
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
Welcome to the Sensor Intelligence Series for April 2023. Last month was comparatively quiet in terms of attack traffic, like March before it. CVE-2020-8958 (an OS command injection vulnerability in a GPON router) remained the top-targeted vulnerability, as it has for nine of the last ten months. Many of the other top targets, such as CVE-2022-22947 and CVE-2020-0688, are well known to us, and have been in the top ten for months.
However, attacks looking for CVE-2022-24847 caught our attention during our routine check for attacks we hadn’t identified yet, and we added a new signature for it. Whereas most of the vulnerabilities we’ve discussed in the last six months have either been either Microsoft Exchange RCEs or IoT devices, CVE-2022-24847 is an Improper Input Validation vulnerability in an open source server named GeoServer. This vulnerability allows for an unchecked JNDI lookup, which can lead to remote code execution through class deserialization.1 This brings the total number of CVEs whose exploitation we have observed up to 65.
April Vulnerabilities by the Numbers
Figure 1 shows the top ten vulnerabilities and their traffic for April. The gap between the CVE-2020-8958 at the top and the next vulnerability down is striking, even if CVE-2020-8958 is still experiencing roughly half of the traffic it received at its peak in January. The second place goes to the CVE-less JAWS vulnerability in several digital video recorders,2 followed by our newcomer, CVE-2022-24847.
The remainder of the top ten are types of vulnerabilities we’ve seen many times before—more IoT vulnerabilities, Microsoft Exchange RCEs, and flaws in various PHP tools and frameworks.
Table 1 shows traffic volumes for all vulnerabilities that we’re tracking, along with change from the previous month.
| CVE Number | Count | Change |
| CVE-2020-8958 | 7146 | 2635 |
| 2018 JAWS Web Server Vuln | 2677 | 1391 |
| CVE-2022-24847 | 2624 | 1348 |
| CVE-2022-22947 | 2089 | 391 |
| CVE-2017-9841 | 2062 | 298 |
| CVE-2020-0688 | 1365 | 254 |
| CVE-2018-10561 | 1028 | 203 |
| CVE-2021-28481 | 829 | -68 |
| CVE-2022-41040/CVE-2021-34473 | 799 | 81 |
| CVE-2019-9082 | 521 | -43 |
| CVE-2021-3129 | 485 | -101 |
| CVE-2018-13379 | 457 | 54 |
| NETGEAR-MOZI | 268 | -101 |
| CVE-2020-15505 | 255 | 35 |
| CVE-2014-2908 | 248 | 25 |
| CVE-2013-6397 | 247 | -53 |
| Citrix XML Buffer Overflow | 246 | 19 |
| CVE-2019-18935 | 221 | 107 |
| CVE-2021-22986 | 212 | 165 |
| CVE-2021-40539 | 206 | 0 |
| CVE-2019-12725 | 128 | 111 |
| CVE-2017-18368 | 114 | -28 |
| CVE-2021-26086 | 97 | -127 |
| CVE-2017-1000226 | 90 | -69 |
| CVE-2021-44228 | 48 | -303 |
| CVE-2022-22965 | 34 | -13 |
| CVE-2022-40684 | 33 | -32 |
| CVE-2020-25078 | 25 | -500 |
| CVE-2019-9670 | 24 | 11 |
| CVE-2020-3452 | 13 | 0 |
| CVE-2021-21985 | 10 | -6 |
| CVE-2018-7600 | 3 | 1 |
| CVE-2022-1388 | 1 | -26 |
| CVE-2021-25369 | 1 | -9 |
| CVE-2021-41277 | 1 | -13 |
| CVE-2008-2052 | 0 | 0 |
| CVE-2008-6668 | 0 | 0 |
| CVE-2017-0929 | 0 | 0 |
| CVE-2017-9506 | 0 | 0 |
| CVE-2018-1000600 | 0 | 0 |
| CVE-2018-18775 | 0 | 0 |
| CVE-2020-13167 | 0 | 0 |
| CVE-2020-17505 | 0 | 0 |
| CVE-2020-17506 | 0 | 0 |
| CVE-2020-25506 | 0 | 0 |
| CVE-2020-28188 | 0 | 0 |
| CVE-2020-7796 | 0 | 0 |
| CVE-2020-9757 | 0 | 0 |
| CVE-2021-20167 | 0 | 0 |
| CVE-2021-21315 | 0 | 0 |
| CVE-2021-26084 | 0 | 0 |
| CVE-2021-29203 | 0 | 0 |
| CVE-2021-33357 | 0 | 0 |
| CVE-2021-33564 | 0 | 0 |
| CVE-2021-3577 | 0 | 0 |
Table 1. CVE targeting volumes for April, along with change from March.
Targeting Trends
To better understand how April contrasts with previous months, Figure 2 shows a bump plot of targeting frequency. To avoid overplotting, this shows fourteen CVEs which together constitute the top five for each of the twelve months. Overall the last few months have seen few dramatic changes compared with Autumn 2022, with one exception: the chartreuse curve showing up in March and April represents the newly added vulnerability CVE-2022-24847, which seemingly came from nowhere to capture ~2500 connections in April.
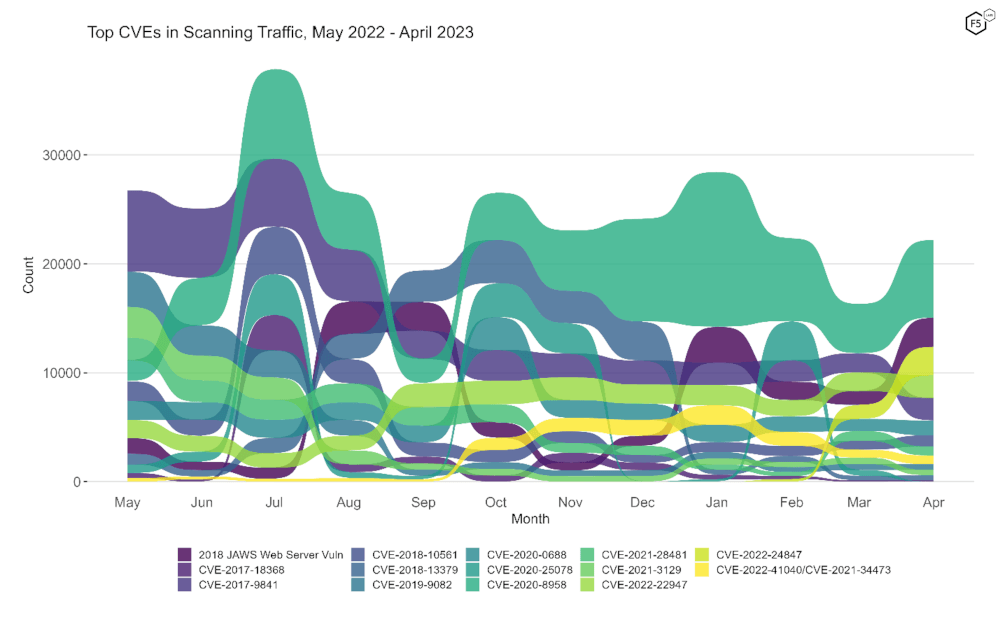
Figure 2. Evolution of vulnerability targeting in the last twelve months. This plot shows fourteen vulnerabilities which collectively represent the monthly top 5 for all twelve months.
Long Term Trends
Figure 3 shows traffic volume over the past year for all of the CVEs we track. In this view, the growth of the previously-untracked CVE-2022-24847 (fourth row, second column) over the previous three months is clear. The decline in CVE-2020-25078 (second row, third column) is also interesting, as it previously diminished in popularity only to resurge to a new peak in February 2023. Its subsequent subsidence to only 25 connections last month is further evidence about the unpredictable nature of attacker attention.
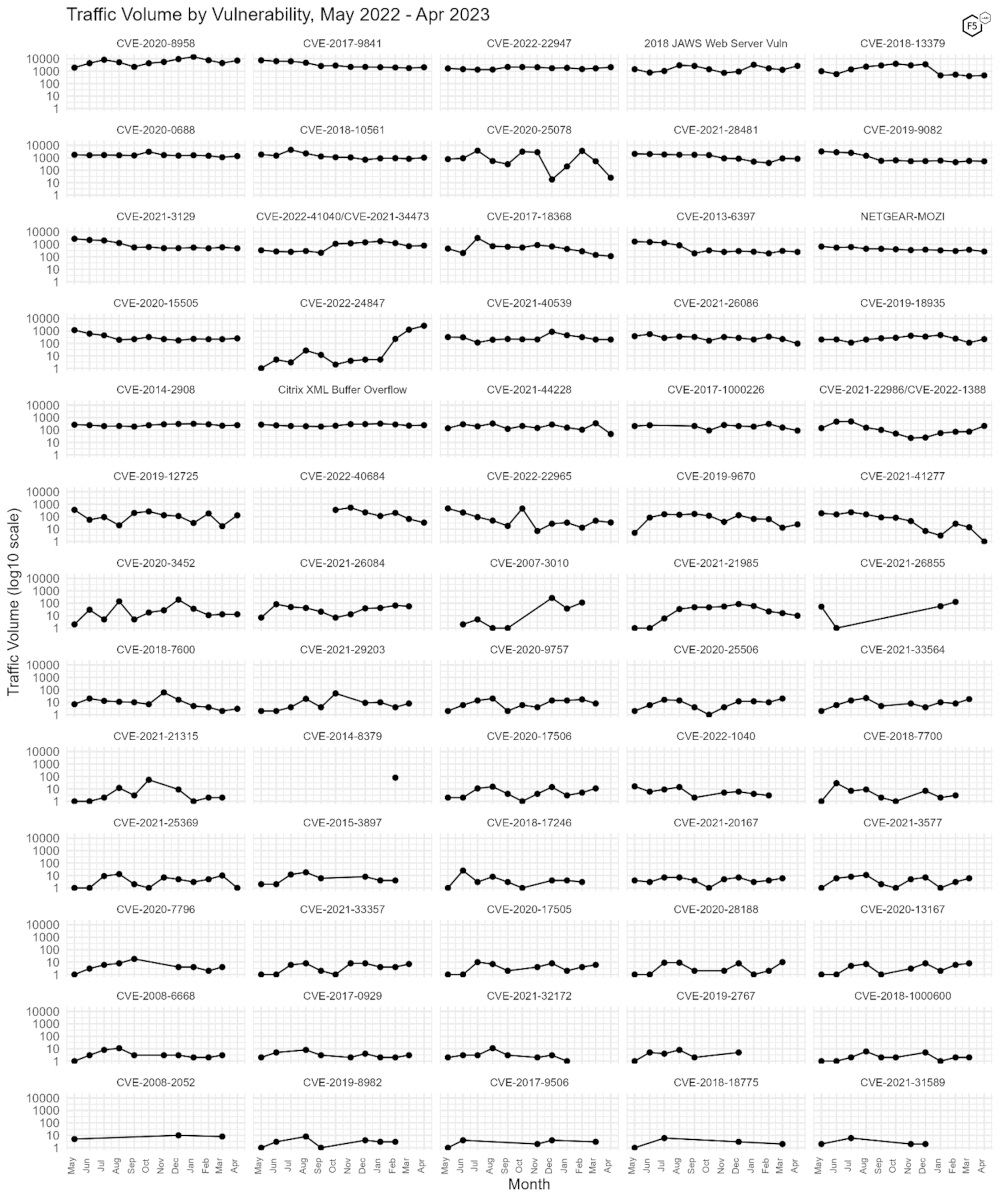
Figure 3. Traffic volume by vulnerability. The growth of CVE-2022-24847 (fourth row, second column) is apparent here, going from less than 10 connections for most months before growing to more than 1000 in March. Note log10 scale on y axis.
Conclusions
In April, our analysis of March traffic indicated that attacker focus on poorly secured IoT devices was being rivaled by their focus on Microsoft Exchange remote code execution vulnerabilities. With a few notable exceptions, all of which are focused on lightweight PHP web applications or services, this remains true, which is what makes our newest vulnerability in an open-source geospatial data web server a nice breath of fresh air.
Nevertheless, the high-altitude view of these attack trends do make certain attack scenarios or profiles stand out more than others, and the two that continue to float to the top here are high-impact compromises of Exchange servers leading to lateral movement and data exfiltration, as well as DDoS and other kinds of highly automated attacks. In general, we have been referring to the IoT threat as DDoS specific, and the fact that two gigabit-capable routers are in the top ten CVEs would seem to back this up, since their high throughput makes them extra-useful for DDoS. However, attacker infrastructure composed of IoT devices could also be instrumental in any kind of attack relying on scalability and distribution, including credential stuffing, reseller bots, or automated exploits of web vulns. In our urgency to alert everyone about the threat of DDoS, it is important not to undersell other threats as well. And with that, we’ll wrap it up and see you in June.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


