Key Findings
- Using data continuously captured by OpenPhish, we analyzed data from May, September, and November 2021 to see how trends in attacker activity changed as the holiday season approached.
- After generic (not industry specific) phishing, the top attacked sector, month after month, was finance. Individual financial institutions were attacked less than organizations, such as Facebook, in other sectors, but the sheer quantity of banks targeted made finance the most common sector for phishing attacks.
- Although finance, collectively, was the most attacked sector, the two highest targeted brands were Facebook and Microsoft Office 365/Outlook, which each received, on average, 10% of the phishing attacks analyzed.
- November saw increases in phishing activity, with attackers likely taking advantage of the increase in online shopping for the holiday season:
- The number of unique fraudulent domains jumped 157% in November, compared to the average for the rest of the year.
- Attacks targeting e-commerce experienced a 200% spike.
- Amazon was the top target in November, with Facebook the second most targeted.
- November also saw a large-scale phishing campaign against cryptocurrency exchanges and wallet services:
- Cryptocurrency platforms experienced an almost 1800% increase in attacks, possibly linked to the rise in the value of Bitcoin at this time.
- A single campaign was responsible for 90% of the cryptocurrency-related sites.
Phishing Continues to Grow as an Attack Vector
Phishing, which tricks victims into visiting fraudulent websites or into opening malicious email attachments, continues to grow unabated. For the ins and outs of phishing, read What Is Phishing (/content/f5-labs-v2/en/archive-pages/education/what-is-phishing--how-to-recognize-and-avoid-it.html). The 2021 Application Protection Report noted that phishing was the second most common initial attack technique leading to a successful data breach. This trend is seen across the security industry. In November, the Anti-Phishing Working Group (APWG) reported that phishing had doubled since early 2020, with July 2021 seeing the largest number of attacks in their reporting history.1 Europol’s 2021 Internet Organised Crime Threat Assessment (IOCTA) notes that due to the growth in online shopping (caused, in part, by the increase in working from home), delivery services are a frequent target for luring victims to fraudulent sites. The report finds that phishing remains the primary driver behind payment fraud “increasing in both volume and sophistication.”
The illegal use of stolen credentials can be applied at multiple stages of an attack chain. Some attacks culminate with the theft of a password database, other attacks use stolen credentials to gain access to an application or network, while other attacks use the credentials to send internal spear phishing emails from valid corporate accounts. The 2021 Credential Stuffing Report found that an average of 2.3 billion credentials are stolen each year, with the IOCTA report stating that the market for passwords and personal information is growing, since it improves the success rate of all social engineering attacks.
Top Phishing Targets
F5 Labs found this year that while a considerable proportion of phishing attacks are generic and indiscriminate in nature (on average 20%-30%), attackers increasingly use spear phishing to move laterally inside the network—once a low-level employee is compromised, it’s easier to phish other, more senior staff members. The IOCTA report corroborates this finding, remarking that social engineering as a whole is becoming more targeted, with attackers focusing on upper-level management.2
The Most Targeted Phishing Sector: Finance
Last year, F5 Labs found that the finance sector was hit particularly hard by targeted spear phishing. A third of all breaches against banking, insurance, and financial services were a result of business email compromise (BEC) in which attackers targeted specific roles (typically finance business units) pretending to be the chief executive or another high-level manager.
In 2021, this same industry was also the top target for phishing campaigns, accounting for 20%-23% of all fraudulent sites, as shown in Figure 1. Though no single financial institution was targeted significantly more than the rest, banks such as Wells Fargo and Crédit Agricole S.A. dealt with 2%-4% of all phishing sites abusing their name.
E-Commerce Under Attack During the Holiday Season
The month of November saw increases in phishing activity across the board. The number of unique domains used for fraudulent purposes increased by 157% compared to the average for May and September. Additionally, Figure 1 shows something interesting for November—a shift in attacker focus. Two sectors received considerably more phishing campaigns during this time: e-commerce and cryptocurrency exchanges. The huge spike in attacks against cryptocurrency exchanges, an increase of almost 1800% compared to previous months, deserves some deeper analysis (below).
The rise in phishing campaigns targeting e-commerce is perhaps easier to explain. The months of November and December typically see large increases in online shopping for the holiday season, so spikes in fraudulent sites pretending to be online retail stores or delivery companies are expected.
Most Attacked Companies
While the finance sector as a whole is clearly a top target for attackers, Figure 1 does not paint the entire picture. Generic phishing campaigns (that target no specific individual, organization, or sector) typically account for 20%-30% of all fraudulent sites in any given month. The most attacked individual sites were typically Facebook and Office 365/Outlook, which trade the lead during any given month (see Figure 2).
Amazon saw a 208% rise in the number of phishing campaigns in November 2021, with attackers clearly jumping on the increase in online shopping during the festive period.
Just as with top attacked sectors, the top attacked “brand” in November was Crypto/Wallet, accounting for almost 20% of all malicious websites. Let’s take a look at what went on.
Cryptocurrency Exchanges Attacked
Phishing attacks that target cryptocurrency-related sites and services tend to sit low in the list of priorities for attackers. Most months see only 1% of all phishing attempts targeting the cryptocurrency sector. Something changed in November, however, when fraudulent cryptocurrency-related sites suddenly accounted for just over 20% of all targets, an increase of over 1800%.
Delving into the raw data, it became apparent that one malicious domain stood out above the rest: krakentxy.com. Registered on November 3, 2021, it quickly became the most prolific site targeting cryptocurrency. The threat actor responsible for this campaign created 9,117 unique subdomains, all of which closely resembled those shown in Figure 3. Each krakentxy.com subdomain was hosted in Azure with a Let’s Encrypt certificate.

Figure 3. Example of a krakentxy.com domain targeting cryptocurrency users.
This particular domain made up 90% of all fraudulent cryptocurrency sites in November 2021. Although this domain is currently blocked by browsers and its DNS records no longer exist, using the Open Web Application Security Project (OWASP) Amass Project tool reveals another 194 domains currently hosted in Amazon Web Services (AWS). Although these additional domains do not currently resolve, it serves to show the cat-and-mouse game that attackers and defenders constantly play.
Even when excluding the krakentxy.com domain, cryptocurrency-related phishing sites still rose by 356% in November. The sudden interest by attackers could be attributed to the increased value of many cryptocurrencies in November. Bitcoin (BTC) rose to an all-time high of $64,400 for one BTC on November 12 (see Figure 4).
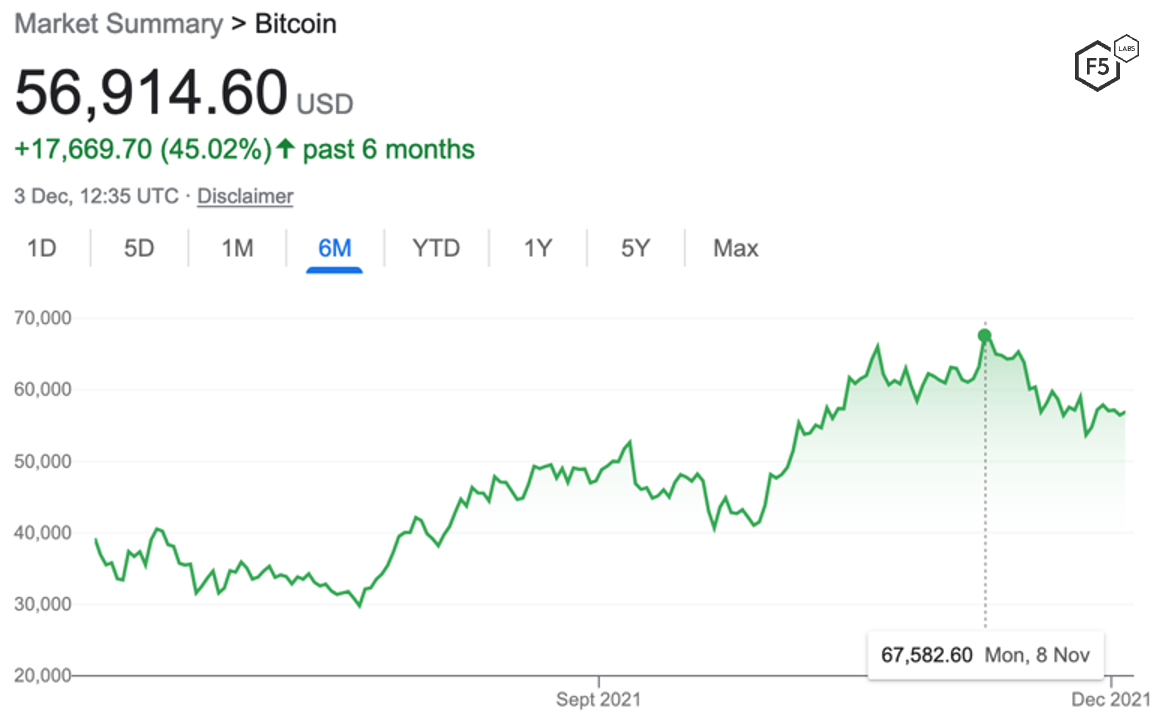
Figure 4. Bitcoin USD value, July to December 2021.
Phishing is not the only method that attackers used against cryptocurrency exchanges and wallets. As noted in the 2021 TLS Telemetry report, malicious Tor exit nodes were also used to strip SSL/TLS connections, which allowed attackers to harvest credentials to cryptocurrency exchanges.
Investigating Attacker Methods
Threat actors frequently refine their techniques to improve the success rates of phishing attacks. Using stolen personal data and encryption and disguising website addresses are all useful methods in the attacker’s toolkit.
Secure Does Not Mean Safe
Using valid TLS certificates allows attackers to lead potential victims into believing the site is secure and therefore “trustworthy.” The use of encrypted phishing sites has steadily increased over the years. This time last year, 72% of fraudulent websites were encrypted; this year that figure has increased to 81% of phishing sites.
Phishing links, delivered via email, text message, or social media, often use redirection so that the initial URL is rarely the final URL the victim lands on. In some cases, the original phishing link uses HTTPS and redirects to an HTTPS website. In some cases, an unencrypted phishing URL actually redirects to an encrypted HTTPS site. Table 1 breaks down the use of encryption across initial phishing URLs and final destination URLs.
| HTTPS link with HTTPS destination | 46% |
| HTTP link with HTTPS destination | 34% |
| HTTPS link with HTTP destination | 8% |
| HTTP link with HTTP destination | 12% |
Table 1. Comparison of initial phishing URL with final URL.
Attackers will always look for the easy route, as many of us do. When it comes to securing their malicious sites, they often take advantage of automated and free services provided by the hosting provider. Google certificate authorities (CAs) account for roughly 8% of certificates and Cloudflare for about 7%. Let’s Encrypt always takes the top spot, however, accounting for an average 41% of certificates used on fraudulent sites.
Disguising URLs
Web browsers are doing a better job at highlighting the actual domain that appears to users. Browser address bars commonly highlight the base domain, such as example.com, while graying out nonessential information, such as the subdomain and path. Despite this, attackers still attempt to confuse and trick victims by including company names, brand names, or keywords somewhere in the URL. Table 2 shows the top 10 most common terms used in the path of a phishing URL.3
| Term | Percentage |
| login | 9.2% |
| .com | 4.7% |
| wp- | 4.5% |
| 3.8% | |
| secure | 2.4% |
| profile | 2.1% |
| bank | 1.7% |
| www. | 1.6% |
| discovercard.com | 1.4% |
| 0.4% |
Table 2. Top 10 terms used in phishing URLs to trick victims.
The word login indicates that nearly 10% (though likely more) phishing sites are targeting credential theft, while the use of www. and .com in the path implies that attackers are hoping that a domain name, such as www.mybank.com in the path, will be enough to fool the victim into thinking they are on their bank’s genuine site. Table 2 shows that one company’s domain name, more than any other, kept showing up in phishing sites: discovercard.com. The use of profile in the path is almost exclusively related to fraudulent Facebook sites.
Most Abused Top-Level Domains
F5 Labs' 2020 Phishing and Fraud Report noted that .com remained the most frequently abused top-level domain (TLD) by fraudsters, accounting for 51% of all phishing sites. The .net TLD came in second at 3.4%. This year saw some change: the ubiquitous .com TLD still comes in at the top, but its lead has shrunk to just over 45%. A new entry in second place is .app at 7.5% of phishing sites, with .org in third place at 5%.
The 20 TLDs shown in Figure 5 represent 80% of the most frequently abused TLDs out of the list of 415 unique TLDs attackers used.
MITRE ATT&CK Groups Analysis
The MITRE ATT&CK knowledge base (/content/f5-labs-v2/en/labs/learning-center/mitre-attack-what-it-is-how-it-works-who-uses-it-and-why#attcks_easytomiss_invaluable_resources) is a powerful resource for looking at how threat actors use phishing. It details the specific behaviors used by 129 advanced attacker groups, including their known attack methods based on observations in the wild.
We added up all the attack methods these groups used (most groups use multiple techniques). In total, we found 334 entries falling into nine techniques; of those, the most commonly mentioned was phishing, at 48.2%.
The techniques mentioned provide enough detail to break this down even further into three phishing subtechniques. The most frequently mentioned subtechnique (63%) was Spearphishing Attachment (T1566.001), and the most commonly noted types of attachments were Microsoft Office documents (46%). The second most frequently mentioned phishing subtechnique (31%) was Spearphishing Link (T1566.002), with the most commonly noted link tied to downloading malware. The least mentioned phishing subtechnique (4%) was Spearphishing via Service (T1566.003), with social media the most cited example (86%).
This information gives you an idea of current attack trends. Just because a particular technique or subtechnique wasn’t mentioned frequently in the known behaviors of attacker groups doesn’t preclude them from being used in the future. Remember, attackers are intelligent and will change tactics if something isn’t working.
Phishing Introspection
F5 is a large company with thousands of employees across the globe. Our internal threat intelligence team shared their observations of phishing threats during the year. First off, their data indicates that 45% more phishing emails were detected during the middle of 2021 (March through October). Second, they reported that a lot of ransomware droppers are coming in via phishing email. Table 3 breaks down the top phishing-delivered malware seen over the year.
| Malware | Type | Note |
| FormBook | Data stealer—collects confidential data from infected machines. | Very easy-to-use malware—available in a Malware as a Service model. |
| Agent Tesla | Data stealer—collects confidential data from infected machines. | Keylogger, a downloader, a password-stealing malware, and a screen-capturing malware. |
| LokiBot | Credential harvester—uses a keylogger to record login names and passwords. | Creates a back door to install more malware. |
| Dridex | Banking trojan—specifically designed to steal financial data. | More info in F5 Labs article, Dridex Is Watching You. |
| ZLoader | Banking trojan—specifically designed to steal financial data. | A variant of the Zeus/Zbot malware, often infects through compromised documents. More info from F5 Labs about banking trojans. |
| TrickBot | Banking trojan—specifically designed to steal financial data. | Known to drop other types of malware, such as credential harvesters. More info in F5 Labs article, Tricky Trickbot…. |
| Ave Maria | Data stealer—collects confidential data from infected machines. | Also known as Warzone. Can also keylog and assume control of a camera. |
Table 3. Most common malware observed in phishing attempts against F5.
Mitigation
Recommendations to mitigate the effectiveness of phishing attacks can be boiled down to three sets of controls:
- Limit brand impact: This consists of controls and methods that can limit the impact to a brand. This includes continuously monitoring for domains that make use of a company’s name or brand. Whois records and TLS certificate transparency logs are both useful for this.
- Prevent staff from visiting fraudulent sites: Methods to prevent staff members from visiting fraudulent sites should include the ability to inspect web traffic and block malicious content from being downloaded. With the web rapidly approaching 100% encryption, web proxies should be able to “break and inspect” SSL/TLS connections and block other encrypted traffic that cannot be inspected. End-user anti-malware continues to be an essential control to detect and stop malware that can bypass web proxies.
- Block credential abuse: Use controls that can prevent attackers making use of phished credentials to gain access to your applications and data. Controls here focus heavily on strong password policies, including the use of multifactor authentication. Real-time phishing proxies, as covered in the 2020 Phishing and Fraud Report, can circumvent multifactor authentication, so it is important to be aware of its shortcomings. Attacker automation means that application defenders should consider controls that can detect nonhuman traffic and either block it or perform increased scrutiny before granting access.
For all aspects of phishing, frequent and up-to-date user training is essential. The controls and techniques outlined in Table 4 are covered in more detail in the 2021 Application Protection Report.
| Phishing (T1566) | Antivirus/anti-malware Network intrusion prevention Restrict web-based content User training |
| Credential stuffing (T1110.004) | Account use policies Multifactor authentication Password policies User account management |
| Internal spearphishing (T1534) | User training |
| Phishing via link (T1566.002) | Restrict web-based content User training |
Table 4. Controls that MITRE ATT&CK recommends to mitigate phishing attacks.
Conclusion
Phishing attacks continue to grow as attackers recognize it is often significantly easier to fool a human than it is to compromise a vulnerable application, with 2021 seeing the highest number of phishing attacks ever recorded by the APWG.
The dearth of stolen personal data enables threat actors to refine their tactics, allowing for more targeted and genuine-looking spear phishing and BEC attacks. Malicious motivations are typically driven by consumer behavior—increased online shopping in November led to a 200% increase in fraudulent retail sites, and the high market value of Bitcoin led to an explosive 1800% growth in phishing attacks against cryptocurrency wallets and exchanges.
Attackers continue to focus on Office 365 as well as Facebook. It is essential that user training highlights the tactics of phishing emails that attempt to emulate the look and wording of OneDrive, SharePoint, and Facebook notifications.
Recommendations
- Enforce TLS everywhere or use the HTTP-Strict-Transport-Security (HSTS) header on web apps
- Inspect all staff web browsing traffic using web proxy, including encrypted SSL/TLS sessions
- Route all web browsing traffic for remote users through VPN via same web proxy
- Deploy multifactor authentication (MFA) for all systems
- Conduct user awareness training for employees and customers
- Search certificate transparency and domain registration services
- Ensure app defenses detect credential stuffing attacks
- Maintain antivirus on all corporate devices
- Work with domain registrars and law enforcement to take down fraudulent websites
- Change passwords and email addresses of targeted employees


