
The Sensor Intel Series is created in partnership with Efflux, who maintains a globally distributed network of sensors from which we derive attack telemetry.
Additional insights and contributions provided by the F5 Threat Campaigns team.
Introduction
This article provides an analysis of the most active CVEs for March 2025, highlighting trends in exploitation activity and offering insights into mitigation strategies. Alongside the CVE analysis, we uncovered a new campaign targeting websites hosted in EC2 instances on AWS, involving exploitation of EC2 Instance Metadata via Server-Side Request Forgery. The data is derived from observed traffic and includes a focus on the top 10 CVEs, their long-term trends, and their relative activity over the past year.
Trending CVEs for March 2025
CVE-2017-9841, a PHPUnit Remote Code Execution vulnerability, continues to dominate scanning activity with close to 15x the activity of the second most active CVE this month. Despite being around 8 years old this CVE saw very little monthly scanning activity over the past few years, but we detected a huge increase in scanning for CVE-2017-9841 beginning in May 2024. While activity dropped off again a few months later, it appears that threat actors have commenced a new campaign with scanning activity almost reaching the levels we saw last year. Organizations should ensure that their PHPUnit installations are updated to secure versions or are otherwise shielded from malicious requests.
CVE-2023-1389, a TP-Link Archer AX21 Remote Code Execution vulnerability, remains a significant concern. This vulnerability can be exploited remotely, and users should follow TP-Link's patching guidelines to secure their devices. Last month’s headline “Enterprises Should Consider Replacing Employees’ Home TP-Link Routers” remains relevant.
CVE-2024-4577 is a PHP-CGI argument injection vulnerability affecting Windows systems by exploiting a character encoding bug. Attackers are reportedly leveraging this exploit for the typical end games: to deploy cryptocurrency miners, Remote Access Trojans, and distribute botnets.1 If feasible it is advisable to update PHP to the latest versions, or even more ideally switch from PHP in CGI mode to PHP-FPM (FastCGI Process Manager).2 It is understood that doing so will mitigate this class of exploitation.
CVE-2019-9082, a vulnerability in ThinkPHP, has seen a resurgence in activity. This flaw allows remote code execution and should be addressed by updating to the latest ThinkPHP version. It’s an unfortunate indictment of the state of security that our data continues to show demonstrate adversarial interest in old vulnerabilities such as this one. GreyNoise corroborated this recently: “40% of exploited CVEs were at least four years old”.3
Exploitation of EC2 Instance Metadata via Server-Side Request Forgery
Amongst our passive sensor data, this month we detected a brief spike in activity targeting insecure websites hosted within EC2 instances in AWS. This is a novel campaign unrelated to a CVE. While the exploitation technique is straight-forward, there’s a bit more to understanding the technical side of this exploit.
Campaign Timeline
During March 2025 we observed a four-day flurry of activity attempts to compromise EC2 Instance Metadata being inadvertently exposed by web sites through Server-Side Request Forgery (SSRF).4 EC2 Instance Metadata is a feature provided by AWS that allows an EC2 instance to access information needed at runtime without needing to authenticate or make external API calls. It can expose information such as the public or private IP address, instance ID, and IAM role credentials.5 Much of this is sensitive data of interest to attackers.
Early scouting activity shows up briefly on 2025-03-13 from a single IP address (193.41.206.72). The campaign kicked off on 2025-03-15 from 193.41.206.189 (and transitioned over the next six days through multiple IP addresses (all from the same ASN), until it quietened down and then finally ceased on 2025-03-25 (see Figure 1).
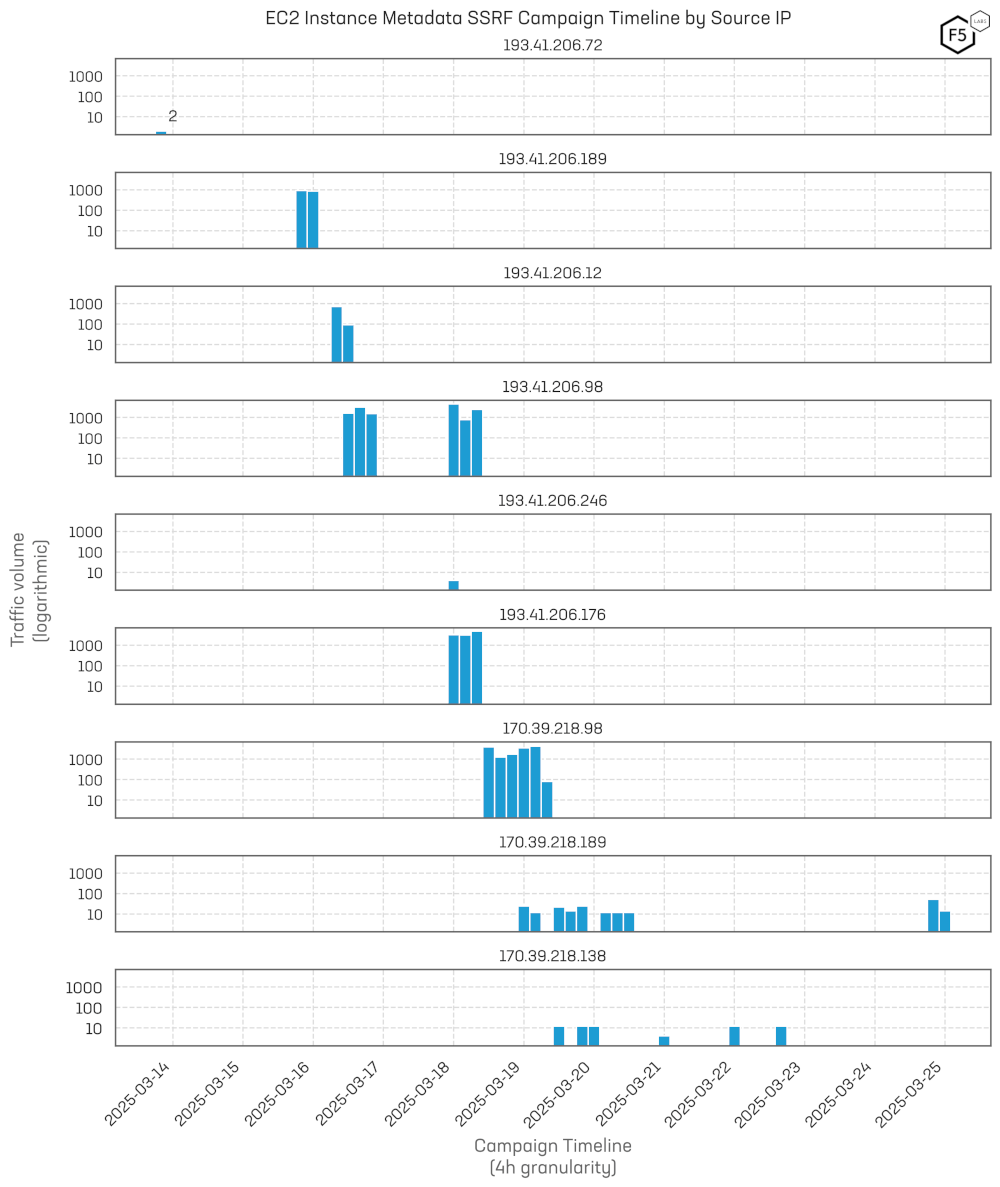
Figure 1: Campaign timeline of activity for exploitation of EC2 Metadata exposure via SSRF.
Exploitation Technique
Exploitation for this campaign is a combination of CWE-200: Exposure of Sensitive Information to an Unauthorized Actor6, and CWE-918: Server-Side Request Forgery (SSRF)7. The technique is relatively straightforward. We observed GET requests like /?url=hxxp://169.254.169.254/latest/meta-data/iam/security-credentials/. More generally, the requests were of the form /?parameter=hxxp://169.254.168.254/latest/subpath. In all, six distinct variations of parameter (dest, file, redirect, target, uri, url) combined with four variations in subpath were used in the campaign (see Table 1). Interestingly, F5 Labs was able to deduce that the behavior from all of these IPs displayed the same behavior of selecting these variations with uniform randomness. As then the exploitation technique was consistent across all IPs, F5 Labs concludes that this campaign stems from a single actor.
| subpath |
| /meta-data/ |
| /meta-data/iam/security-credentials/ |
| /meta-data/iam/security-credentials/admin-role |
| /user-data |
Exploitation Impact
Readers will be forgiven if the impact of the vulnerability and exposure combined is not apparent. EC2 Instance Metadata, IMDSv18 in this case, commonly exposes sensitive data such as valid AWS credentials to the EC2 instance via hxxp://169.254.169.254. Server-Side Request Forgery (SSRF) is a means of leveraging intentionally or unintentionally exposed functionality in a website for retrieving content over HTTP.
This excerpt from AWS documentation illustrates the impact of credentials in IMDSv1 in the light of an SSRF vulnerability:
“… [IMDSv1] data is not protected by authentication or cryptographic methods. Anyone who has direct access to the instance, and potentially any software running on the instance, can view its metadata...”9
Campaign Infrastructure
All IP addresses used in the campaign belong to the ASN: 34534. This ASN is owned by a French company “FBW NETWORKS SAS”, even though geographically the IP addresses are based in both France and Romania. According to Shodan, the hosts have remarkably similar configurations. All exposed the same version of SSH (OpenSSH_9.2p1 Debian-2+deb12u4). The majority had port 10250 open (commonly used for Kubernetes), with TLS certificates following a common pattern (Subject Alternative Names of either DNS:cold01 or DNS:cold07). The commonality of these characteristics suggests shared infrastructure.
Remediating Exploitation
In general, it is advised to consult authoritative sources of guidance such as from OWASP.10 For the specific case of IMDSv1 endpoints, it is advisable to consider applying WAF rules as 169.254.169.254 should not occur within legitimate requests.
The most robust and wide-reaching remediation guidance is to migrate from IMDSv1 to IMDSv2.11 Doing so requires an attacker to supply a secret via a custom header (X-aws-ec2-metadata-token). This fully mitigates exposure of EC2 Metadata via SSRF as SSRF vulnerabilities do not generally expose the ability to specify headers, and an attacker would need to determine the secret in addition.
Top CVEs for March 2025
In March, we observed over 69,000 instances of attempting to exploit CVE-2017-9841 which dominates activity for the month (as shown in Table 2). CVE-2023-1389 and CVE-2024-4577 follow with moderate activity levels, while CVE-2019-9082 and CVE-2022-24847 round out the top five.
| CVE ID | CVE Name | March Traffic | CVSS | EPSS | KEV |
| CVE-2017-9841 | PHPUnit eval-stdin.php RCE | 69433 | 9.8 | 0.94406 | ✓ |
| CVE-2020-8958 | Guangzhou ONU OS Command Injection RCE | 4773 | 7.2 | 0.84912 | × |
| CVE-2023-1389 | TP-Link Archer AX21 Command Injection RCE | 4698 | 8.8 | 0.94149 | ✓ |
| CVE-2019-9082 | ThinkPHP PHP Injection RCE | 3534 | 8.8 | 0.94141 | ✓ |
| CVE-2022-22947 | Spring Cloud Gateway Code Injection RCE | 2537 | 10 | 0.94474 | ✓ |
| CVE-2022-24847 | GeoServer JNDI Lookup RCE | 2291 | 7.2 | 0.00103 | × |
| CVE-2020-11625 | AvertX Camera Username Enumeration Vulnerability | 1747 | 5.3 | 0.00201 | × |
| CVE-2022-42475 | FortiOS SSL-VPN Heap Overflow RCE | 1575 | 9.8 | 0.92895 | ✓ |
| CVE-2022-47945 | ThinkPHP Local File Inclusion RCE | 1456 | 9.8 | 0.94376 | × |
| CVE-2024-4577 | PHP-CGI Argument Injection RCE | 1386 | 9.8 | 0.87359 | × |
Targeting Trends
CVE-2017-9841 saw increased activity levels over last month, maintaining the top spot (see Figure 2). CVE-2023-1389 held on to second place, while CVE-2024-4577 overtook CVE-2022-22947 and CVE-2019-9082.
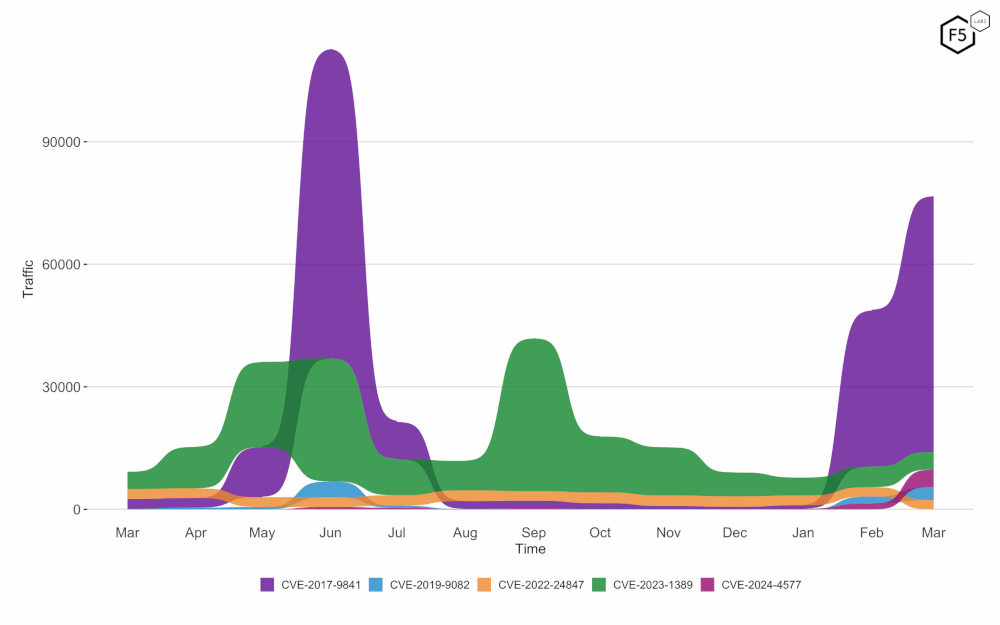
Figure 2: A bump plot showing the change in CVE traffic volume and position over the last twelve months.
Long Term Trends
Three CVEs stand out in the March data (see the logarithm scale plots in Figure 3). CVE-2019-9082 has shown a steady increase in activity, maintaining its breakaway from its previous downward trend. CVE-2024-4577 continues its upward trends. CVE-2022-47945 also maintains its new trend in sustained activity.
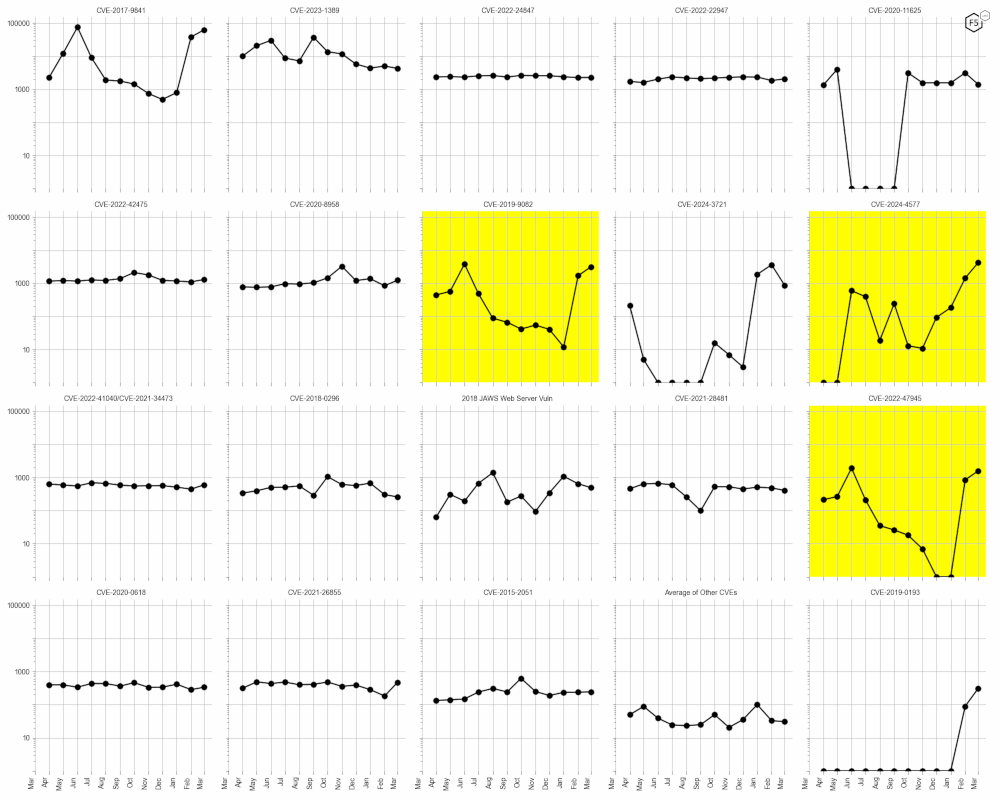
Figure 3: Evolution of vulnerability targeting in the last twelve months. This view accentuates the recent changes in CVE activity, of which the highlighted CVEs are most notable.
Conclusion
March 2025 saw significant activity across several CVEs, with CVE-2017-9841 continuing to lead the pack. The mounting interest in scanning activity for CVE-2024-4577 is one to keep an eye on. This month we detected novel exploitation of EC2 Instance Metadata exposure via SSRF. The exploitation was straight-forward but the technical details and impact were less obvious. As always, organizations should remain vigilant, prioritize patching critical vulnerabilities, and consider replacing outdated or vulnerable devices to mitigate risks effectively.
Recommendations
- Scan your environment for vulnerabilities aggressively.
- Patch high-priority vulnerabilities (defined however suits you) as soon as feasible.
- Engage a DDoS mitigation service to prevent the impact of DDoS on your organization.
- Use a WAF or similar tool to detect and stop web exploits.
- Monitor anomalous outbound traffic to detect devices in your environment that are participating in DDoS attacks.


