As service providers start gearing up for their digital transformation, they need to have insight into the threat landscape of their mobile telecommunications ecosystem. Digital transformation means that service providers must simultaneously manage multiple networks—3G, 4G, and 5G, each with their own complexities and vulnerabilities. This means that service providers are not only dealing with increased network complexity, they also must address increases to their attack surface. Mitigating and managing existing threats while anticipating the demands of 5G security is critical to providing network security and ensuring customer trust.
As security threats become more prevalent and sophisticated, understanding the source of these threats makes it easier to establish proper defenses

Service providers will be faced with an increasing number of connected devices as 5G brings reduced latency and improved bandwidth. GSMA predicts that, by 2025, service providers will need to support:
As the number of connected devices increases, so will attacks, including attacks that take advantage of inherent vulnerabilities in the simple, everyday tasks that most users take for granted. This diagram lists some activities that customers take that can increase their vulnerability to attack. Security must protect customers from these vulnerabilities and adapt as attackers retool to bypass countermeasures.

Additional attacks against mobile users include:
5G brings increased network complexity and an exponential increase in the number of connected devices. More connected devices means there is a bigger attack surface that could be exposed to sophisticated and malicious attacks. As the attack surface grows, it will become harder to assess and intercept cybersecurity risks. Several threats will be discussed such as IoT, signaling, API and N6/Gi-LAN threats.
GSMA estimates that the number of IoT connections will reach 24.6 billion 2025.2 IoT devices are increasingly used in botnets. Botnets (compromised networked devices used to initiate malicious attacks) are most commonly used to carry out distributed denial-of-service (DDoS) attacks. As 5G networks are embraced by industries like healthcare, manufacturing, fintech, government, and others, protection against botnets becomes even more critical. A recent study confirmed that IoT security is top of mind for service providers; 39% of the respondents are already implementing IoT security, and a further 27% of respondents will implement measures in 2021.3

Service providers must address the signaling challenges caused by increased traffic volumes in 5G network deployments. Legacy security issues in 4G and 3G networks also must be addressed as service providers migrate to 5G and standards evolve.
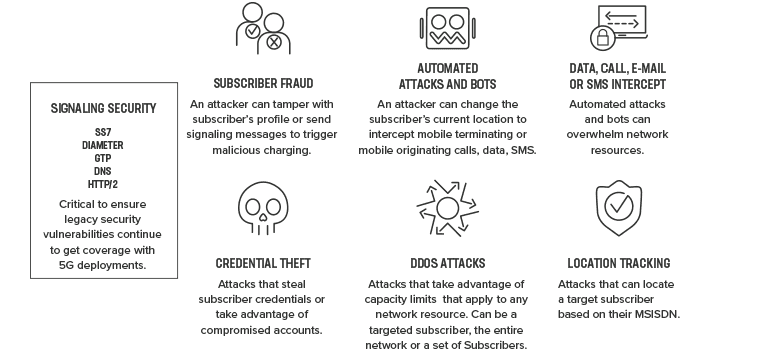
Signaling security is vital for service providers. Based on the Heavy Reading analyst report, the top three priorities for control plane security are NEF (41%), 5G HTTP/2 signaling firewall (40%), and NRF (37%). Somewhat concerning are the two groups that represent 28–38% of all service providers that plan to implement these capabilities within either 12–17 or 18–24 months after commercial launch. Because 5G will coexist with 4G networks, service providers need time to ensure seamless interworking with existing 4G security network platforms, making security implementation that much more important.5

API Threats The 5G network core is based on SDN/NFV, making heavy use of the HTTP/2 and REST API protocols. Because these protocols are well known and widely used on the Internet, tools for finding and exploiting vulnerabilities are available to any bad actor. Web security faces widespread challenges; despite the best efforts of the IT and security industries, well-protected websites are the exception rather than the rule. The average web application contains 33 vulnerabilities and 67 percent of web applications contain high-risk vulnerabilities.7 APIs are designed for machine-to-machine data exchange; many APIs represent a direct route to sensitive data. This means that most API endpoints need at least the same degree of risk control as web applications.

The N6 LAN (previously known as S/Gi-LAN) is the interface that lies between the user plane function (UPF) and the Internet. N6 LAN functions are often consolidated to optimize network performance and reduce costs. This interface is the gateway to the Internet and must be properly secured. Some security features that are normally located here include: Carrier-grade network address translation (CGNAT) N6 (Gi) firewall DDoS protection IoT firewall Subscriber security services Secure DNS cache Service providers continue to see a role for traditional Gi-LAN products in their 5G portfolio. The figure below shows the results of a survey in which service providers were asked to rank the solution offerings of Gi-LAN/N6. Firewalls, DDoS mitigation, and CGNAT represent the top three security concerns.

Service providers will be able to monetize their 5G networks by offering edge use cases for enterprise innovations. 5G networks are decentralized and incorporate a distributed, multi-cloud architecture. In a distributed cloud model, cloud services are extended from edge devices all the way to the 5G core data center. Edge computing increases the security risk for service providers, with IoT devices, increased data volume, and edge infrastructure all providing rich targets for bad actors.
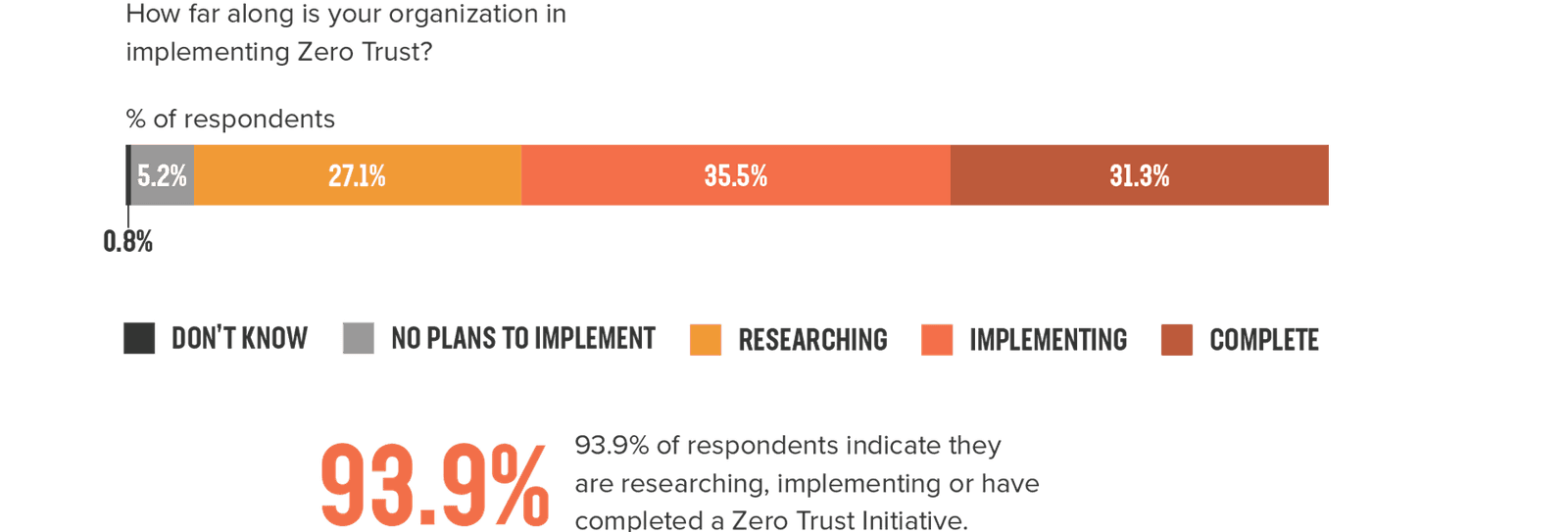
With hybrid and multi-cloud architectures, many service providers are adopting a Zero Trust security model. Zero Trust security uses real-time information collected from each subscriber. Analysts report that 93% of respondents are either researching, implementing, or have completed a Zero Trust initiative.10 The exponential growth of IoT devices provides further motivation to adopt a Zero Trust security model, lest zombie IoT devices carry out DDoS attacks at the speed of 5G.
“"Security at the edge remains a huge challenge, primarily because there are highly diverse use cases for IoT, and most IoT devices don't have traditional IT hardware protocols. So the security configuration and software updates which are often needed through the lifecycle of the device may not be present," says Barika Pace, research director at analyst firm Gartner.11”
Although most mobile networks use private clouds, edge locations are increasingly relying on public cloud solutions. Mobile network operators are partnering with hyperscalers to build an edge solution that will appeal to enterprise industry. Every service provider will have different architectures, deployment plans, and timelines, but these all must be informed by a security strategy that ensures end user Quality of Experience (QoE). In the 2020 State of Application Services Report: Telecom Edition, we reported that 90% of respondents are operating in a multi-cloud environment, and the majority of these respondents report that security was a major concern when planning their networks.13 Among service providers, 90% are selecting their cloud infrastructure based on their specific use cases. Matching cloud services based on the application drives operational improvements and could enable service providers to leverage functionality offered by the cloud provider.
“90% of telecom providers are operating in a multi-cloud environment, with security concerns top of mind.14”

As service providers embark upon their 5G migration journeys, they are faced with new cybersecurity threats throughout their digital landscape, from devices to the edge to the 5G network and into the cloud. To mitigate these threats, they must proactively incorporate security into every step they take as they build 5G networks and integrate them with their existing infrastructure.
Contact us to learn more about how F5 can help you adopt a strong 5G security posture.
1 GSMA: The Mobile Economy 2020
2 GSMA: The Mobile Economy 2020
3,4,5,6 Heavy Reading, 5G Security: The Multifaceted Art of Cloud-Native Threat Management
8 Heavy Reading, 5G Security: The Multifaceted Art of Cloud-Native Threat Management
9 Heavy Reading, 5G Security: The Multifaceted Art of Cloud-Native Threat Management
10 AT&T Cybersecurity: 5G and the Journey to the edge 2021
11 ZDNET, Edge Computing: The cybersecurity risks you must consider
12 AT&T Cybersecurity: 5G and the Journey to the edge 2021
13,14,15 F5: 2020 State of Application Services Report, Telecom Edition