The Evolution of Ransomware
We’ve finally reached the boiling point with ransomware attacks. It’s gone from being a nuisance to a significant financial burden as well as a mortal threat to our critical infrastructure. In 2017, during worldwide WannaCry attack, F5 Labs raised the possibility of a ransomware infection at a hospital causing a patient’s death. It looks like we’re finally there.1 In addition, financial damage from ransomware attacks has escalated to hundreds of millions of dollars for some organizations.2
A single ransom demand to decrypt encrypted data can cost millions of dollars.3 But maybe you shouldn’t pay? The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has issued an advisory that paying ransomware could constitute illegally providing financial assistance to sanctioned countries like North Korea, Iran, and Russia or to specially designated nationals and blocked persons (SDN).4
In 2019, we talked about how to defend yourself against ransomware. It’s 2020, and attackers have improved and strengthened their ransomware capabilities. We’re now seeing thousands of ransomware variants, with names like Ryuk, Dreamon, Ragnar Locker, Crysis, RansomEXX, Clop, Netwalker, WastedLocker, Egregor, Netwalker, Nefilim, CryptoMix, Sodinokibi, SymmyWare, and DoppelPaymer.
Ransomware as a Service
Like every other business venture, criminal or not, ransomware has moved from early attacks of opportunity to a full-fledged commodity that’s packaged and priced for all comers. It didn’t take long to find ransomware as a service (RaaS) advertisements like the one shown in Figure 1.
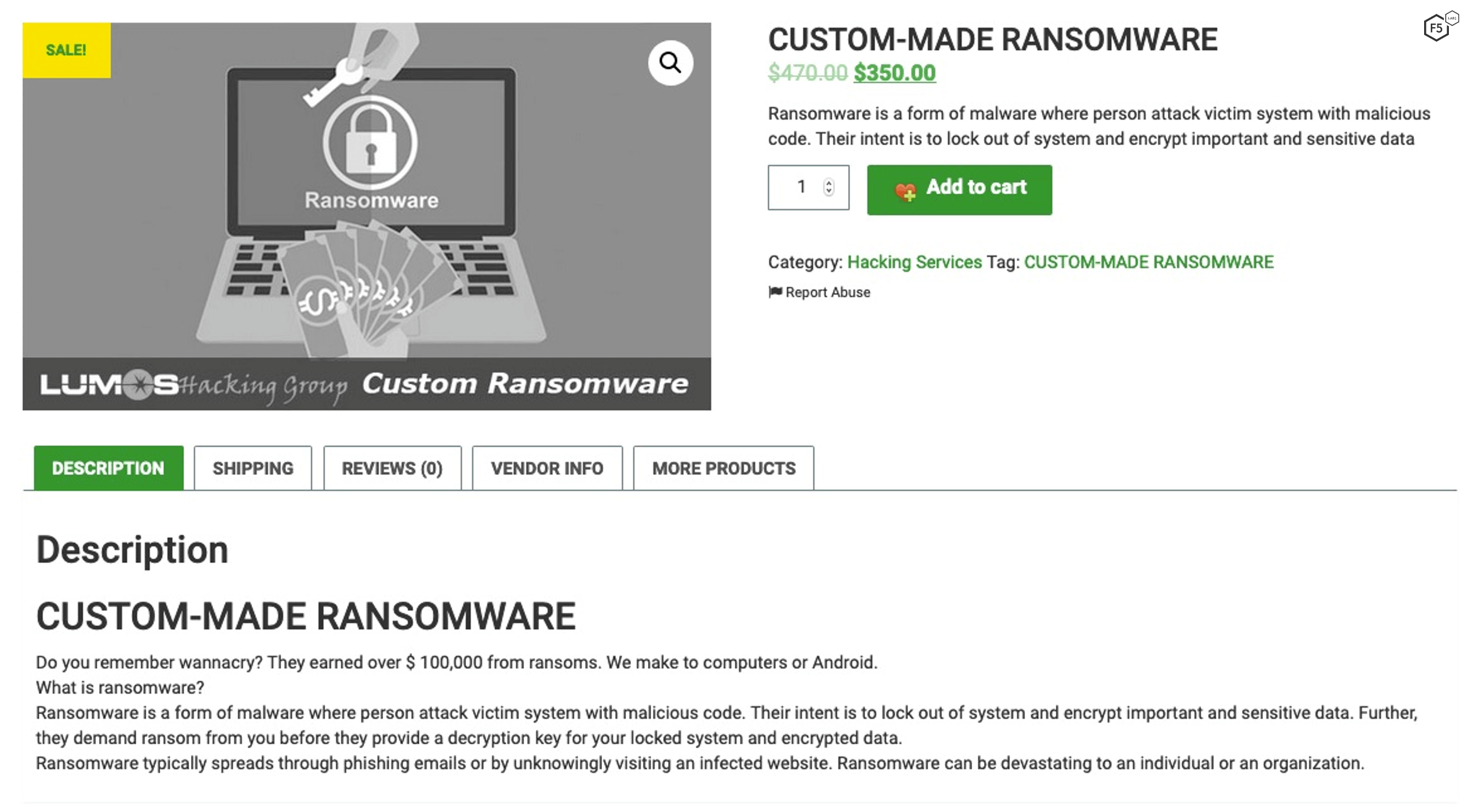
Figure 1. Dark web advertisement for customized ransomware for $350
How Ransomware Has Gotten Faster
Someone who’s on the frontlines of ransomware attacks is John-Luke Peck, principal consultant and deputy CISO for CI Security, which provides managed incident detection and response. He warns about the lightning speed of a ransomware attack: “Some companies learn about suspicious activity by getting a call from law enforcement one evening, and by the next morning their servers, workstations, and all their disk-to-disk backups were encrypted.” Let’s dig into how ransomware has changed to strike so quickly.
Smarter Encryption
One way to get faster is to work smarter—finding shortcuts and removing unnecessary steps can save time when seconds count. And it takes a lot of time to encrypt a multigigabyte file using a 4096-bit key with AES-256 encryption. One trick is to skip encrypting large files, hoping the victim doesn’t notice or hoping those files aren’t as valuable. Another shortcut is to encrypt only part of the file, which is often enough to cause an application-halting error when accessed.
Another timesaver is for the infection to check the physical location where it’s running. If the infector sees it’s not in a targeted country, it may delete itself and move on. Which countries does it avoid? Some ransomware variants will self-destruct if they think they’re within any of the nine Russian Commonwealth of Independent States.
Another way to work smarter is to spread from highly connected internal network nodes, such as Windows domain controllers. Since these kinds of servers interact with a majority of internal systems, they are excellent launching points to spread infections quickly. Figure 2 shows an advertisement for the new Dreamon malware with many of these features.
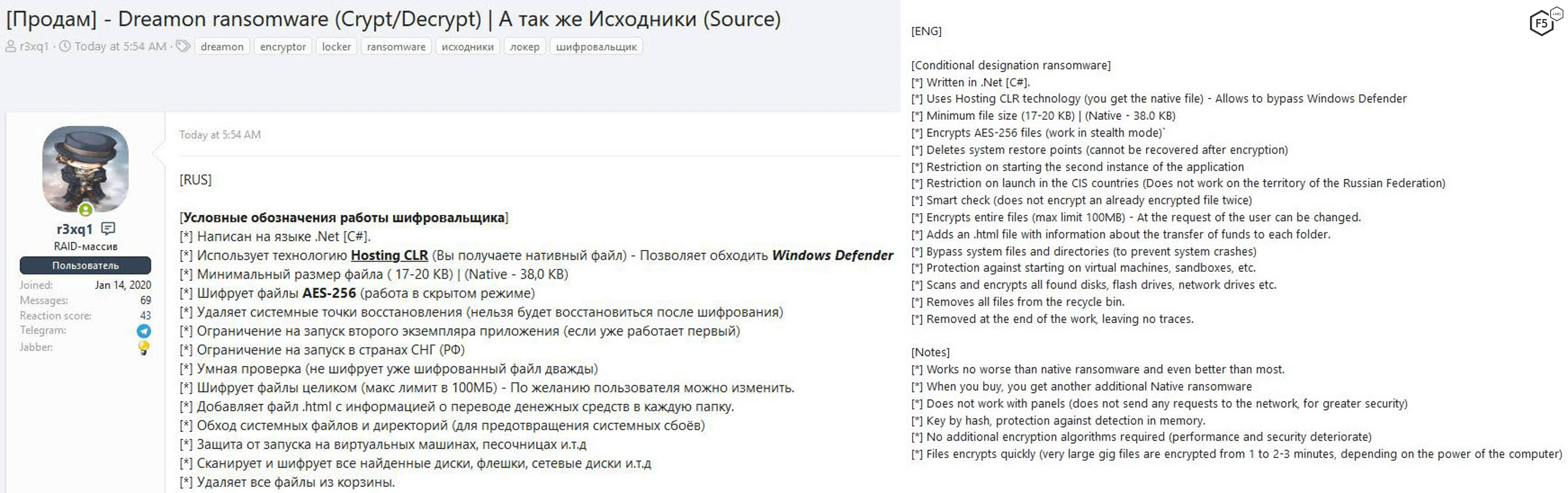
Figure 2. Russian darknet advertisement for Dreamon ransomware for $640
Hidden Malware, Crouching Ransom
One reason ransomware can appear to strike so quickly is because you only notice it once it’s too late. “Just because they’re in your network doesn’t mean you’ll see them,” notes Peck. “Ransomware and attackers often linger long before the ransomware goes active and begins encrypting your data.” The ransomware may remain dormant for quite some time, creeping around silently looking for the best place to strike. Attackers use this time to corrupt backup restore points and empty recycle bins, all to foul recovery efforts. Then, on a set date, the ransomware wakes up and begins encrypting everything at once.
How Ransomware Has Gotten Stealthier
If the ransomware is staying dormant longer, that means it needs to hide itself well. In fact, staying completely dormant upon load is a trick to bypass antivirus filters, which expect malware to begin executing immediately. Most modern ransomware will try to turn off antivirus software if it can. If not, it will obfuscate or encrypt itself and only unpack into memory to evade disk scanning tools.5
As for the encryption process itself, it’s helpful to examine it from a technical point of view. After loading the file into memory and encrypting it, it can replace the original file in only a few ways:
- Write the new encrypted data into the original file itself.
- Save the encrypted file as a new file, delete the original, and then rename the encrypted file to match the original.
- Save the encrypted file as a new file and use the built-in rename-and-overwrite-file function to replace the original file.
A Microsoft Defender anti-ransomware function called Controlled Folder Access can alert and block these operations.6 However, newer variants of ransomware use a stealth trick called RIPlace, which takes advantage of a Windows legacy function that allows rename-and-overwrite-file to run undetected, bypassing Controlled Folder Access.7
While ransomware is encrypting, it can slow down system performance noticeably. New ransomware can hide this by displaying fake error messages to mislead the user. Lastly, many ransomware variants try to use the built-in Windows tools and features to do their scanning and targeting, known as “living off the land.” By doing this, ransomware attacks reduce the number of detectable malware components running on the network.
How Ransomware Strikes Harder
Near the end of 2019, the Maze ransomware added a new feature: data leakage extortion. Not only did this malware encrypt all your data, it exfiltrated the confidential data to its servers. This quickly caught on as a powerful new motivator for ransomware authors.
Peck notes, “Some ransomware groups are exfiltrating data to the tune of terabytes copied out over days and weeks before the ransomware locks out the systems and data. This lets them get a copy of your important data for additional extortion—pay us or we’ll leak your data—and then get additional financial gains out of selling the stolen data as well as ransoming your network.”
Security-Resistant Ransomware
A common technical response for early ransomware was to perform forensics on the ransomware binary itself, either on disk or within memory. Sometimes this provides the encryption key, so you don’t have to pay to unlock all your data. Sometimes it’s to inform threat intelligence on ransomware and create new anti-ransomware defenses.
Ransomware countered with self-destructing malware. If the service running the ransomware stops, it crashes the machine so memory cannot be read. Ransomware was also designed to not run if it detected itself running inside a virtual environment or a debugger. The malware code itself can now also include random code fragments that mislead analysis tools. Some ransomware won’t activate without an unlock code, which the remote attacker sends. This makes it difficult for defenders to capture and analyze the ransomware program.
Stopping the Evolved Ransomware
How do you defend against this newer, more powerful ransomware? Obviously, practical and pragmatic security awareness training (/content/f5-labs-v2/en/labs/articles/cisotociso/information-security-awareness-training--reimagined.html) is a first step, especially stressing the seriousness of the threat and how everyone needs to work together. But you can muster your defenses on other battlefronts.
Stopping Ransomware’s Primary Vectors
No matter how sophisticated the ransomware code, the infection still needs to get into your systems. It does this in three primary ways: (1) by phishing, one of the most common ways attackers breach organizations; (2) by gaining unauthorized access, either by guessing/stealing login credentials or by entering through a trusted third-party access; and (3) by exploiting known vulnerabilities where it can load the ransomware. Our advice here is to:
- Investigate and inventory your attack surface to understand your exposure.
- Decrypt, inspect, and block user downloads and mail traffic.
- Review third-party security and restrict access to minimum necessary.
- Patch vulnerabilities—prioritize patches for known exploits in the wild.
Slow the Spread of Ransomware
Once ransomware gets into your systems, which is likely in organizations with large attack surfaces, you need to set up defenses in depth. We know that the ransomware will target your domain controllers, so harden and patch them. If attackers are going to try to “live off the land,” then restrict tools like PowerShell, Nltest, PsExec, McpCmdRun, and WMic via Group Policies. In general, only system administrators and power users should need this access anyway.
Restrict open internal file shares, especially ones with wide-open permissions, such as Authenticated Users, which means everyone in the organization has access. If ransomware infects any user’s machine, it’s safe to assume everything in those shares is going to be encrypted and/or leaked. If feasible, remove or disable outdated versions of Server Message Block (SMB), which most ransomware can easily subvert.
Reducing the Impact of Ransomware
If ransomware is going to exfiltrate terabytes of data, then either restrict or monitor outbound traffic. This means tools like SSL decryption and inspection. Peck adds, “Early detection is key, and early detection comes from good endpoint detection and protection, and good network monitoring and protection.”
Be sure to back up critical systems and data and store these backups offline so that attackers can’t corrupt them. Don’t forget build templates so that you can quickly reconfigure systems from scratch as well. If you are infected with ransomware, contact law enforcement. Not only will this help bring the perpetrators to justice, but it can also lessen potential OFAC violations if you decide to pay. Even if you pay the ransom, you should still rebuild any potentially compromised systems to ensure they are clean.
Lastly, prepare and exercise an incident response plan so everyone knows who to notify and what to do when attackers strike.
Recommendations
- Implement authentication solutions
- Use multi-factor authentication
- Deploy anti-virus solutions
- Use an intrusion prevention system (IPSs)
- Restrict Administrative Tools
- Restrict internal filesharing via SMB
- Harden critical internal systems such as Domain Controllers
- Denylist suspicious URLs
- Inspect & Filter encrypted traffic
- Enforce separation of duties
- Provide security awareness training
- Use intrusion detection systems (IDSs)
- Actively monitor systems and review all logs
- Review access rights
- Review audit logs
- Review user permissions
- Initiate backup and restore plans
- Patch vulnerable systems
- Implement business continuity plan and incident response plan


