Companies like Uber, Airbnb, PayPal, and others with platform business models have flourished in the past few years by matching up service providers (such as restaurants and drivers) to consumers and hiding the complex, behind-the-scenes processing (like payments) from users The rapid adoption of this business model has brought it into the cross hairs for fraudsters, who are always scheming to game the system and illegally monetize legitimate business processes. F5 Labs has found that attackers are defrauding digital systems by colluding with other participants who serve different roles on the platform. This article discusses this phenomenon, which we call collusion fraud.
What Is Collusion Fraud?
Collusion fraud occurs when two or more participants conspire to defraud another participant in a digital business transaction that involves multiple participant groups. This type of fraud is growing in prominence as more digital businesses pivot to become platforms that serve more than just one purpose. For example, an online e-commerce provider’s digital platform allows a consumer to select items from a seller of their choice and have it delivered. A single business transaction on that platform provides online processing, payment, preparing goods, logistics, and delivery. Completing these activities require services from multiple providers specializing in different areas, which at times takes the processing out the platform’s control. The collaborative act to complete these multistep business transactions provides an avenue for malicious players. Fraudsters design these hacks so they can quickly make money and target returns that are generated as by-products of the main transaction, such as a cashback reward or gratuity. These by-products are usually managed separately from the main transaction and are often hard to reclaim post–fraud detection if the consumer or other participant has already used them.
Collusion Fraud in Action
Collusion fraud can happen in any industry vertical. F5 Labs and Shape Security researchers followed two cases of fraud that revealed collusion in action. Fraudsters made gains in these cases in the form of gratuities and cashback rewards points.
Case One: Leading Food and Beverage Company
The first case involved a leading food and beverage (F&B) company in which collusion fraud manifested as gratuity, or tip, abuse. The company’s digital platform provides a convenient service to its customers by bringing together the restaurant outlet, logistics requirements, and online payments. Figure 1 explains the legitimate process in completing an online transaction that includes a tip.
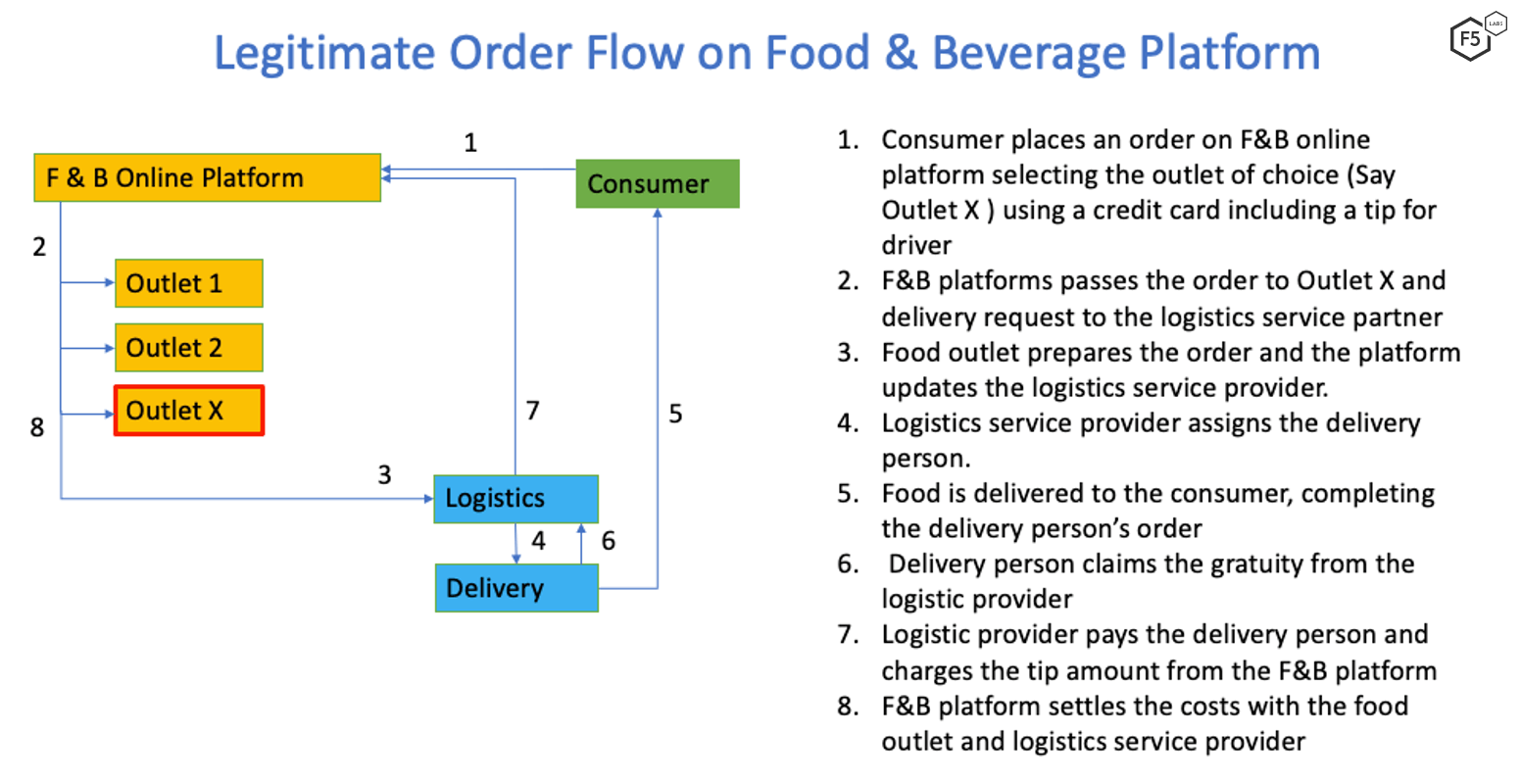
Figure 1. Order flow on a food and beverage provider platform.
In this specific case, the consumer-fraudster and a delivery person collude to monetize stolen credit cards. They achieve the collusion fraud through the following steps:
Using a stolen card, a fraudster places an expensive order (more than $300) that includes a generous tip (usually more than 30 percent).
The order goes through the standard, legitimate lifecycle, as described in Figure 1.
The credit card owner detects the transactions and disputes the charges with the bank. This leads to a charge-back on the F&B platform for the full amount of the order, including the tip.
The tip amount that was paid out for the delivery service cannot be recalled.
Shape’s security data reveals that in a period of three months this particular F&B online platform received almost 3,000 collusion fraud orders with a cumulative value of USD $1.5 million and gratuity/tip amounting to about USD $350,000.
Case Two: Leading Online Payment Wallet
The second case involved a leading online payment wallet that suffered in the form of cashback rewards due to collusion. Figure 2 documents the legitimate flow of a transaction initiated by a consumer.
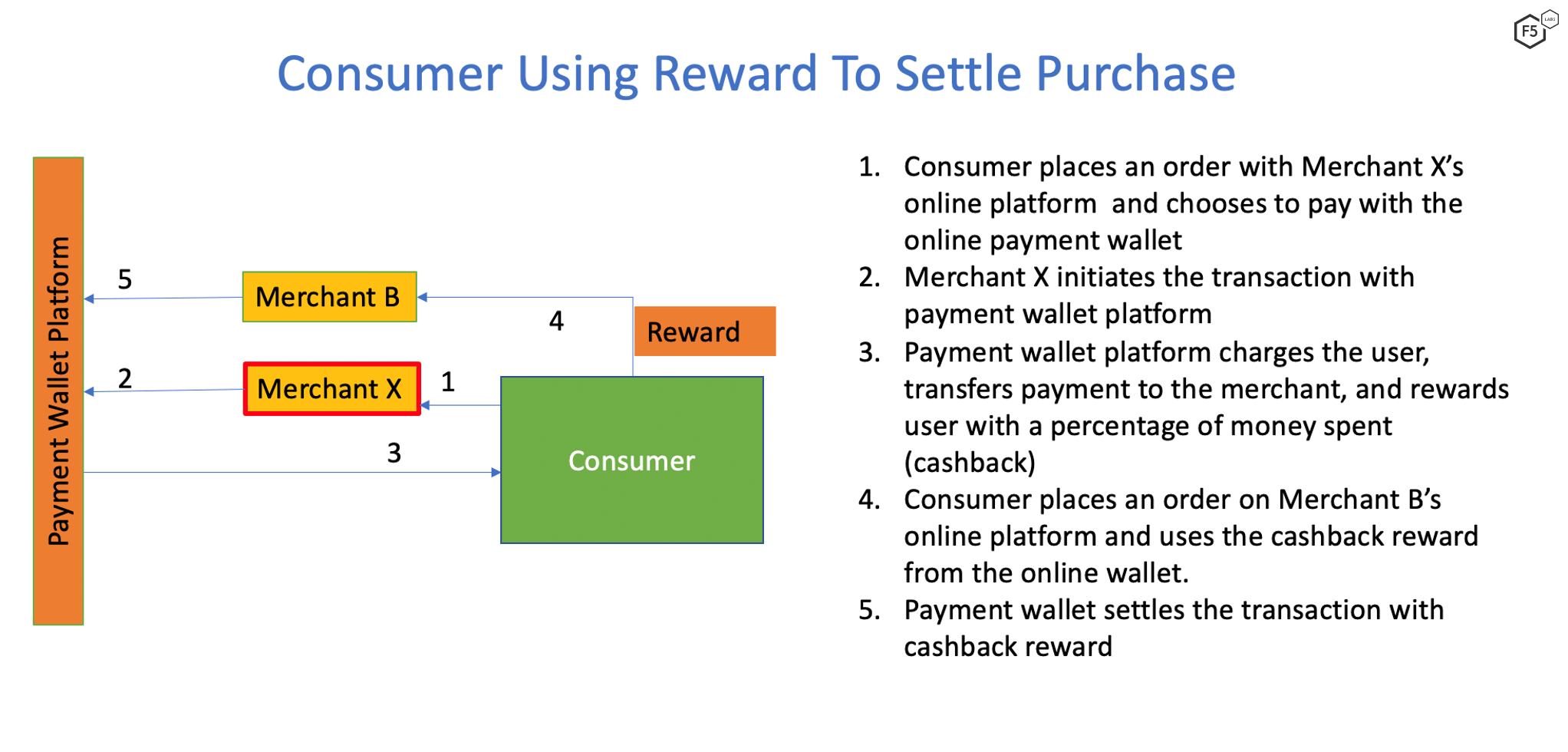
Figure 2. Consumer flow for earning and spending cashback rewards.
In this case, the consumer and Merchant X conspire to defraud the payment wallet platform of rewards points in the following manner:
Consumer purchases goods from Merchant X using a payment wallet platform.
As shown in Figure 2, the consumer earns rewards points, which are then used to purchase goods from Merchant B. Once the cash back reward is consumed, Merchant X refunds the original sum to the user, citing reasons such as unavailability of stock.
The payment wallet refunds the original sum to the user, but the cashback rewards are not recoverable.
Conclusion
As the adoption of digital services and platform businesses grows, consumers will be enticed by various incentives beyond cashback rewards. Fraudsters will find a way to collude to steal these incentives, resulting in greater varieties of collusion fraud.
Detecting collusion is difficult and will require artificial intelligence to weed out such transactions at scale. F5 recommends the following security controls:
Recommendations
- Use artificial Intelligence-powered analytical models, clustering groups and transaction to detect collusion fraud.
- Train and retrain the AI models as fraud techniques evolve.


