Executive Summary
Phishing remains a popular method of stealing credentials, committing fraud, and distributing malware. But what appears on the surface to be a juvenile form of cybercrime can be, in practice, a well-orchestrated, multi-faceted, and sustained attack campaign by organized crime groups. From finding victims and creating phishing sites to harvesting and fraudulently using victims’ credentials, it can be difficult to build a complete picture of the end-to-end process. We focus our report on how fraudsters are building, staging, and hiding their phishing sites and the tactics they use to remain hidden. Using insight from Shape Security, we also show how quickly cybercriminals are making use of their stolen goods.
This year’s Phishing and Fraud report examines five years’ worth of phishing incidents from the F5 Security Operations Center (SOC), and deep dives into active and confirmed phishing sites supplied by OpenText’s Webroot® BrightCloud® Intelligence Services, and analyzes dark web market data from Vigilante. Together, these build a complete and consistent picture of the world of phishing.
In our 2019 Phishing and Fraud Report, we noted a significant abuse of free and automated services, such as blogging platforms and free digital certificate services. Fraudsters made heavy use of automation with very little, if any, financial outlay. We saw emerging use of encryption with just over half of all sites leveraging HTTPS, and attackers were creating lengthy and deceptive web addresses (URLs) in order to appear genuine and confuse their victims.
The past twelve months has been not a revolution in the attackers’ methods but an evolution, and 2020 is on target to see a 15% increase in phishing incidents compared with last year. This year we found that phishing incidents rose by a staggering 220% compared to the yearly average during the height of global pandemic fears. Fraudsters were quick to seize upon the confusion and we saw large spikes in phishing activities that closely coincide with various lockdown rules and the increase in homeworking. Using certificate transparency logs, we found that at its peak, there were almost 15,000 active certificates using “covid” or “coronavirus” in their names. On the topic of encryption, the use of HTTPS also rose sharply across all phishing sites with an impressive 72% making use of digital certificates and TLS encryption. The dramatic increase in phishing activity at the beginning of lockdown could well be a factor in the sharp rise of stolen payment cards discovered in May and June of this year. The number of cards of seven major global banks found on darknet markets was almost double a similar peak period in 2019.
Fraudsters are becoming more creative with the names and addresses of their phishing sites. Attempting to create ever more realistic website addresses, we found that 55% of phishing sites made use of target brand names and identities in their URLs. We tracked theft of credentials through to their use in active attacks and found that criminals were attempting to use them within 4 hours. In some cases, the attacks occurred in real time.
Vulnerable websites continue to present an opportunity for fraudsters to host their phishing pages on a reputable URL, for free. We found that WordPress sites alone accounted for 20% of generic phishing URLs.
This year we also found that Office 365 continues to present a rich and compelling target for attackers with fraudsters employing new tactics such as “consent phishing”. And an increasing number of phishing sites are using evasion techniques to avoid detection and inspection by targeted businesses and security researchers.
Despite the continued growth of phishing attacks, security controls and user training are failing to adequately combat it. Fraudsters know that the way to make a quick buck isn’t to spend months attempting to breach an organizations security, it’s simply to ask nicely for the username and password so they can walk right in through the front door.
Introduction
Phishing, the email focused form of social engineering, shows no sign of abating. It remains just as popular with organized cybercrime as it is with nation states for one simple reason: it works. The number of phishing incidents in 2020 is projected to increase by 15% compared with last year, according to data from the F5 Security Operations Center (SOC) (see Figure 1). F5 Labs’ 2020 Application Protection Report (/content/f5-labs-v2/en/labs/application-protection.html) found that 52% of all breaches in the US were due to failures at the access control layer. These include credential theft, brute force login attempts, and phishing. Across the pond, data released by the UK’s Information Commissioner’s Office (ICO), showed that phishing was the number one cause of cyber related data breach for their reporting period covering April 2019 to March 2020, accounting for 28% of all cases.1 The trend continues all over the world. Numbers from the Office of the Australian Information Commissioner (OAIC) show that phishing holds the top spot in malicious cyber incidents, accounting for 36% of all cases reported to them.2 Theft of credentials, one of the most common initial attack vectors for cybercriminals, is a close second and is responsible for 29% of all incidents (July 2019 to June 2020).
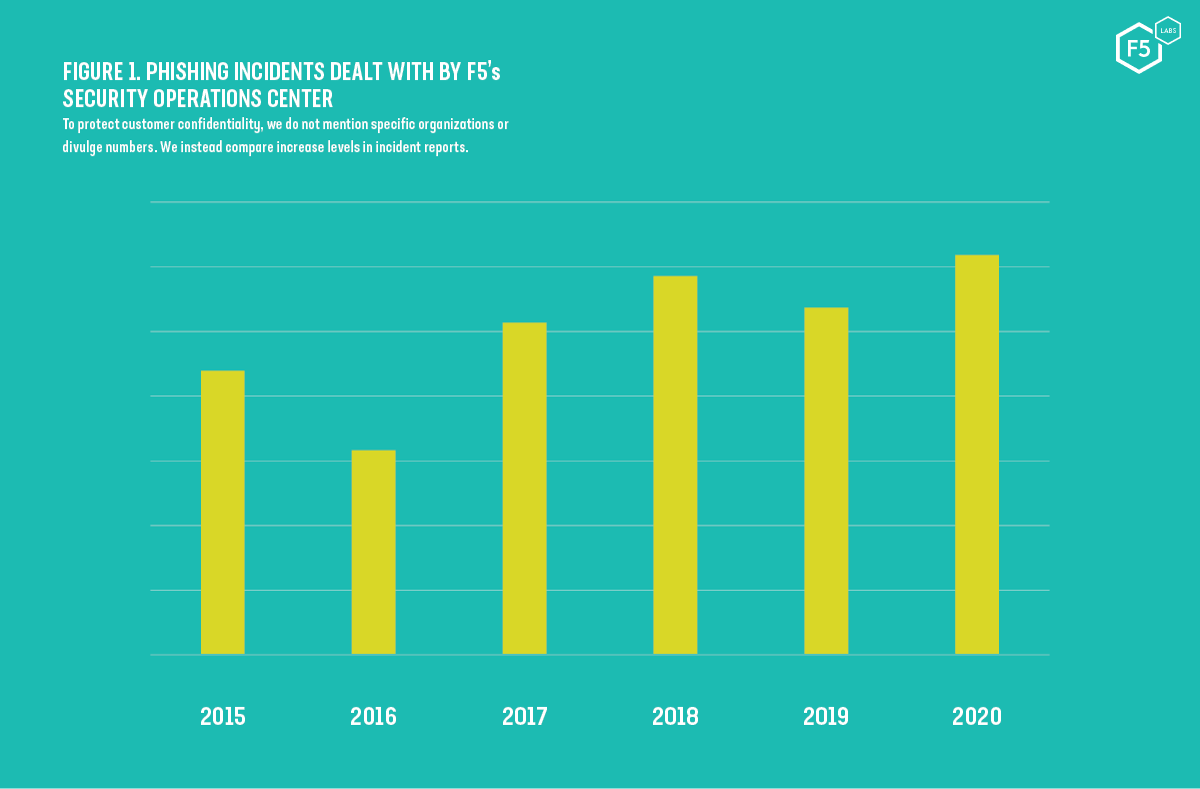
Figure 1. Phishing incidents dealt with by F5's Security Operations Center.
Phishing is now such a problem that the 2020 Verizon Data Breach Investigations Report (DBIR) noted the use of malware and trojans had dropped significantly and that “attackers become increasingly efficient and lean more toward attacks such as phishing and credential theft.”3 Europol’s latest Internet Organised Crime Threat Assessment (IOCTA) report stated, “Social engineering and phishing remain a key threat,” and that “both demonstrate a significant increase in volume and sophistication.”4 Yet, while the organized cybercriminal element are indeed becoming far more skilled in their use of social engineering, using multi-vector attacks and intercepting SMS tokens, phishing has dramatically increased due to the ease with which it can be conducted. Phishing kits and Phishing-as-a-Service, not to mention the ease with which personal data can be obtained, all mean that virtually anyone can start a phishing campaign with very little prior knowledge. Since likelihood is a factor in calculating risk, we must assume that our risk of being phished is now greater than ever.
Non-cash payment fraud, such as credit card theft, skimming, or phishing, is commonly used to enable the majority of other cyber-dependent crime, such as extortion, theft of data, and deployment of malware. Advanced persistent threat (APT) groups have long been known to conduct active cyber espionage campaigns. Social engineering of APTs' victims via email and social media phishing campaigns is commonly the first step in the attack chain. In September 2020, a new campaign by the Iranian-linked Charming Kitten APT combined targeted spear-phishing via WhatsApp with bogus LinkedIn profiles in order to create believable back stories. Their aim was to trick the victim into downloading malware or harvest the victim’s credentials.5
Business email compromise (BEC)—spear-phishing that targets staff members who have access and the authority to transfer money—is on the rise as attackers show an increased understanding of internal business relationships and processes. The second-quarter 2020 report from the Anti-Phishing Working Group (APWG) showed that the average wire transfer attempt was more than $80,000, with one specific threat actor targeting companies for an average of $1.27 million.6
Despite many advanced tools, techniques, and procedures (TTPs), many phishing attacks are simple in nature and succeed because of poor security controls and lack of awareness by users.
How Cybercriminals Capitalized on COVID-19 in 2020
Always keen to hook onto emotive topics, cybercriminals were quick to capitalize on the global outbreak of SARS-CoV-2, colloquially known as Coronavirus or COVID-19. While millions of people struggled to learn the real facts about the pandemic from world leaders, the morally absent cybercriminal community saw their opportunity. Phishing emails began hitting inboxes around mid-March with subject lines such as “Covid-19 in your area?” and “Message from the World Health Organization.”
The APWG reported that targets were predominantly “workers, healthcare facilities and the recently unemployed.”7 Figures 2 and 3 show just two samples of many pandemic-related phishing emails F5 Labs has seen.
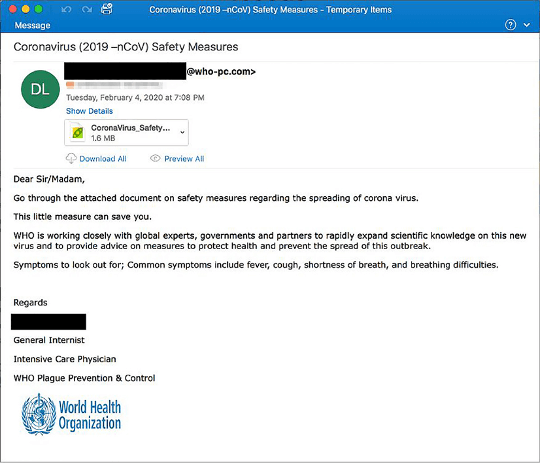
Figure 2. A phishing email that used fear of the pandemic to hook its victims
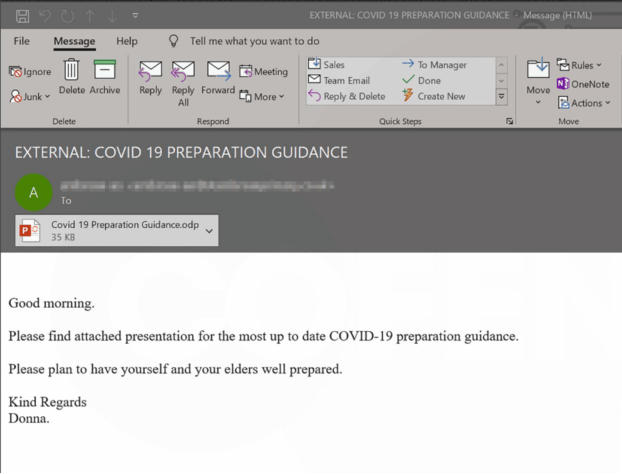
Figure 3. Another COVID-19 related phishing email with malicious presentation attached
Three primary objectives for COVID-19 related phishing emails became apparent. Fraudsters focused their efforts on:
- Asking for donations to fake charities
- Credential harvesting
- Malware delivery
While criminals seized on the opportunity to spoof login and download pages for increasingly popular web conferencing apps, such as Zoom, Skype, and WebEx, it’s remarkable how unremarkable many of these attacks really were. Europol’s IOCTA 2020 report summarizes this well stating, “COVID-19 demonstrated how cybercrime—at its core—remains largely the same but criminals change the narrative.”8 This echoes the previous discovery by F5 Labs of a Mirai botnet lazily cloned to include references to COVID-19.
The number of phishing incidents reported to the UK ICO for each quarter of 2019 and 2020 averaged 289, while new figures, released for the months covering April to June 2020, show a sharp decline with only 185 confirmed cases. The F5 Security Operations Center (SOC) saw a similar trend, with initial phishing statistics broadly following patterns of previous years but with a large spike around the start of 2020, a slump between March and April, and another significant rise over the spring and early summer months (see Figure 4).
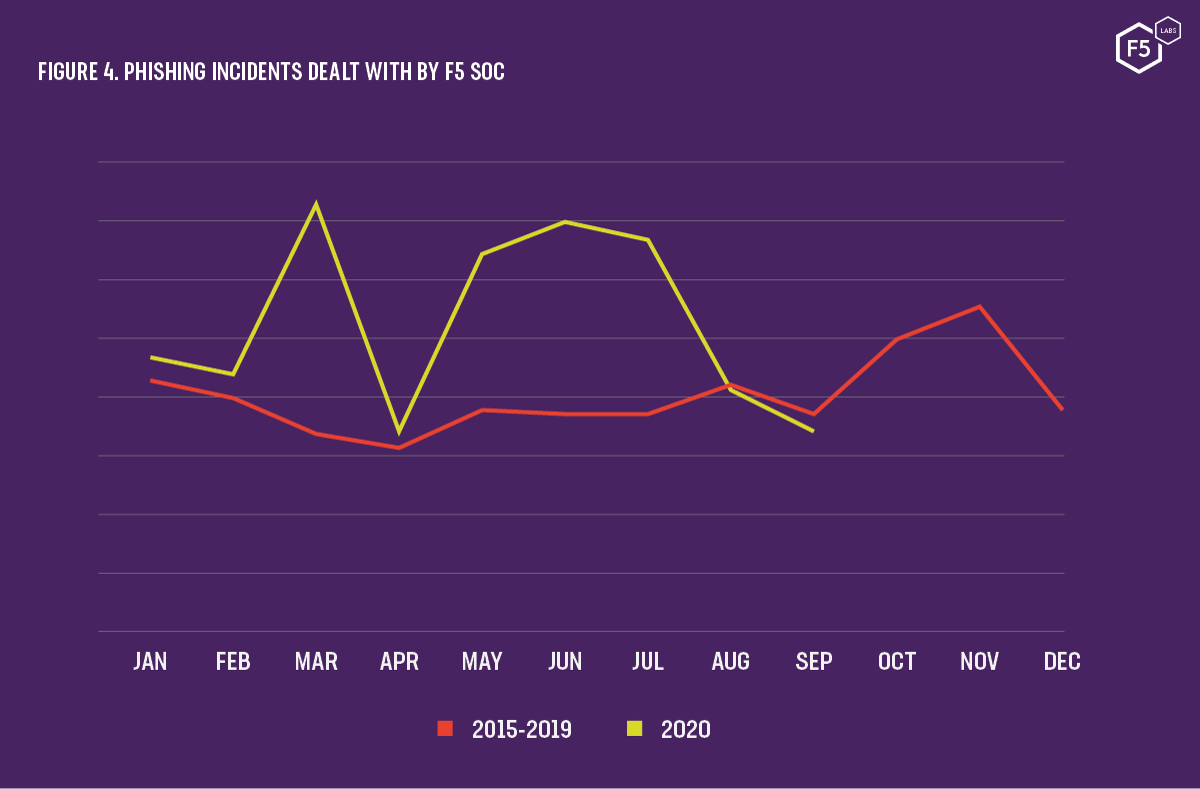
Figure 4. Phishing incidents dealt with by F5 SOC
Across the SOC datasets for the months of July to September, we found 320 unique malicious domains making use of the specific terms “covid” or “corona” in their URLs. Many other malicious sites used deliberate misspellings or simply used unrelated domain names for their attacks.
Using certificate transparency logs, we can also search for specific words or values within HTTPS certificates. It is no surprise that when the pandemic was headlining every news outlet in March, the number of certificates created that month with the words “covid” or “corona” peaked at 14,940 (see Figure 5).
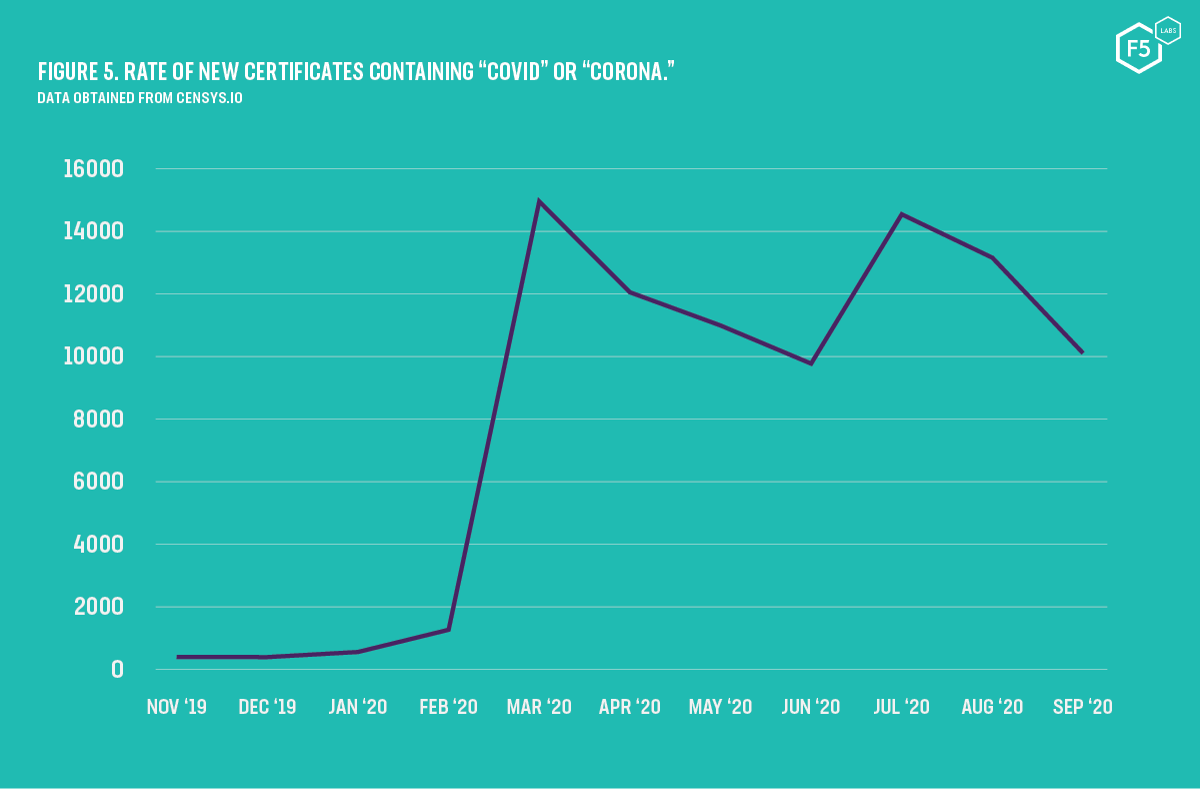
Figure 5. Rate of new certificates containing "COVID" or "CORONA."
Security practitioners are generally well aware of how phishers bait and hook their victims by using provocative topics, but if these trends tell us anything, it’s that end users—our staff and our customers—need to know this. Phishing awareness training must drive home the message that attackers are quick to jump onto new trends. Users need to be extra vigilant watching for email, voicemails, and text messages that appear to be related to widely discussed topics in the media or popular culture.
The Business of Phishing
There are many ways to phish, and the tools and tactics required are often determined by what the attacker is aiming to catch. As we covered in F5 Labs’ 2019 Phishing and Fraud Report, the three broad methods of phishing are:
- General, indiscriminate, in which the attacker targets many unrelated victims knowing that they are likely to get a few bites
- Semi-targeted, in which attacks are focused against a specific organization or group
- Spear phishing, in which a specific individual (often C-level or IT administrator) is directly targeted.
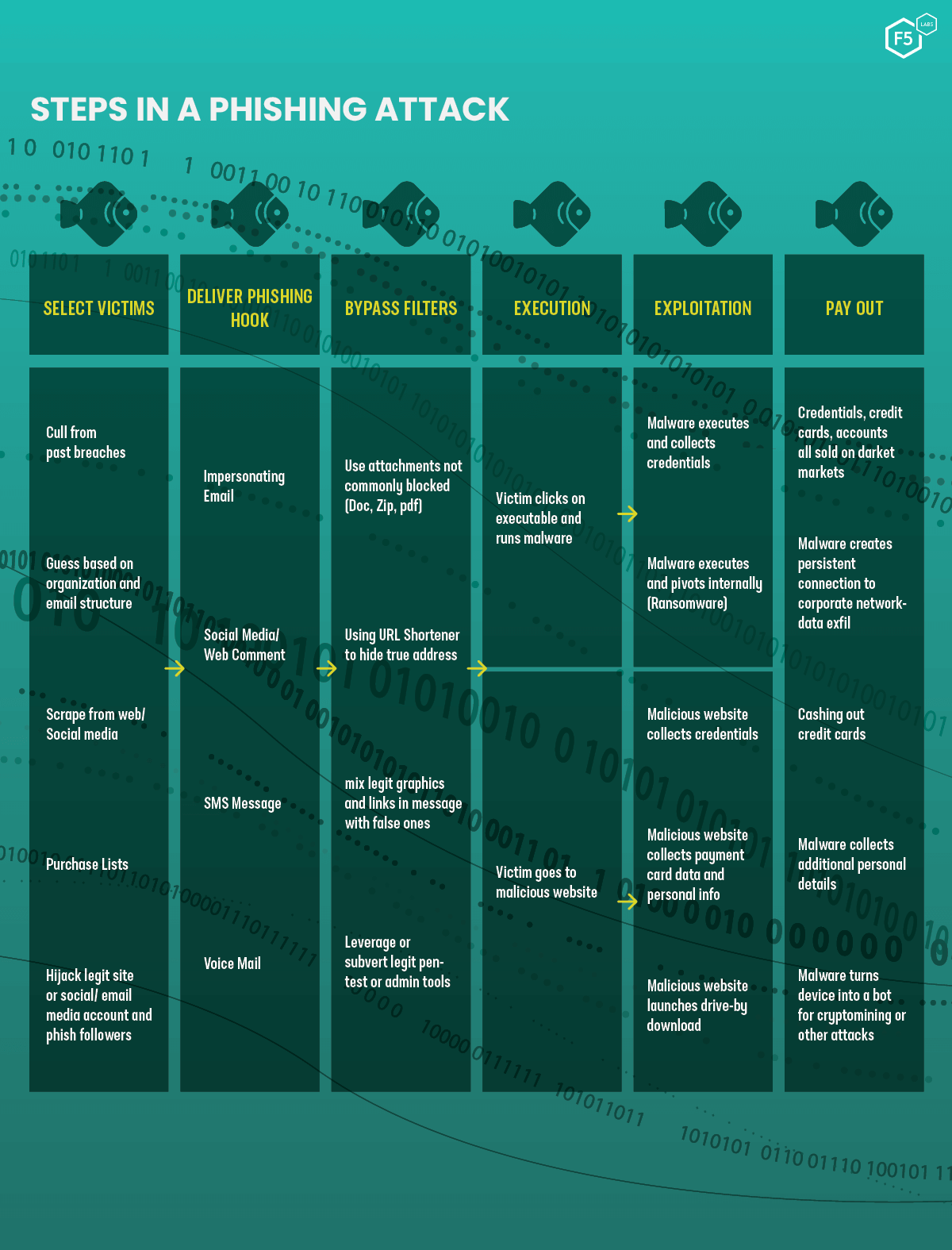
Steps in a phishing attack
While the catch (the pay-out) might be different between phishing campaigns (some attackers are looking to harvest credentials while others want to distribute malware), the commonality is that fraudsters use one or more social engineering tactics to circumvent a victim’s critical thinking. In a 2013 paper, A Study of Social Engineering in Online Frauds, the authors found the five most common methods of persuasion used were authority, urgency, fear/threat, politeness, and formality.9 In 100% of the phishing emails they examined, the cybercriminal used authority, and 71% of phishing emails added a sense of urgency. Whether it be a missed package delivery, a deadline for a competition, or threat of imminent “legal action,” fraudsters know that persuading us to rush increases the likelihood that we will not logically evaluate the request. This year we’ve very much seen this to hold true with the huge jump in phishing traffic around the periods of national pandemic lockdowns and many examples of emails claiming to have information about the virus.
Phishing Objectives
Social engineering, and primarily phishing, is often used as an enabler of both newer cyber-dependent crime (for example, ransomware and website compromise) as well as cyber-enabled crime (such as fraud and theft). Here, we focus on two of the most common objectives for fraudsters: credential harvesting and financial fraud.
Credential Harvesting
Usernames, email addresses, and passwords can often be the actual target of the fraudster, with stolen credentials commonly selling in bulk on darknet markets. These data sets of stolen credentials are purchased by other organized crime groups to enable others to carry out activities such as credential stuffing attacks.
More often, however, credentials are used to accomplish further objectives such as the theft of intellectual property or committing financial fraud. Attackers rarely have a problem obtaining usable credentials. Shape Security’s 2018 Credential Spill Report found that 2.3 billion credentials were breached in 2017.10 And 2017 was, according to Wikipedia, a quiet year for data breaches.11 12Figure 6 shows the number of data breach incidents per year compared with the cumulative number of records breached. Despite a fluctuating number of incidents from year to year, the total number of records lost or stolen appears to be growing exponentially.
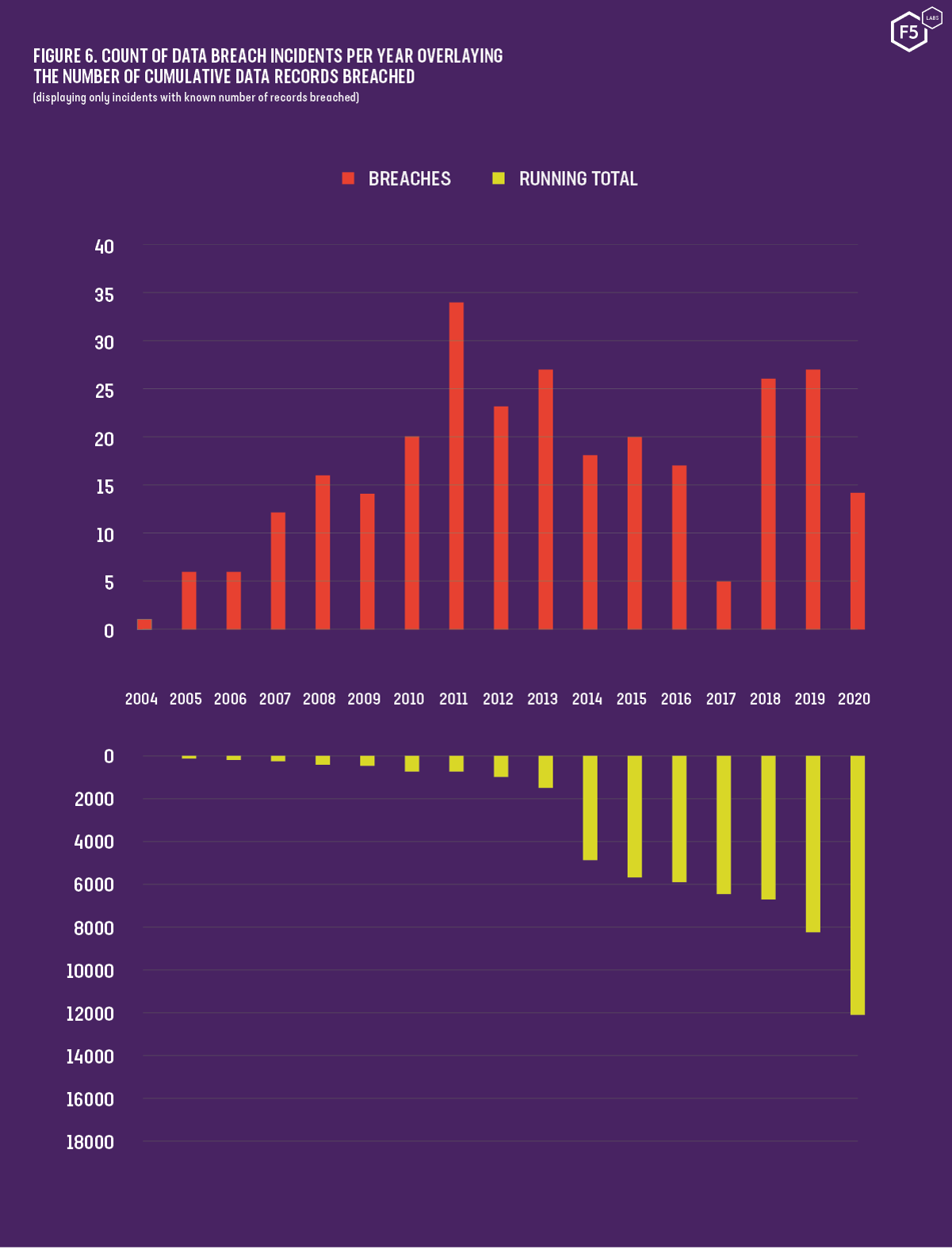
Figure 6. Count of data breach incidents per year overlaying the number of cumulative data records breached
Office 365 Provides a Rich Target
Microsoft’s incredibly popular email, productivity, and collaboration platform, Office 365, is a prime target for attackers. Once credentials have been captured, attackers have a multitude of options open to them. They might choose to send more fraudulent emails, now with the benefit of having them appear to come from a genuine corporate account. This same Office 365 account is likely to have access to SharePoint and OneDrive, which could provide direct access to intellectual property and sensitive data. The worst-case scenario might involve the compromised account being a member of a privileged access group, which then grants the attacker the ability to modify access privileges for the Office 365 platform itself.
A common tactic to phish for Office 365 credentials is to send a victim an email claiming that a Word or Excel document has been shared with them. To retrieve it, the victim must authenticate to the (spoofed) Office 365 website.
Consent Phishing
Now that businesses are starting to better secure their credentials (by federating user accounts, performing device posture checks, and applying MFA), fraudsters are beginning to shift their targets. With credentials becoming harder to steal, fraudsters are asking the victim for direct access to their account in an attack called consent phishing.
There are hundreds of mobile and desktops apps that promise to tidy your inbox, organize your contacts, or provide some incredibly useful new productivity feature. To use one of these apps, all you have to do is download it to your phone or laptop and authorize it to connect to your Gmail or Office 365 account.
The process for authorizing apps to your email or productivity platform is as follows:
- Tell your new app of choice what platform you use, for example, Office 365
- Your app then directs you to a login page for your Microsoft account
- You authenticate to Microsoft by entering your credentials
- Finally, you see a page, such as the one shown in Figure 7, in which you accept the permissions being requested by the app
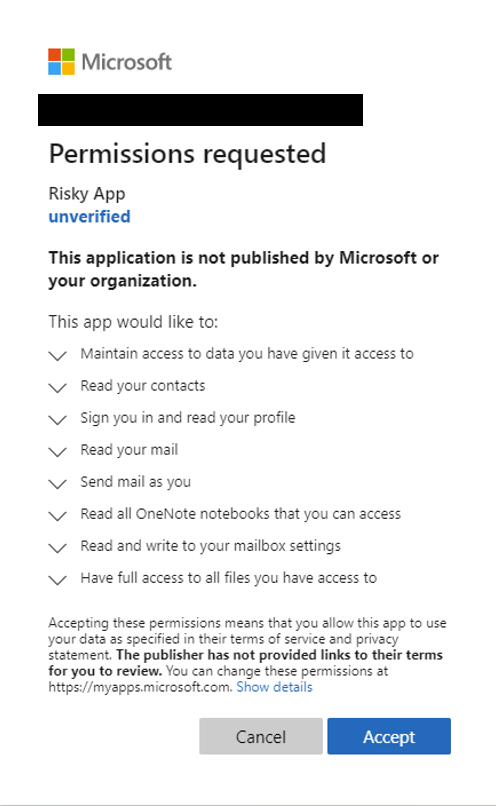
Figure 7. Granting an app permission to access your Microsoft account. Image credit: Microsoft
You might assume you’ve handed your credentials to your newly downloaded app. You haven’t. Instead, you’ve told Microsoft to hand the app a special token that grants it (often) indefinite and (commonly) unlimited access to your email as well as your entire Office 365 or Google account. Not surprisingly, criminals are abusing this to gain fraudulent access to Office 365 and Gmail accounts. Fraudsters correctly assume that many everyday users of these platforms don’t fully read the permissions or, very likely, have no idea what they really mean and, since so many people now use these platforms, their net can be cast far and wide.
Financial Fraud
Generic phishing campaigns often ask victims to hand over cash in order to claim a prize or to donate money to a charity. Often these scams trick visitors into making a one-time donation to a non-existent charity or getting them to sign up for regular direct debits. Semi-targeted phishing attacks, however, will go after customers of a specific bank or service and aim to steal their payment card details for later use. These campaigns frequently ask victims for payment card details as well as logon credentials. Not only can the card details help authenticate the criminal to the victims’ online accounts, they can also be resold on dark web markets.
Using information supplied by threat intelligence firm Vigilante, we analyzed stolen payment card details found over the past four years. The data represents over 44,000 debit and credit cards supplied by seven of the world’s largest banks, some with headquarters in America, UK, Singapore, Hong Kong, and Australia. We compared the dates on which these stolen cards were discovered with their expiration dates and other associated personal information.
Looking at a near four-year average, from late 2016 through mid-2020, almost half of all cards, 42%, were found to be in-date at the time of discovery. An impressive 98% of cards had some personal data associated with them. In most cases, this included names and addresses, but some also contained phone numbers and email addresses.
Since 2016, 98% of stolen payment cards had some personal data associated with them
Thankfully, across the seven multinational banks we analyzed, we have found that these numbers have been declining. At the peak in 2016, 97.2% of all cards had full names associated with them. In 2020 this number has dropped to 84.9%. Likewise, card validity has also fallen. At its worst in 2017, 76% of cards were in date at the time of discovery. This had dropped to just 32.8% in 2020.
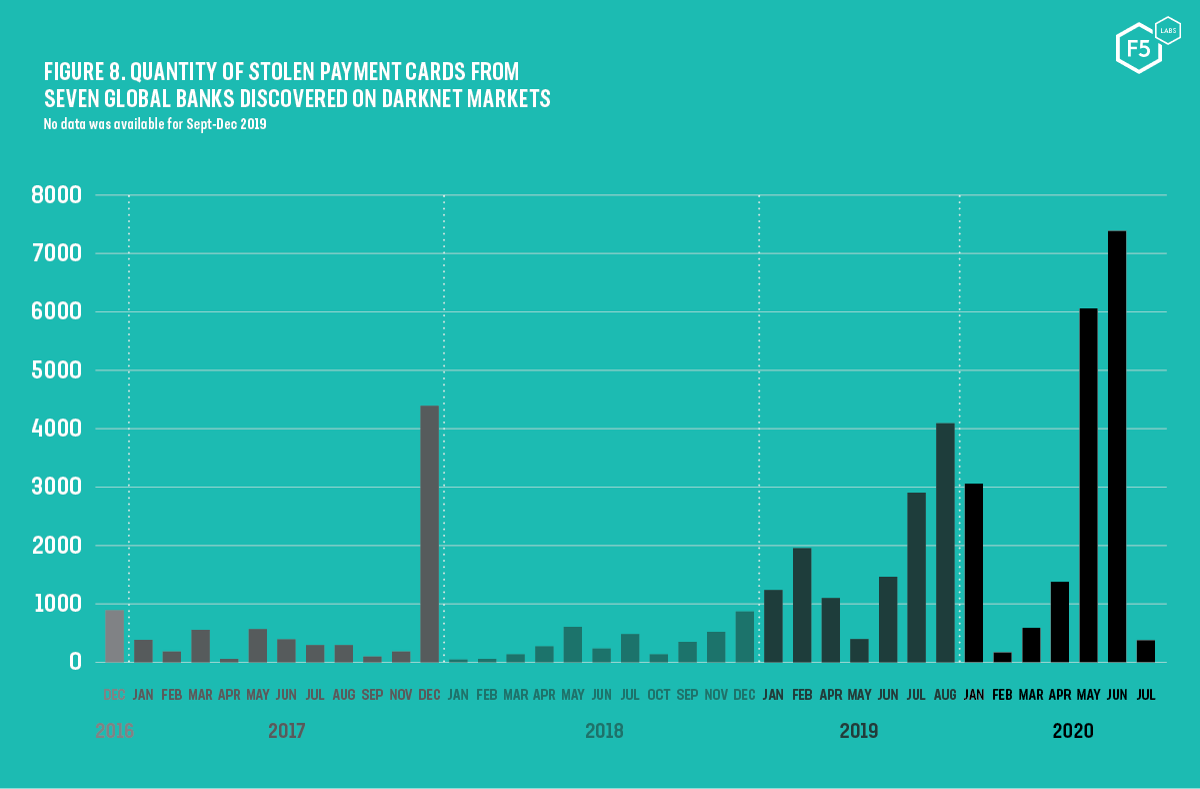
Figure 8. Quantity of stolen payment cards from seven global banks discovered on darknet markets
Physical card skimming is still commonplace within the organized crime world, but this process typically only captures a victim’s card number. Payment card data with associated personal information is significantly more valuable to the cybercriminal. Having access to a victim’s name, physical address, and email address allows the criminal to create fraudulent accounts in the victim’s name. Additionally, physical addresses allow them to pay for goods using the correct billing address while sending goods to a different location.
The large amount of personal data associated with payment card numbers points to several possible sources:
- Breached databases storing payment card details
- Formjacking (a form of cyber card skimming)
- Simple scams asking users to enter payment details to claim a prize
- Phishing pages designed to imitate real banking websites
Cybercriminals are quick to act. They understand that once they have tricked the victim into handing over their payment card details or banking credentials, the quicker they act the more likely they are to successfully steal the victim’s money. Shape Security, now part of F5, frequently investigates phishing sites that imitate real banking login pages. By tracking the known payment card details entered into the phishing site and detecting when an attempt was made to use that card, we were able to build a complete picture of the phishing campaign. The average time between a victim entering payment card details into a phishing site and a cybercriminal fraudulently using those credentials was just four hours. In many cases, a repeated login was attempted another seven hours later.
4 HOURS
the average time between a victim entering payment card details into a phishing site and a cybercriminal fraudulently using those credentials in an attack
Modern Phishing Practices
Phishing is slowly evolving. While there is rarely a radical shift in how phishing attacks are carried out, fraudsters are certainly adapting to security controls and improving their level of sophistication. In this section we look at how attackers build and host their phishing sites and what methods they use to avoid detection.
Building a Phishing Site
Cybercriminals have a number of ways to build their phishing sites. Although creating a fake site completely from scratch is possible, it is rarely worth the phisher’s time. Instead, they use one of two methods: clone the real site or purchase a phishing kit.
Cloning a Site
Cloning a real webpage can be a simple three-step process:
- Visit the genuine website
- Right-click and select Save Page As…
- Take the HTML, CSS, and images just saved and host them on a rented server
While these steps are somewhat over-simplified, the principle is entirely valid. The F5 SOC is often involved in phishing site takedowns in which the malicious site was a simple clone of the genuine one. The benefit of site cloning is that the phisher captures all the elements of the real web page, including CSS and images. They need only alter a few components of the site, such as where the credentials are sent, and they’re good to go.
Figure 9 compares the source code from a phishing campaign spotted in August 2020. The code on the left shows the legitimate UK Government website HTML and the code from the malicious site is shown on the right. Only small changes have been made to the code; it uses as much of the original source as possible.
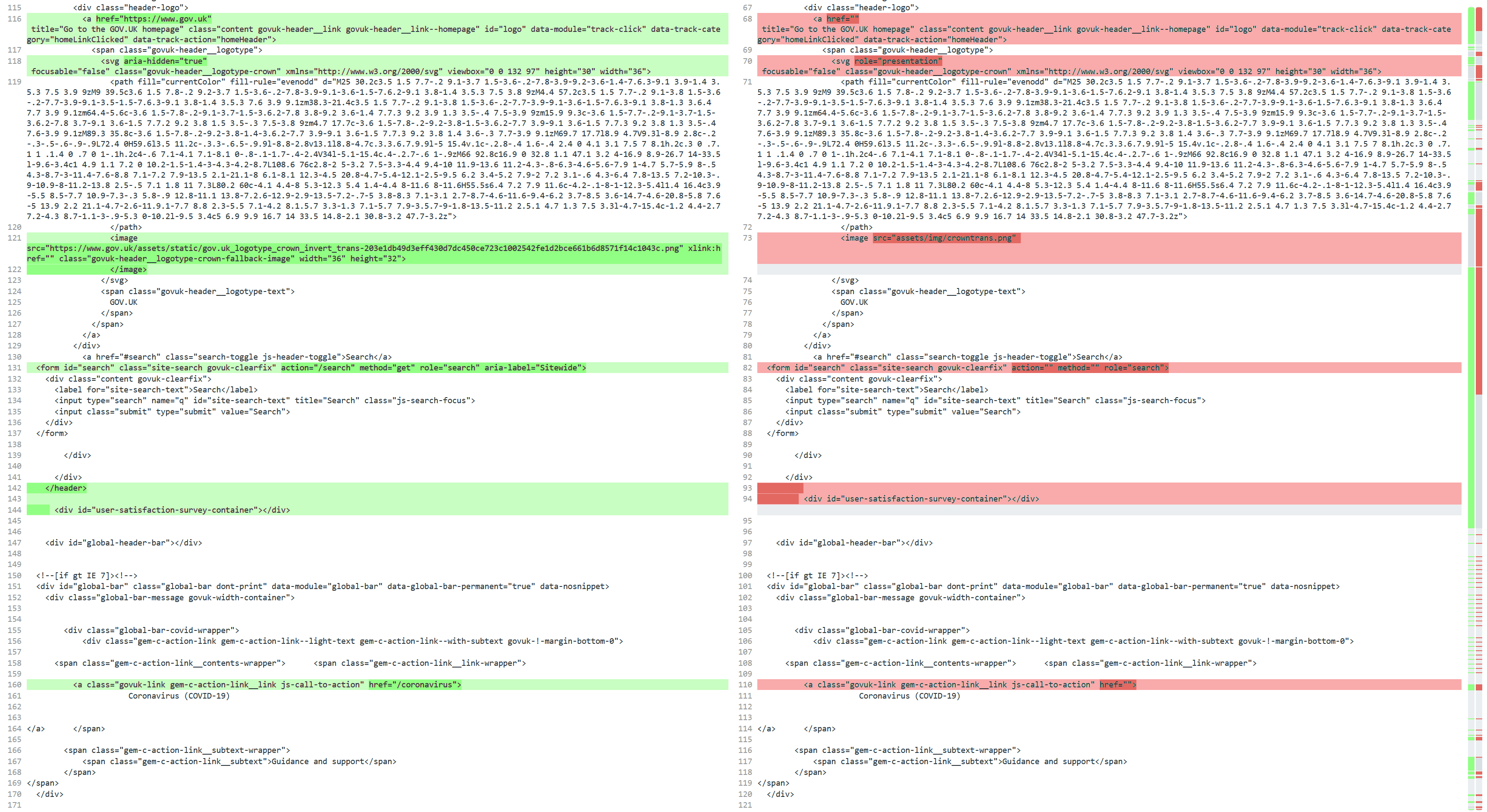
Figure 9. Comparison of legitimate UK Government site (left) and spoofed site (right)
Phishing Kits
The alternative—and arguably an even easier method than cloning a site—is to acquire a phishing kit. These are turnkey phishing solutions that come packaged with all the HTML, images, and code needed to create a fraudulent site (see Figure 10).
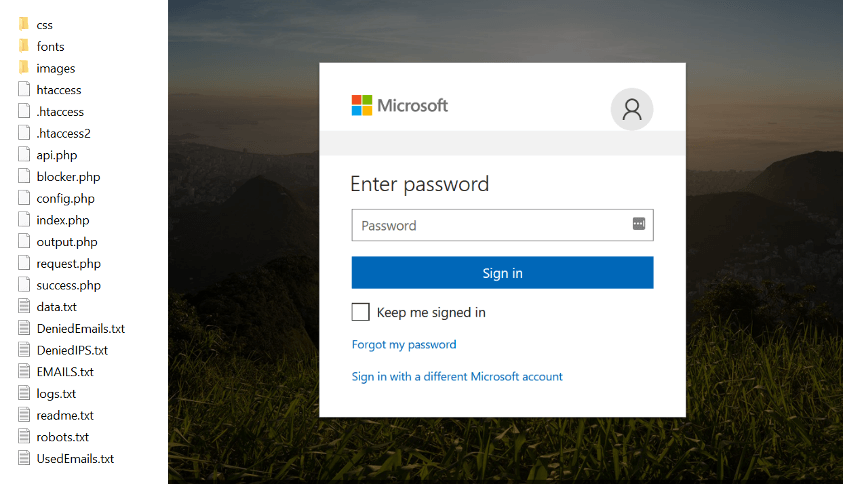
Figure 10. Left: The components of a phishing kit. Right: How the phishing site appears to visitors.
Kits are developed to target a specific organization or brand. For example, kits for logistics firm DHL attempt to trick victims into paying a fee to deliver their (non-existent) parcels. Banking kits are designed to steal credentials, payment card details, and answers to security questions. One of the most popular targets for generic phishing is the Microsoft Office 365 logon page. The productivity and collaboration platform enjoys widespread global usage with many businesses often moving their entire back office systems onto the platform. Attackers know that stealing Office 365 credentials can grant them access not only to email but also corporate documents, finance, HR, and many other critical business functions.
Phishing kits vary in complexity, but the more advanced ones require an active license from the author and employ numerous tricks to avoid detection by researchers and casual observers. One such recent example is the OfficeV4 kit, which, not surprisingly, targets users of Office 365.
OfficeV4 fraudsters must have an active license in order to use the kit. Figure 11 shows a portion of the configuration file, which is dynamically included in every page of the kit, meaning that every page load requires a lookup for an active license.
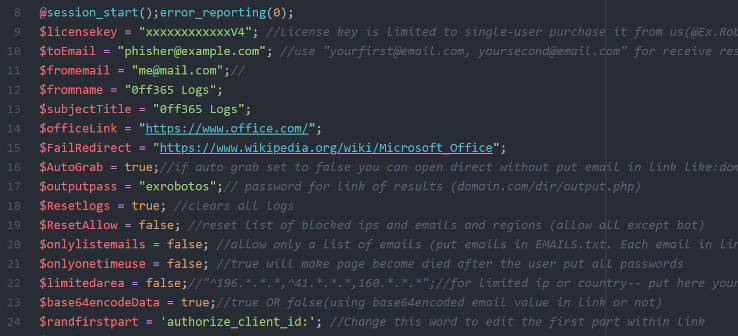
Figure 11. The configuration file for the 'OfficeV4' phishing kit, which requires users to enter their license key
Phishing kit
Stealth and Evasion
Where and how phishers decide to host their fraudulent site will depend on how frugal they are and what they want their website address to look like. While some attackers leech off a vulnerable website, many choose to register their own domain names. Fraudsters are also keen to avoid detection by security researchers, so they employ a number of techniques in an attempt to remain hidden.
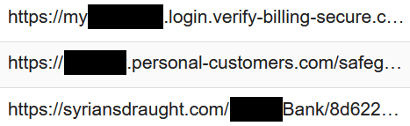
Figure 12. Attackers use target names in the domain or path of the URL (Source: F5 SOC)
Spoofing Brands by Using Similar URLs
Attackers use a combination of tactics to make their phishing URLs appear genuine. From making use of target brands in the domain to the implementing genuine HTTPS certificates, their goal is to minimize the risk of victims being suspicious about the site they are visiting.
Using Custom Domain Names
In targeted campaigns attackers often include the name of the target organization somewhere in the URL. Analyzing the fraudulent domain names of phishing sites detected by the F5 SOC shows that, in 2020, 52% of malicious links contain the brand name either in the domain name or the path.
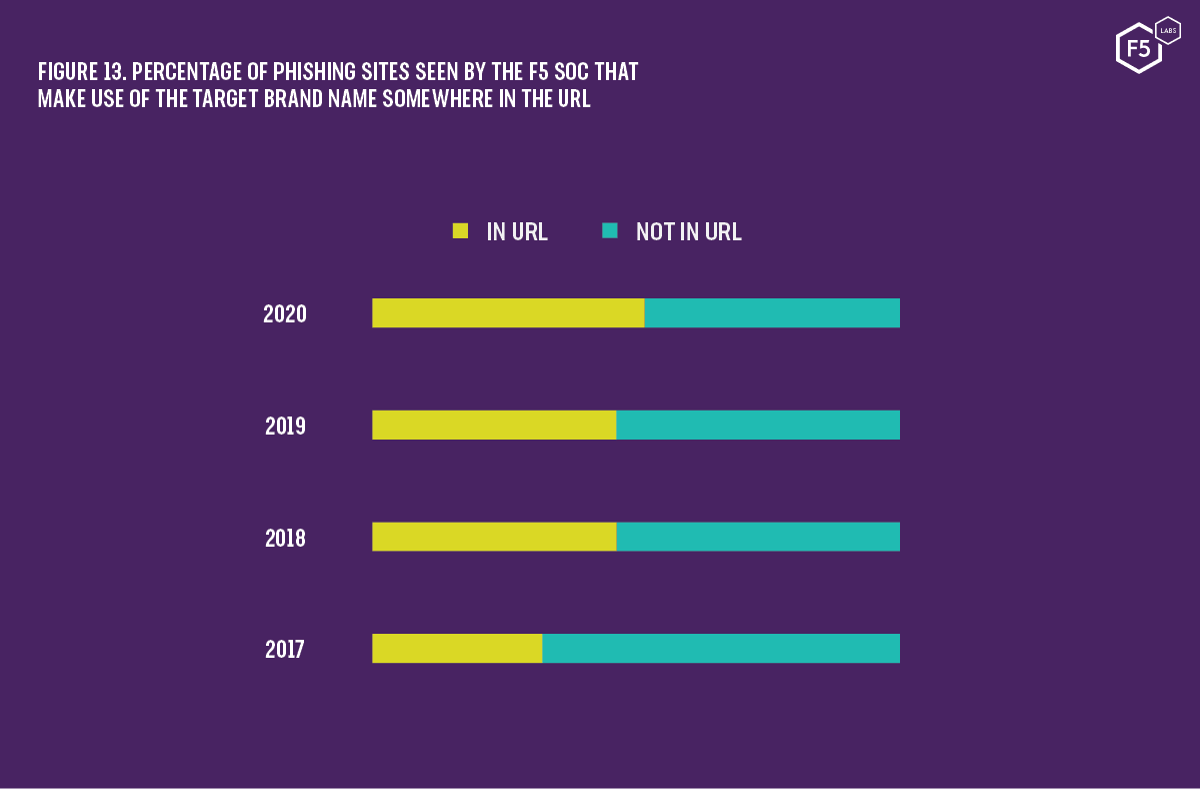
Figure 13. Percentage of phishing sties seen by the F5 SOC that make use of the target brand name somewhere in the URL
Attackers often choose a subdomain that makes use of the target name. Victims—not paying close attention or simply unaware of the rules that govern the web and how URLs function—will see a genuine looking part of the domain name and may assume it is an authentic site (see Figure 12).
Some browser vendors, aware that this is now a common practice, attempt to highlight the true domain, but there is much inconsistency among them. Google’s Chrome browser, for example, shades the path of the website in gray and highlights both the domain name and also any subdomain (Figure 14).
Firefox, however, recognizing that phishers often use subdomains to trick their victims, grays all parts of the URL, apart from the base domain (Figure 15).
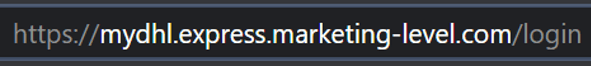
Figure 14. Chrome highlighting the full domain of a phishing site
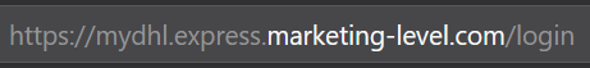
Figure 15. Firefox highlighting only the base domain of the URL
Is domain highlighting a big enough move, however? We found that almost 30% of phishing sites made use of the target brand in the domain portion of the URL while only 25% used that brand name in the path only.
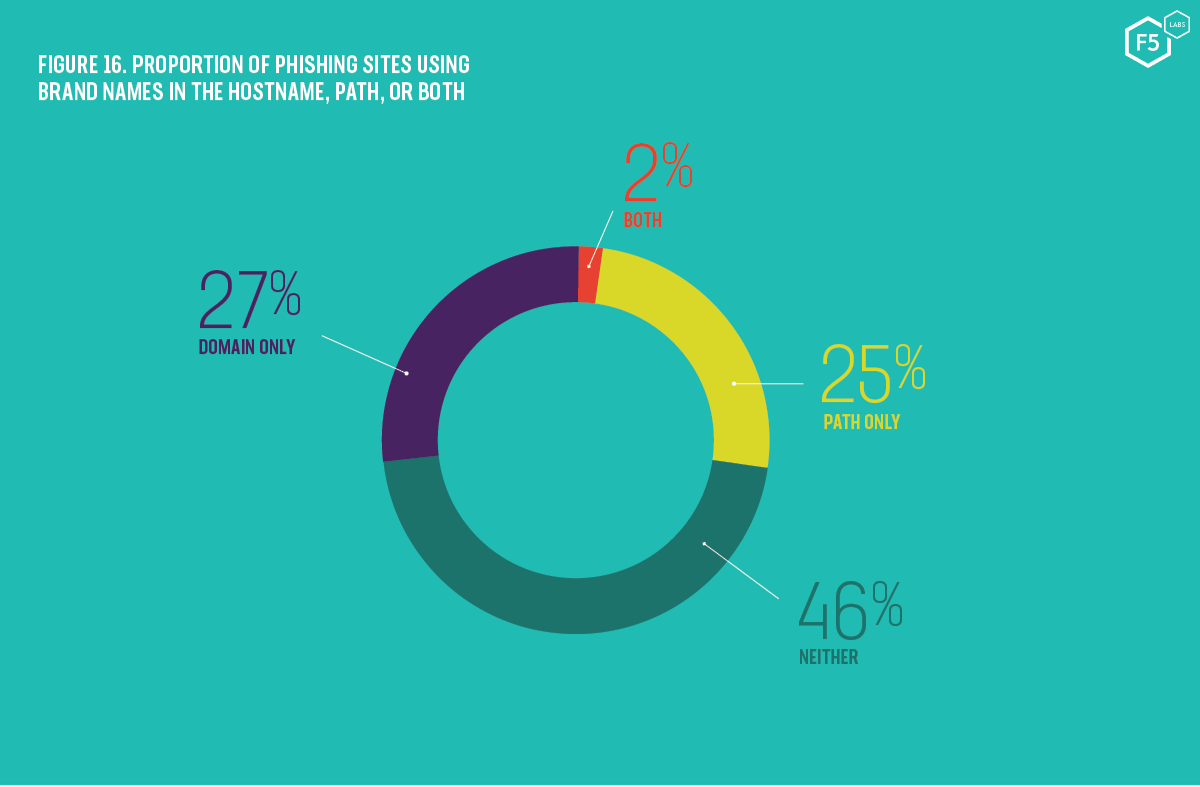
Figure 16. Proportion of phishing sites using brand names in the hostname, path or both
In addition to creating genuine looking URLs, fraudsters often create subdomains so long that the true base domain is hidden from view off the end of the address bar. Despite graying the subdomain, all the victim can see is the start of the address, which includes some authentic looking words such as ssl, encryption, and security.

Figure 17. Phishing site URL making use of deception techniques to hide the true address
In an attempt to fully address this, the Chrome browser is now testing a feature to auto-hide the path of a website until a user clicks in the address bar (see Figure 18). This is similar to way that Apple’s Safari browser displays URLs (so long as the “Show full website address” option is unchecked). For the majority of web users who know or care little about the difference between domains, subdomains, paths, and query strings, this is a positive move. It allows them to focus their attention on the full domain of the site they are visiting.

Figure 18. Chrome 86 is testing a feature to automatically hide website paths until they are needed
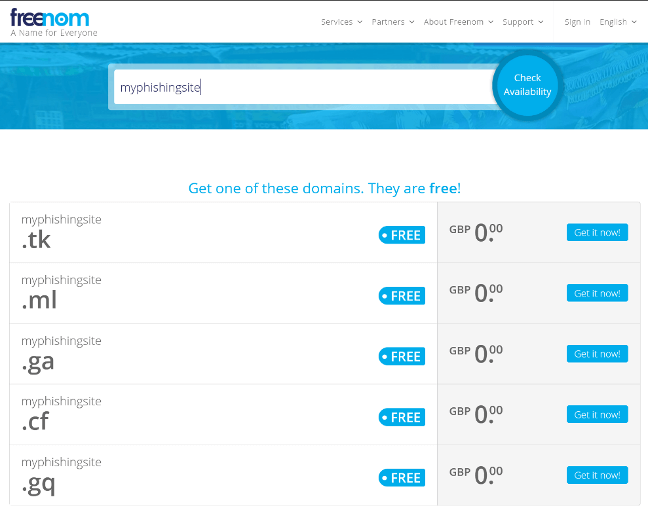
Figure 19. Freenom is the registrar in charge of .tk country code TLDs and offers them for free
Abusing Free Top-Level Domains
Registering a domain such as myphishingdomain.com (or something slightly less obvious, such as secure-site-login.com) brings with it a cost charged by the registrar. This can range from a few dollars a year to many thousands of dollars if the domain name contains popular or trademarked keywords. However, we are now seeing increased use of free registrars (such as Freenom) for certain country code top-level domains (ccTLDs) such as .tk, .ml, .ga, .cf, and .gq (see Figure 19).
This allows both legitimate and fraudulent users to register domains entirely for free, once again lowering the financial cost to the attacker. In fact, these free domains have become so popular that .tk is now the fifth most popular TLD by number of registered domains (see Figure 20).13
The F5 SOC has observed numerous campaigns in which a crime group created almost 1,000 custom domains that all contained short strings followed by the suffix “-71”. The same domain was registered for each of the free TLDs, as shown in Figure 22.
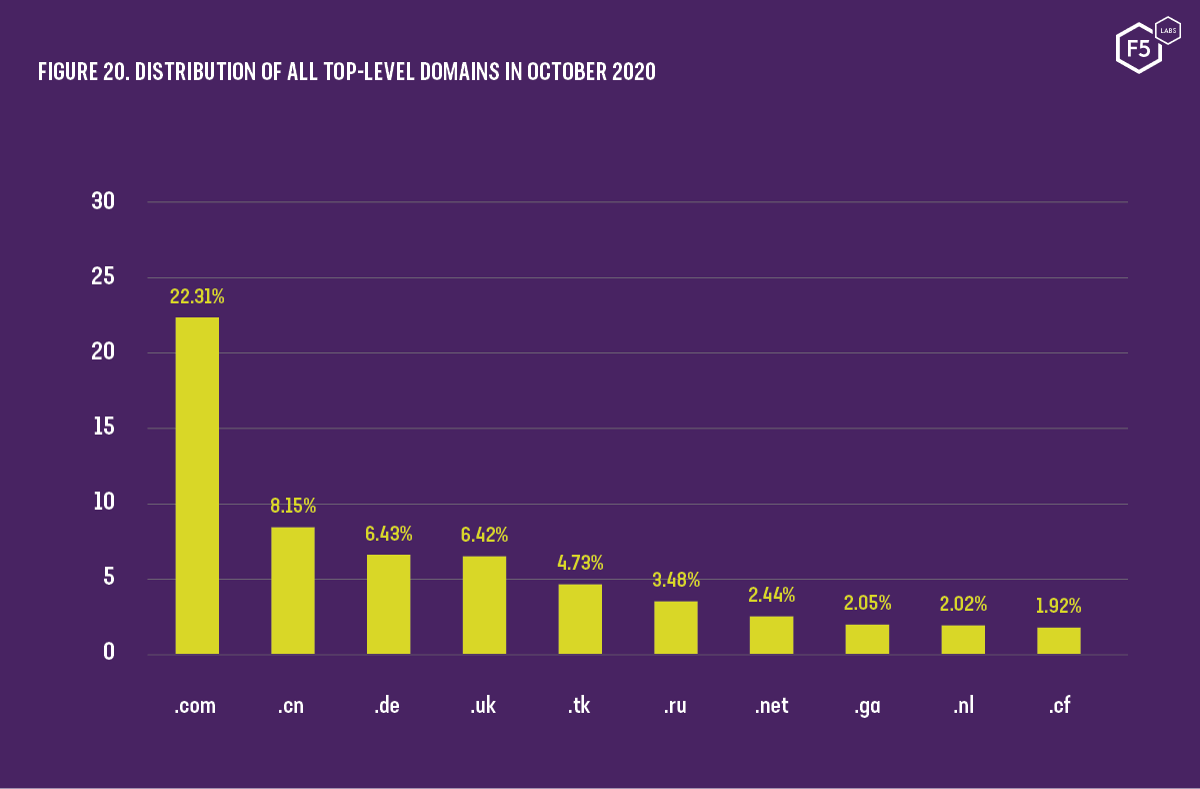
Figure 20. Distribution of all top-level domains in October 2020
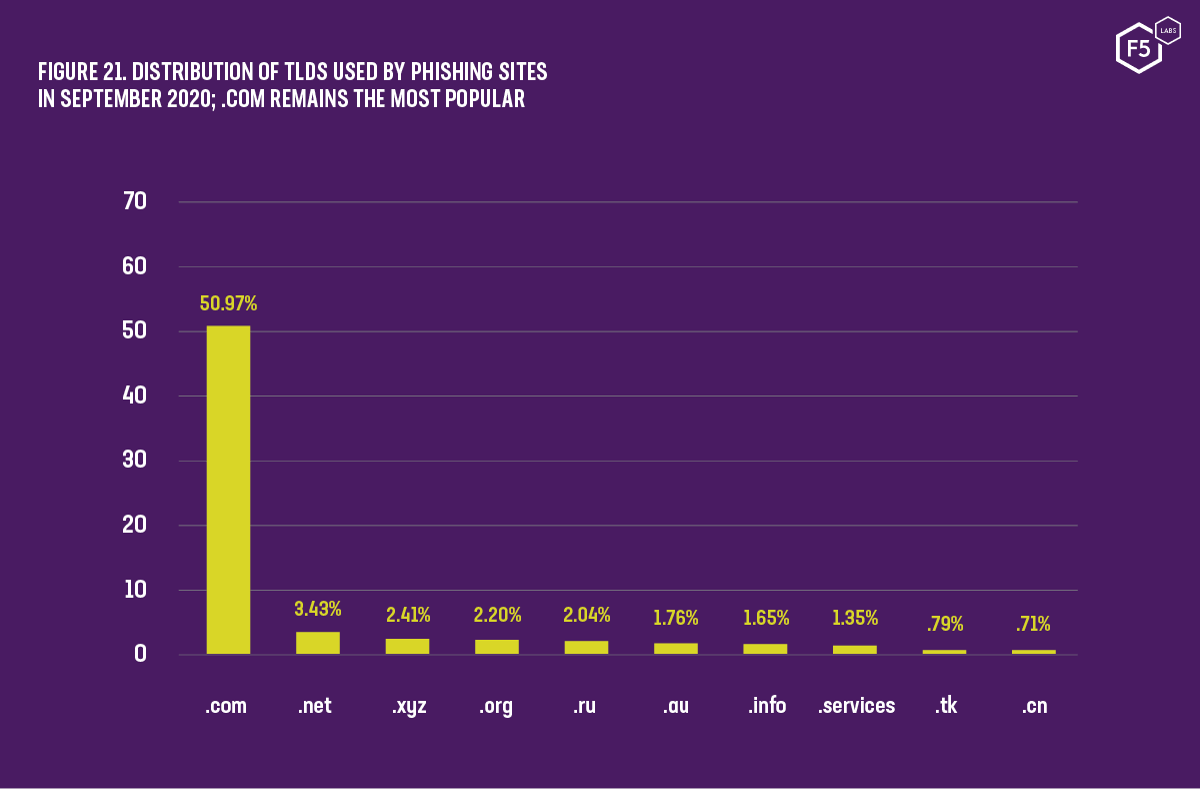
Figure 21. Distribution of TLDS used by phishing sites in September 2020; .com remains the most popular
These nearly 1,000 domains resolved to just under thirty IP addresses that were hosted on various public clouds, predominantly Alibaba, Amazon AWS, and Microsoft Azure. These IP addresses also hosted many other non-malicious websites. It’s likely that the short length and numbering of these domains made it simple for the attackers to identify and automate the deployment of malicious sites through the use of scripts that called out to web shells, instead of managing them via cloud-native tools that differ among the providers.
Despite the growing use of free top-level domains, the ubiquitous .com TLD remains a clear favorite for phishers. While global TLD statistics show overall use of .com at just over 22% (see Figure 20), the average value we see from our combined datasets show phishing sites using .com at over 50% (see Figure 21).
Phishers are also getting creative and having fun with their domain names. Punycode, the ASCII translation of domain names using non-English character sets, has long been popular with phishers looking to trick their victims. One of the malicious domains found in our dataset this year, for example, was shop.dev.xn--blockchin-c2d.com which, when displayed in Punycode, displays as shop.dev.blockchɑin.com in the browser address bar. This is known as an IDN homograph attack, and virtually all modern browsers mitigate it by displaying domains with mixed character sets entirely in ASCII, making the Punycode visible. For this reason, the number of phishing domains we see attempting to exploit this attack vector is low, only 0.25%.
While mixed character sets are generally not displayed in browsers, domains made up entirely of Punycode are indeed visible. Fraudsters have become playful with their domains, using emojis to give some indication of what might wait for the visitor if they follow the link (see Figure 23).
Once the domain name is registered, the phishing site needs to be placed onto a website. This year, like last, we saw extensive use of free and cheap cloud hosting services. Table 1 shows the most common web hosting platforms used by phishers and, for the second year running, 000webhostapp.com is the most popular.

Figure 22. A redacted sample of the nearly 1,000 malicious "-71" domains created by cybercriminals

Figure 23. Emoji-based domain names used by phishers
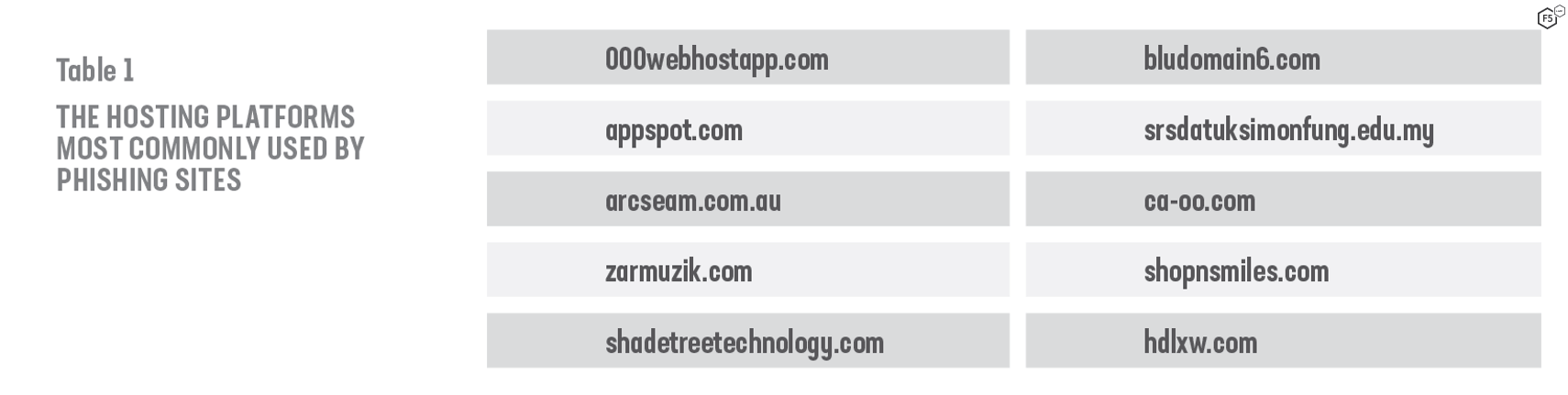
Table 1. The hosting platforms most commonly used by phishing sites
Figure 24. Free web hosting from 000webhostapp.com
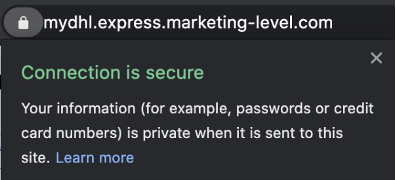
Figure 25. Phishing site making use of a valid certificate
With free hosting for small web sites, it is easy to understand why attackers are using these platforms (Figure 24).
Hiding in Plain Sight
Phishers use whatever means they have at their disposal to make their fraudulent site appear as genuine as possible. In today’s online world, using TLS certificates so that websites appear secure is a virtual necessity. Despite domain names that have nothing to do with brand the site is impersonating, unwitting victims often see the padlock and phrases such as “Connection is secure” and believe the site is trustworthy (see Figure 25).
F5 SOC statistics (see Figure 26) show that a rapidly growing number of phishing sites are using encryption. The majority, 71.2% of phishing links, make use of valid HTTPS certificates in order to present credible looking links to their victims. Corroborating our own data, we found that:
- Scans of phishing sites from Webroot BrightCloud Intelligence showed that 72% uses HTTPS
- The APWG’s recent Phishing Activity Trends report similarly found that 78% of phishing sites now use SSL/TLS, up from 75% at the start of the year16
Drop zones, destinations to which malware sends stolen data, make use of TLS encryption in 100% of incidents the F5 SOC investigated during 2020. Combining incidents from 2019 and 2020, we found that 55.3% of drop zones use a non-standard SSL/TLS port. In all but one of these cases, port 446 was used. Almost all phishing sites, 98.2%, used standard ports: 80 for cleartext HTTP traffic and 443 for encrypted SSL/TLS traffic. A non-trivial number of incidents, 1.5%, featured sites hosted port 32000.
72% of all phishing sites secure their site with SSL/TLS
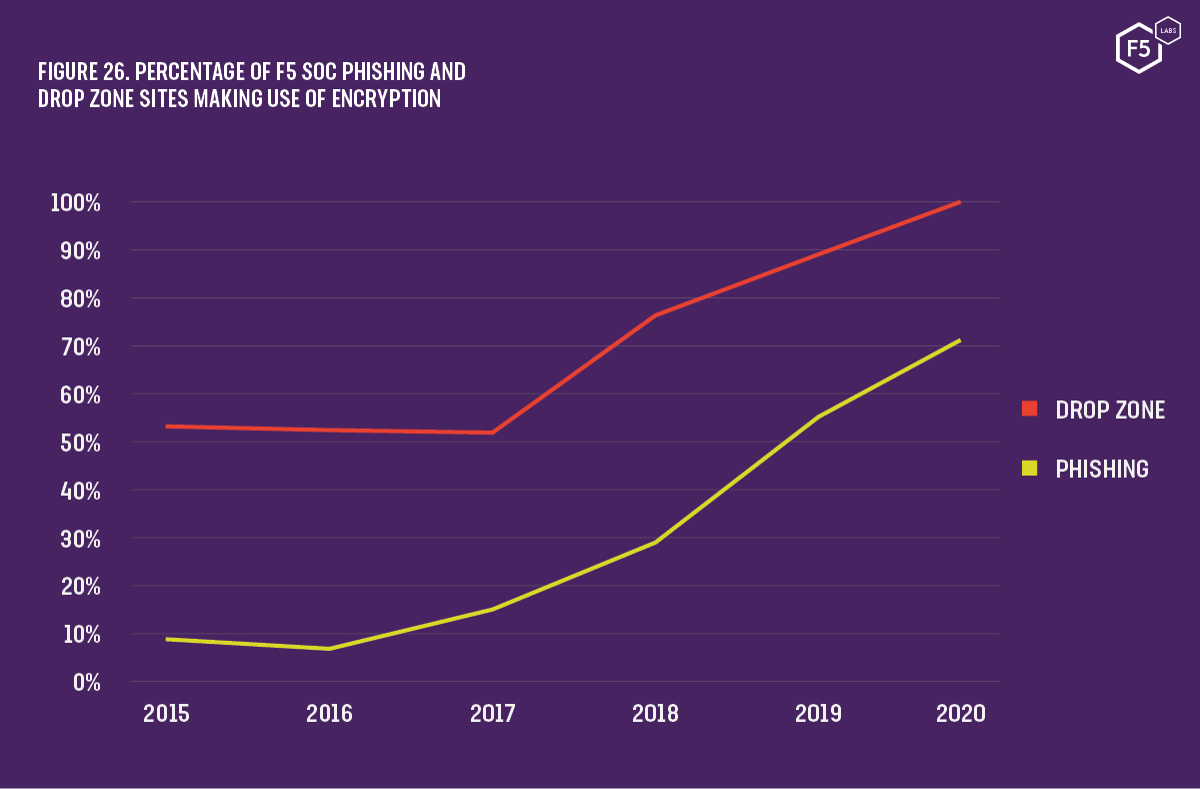
Figure 26. Percentage of F5 SOC phishing and drop zone sites making use of encryption
Compromising Vulnerable Websites
Newly registered domains can be detected and blocked by corporate web proxies. The more discerning phisher might, instead, choose to avoid the costs and worries of domain name registration altogether by exploiting a vulnerability in someone else’s website. By compromising a vulnerable website, they can not only host their phishing pages for free but also benefit from an existing and likely trusted domain name.
Across all our datasets, we found an average of almost 10% of all phishing incidents involved victims being sent to malicious pages built using WordPress. Examining data from the F5 SOC, we see that figure rise as high as 20% when we focus on phishing sites that do not make use of the target brand name anywhere in the URL. This suggests that vulnerable WordPress sites are being used opportunistically. Attackers recognize that they may not have such a strong hook (since they cannot customize the URL), but WordPress sites can represent a low-effort platform upon which to host their fraudulent pages. Exploitation of vulnerable websites appears to be trending up. Focusing on WordPress, we saw only 4.7% of phishing sites use the platform in 2017. This rose to 9% in 2018 and peaked in 2019 at just over 21%.
Vulnerable WordPress sites accounted for 20% of generic phishing links in 2020
Compromising Third Parties
A trend closely followed by F5 Labs has been one in which attackers are increasingly breaching third-party services in an effort to massively scale their attacks and bypass security controls. In the past few years, we saw huge formjacking (web card skimming) campaigns that stole personal information and payment card data. Many of these attacks, such as those by the Magecart threat groups, compromised and modified scripts hosted on third party websites. Anyone using those compromised scripts by dynamically linking to it in their code was immediately affected.
Similarly, in August 2020, a large email marketing service found that several of its users had their credentials stolen. Attackers were then using their accounts to send spam and phishing emails. Organizations that had previously added the email provider to an allowlist found that they were suddenly receiving hundreds of phishing emails despite their email filter initially marking it as suspect.
The lesson here is simple. Adding entries to an allowlist should only be used as a last resort and done with limited scope. Entire domains should rarely be allowed without inspection. Instead, create allowlists that are as restricted as possible and clearly document the business justification for doing so.
Evading Prying Eyes
Threat actors are keen to prevent curious victims or determined security researchers from investigating their fraudulent sites. To this end, they employ a number of methods to block anyone that might not be a genuine victim.
Blocking Security Researchers
A common tactic to hide from prying eyes is to perform geolocation of the IP address to identify which country the connection is coming from. Russian scammers, for example, commonly block IP addresses from their home country so that they do not draw the eyes of Russian law enforcement. For this same reason, Tor exit nodes are also prevented from viewing the real phishing site. Additionally, victim IP addresses are logged and, once visited, repeat visitors are blocked and either shown a benign page or redirected elsewhere on the web, such as to Wikipedia.
Phishing kits, such as ‘OfficeV4’ as described in the Phishing Kits section, uses the .htaccess web server configuration file to block access from certain locations. The OfficeV4 kit contained over 1,000 lines of IP ranges, headers, and referring domains, such as google.com and firefox.com. The code sharing website Pastebin has many sample .htaccess files with preconfigured IP ranges and domains that other phishers can use to get started.
Many phishing kits examine the user-agent header of the client browser. Researchers often use scripts or tools to view malicious websites. Phishing pages attempt to detect what tool or browser is requesting access by examining this header and will block everything other than standard web browsers, such as Chrome and Safari. Mobile phishing scams follow the same pattern by blocking access to any device that does not appear to be an Android or iOS phone.
Attackers know how and where their links were distributed. If the referer header is blank or comes from a site they were not expecting, there’s a good chance a security researcher is investigating the site and the connection is blocked.
Use Images Not Text
Security controls, such as web proxies, attempt to detect when a staff member is visiting a potential phishing site by examining the content of the incoming web page. By detecting the use of certain phrases, such as “failed login” or “password is incorrect,” a proxy can determine the risk a site poses. Knowing this, phishers avoid being detected by using images to display text whenever possible. Figure 27 shows images used by the OfficeV4 phishing kit. It uses PNG images to display text such as “Enter password” instead of using raw text within the HTML page itself.
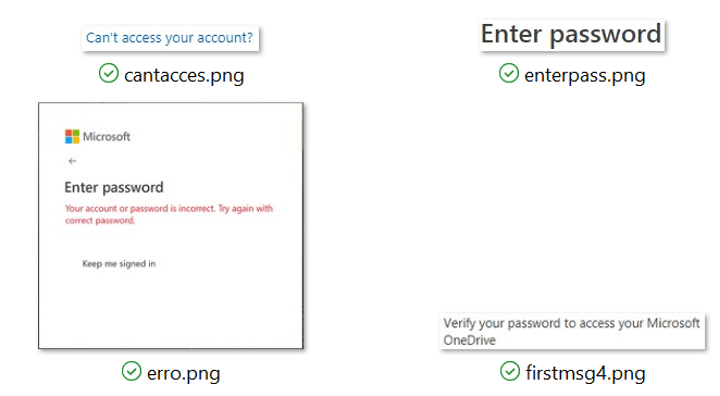
Figure 27. A phishing kit that targets Office 365 and uses images to display basic text
The Future of Phishing
Phishing is a lucrative business, and organized crime organizations operate much like any traditional organization. Under the leadership team are skilled individuals who specialize in different areas of phishing and fraud. Experts in human psychology and social engineering devise new lures to hook victims, web developers clone and host the fake sites, while others recruit unsuspecting members of the public to function as money mules. Since late 2018, Shape Security researchers have identified two growing trends in phishing attacks.
Where Botnets Fail, Click Farms Succeed
As the success of phishing continues to grow, so too does the need for the criminal organization to scale their operation. Botnets, a collection of compromised servers, home routers, and Internet of Thing (IoT) devices, allow the criminal organization to rapidly validate harvested credentials and automate fraudulent financial transactions. Over the past few years, however, security controls such as web application firewalls and fraud detection engines have become adept at detecting automated bot traffic. Aware of this, attackers are slowly making use of click farms (see Figure 28). Dozens of remote “workers” systematically attempt to log onto the target website using recently harvested credentials. Since the connection is coming from a real human using a standard web browser, the fraudulent activity can be harder to detect than bot traffic.
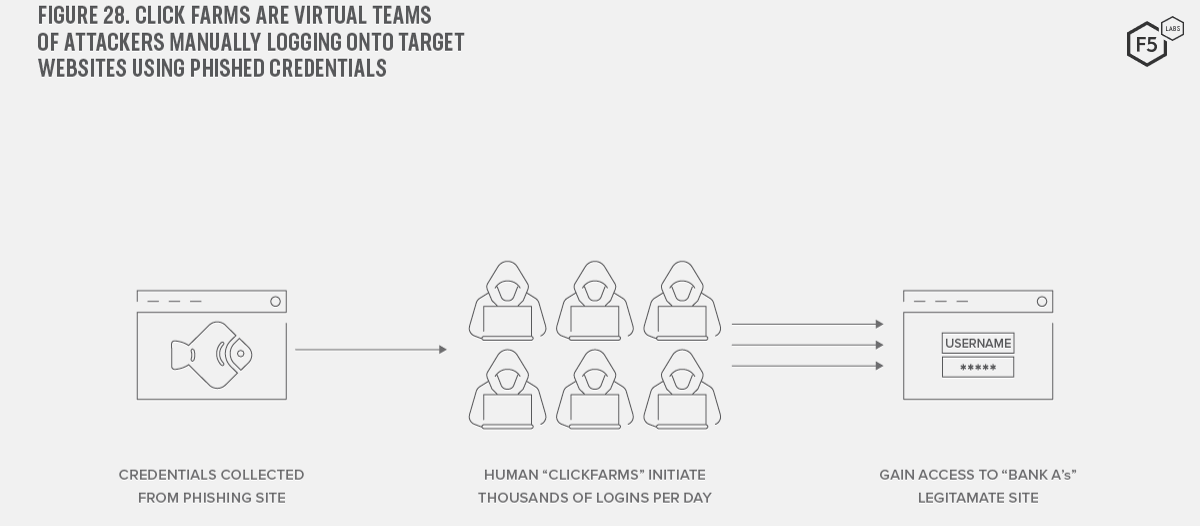
Figure 28. Click farms are virtual teams of attackers manually logging onto target websites using phished credentials
Figures from Shape Security show that, from a sample of 14 million human logins per month for one financial services customer, 0.4% were detected as humans attempting manual fraud. While this sounds like a tiny proportion of traffic, this still equates to 56,000 fraudulent logon attempts.
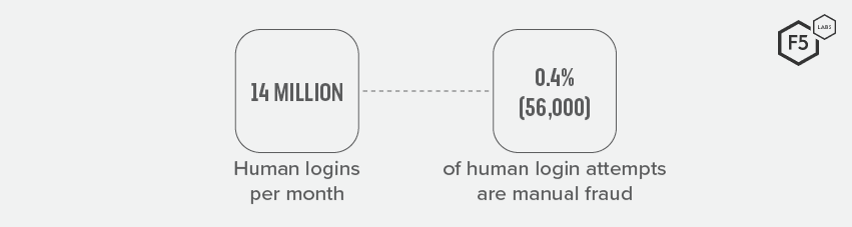
Figure 29. Comparing the total number of human logons per month to detected manual fraud attempts for a large financial services customer
The Emergence of Real-Time Phishing Proxies
Phishing is typically an asynchronous attack in which the attacker does not need to be active at the same time a victim is using their phishing site. Fraudsters craft an email, SMS, or voicemail, wait for victims to log onto the fake site and then, at some time in the future, collect the stolen credentials and attempt to log onto the target website (see Figure 30).
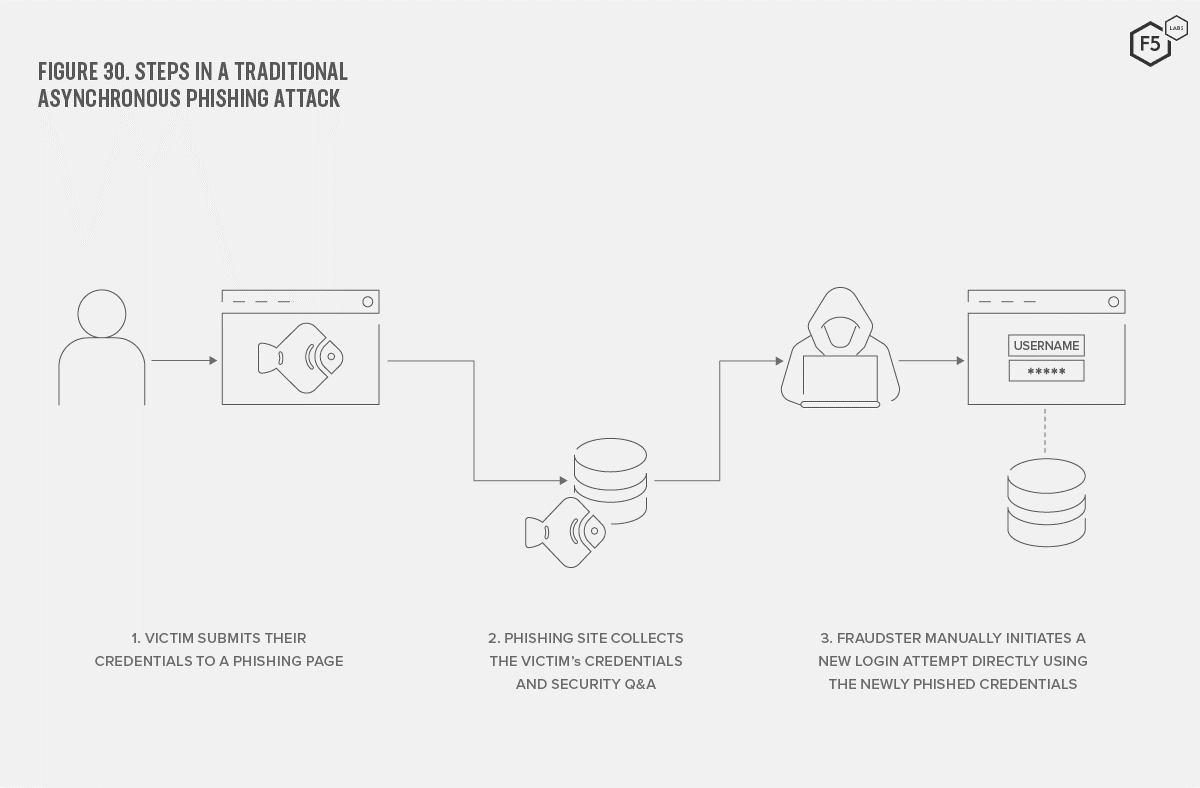
Figure 30. Steps in a traditional asynchronous phishing attack
This traditional model has several disadvantages. The longer the attacker waits to collect harvested credentials, the more likely the victim is to have reported the attack or changed their password. The model also struggles to contend with time-based authentication systems, such as multi-factor authentication (MFA) schemes. Standard phishing pages commonly ask the victim to enter far more information than simply their username and password. Often, they will ask for additional data such as mother’s maiden name, credit card number, postal address, and so on. These are all data that can be replayed at any point in the future. Since MFA codes—typically 6- or 8-digit numbers—change every 30 to 60 seconds, it is not possible for an attacker to capture one and reuse it hours or days later.
Shape Security researchers have recently found an increase in the number of real-time phishing proxies (RTPP) that can capture and use MFA codes. Instead of setting up a phishing site and directing users to it, the RTPP acts as a person-in-the-middle and intercepts the victim’s transactions with the real website. Since the attack occurs in real time, the malicious website can automate the process of capturing and replaying time-based authentication such as MFA codes and can even steal and reuse session cookies.
Table 2 compares characteristics of traditional phishing with the use of real-time phishing proxies.
Two real-time phishing proxies found in active use are Modlishka and Evilginx2.14F5 Labs and Shape Security will be monitoring the growing use of RTPP over the coming months.
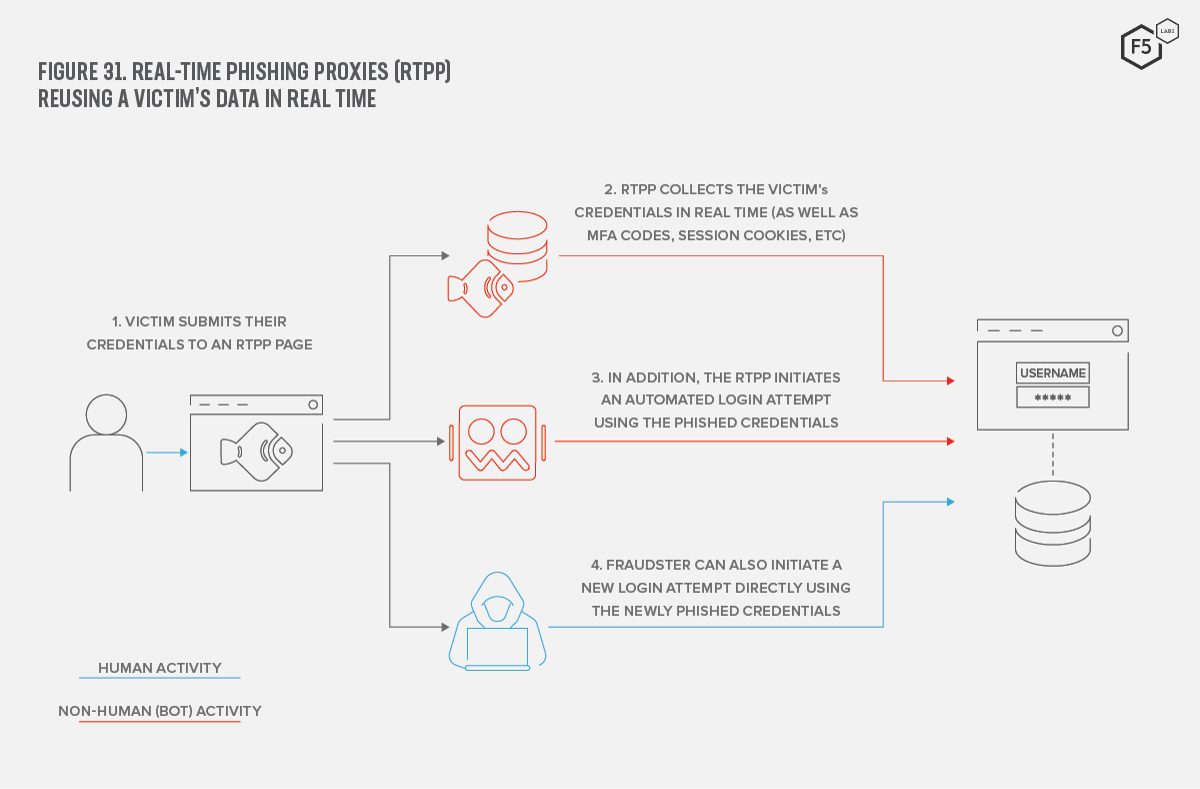
Figure 31. Real-time phishing proxies (RTPP) reusing a victim's data in real time
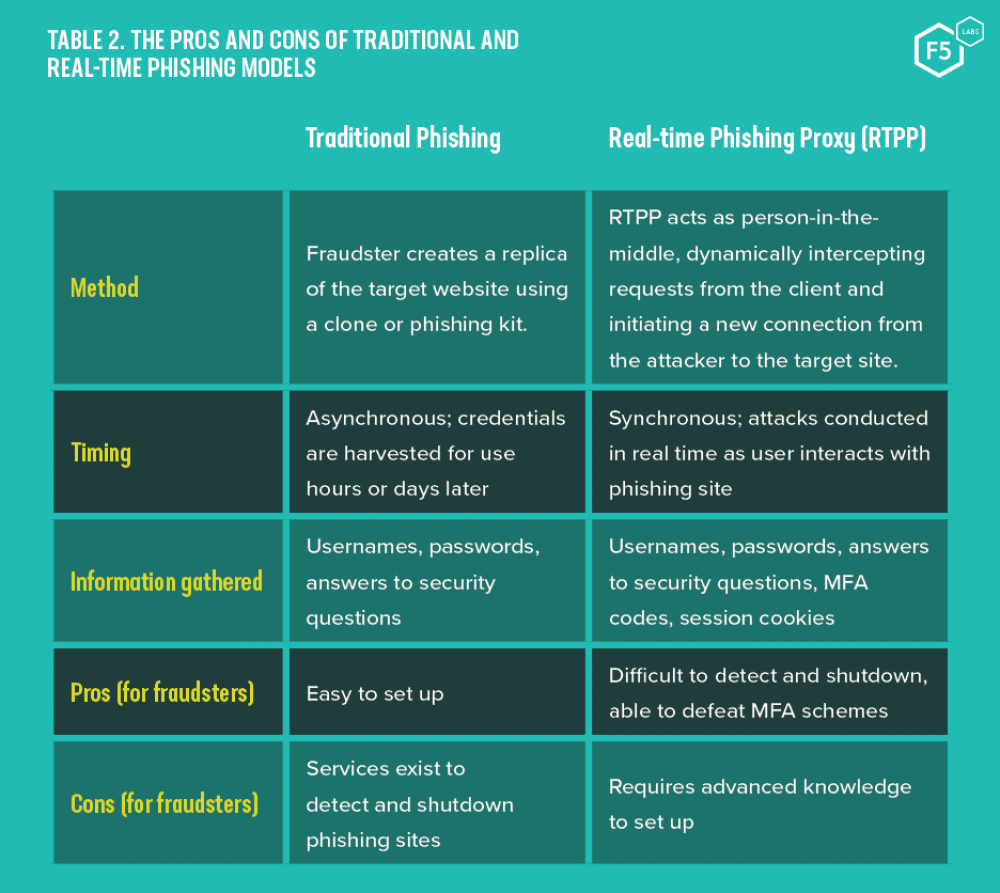
Table 2. The pros and cons of traditional and real-time phishing models
Figure 32. The NIST Cybersecurity Framework Five Functions
Combating Phishing
As with other social engineering tactics, phishing attacks look to exploit the human element of any system. While businesses can and should look to ensure they are taking a proactive stance to combat phishing, end users also need to be vigilant.
Protecting the Business
Every organization will be a target of phishing attacks, whether those attacks are directed or indiscriminate. Not all organizations implement robust information security management frameworks, however, and while many of them accomplish the same goals, the NIST Five Functions15 provides a useful way to think about any cyber threat.
Identify Your Assets and Highly Targeted Users
- Learn how your brand or business might be targeted.
- Consider use of attack chain frameworks, such as ATT&CK,17 (https://www.f5.com/labs/articles/threat-intelligence/2020-phishing-and-fraud-report#_ftnAutoIncr17) to help identify likely avenues of phishing messages (for example, email, SMS, WhatsApp, Facebook, etc.).
- Consider staff members as well as customers.
- Understand how attackers are likely to clone your site.
- Determine which staff members are high risk (C-level, finance operators, IT administrators).
- Think about which suppliers or services fraudsters may use to trick employees.
- Understand the workflow and authorization procedure for financial transactions.
- Identify all web properties that could be compromised by fraudsters to host phishing pages.
Protect Your Users and Your Networks
- Train staff members in modern phishing tactics such as fraudsters emulating Office 365 login pages.
- Implement strong password practices.
- Monitor lists of breached accounts and passwords.
- Proactively ask staff and customers to change passwords should their account be detected in another data breach.
- Do not allow the use of the most common passwords.
- Implement multifactor authentication wherever possible, particularly for high-risk people and technology. Understand the limitations of MFA and how attackers can circumvent it.
- Consider technologies to mitigate web app compromise, bot attacks, and fraudulent transactions (automated and manual).
- Ensure that web apps and content management system (CMS) plugins are always up to date to reduce chances of the website becoming compromised.
- Block frequently abused domains, such as 000webhostapp.com, appspot.com, etc.
- Block or closely monitor traffic to newly registered domains.
Detect Encrypted Traffic and Active Phishing
- Discover phishing sites impersonating your business.
- Monitor certificate transparency (CT) logs.
- Monitor newly registered domains.
- Make use of a phishing detection service.
- Monitor inbound traffic.
- Detect automated (bot) transactions to minimize malicious login attempts.
- Monitor encrypted outbound traffic.
- Block non-standard outbound web ports to prevent malware communicating with command and control and drop zone servers.
- Inspect SSL/TLS connections to ensure that malicious and potential phishing web traffic is being blocked.
Respond to Phishing Campaigns
- Have a plan and know who to work with to take down phishing sites as soon as they are identified.
- Investigating phishing sites can identify the primary target and activity of the fraudster, but evasion techniques may make this difficult.
- Make use of a good VPN service and user-agent switcher extension for your browser when performing reconnaissance.
- Consider a dedicated mobile device for investigative purposes since phishing sites may only reveal themselves if the correct target device tries to connect.
- Despite the best efforts of the business, customers and end-users are likely to identify more phishing attacks and malicious sites than any security control. It is essential that users have a clear and simple way to report successful and unsuccessful phishing attempts to your business.
Recover and Improve Your Phishing Plan
- Good information security management policies should be constantly evolving.
- Learn from active phishing attempts and successful attacks to focus on the most targeted job roles within the business.
- Put policies in place in order to deal with and recover from successful phishing attempts. Plan how to deal with stolen credentials, fraudulent money transfers, and unauthorized access to networks, applications, and data.
Protecting Users
Regardless of the lengths to which businesses go to protect their brand and their customers, the end user will always be a target of social engineering attacks. Just as security programs must keep up to date with changing tactics, so too must consumers. Here are some useful tips to avoid losing your password and, possibly, your life savings.
Use a Password Manager
A password manager—best used as a browser extension—serves two obvious purposes. Firstly, it helps create random and unique passwords for each site you visit. This is incredibly important password hygiene as it prevents the theft of your password from one website being used against you on another. Secondly, it remembers them all for you. All you need to remember is one long complex password which, yes, is okay to write down (so long as you leave it at home). But the less talked about benefit of the password manager is the ability to automatically enter your passwords into web sites for you (autofill), and the side benefit this has of potentially highlighting malicious sites. Since password managers will only autofill your password for a domain it recognizes, any spoofed site, no matter how genuine looking, will not prompt the extension to autofill (see Figure 33 and Figure 34).
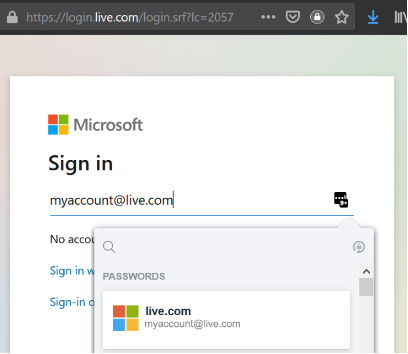
Figure 33. Password manager has known passwords for this site
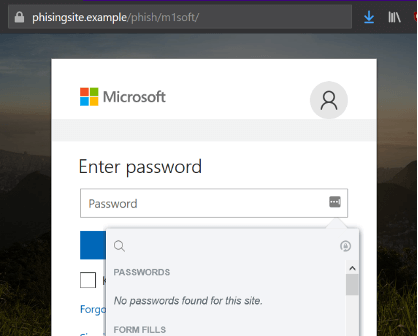
Figure 34. Password manager has no saved passwords for this domain
Don't Trust the Padlock!
We’ve been teaching users for years to “look for the padlock.” With almost 80% of all phishing sites now using HTTPS certificates, simply looking for the padlock or an address that starts with https:// is no longer suitable. In fact, it’s actively dangerous to advise this since it implies that sites are inherently trustworthy simply by having a digital certificate. We must train users to look for the valid domain at the end of the URL.
Never Click on Links in Emails
From hiding hyperlinks to disguising text as images, there are too many ways for fraudsters to mask the real destination of a hyperlink within an email. Many businesses now recognize this and do not include links in emails (although many still do). Consumers must become develop the habit of entering the website address themselves and manually searching for the information they seek.
Use Prepaid or Disposable Credit Cards
Similar to how multi-factor tokens constantly change their value, disposable credit cards allow shoppers to use a credit card with a constantly changing card number. These cards allow users to pay for goods and services online without worrying about their payment card details being stolen. After each transaction, the disposable credit card generates a brand-new card number for the subsequent use. Should a cybercriminal manage to capture payment card details, they will soon find that this card number has immediately become invalidated.
Conclusion
Phishing attacks will continue to be successful as long as there is a human who can be psychologically manipulated in some way. Security controls and web browsers alike must become more proficient at highlighting fraudulent sites to users. From deceptive URLs to abuse of HTTPS certificates, both staff and customers must be continuously trained on the latest techniques that fraudsters are using.

Robot

Download the report now!


