During the evaluation of various service and solution offerings that would potentially meet their requirements, our customer, a global IT solutions company, performed an extensive review of the variables involved in deploying and operating a solution that combines a content delivery network (CDN), Web Application Firewall (WAF), and protections against Fraud/Bots and distributed denial-of-service (DDoS) attacks. After considerable analysis and internal discussions with multiple teams, our customer determined that the best solution would be a combination of F5 Silverline and the Amazon CloudFront content delivery network.
Our customer chose this solution because it offered managed security services, fast deployment, and lower cost to provision, maintain and operate. The internal customer teams defined a plan for the evolution of the website and focused on completing each phase of their plan quickly, without major impact to ongoing operations.
The ease of implementation and combined benefits of the architecture provided continuous performance improvements, additional security controls, and extensive reporting and logging with data-export capabilities to SIEM and other log-analysis platforms. This allowed our customer's team to focus on what they do best: providing a seamless and engaging customer experience.
Our customer selected F5 and AWS solutions for the implementation of the fourth phase of their plan (Figure 1) primarily because of the flexibility each service offered in their configurations, the low cost of operation, and the ability to grow the system over time through multiple iterations. Another key factor was the ability to work with the F5 Silverline Security Operations Center (SOC) analysts, who continually monitor the Silverline platform. (Silverline is F5’s cloud-based, managed security services platform.) The SOC analysts helped our customer define their security posture and maximize the usability of the system. This allowed our customer to provide a frictionless experience while relentlessly fighting fraud and abuse.
Balancing the cost of operations with performance improvements over the evolution of a web application while providing a fast, secure, and frictionless customer experience
Companies are faced with several challenges and constraints when architecting and designing web applications. A major consideration is balancing the cost of acquiring, deploying and managing the technology and personnel effectively to allow continuous performance improvements over the application lifecycle. The illustration below depicts the analysis our customer performed regarding the balance of cost versus performance that is required to evolve a web application.

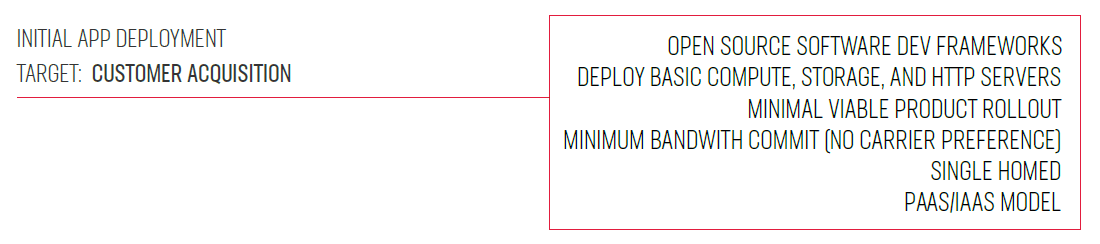
During the initial phase, our customer focused on deploying the application and obtaining customers. The steps they executed to achieve their target involved:
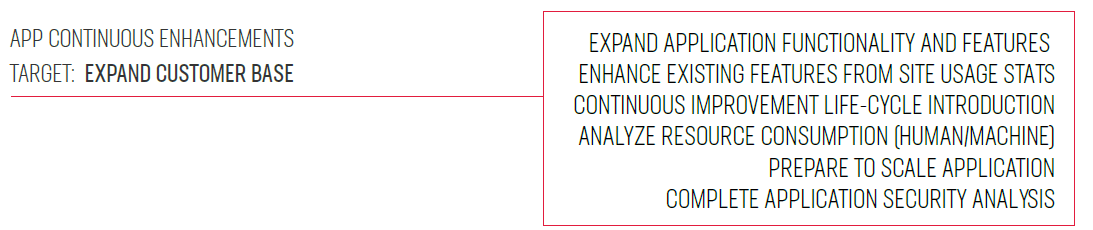
In phase two, the customer focused on enhancements and improvements to acquire a customer base and prepare for additional expansion.
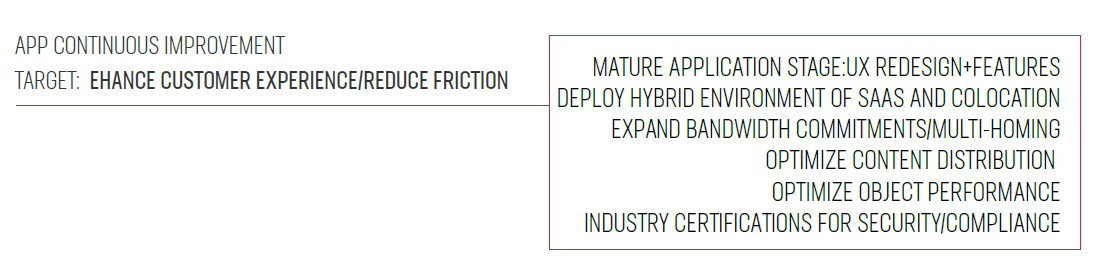
In phase three, our customer worked with our F5 Silverline account team to deploy the managed security components and configure Amazon CloudFront to ensure the application would scale and accommodate all traffic generated.

For phase four, our customer analyzed customer origin requests and determined that many of their customers were transacting from countries outside the US. This observation, coupled with additional analysis of increased demand in the US, motivated their implementation of Amazon CloudFront to extend their reach and improve global performance.

For the final phase, customer teams focused on deploying a hybrid environment of both mixed colocation services and SaaS/IaaS/PaaS platforms to enhance their operational capabilities and adaptation to fast-changing global market environments.
This document will focus on the technical steps our customer executed to complete the phase four integration of Amazon CloudFront with the F5 Silverline managed security services platform.
Basic requirements to ensure a successful service deployment and system integration
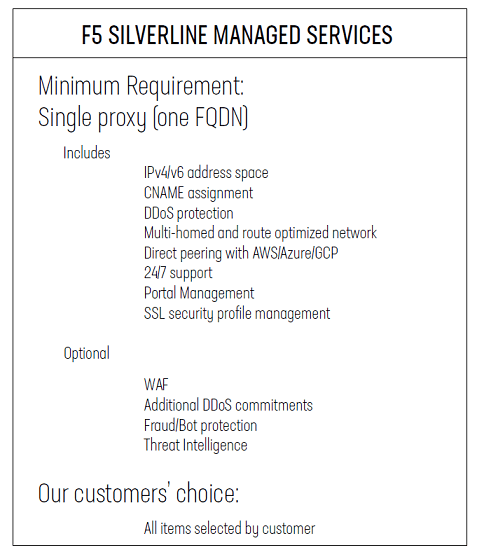
To prepare for the integration of Amazon CloudFront into the F5 Silverline Platform, our customer provisioned the following items, with assistance from the Silverline team:
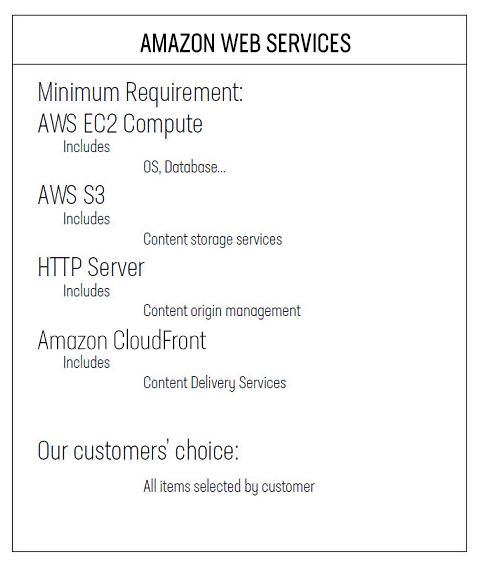
Building a secure and scalable network that allows customers to obtain the best performance and engagement experience globally
Deploying a secure, fast, global network with multi-homed links and multiple services is not easy for any organization. Fortunately, customers can benefit from the combined investments in infrastructure and services that F5 and AWS can offer. This allows customers to construct a solution that can be deployed rapidly to onboard applications with maximum efficacy and realize an immediate return on investments.
The architecture our customer chose to deploy is depicted in the illustration below:

Ease of deployment for rapid integration
Organizations are being pressed to roll out applications that quickly respond to market challenges to gain a competitive advantage and/or cost savings. Deployments that can be done in a short period of time offer a considerable advantage over deployments that require extensive resources and additional costs. With F5 and AWS, the deployment of these configurations is easy; if customers have all the components and data ready to configure, it can be done in minutes.
With phase three complete, our customer moved to the fourth phase, which entailed integrating Amazon CloudFront with the F5 Silverline Platform and included the following steps:
When our Silverline SOC team deploys the portal account, customers can log in and configure the proxy root object with required settings for the proxy display name, the FQDN (Fully Qualified Domain Name), the origin server IP address or ELB CNAME (Canonical Record), Threat Intelligence profiles, WAF policies, SSL certificates, and Fraud/Bot protection endpoints. Customers will review these steps with a Silverline SOC analyst during the onboarding phase. Customers may also engage a SOC analyst to assist with any proxy deployment.
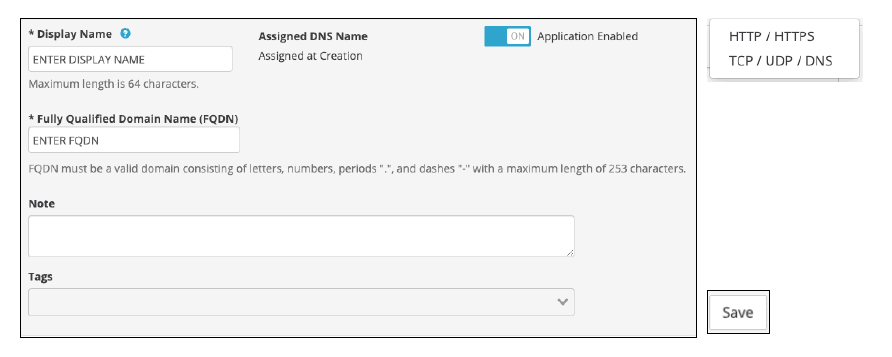
Once the proxy has been saved and deployed to the Silverline platform, customers will receive a unique CNAME that will be used as the origin for the Amazon CloudFront network. Customers may locate this proxy CNAME in the main configuration panel after deployment.

Once the proxy is enabled, it is ready to receive traffic immediately and can be used to route user requests from CloudFront as soon as that service is configured.
Amazon CloudFront - Service Configuration
To ensure a smooth integration, customers should have the following information available before performing the CloudFront integration.
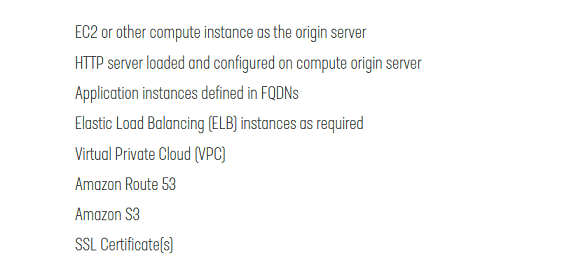
Once these components are in place and provisioned, customers can initiate the CloudFront configuration by navigating to the AWS management console. In the console menu, locate and select the sub-category "Networking & Content Delivery" / CloudFront. Locate and select the "Distributions" link and proceed to create the initial distribution.
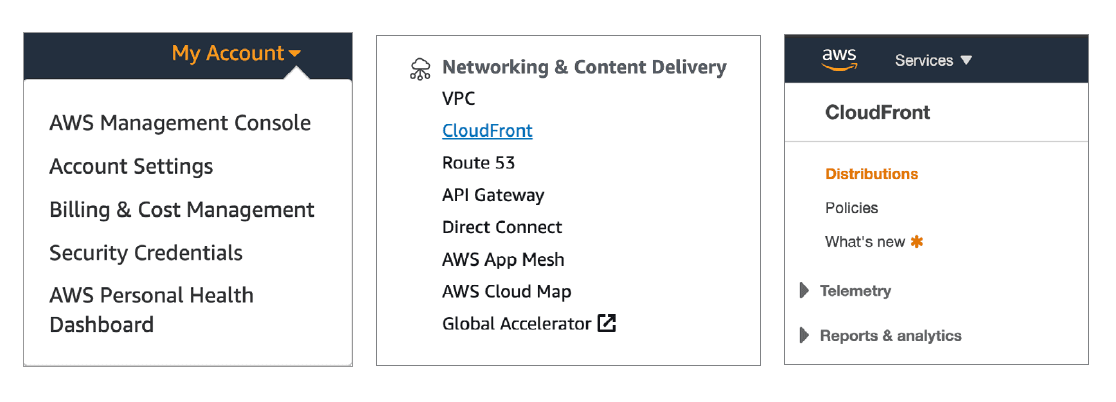
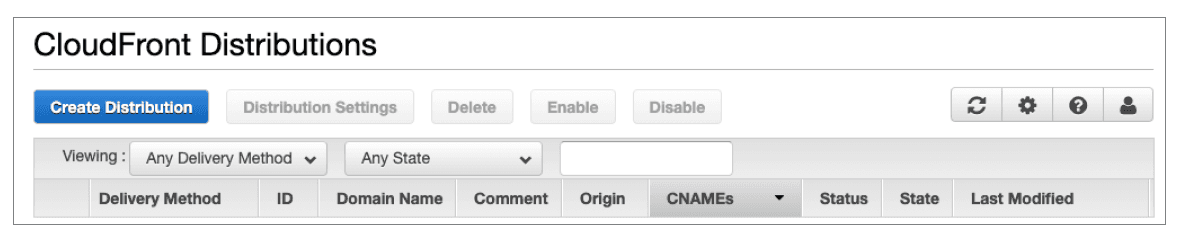
To initiate the object configuration, select the "Create Distribution" control. You may be prompted to create a "Specific Deliver Method". Our customer chose the "Web" delivery method.
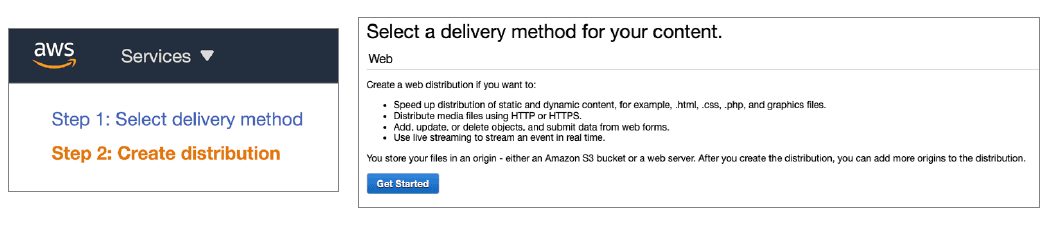
Select the "Get Started" control. The panels below will render on the browser. Configure the Origin Settings as shown:
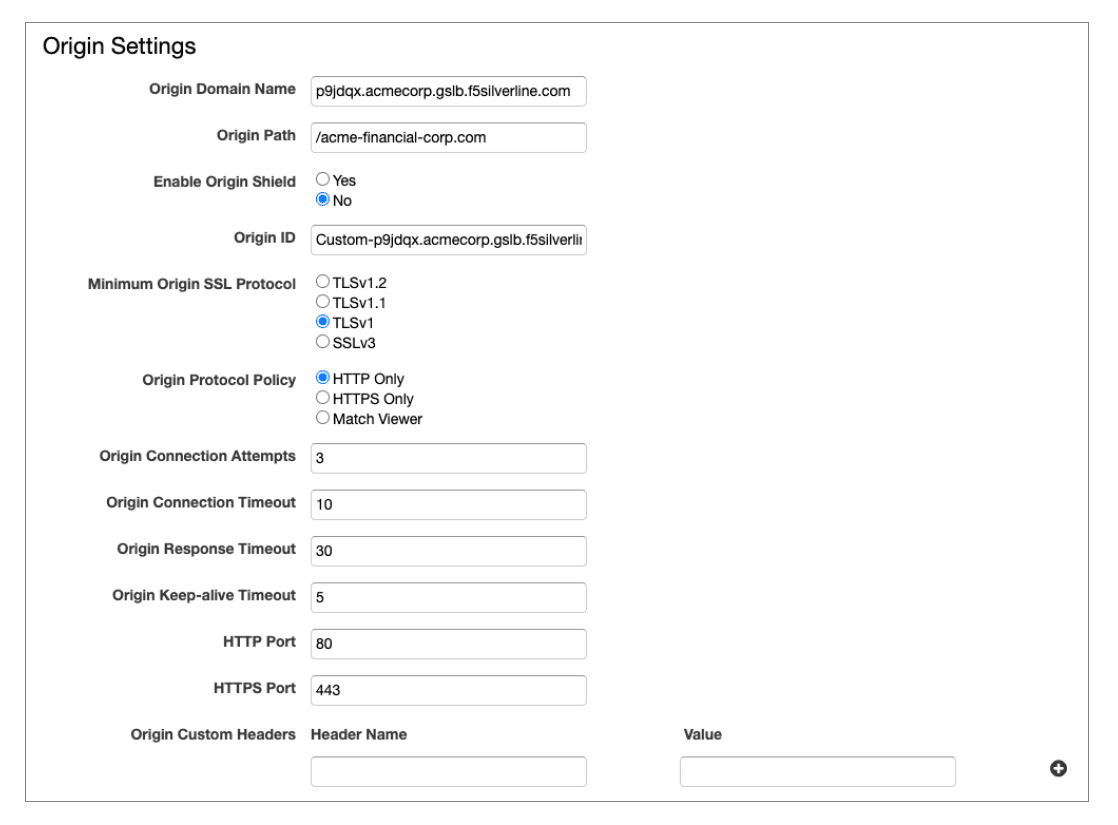
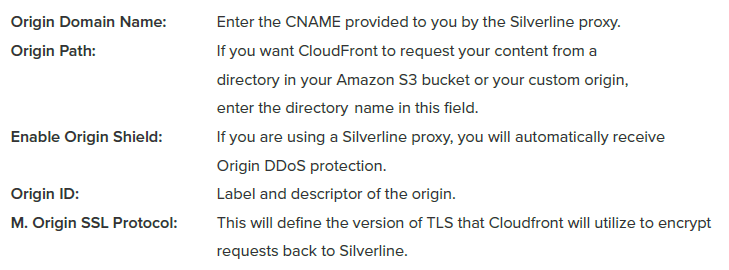
Origin Connection Attempts, Origin Timeout, Origin Response Timeout, Origin Keep-Alive Timeout, HTTP and HTTPS Ports should remain as defaults unless a change is required.
Origin Customer Headers: Custom header keys and values will be in every request to origin. These settings may also be used to filter out any requests at the Silverline proxy that are not originating from CloudFront.
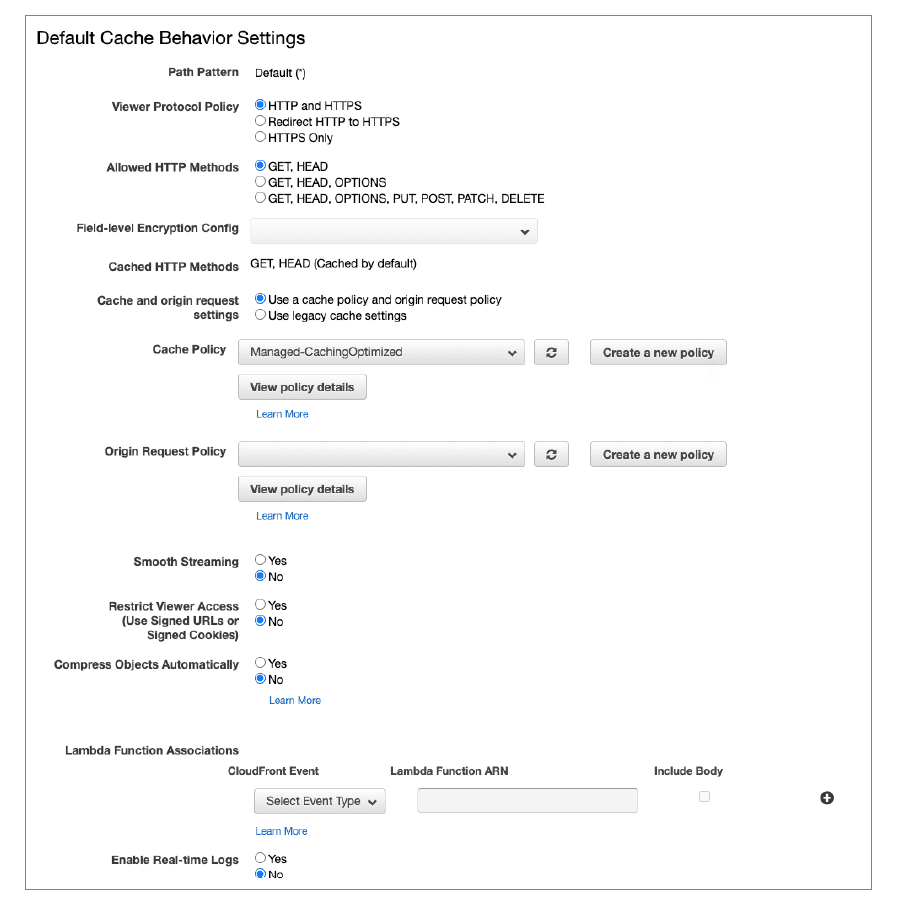
Default Cache Behavior Settings can be programmed according to internal policies defined by the application developers, information technology, DevOps, security teams, and other stakeholders. It is critical to emphasize the importance of understanding the degree of impact any changes to the values may have on the overall operation of the application. F5 Silverline recommends an evolutionary approach as each setting may introduce variances in cost, security exposure, performance impact, and interaction with the Silverline WAF or Bot/Fraud protection. AWS provides excellent documentation from the management console to help organizations understand how to apply each control and what impact it may have on existing operations. Our Silverline SOC analysts may also provide information on how these settings will affect the Silverline proxy, WAF or Bot/Fraud protection.
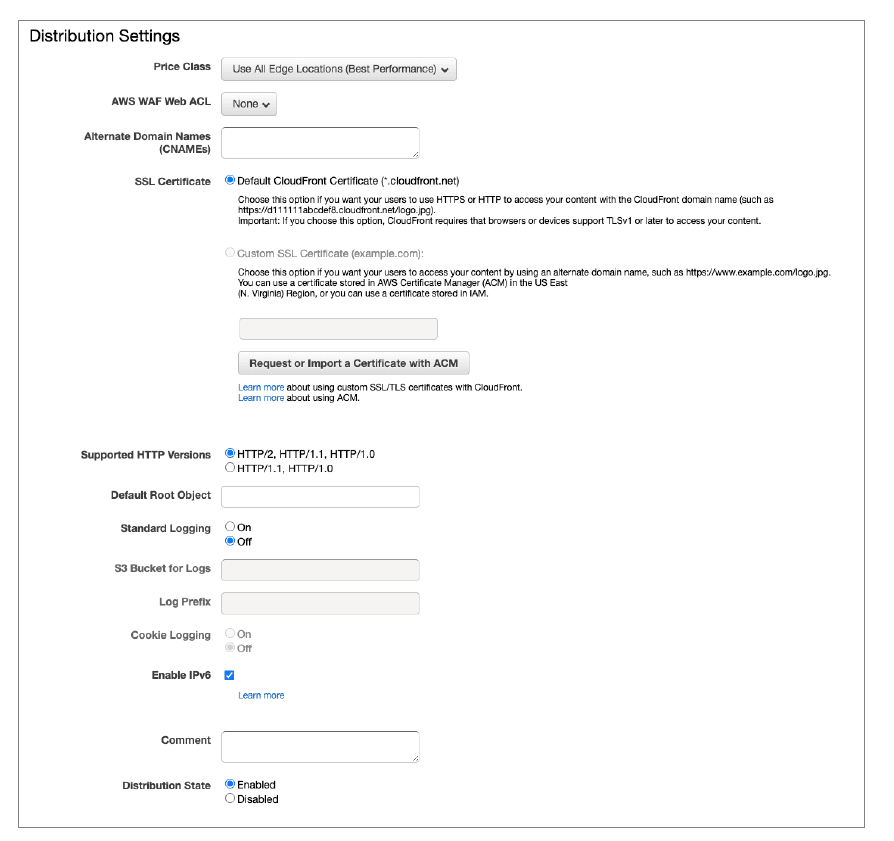
Distribution Settings may also have a considerable impact on operations. The settings that are worth additional consideration are as follows:
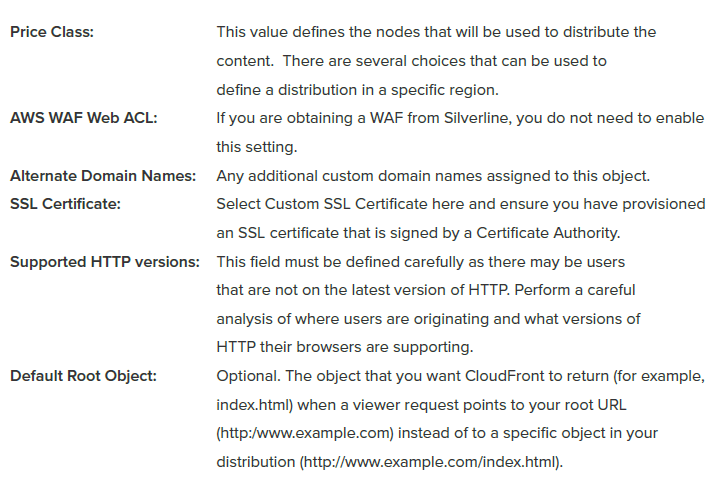
The final step will be to create the distribution.
This should take a few minutes and, once completed, customers will receive a CNAME.

The CNAME issued by Amazon CloudFront can now be used with AWS Route 53 as the authoritative record of resolution for any traffic bound for the application.
Our customer's internal security, information technology, operations, and development teams spent a lot of time evaluating the best solution for their customer engagement and marketing strategy goals. Once our customer selected the solution, the implementation proceeded without any roadblocks and they had the services and applications up and running globally within minutes, providing their worldwide customers with a much smoother and faster engagement experience.
PUBLISHED JANUARY 11, 2021