
The Sensor Intel Series is created in partnership with Efflux , who maintains a globally distributed network of sensors from which we derive attack telemetry.
It is time for another monthly round-up of web scanning and attack telemetry from our data partners Efflux. As usual, we focus on ports 80 and 443. It's been said for a long time that new services will increasingly use HTTP/TLS as their transport protocol, which is certainly true, especially as web API becomes a dominant way to provide services.
It's worth noting, however, that there is nothing inherent in those protocols that require them to be run on port 80 or 443. Indeed, many IoT devices, "private/internal" services, and proxies run webservers on alternate ports and are not therefore included in our analysis. Yet, we know that scanners are looking for HTTP/TLS services on alternate ports as well, and this should be a factor in any risk assessment.
November’s data doesn’t feature a huge amount of change from October, with most of the top vulnerabilities remaining consistent in terms of rank. However, the top-ranked vulnerability from October, CVE-2020-8958, outstripped its competitors in attack volume in November, featuring nearly double the traffic of the next vulnerability, CVE-2018-13379.
CVE-2020-8958
A command injection vulnerability in Guangzhou 1GE ONU V2801RW 1.9.1-181203 through 2.9.0-181024 and in V2804RGW 1.9.1-181203 through 2.9.0-101024 which allowed remote attackers to execute arbitrary OS commands. NVD
November Vulnerabilities By the Numbers
Figure 1 shows the attack or scan traffic for the top ten vulnerabilities in November. In this view, the difference between CVE-2020-8958 and the other vulnerabilities this month is notable.
CHART NEEDS ADDED HERE
Figure 1. Top ten vulnerabilities by traffic volume during November 2022. CVE-2020-8958, an IoT OS command injection vulnerability, received nearly double the amount of attack traffic as the next vulnerability down, CVE-2018-13379.
Even a single exploit attempt against a vulnerable system can be devastating, however, so Table 1 shows the attack volume and change from October for all 40 of the vulnerabilities that were targeted in November.
TABLE NEEDS ADDED HERE
Table 1. CVE targeting volume for November, along with traffic change from October.
One vulnerability, CVE-2014-2908, is a newcomer to our analysis.1 Despite being a very old vulnerability and having been in our logs the entire time, we recognized the indicators of attack and developed a signature for it only recently, which is why this is the first month it has shown up in the Sensor Intel Series. Note that the traffic volume for this vulnerability was 291 connections in November, which is consistent with its volume throughout 2022, so it would not have shown up in our top ten for any given month in any case.
CVE-2014-2908
A cross-site scripting (XSS) vulnerability in the web server embedded within Siemens SIMATIC S7-1200 industrial controllers v2.X and 3.x. NVD
Targeting Trends
To understand how attacker attention evolves over time, Figure 2 shows changes in rank and attack volume for the most heavily targeted vulnerabilities. The eleven vulnerabilities plotted here represent the top five per month across all eleven months, since plotting all 49 tracked CVEs would be impossible to decipher.
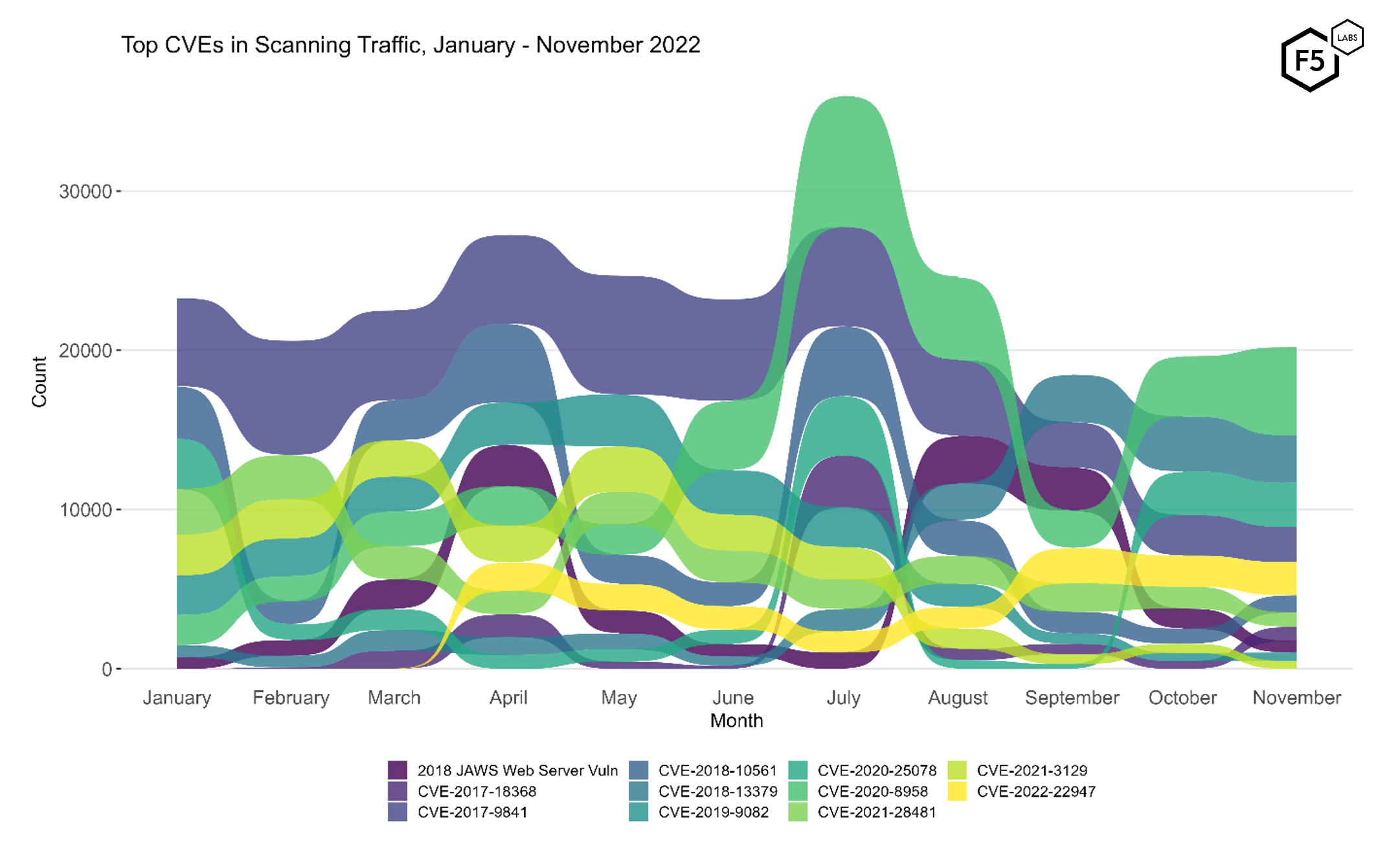
Figure 2. Evolution of vulnerability targeting, January - November 2022. Compared with October, there was no significant change, with all of the top five targets remaining consistent in rank.
Figure 2 makes it easy to see the comparative stability in attacker traffic between October and November, with the top five CVEs remaining consistent in rank. With the exception of CVE-2020-8958, which grew in traffic by nearly 50% in November, they also stayed roughly consistent in terms of attack volume.
Identifying Rapid Growth
Figure 3 shows the traffic over 2022 for all 49 vulnerabilities, ranked in order of total number of connection attempts from January to November. As discussed in the September and October SIS, this plot makes it easy to spot dramatic changes in attacker attention, as we see in CVE-2022-22947 in April and CVE-2017-18368 in March.
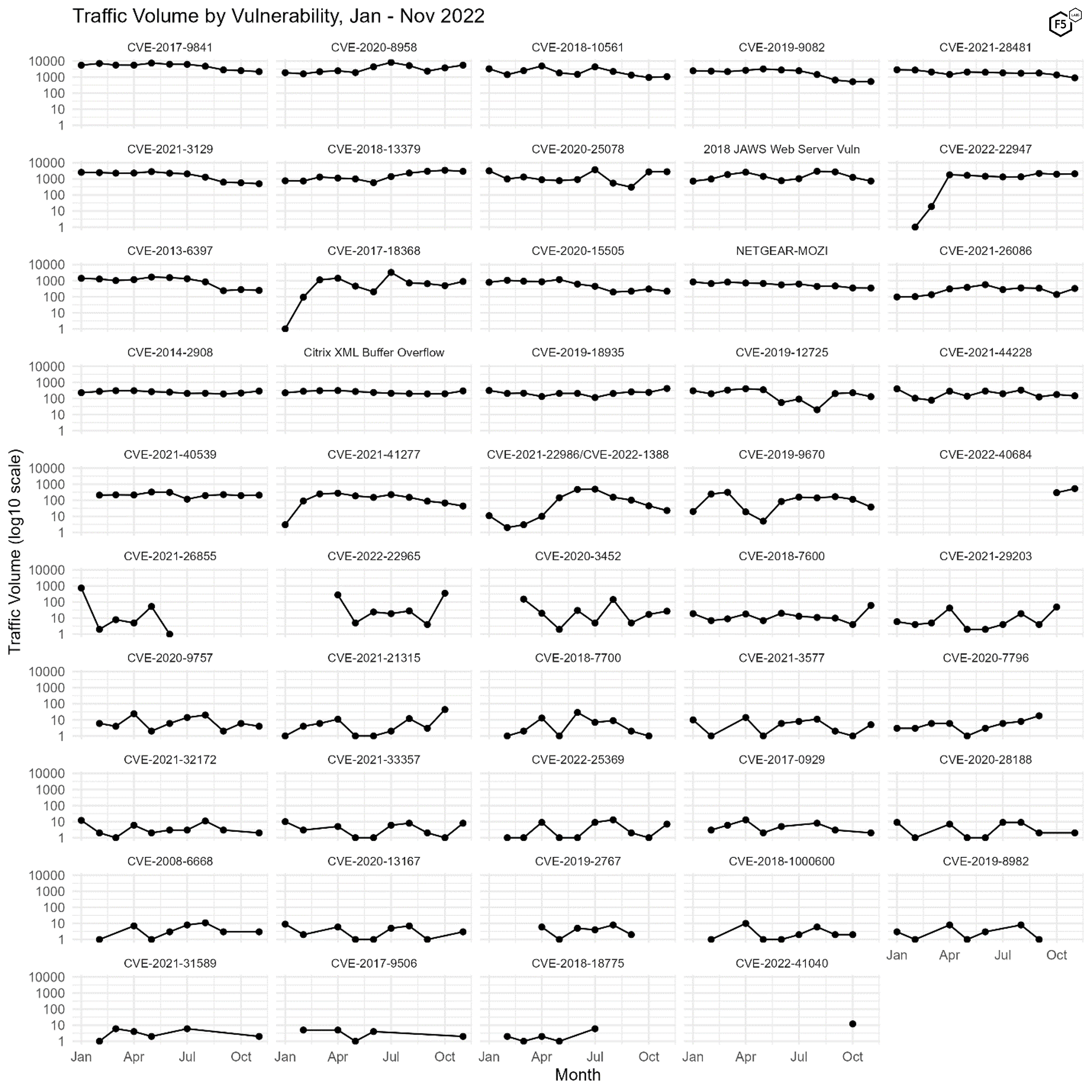
Figure 3. Plot of all 49 tracked CVEs over time. Note log10 scale on y axes.
Another interesting aspect of Figure 3 is identifying when vulnerabilities drop off for periods of time. In October we identified two recently released vulnerabilities, CVE-2022-40684 and CVE-2022-41040, in our logs. Both are severe vulnerabilities; CVE-2022-40684, an authentication bypass vulnerability in various Fortinet security appliances, has a CVSS 3.1 score of 9.8,1 and CVE-2022-41040, an escalation of privilege vulnerability in Microsoft Exchange Server, has a CVSS 3.1 score of 8.8.3 (https://www.f5.com/labs/articles/threat-intelligence/sensor-intel-series-top-cves-november-2022#_ftnAutoIncr3) CVE-2022-41040, the Exchange Server vulnerability, did not recur in our logs in November (which is good news), whereas CVE-2022-40684 increased in volume by nearly 80 percent (bad news). Owners of vulnerable Fortinet systems should take note and patch aggressively due to this growth in interest. We note that while attention on the other significant Fortinet vulnerability here, CVE-2018-13379, was nearly sixfold the traffic looking for CVE-2022-40684, CVE-2018-13379 is beginning to decline in prominence, so if the current trends continue, the more recent Fortinet vulnerability will eventually supersede it.
Conclusions
As ever, the number one conclusion from the Sensor Intel Series remains constant: patch if you’re vulnerable. Even the low-traffic vulnerabilities on this list have a demonstrated amount of attacker intent, which places them in the minority of vulnerabilities.
Furthermore, significant growth in CVE-2020-8958, alongside the recent addition of CVE-2014-2908 to our logs, should serve as a reminder about the relationship between IoT vulnerabilities and botnets for DDoS. This means that there is another recommendation for all organizations, irrespective of whether their footprint contains any of these vulnerabilities: plan for future DDoS attacks.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


