month, grouped and plotted across all months.) Ranking of vulnerabilities stayed largely consistent with November, with the exception being CVE-2020-25078, which dropped from roughly 3,000 connections in November to 18 in December.
Figure 2 also reiterates the growth in CVE-2020-8958, which had already increased from October to November. Note that this same vulnerability experienced our previous record for targeting traffic in July, with 8200 connections, only to drop off the map in September. Hindsight has shown that September was the anomaly, as attacker focus on this vulnerability has reached new heights.
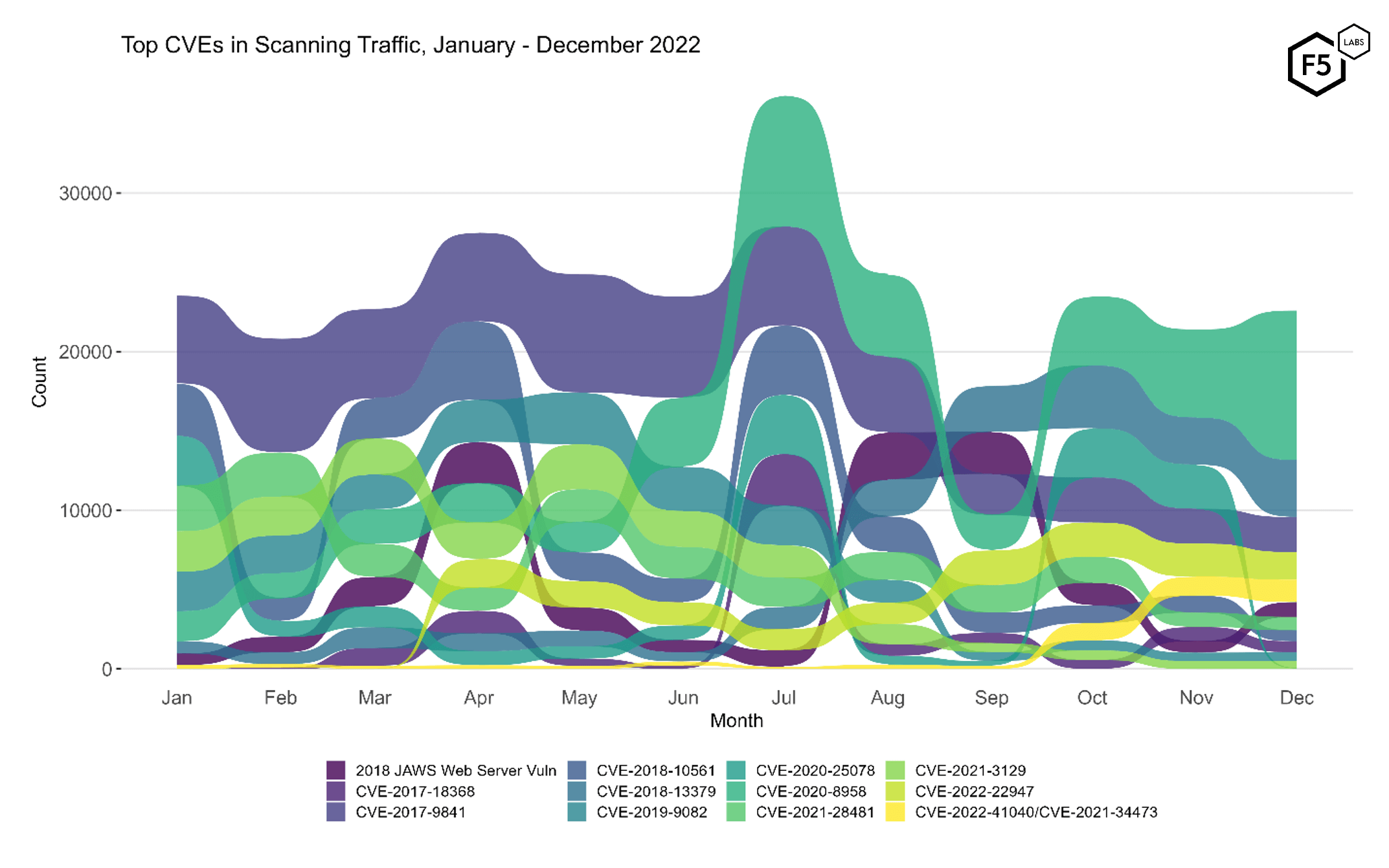
Figure 2. Evolution of vulnerability targeting over the course of 2022. Many of the more prominent vulnerabilities stayed constant in rank and consistent in volume, with the exceptions being the continuing growth of CVE-2020-8958 at the top, and the disappearance of CVE-2020-25078, which dropped 99.4% in volume and fell out of the top ten.
New Signatures and Old Favorites
Figure 3 shows traffic volume over time for all of the CVEs we are currently tracking. This view makes it easy to identify periods of rapid growth, especially since the log10 y-axis means that any vertical change in the plot represents an order of magnitude growth. This provides yet another view into the decline in traffic targeting CVE-2020-25078 (2nd row, 3rd column).
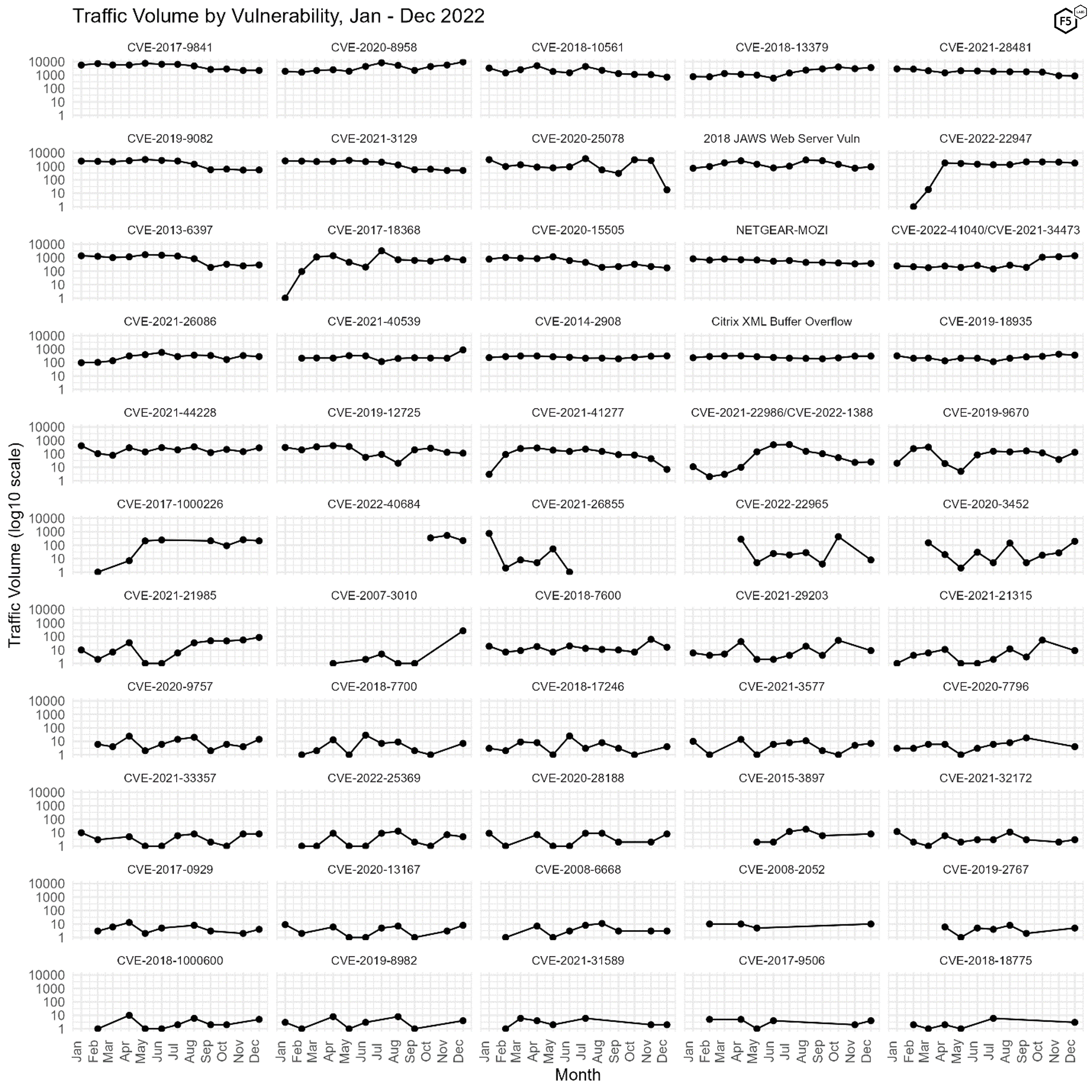
Figure 3. Traffic targeting all 55 tracked CVEs over time. Note log10 scale on y axes, as well as a number of novel additions to our bank of tracked CVEs.
Vulnerabilities New and Old
Particularly avid readers, or perhaps just readers with a magnifying glass, will note that there are six-and-a-half new vulnerabilities in Figure 3 compared with our November SIS. We say a half-new vulnerability because one of the new ones is indistinguishable from an existing signature. While tuning the pattern for CVE-2022-41040, a Microsoft Exchange Server zero-day vulnerability that emerged in late summer 2022, we discovered that our sensors are not able to fully differentiate between CVE-2022-41040 (which is known as ProxyNotShell), and the earlier, similar CVE-2021-34473 (aka ProxyShell). These two vary primarily on whether they require authentication—CVE-2022-41040 requires authentication, while CVE-2021-34473 does not, and our sensors do not offer that level of application simulation. As a result, CVE-2021-34473 has been added to the plot with CVE-2022-41040. (Either way, please patch those Exchange servers.)1
Recently Added CVEs
These are the vulnerabilities that were only recently identified in our logs and added to our signatures.
CVE-2007-3010
A remote command execution vulnerability in the Alcatel-Lucent OmniPCX telephony server versions <=7.1. Attackers can use shell metacharacters in the user parameter to pass commands during a ping action. Our logs showed attackers attempting to download a shell to the /tmp/ folder, escalate privileges and run the shell. NVD
CVE-2017-1000226
A user enumeration vulnerability in a WordPress plugin ironically named Stop User Enumeration versions <= 1.3.9. While the plugin prevents REST API GET requests to endpoints containing ‘/users/’, the API will accept POST requests requesting user enumeration. However, we noted that all of the connections on our sensors were GET requests to an endpoint containing ‘/users/’ and therefore would probably have failed anyway. NVD2
CVE-2021-21985
A critical remote code execution vulnerability in the vSphere Client in VMware vCenter Server versions 6.5, 6.7, and 7.0. NVD
CVE-2018-17246
A critical arbitrary file inclusion vulnerability in Kibana versions < 6.4.3 and 5.6.13. Attackers with access to the Kibana Console API could send a request that would execute arbitrary Javascript. Our logs showed attackers testing a path traversal technique to reach /etc/passwd to confirm local file inclusion. NVD
CVE-2008-2052
An open redirect vulnerability in Bitrix Site Manager 6.5, allowing attackers to redirect users to arbitrary sites and/or conduct phishing attacks. Roughly half of the exploit attempts against this vulnerability were benign testing and therefore probably researchers. The other half attempted to download a web shell. NVD
CVE-2015-3897
A directory traversal vulnerability in Bonita BPM portal versions <6.5.3. This vulnerability allows attackers to read arbitrary files. Some of the logged attack traffic attempted to locate a password file, the other attempted to find Windows system files. NVD
Conclusions
Since the purpose of this series is to document attacker interest in vulnerabilities to help defenders prioritize patching, our primary recommendation is straightforward: if your enterprise application footprint includes any of these vulnerabilities, all of which have demonstrable attacker intent behind them, you should consider patching as soon as possible.
As in the last several months, the ongoing interest in vulnerable IoT systems is probably a harbinger of future DDoS attacks. We recommend reviewing your DDoS playbook and engaging a mitigation service if availability is mission critical.
We also noted scan activity looking for several vulnerabilities or known vulnerable systems that do not have CVE numbers associated with them. These include three exploits against an Oracle FatWire vulnerability which does not appear to be exploitable in the wild, a Docker enumeration tool, Siemens operational technology port scanners, command and control instructions for a variant of the ZeuS banking trojan, and several Google dorks for easily exploitable systems. This also serves as a timely reminder that not all vulnerabilities are CVEs. While nobody likes having to drop everything and patch when a vulnerability is announced, it sure beats trying to mitigate when there is no patch or indicator of compromise information available.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


