There are a lot of good reasons for a business to move its apps to the cloud, including cost savings, faster deployments, better resilience, and greater elasticity. Knowing this, businesses everywhere are embracing multi-cloud deployments as the best fit for the numerous, highly varied apps in their portfolios—which typically include the full range of classic applications (MS Exchange, SAP, etc.) and custom, in-house apps.
While there are a lot of important considerations when deploying apps in the cloud, two of the most important are security and flexibility. Those considerations, it turns out, are closely linked. The ability to secure web applications, particularly when they are dispersed across multiple cloud locations, can be—indeed, should be—built into your architecture from the outset. Doing so can ensure that you keep a consistent security policy across all your applications and can help your users (employees, partners, customers, or all of the above) enjoy a frictionless experience. That consistency also creates a degree of operational flexibility and resilience that makes it significantly easier to respond quickly to unexpected challenges or pivot to take advantage of new opportunities.
As John Wagnon points out in a recent Lightboard Lesson, cloud users need to know where their responsibilities actually reside. “Generally, the cloud operator is responsible for security of the cloud, and the user is responsible for security in the cloud,” he says. Unfortunately, this conceptualization leaves a lot of security concerns unaddressed. To keep your apps secure, you will need to fill in these gaps.
As you develop a plan for keeping your organization’s apps secure and resilient, three capabilities should be top-of-mind: consistency, control, and agility. The approach we recommend is similar to airport security. Instead of requiring every airline to operate its own security checks, travelers are screened at a consolidated checkpoint and then cleared to proceed to their gates. Similarly, a secure cloud architecture can pass all traffic through a uniform Security Virtual Private Cloud (VPC) before allowing access to a particular app. And just as the gate agent can reassign seats and check travelers’ tickets before boarding, each app can be empowered with additional security functions and capabilities.
In a scenario like this, the Security VPC can be responsible for many critical—and often resource-intensive—capabilities, including load balancing, WAF (and other firewalls), access management, credential encryption, SSL inspection, DDoS and bot protection, API management, performance management, and others.
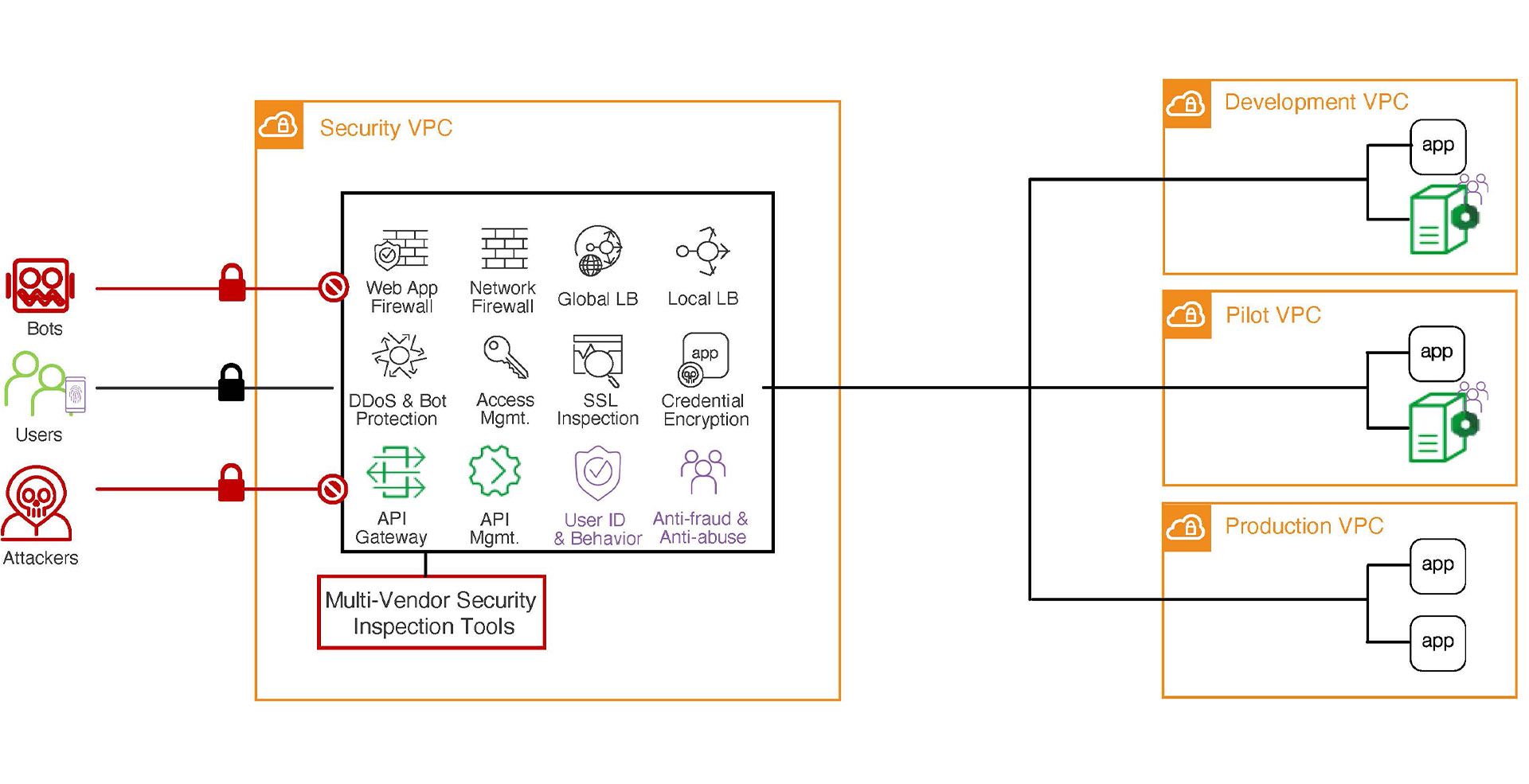
Services in the Security VPC can easily communicate with each other, creating additional benefits. For example, when your WAF intercepts an attack, it can notify your access control services so that they also block the attacker.
The ability to communicate across all elements in the Security VPC enables effective multi-vendor inspection, removing points of friction and redundancy for organizations that deploy inspection tools such as McAfee, FireEye, Palo Alto Networks, etc. Traffic that is unencrypted for SSL inspection can be passed to inspection tools for further examination. This is more efficient than requiring each tool to unencrypt, inspect, and reencrypt the same traffic.
This approach to creating a secure cloud architecture enables high levels of agility and scalability for app developers and helps reduce friction and improve collaboration across teams. Baseline standards are deployed in the Security VPC and should require minimal updates. Developers can add more security at the app level as required, relying on the Security VPC for the basics. Likewise, the network administrator can define security services for each environment (dev, test, production). If a developer launches an app with no pre-defined security capabilities, it is afforded the basic coverage defined at the VPC level.
Bringing apps from code to customer is as complex as ever. There are steps you can take to simplify the process while ensuring security across all environments and throughout multi-cloud architectures. Start by establishing a good entry point for all application traffic and providing baseline levels of security and traffic management through that point. From there, you have the flexibility to define additional security services at the application level. This dual-stage approach delivers reliable security while maintaining consistency, control, and agility.