In early 2017, even decades after its adoption, the Domain Name System (DNS) is still the Achilles’ heel of the internet. This is because nearly everything on the Internet requires DNS, but the DNS service relies on a protocol that is both unreliable and easy to impersonate. It is for these two reasons that attackers target DNS for direct attack or subversion to support other attacks.
We dug deep into this in our 2018 Application Protection Report, noting various types of attacks on DNS as well as its use as a denial-of-service weapon. What are we seeing happening with DNS threats at the end of 2018? To get an idea, we talked to the F5 Security Incident Response Team (F5 SIRT), which tackles security problems for customers. Throughout the year, the DNS incidents they saw primarily fell into four categories.
DNS Water Torture Denial-of-Service Attacks
Customers reported pseudo-random subdomain or “DNS water torture attacks” hitting their networks with half a million connections per second. Outages were occurring even if a network wasn’t the direct target of the attack. For example, service providers still felt the effects as the DNS water torture traffic passed through their networks and saturated their pipes.
To pull off a DNS water torture attack, an attacker leverages a botnet (or thingbot) to make thousands of DNS requests for fake subdomains against an Authoritative Name Server.1 Because the requests are for non-existent subdomains or hosts, the requests consume the memory and processing resources on the main resolver. If there are intermediary DNS resolvers inline, they too get clogged up with these fake requests. For legitimate end users, all this resource consumption means everything runs slow or even stops, resulting in a denial of service.
Customers were seeing hundreds, thousands or, in some cases, millions of DNS requests for non-existent domains. When examined carefully, each request appeared to be pseudo-randomly generated strings of nonsense such as osentkjz.example.com, szavkcss.example.com, and xispprkn.example.com. The bots were generating the requests as fast as they could and then flooding them in.
What you can do about it
The first step is to understand your DNS environment: know what resolvers you have, where they are located, and what traffic load is normal for your organization. This means actively monitoring your DNS servers, not only for uptime but for load and resource usage. If a DNS water torture attack were to hit, how quickly would you be able to identify it as a DDoS attack and not an operational mishap? Without proper monitoring and security training in place, your team could lose precious minutes or hours of valuable uptime trying to figure out why customers can’t reach your site. The horror is that attacks that shut down DNS can also take out inbound email (as customers can’t resolve DNS MX records), so even customer complaints may not reach you.
The next step is to ensure you have a DDoS response strategy, which can include ensuring resilience for your DNS servers, a DDoS scraping/throttling technical solution, and/or having alerting/escalation plans for your team. As these attacks are a credible threat for most organizations, the impact of a DNS outage should be quantified in terms of expected losses and reviewed with business leadership.
Reflected DNS DDoS Attacks
F5 customers are also seeing old fashioned reflection DDoS attacks using spoofed DNS packets. Since DNS uses the non-stateful UDP protocol, an attacker can “reflect” fake DNS requests off of open DNS resolvers to generate storms of DNS requests to deluge their victims, as shown in Figure 1:
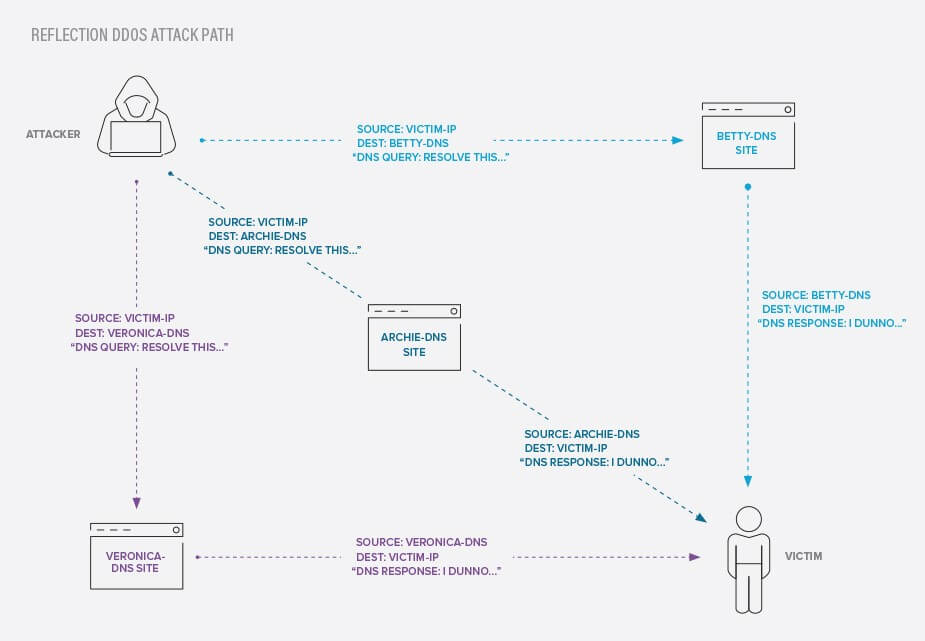
Figure 1: How a DNS reflection attack works
When this happens, customers are seeing lots of DNS queries from a wide variety of never-seen-before addresses. Often these requests are for nonsensical domains or even 'localhost' addresses, as they are bot-generated as with the DNS water torture attack. Sometimes attackers will use large Internet DNS resolvers like Yahoo or Google to reflect their attacks off of, so the source addresses may originate there.
If the DNS requests that are clogging up your Internet connections aren’t landing on live addresses, you may see returning ICMP Destination Unreachable messages bouncing back out from your network, which also add to the traffic jam. In these kinds of attacks, the DNS reflection attack acts like a network-volumetric DDoS, designed to fill up your pipes with traffic rather than targeting a specific service or host.
What you can do about it
As mentioned before, preparing your response to a denial-of-service attack is prudent for any organization that depends on the Internet (which is most). It’s also important not to be part of the problem. You should make sure that you don’t have any Internet-accessible resources that could be used in a reflective DDoS attack. This includes DNS resolvers, but can also include any service that accepts unrestricted spoofable traffic from untrusted sources like memcached servers, or services like Simple Service Discovery Protocol (SSDP), Network Time Protocol (NTP), or Character Generator Protocol (CharGEN).2
Expired Domain Takeovers and Redirection
Several customers reported attacks where some of their sites suddenly began redirecting to strange, disreputable websites. A normal landing page or e-commerce site had become an advertising page for gambling sites, a fake shopping site, or even a malware drive-by page. An attacker had registered the customer’s old, expired domain name and put up bogus sites to hijack the normal customer traffic. Since many of these sites already had large numbers of visitors, this was a semi-legitimate way for scammers to scoop up free website traffic.
Unfortunately, what the attackers did with the traffic was far from legitimate. Users of the original domain were served up annoying advertisements, scam messages, click-fraud sites, or malware. In worse cases, scammers have been known to put up imposter versions of the original site to steal the login credentials or payment cards of the customers3
What you can do about it
One of the reasons this happens is that organizations lose track of the domains they own and when they expire. Ownership of the domain inventory process should be centralized to a single team or role, and the responsibility assigned to track and manage renewals. Strong authentication and the principle of least privilege should also be exercised over domain ownership. When domains are ready to be retired, there should be a planned de-platforming process which can involve forwarding to the new domain for some time period until all users are migrated.
Outbound DNS from Compromised Internal Machines
Some customers contacted the F5 SIRT because they were seeing unusual outbound DNS traffic from their internal network. Investigation revealed it to be originating from compromised workstations and servers.
Let’s face it, malware and hacks are going to happen. Detecting and responding on unusual outbound activity is exactly what we want to happen. And as quickly as possible. These customers did the right thing and were able to contain and mitigate a bad situation before it escalated into something far worse.
What you can do about it
Like those customers above, it’s essential to keep a close eye on unusual outbound traffic, whether it’s DNS or otherwise. Attackers will try to hide their tracks by exfiltrating data and commands in a variety of ways, including DNS as it’s so ubiquitous and innocuous. Another common exfiltration method to sneak out is to hide attacker command and control traffic inside TLS/SSL conversations. Without an SSL decryption solution, the victim may never see what’s going on, just a machine web surfing via HTTPS, but not what’s going on inside.
Stay Vigilant
DNS security is still an existential threat to Internet services. Therefore, it is something that needs attention and protection. These are the current common DNS attacks that we’re seeing, so you should make sure your IT and security teams are well-informed about them. Remember how DNS works and that there are three major components that need to be appraised by security: DNS servers, domain name ownership, and DNS client traffic. Attackers know these are critical weak spots that don’t get enough scrutiny. Be ready for them.


