
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
-----------------------------------------------------------------------------------
Here we are in April 2023, which gives us another opportunity to see what vulnerabilities attackers were most interested in last month. After receiving a huge amount of attacker attention from November 2022 to February 2023, CVE-2020-8958 has returned to volumes of traffic more consistent with what we’d come to expect over the last year or so. However, it still remained the top targeted CVE in our list, with more than double the number of scan or exploit attempts of the next most frequent vulnerability, CVE-2022-22947. We’ll also explore the dramatic decline in traffic targeting CVE-2020-25078, as well as a preponderance of Microsoft CVEs in the top ten for March. Let’s jump into the data.
March Vulnerabilities by the Numbers
Figure 1 shows the top ten vulnerabilities and their traffic for March. CVE-2020-8958 is still sitting at the top, though at a smaller volume than in some recent months. Below that we see a few old regulars, such as CVE-2017-9841. However, we also note that 3 of the top 10, or really 4 of the top 11, are Microsoft Exchange vulnerabilities: CVE-2020-0688, CVE-2020-28481, CVE-2021-34473, and CVE-2022-41040. Note that CVE-2021-34473 and CVE-2022-41040 are lumped together here because they are difficult to differentiate with data from passive sensors. They target the same request URI, and have similar HTTP parameters, but one requires prior authentication and and one does not.
In any case, even though none of these Exchange CVEs is dominating the landscape on its own, collectively they appear to represent an uptick in focus on Microsoft in general and Exchange remote code execution (RCE) vulns in particular.
Table 1 shows traffic volumes for all vulnerabilities that we’re tracking, along with change from the previous month.
| CVE Number | Count | Change |
| CVE-2020-8958 | 4181 | -3428 |
| CVE-2022-22947 | 1669 | 187 |
| CVE-2017-9841 | 1582 | -401 |
| 2018 JAWS Web Server Vuln | 1165 | -523 |
| CVE-2020-0688 | 1062 | -388 |
| CVE-2021-28481 | 864 | 480 |
| CVE-2018-10561 | 791 | -144 |
| CVE-2022-41040/CVE-2021-34473 | 711 | -562 |
| CVE-2021-3129 | 538 | 51 |
| CVE-2020-25078 | 523 | -3067 |
| CVE-2019-9082 | 513 | 71 |
| CVE-2018-13379 | 370 | -160 |
| NETGEAR-MOZI | 356 | 62 |
| CVE-2021-44228 | 351 | 245 |
| CVE-2013-6397 | 251 | 63 |
| CVE-2021-26086 | 224 | -124 |
| CVE-2020-15505 | 220 | 1 |
| Citrix XML Buffer Overflow | 215 | -65 |
| CVE-2014-2908 | 211 | -79 |
| CVE-2021-40539 | 206 | -114 |
| CVE-2017-1000226 | 159 | -152 |
| CVE-2017-18368 | 139 | -140 |
| CVE-2019-18935 | 114 | -129 |
| CVE-2021-22986 | 41 | -9 |
| CVE-2022-40684 | 65 | -136 |
| CVE-2021-26084 | 57 | -9 |
| CVE-2022-22965 | 39 | 26 |
| CVE-2022-1388 | 27 | 20 |
| CVE-2020-25506 | 20 | 10 |
| CVE-2021-33564 | 18 | 10 |
| CVE-2019-12725 | 17 | -164 |
| CVE-2021-21985 | 16 | -6 |
| CVE-2021-41277 | 14 | -13 |
| CVE-2019-9670 | 13 | -50 |
| CVE-2020-3452 | 13 | 2 |
| CVE-2020-17506 | 11 | 6 |
| CVE-2020-28188 | 10 | 8 |
| CVE-2021-25369 | 10 | 5 |
| CVE-2008-2052 | 8 | 8 |
| CVE-2020-13167 | 8 | 2 |
| CVE-2020-9757 | 8 | -9 |
| CVE-2021-29203 | 8 | 4 |
| CVE-2021-33357 | 7 | 3 |
| CVE-2020-17505 | 6 | 2 |
| CVE-2021-20167 | 6 | 2 |
| CVE-2021-3577 | 6 | 3 |
| CVE-2020-7796 | 4 | 2 |
| CVE-2008-6668 | 3 | 1 |
| CVE-2017-0929 | 3 | 1 |
| CVE-2017-9506 | 3 | 3 |
| CVE-2018-1000600 | 2 | 0 |
| CVE-2018-18775 | 2 | 2 |
| CVE-2021-21315 | 2 | 0 |
| CVE-2018-7600 | 1 | -3 |
| CVE-2007-3010 | 0 | 0 |
| CVE-2014-8379 | 0 | 0 |
| CVE-2015-3897 | 0 | 0 |
| CVE-2018-17246 | 0 | 0 |
| CVE-2018-7700 | 0 | 0 |
| CVE-2019-8982 | 0 | 0 |
| CVE-2021-26855 | 0 | 0 |
| CVE-2022-1040 | 0 | 0 |
Table 1. CVE targeting volumes for March, along with change from February. Note the 85% drop in traffic targeting CVE-2020-25078.
Targeting Trends
To better understand how March contrasts with previous months, Figure 2 shows a bump plot of targeting frequency. To avoid overplotting, this shows thirteen CVEs which together constitute the top five for each of the twelve months. While some other views of the data might be more useful for assessing a single vulnerability, this plot is particularly useful for understanding how dynamic this targeting landscape is, and how much our traffic changes from month to month.
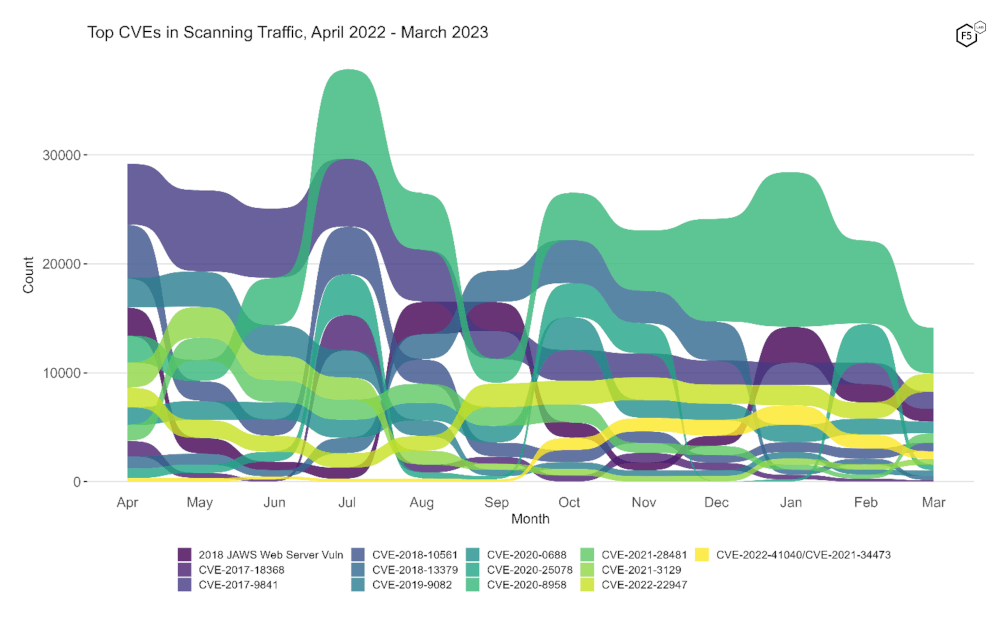
Figure 2. Evolution of vulnerability targeting in the last twelve months. Note the decline in CVE-2020-25078, dropping it from second rank in February to tenth in March.
Long Term Trends
Figure 3 shows traffic volume over the past year for all of the CVEs we track. After we noted the dramatic rise in CVE-2020-25078’s traffic last month, it is interesting to see it decline again precipitously. In this view, the prominent positions of the aforementioned four Microsoft vulnerabilities (CVE-2020-0688, CVE-2021-28481, CVE-2021-34473, and CVE-2022-41040, all in the upper right corner of the plot) look more as though they are due to the decline in other high-frequency vulnerabilities, and less due to their own growth, which has been negative except for CVE-2021-28481.
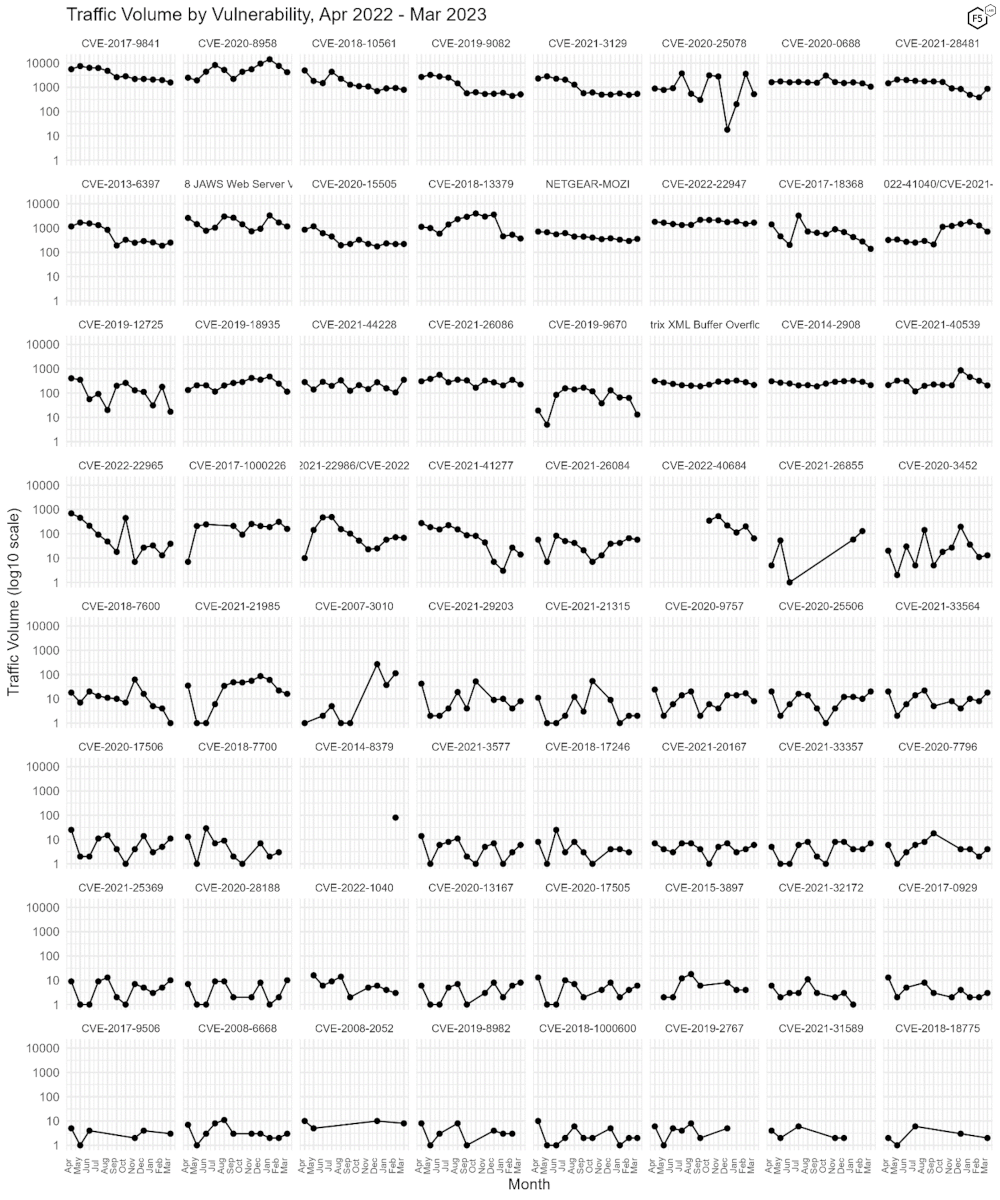
Figure 3. Traffic volume by vulnerability. After growing dramatically between January and February, CVE-2020-25078 declined back to a more baseline amount of traffic.
Conclusions
On the one hand, it is interesting to note the prominence of these Microsoft Exchange RCEs and speculate that perhaps the headline-grabbing CVE-2023-23397, which was published March 14, 2023, drew more attention to other Exchange vulnerabilities that had already been around for some time. However, three of the four mentioned Microsoft vulnerabilities only grew in rank due to the subsidence of other vulnerabilities, and the final Microsoft vulnerability among our signatures was not targeted at all in our data in March. So, as always, we are mostly left to speculate as to which vulnerabilities attackers will focus on in April. Until then.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


