Today’s business challenges are radically different from before the Internet and the explosion of mobile devices. Generation Z members are trickling into the workforce and changing its demographics, bringing new challenges for IT departments. This new workforce wants to bring their own devices to the enterprise; use social media to realize business benefits; and access any device from any location, at any time. IT must now reconcile this new landscape with the need for high security. Even as IT flexes to accommodate these users, budget constraints mean it must also find innovative ways to cut costs, yet maintain high levels of employee productivity. Moving and deploying applications in the cloud promises to address some of these challenges by providing a leveled platform for outsourcing and offering the ability to scale as the business grows.
Business applications play a pivotal role in connecting enterprises and employees. Almost all businesses rely on applications to ensure smooth day-to-day operations. Ensuring that application delivery is always secure, fast, and available is paramount for any business to meet these business priorities:
F5 plays a unique role in helping enterprises address the problems they face as they roll out various initiatives to support these business priorities, including issues related to application performance, infrastructure scalability, and data center security. F5’s strategic position in the data center allows it to intercept and understand the context of user access; it can then provide the necessary control for all traffic flowing into and out of the data center. F5 solutions can assist in cutting costs by consolidating disparate point solutions into a consolidated platform. This not only offers businesses architectural flexibility, but also helps reduce initial investments and running costs and makes it easier to manage the IT infrastructure.
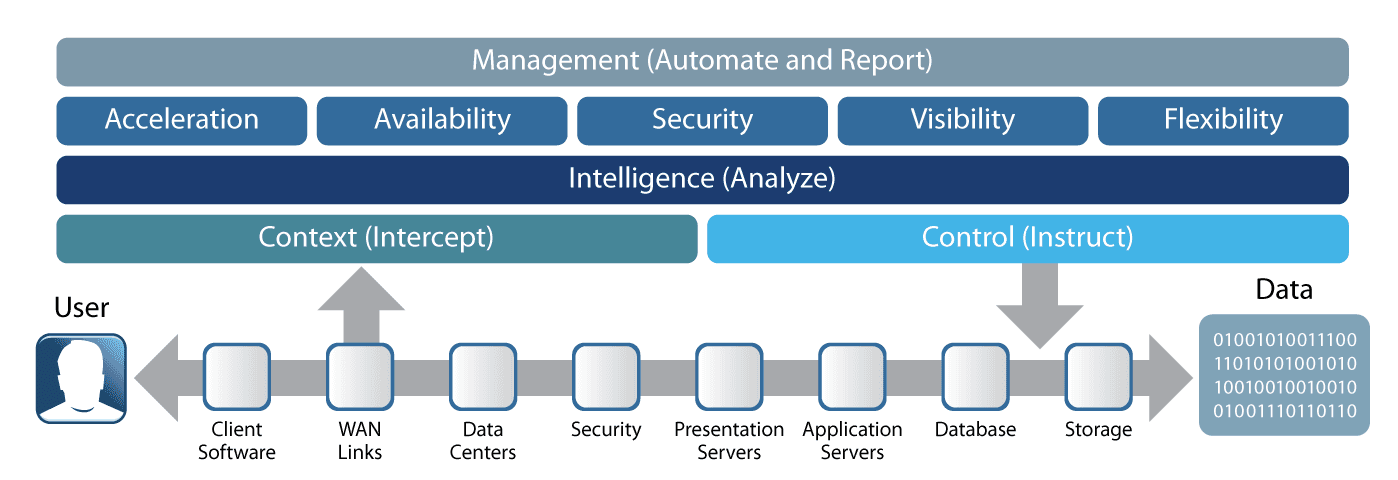
When designing an application delivery architecture, an enterprise should first consider its most important group of stakeholders: its customers, both internal and external. The customer user experience must always be optimal, whether they’re accessing an enterprise’s online store, checking on relationship status, or seeking customer care via the corporate website. From a customer perspective, three key requirements ensure a satisfying experience: optimized performance from any device, consistency, and unfailing but behind-the-scenes security.
“56% of surveyed customers selected an F5 solution over the competition because of application acceleration and optimization.”
Source: TechValidate survey of 107 F5 BIG-IP users; TVID: 467-850-1E5
With the proliferation of smartphones and other mobile devices both at the consumer level and within the enterprise, bring-your-own-device (BYOD) schemes are increasingly becoming the norm. In this environment, application and network managers are facing the challenge of delivering optimized content to the end user device without degrading the user experience.
From the application server end, F5 can address this problem by helping to accelerate application content asymmetrically from the server via advanced caching and compression technologies.
F5 also provides client-based acceleration that can improve user access and speed application performance by up to 8x, enabling faster communications. Dynamic data compression and client-side cache reduce traffic volumes to minimize the effects of network latency and client connection bottlenecks on application performance. Client-side quality of service (QoS) and application traffic shaping for end user devices reduce latency and dropped packets for remote applications. Traffic can be prioritized so specific applications, such as VoIP, are sent before others.
With F5, customers have realized performance improvements of up 8x. Use the Optimization Calculator to test F5 caching and compression.
Customers are likely to access more than one service at a time, and enterprises must offer a consistent, unified experience regardless of the various services they access. F5’s unique application access management and control solution can help by providing access services to application owners.
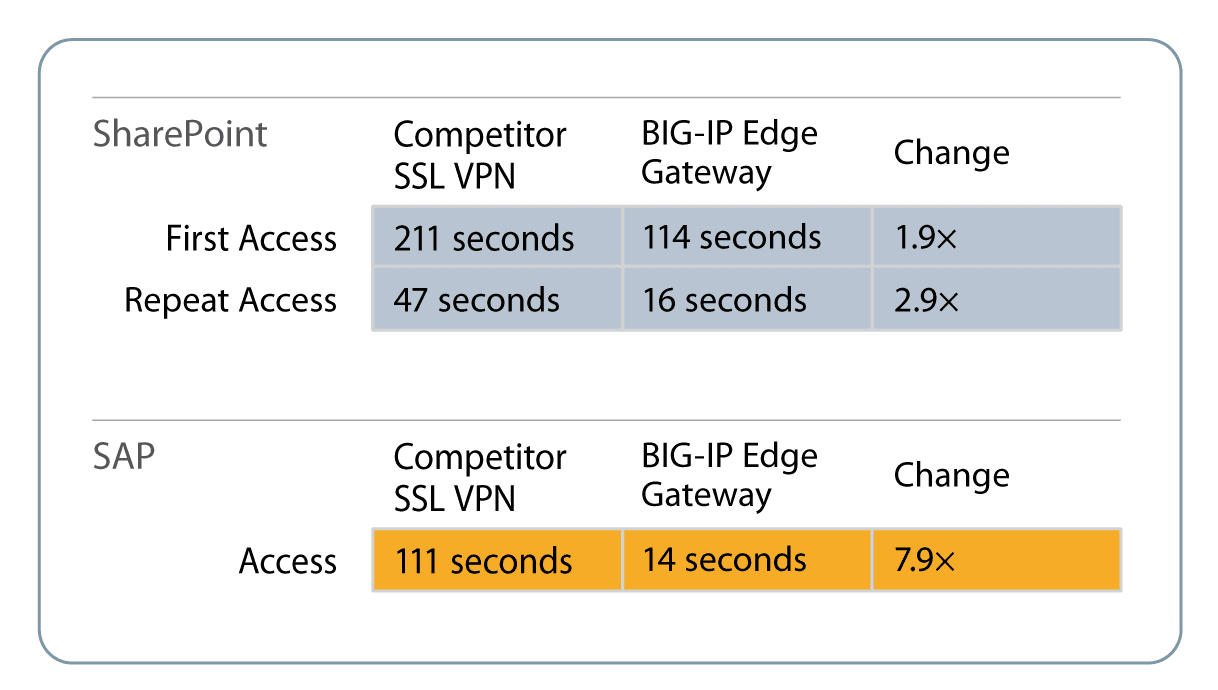
F5 provides single sign-on (SSO) offloading across multiple domains, so users can access multiple applications or services—such as Microsoft SharePoint and Outlook Web Access, and web applications running on Oracle, IIS, Apache, WebSphere, and SAP—via a single credential. F5’s authentication proxy solution that integrates with leading enterprise SSO solution providers such as Oracle Access Manager (OAM) and IBM Tivoli helps organizations simplify application deployment, as well as dramatically reduce the total cost of ownership (TCO) and simplify users’ experience as they access application services.
F5 solutions come with prebuilt authentication policies that greatly reduce the complexity of deployment and time to service. By providing a unified point of enforcement, F5’s integrated solution simplifies auditing and enables IT to control changes in application access control configurations — offering a superior user experience and increasing productivity.
F5 solutions support a wide range of mobile operating systems—iOS, Windows, Linux, and Android—so employees and customers can access enterprise applications and business services securely while on the move and stay productive even when out of the office.
While a seamless user experience across applications is important, organizations also want the peace of mind that comes with knowing access to their services is secure, regardless of customer device and access method.
F5’s unique secure access solutions are well suited for both remote and intranet users who need end-to-end security while accessing any service. More than a dozen integrated endpoint inspection checks are preconfigured, including OS, antivirus software, firewall, file, process, and registry, as well as the device’s MAC address, CPU ID, and HDD ID. A browser cache cleaner automatically removes any sensitive data at the end of a user’s session.
Access can be granted granularly and with a full audit trail via an intuitive graphical visual policy editing tool. Access device hardware can be mapped to user role to allow more decision points for policies. F5 secure access solutions are also built to integrate with leading mobile device management (MDM) and two-factor authentication (2FA) solution providers, making them among the most versatile on the market.
In addition to securing access at the client level, F5 can also help ensure maximum protection at the application level by defending against application layer attacks such as SQL injection, cross-site request forgery (CSRF) and cross-site scripting (XSS). In an age of ever increasing multi-layered threats, F5 security solutions also provide an effective defense against distributed denial-of-service (DDoS) attacks.
Because a pleasant customer experience is critical to retaining and attracting new customers, it’s important to be able to measure the quality of customer experience, and to understand the demographics and context of customers accessing the services. This enables an enterprise to proactively approach customer care and marketing outreach.
F5’s customer experience reporting graphically maps service response times across the customer base and provides information about service utilization, client response time, server response, and many other parameters. This helps IT managers correctly size service implementation without compromising customer satisfaction. F5 Analytics provides detailed reporting on customer experience metrics and a host of rich reports that assist in server capacity planning and that justify the ROI on new service rollouts by tracking their usage.
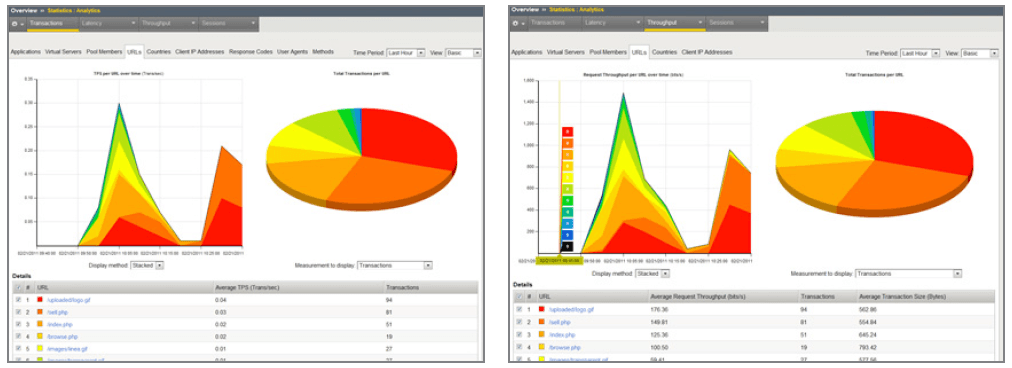
To enable proactive and differentiated customer service and outreach, it is important to understand the context of customer access. F5 technologies take into account the environment and conditions such as customer location, customer device, and the service he or she is trying to access, as well as the customer’s profile to enable the provisioning of a customized service. For example, if a high-net-worth customer from China is accessing a luxury goods portal via an iPad, the F5 solution would direct him to a premier content server that can deliver the page optimized for his iPad.
F5 solutions include technologies such as content switching and context-aware access policies. F5’s unique embedded geolocation service and its industry-leading iRules® scripting language enable network managers to easily set up customer- or application-specific policies to provide a differentiated experience. In addition, the F5 iControl® API enables third-party software providers to interact with F5 solutions, so they can activate services based on external events.
In a globalized environment, businesses must be able to introduce a new service quickly to maximize workforce productivity and minimize time to revenue for that service.
F5 helps organizations cut deployment time with:
Using these tools, organizations can reduce application deployment times by up to 84 percent—a time savings of almost two months.
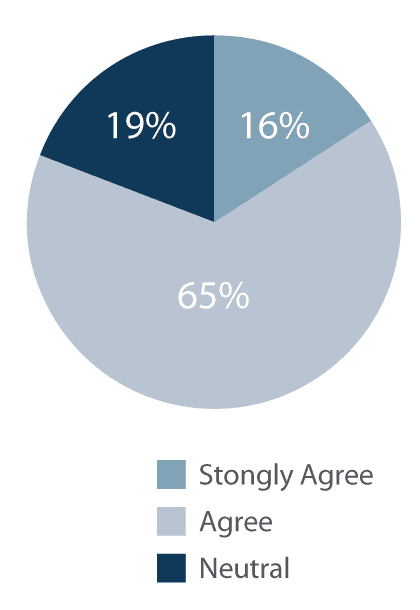
Do you agree with the following statement: “I can respond more quickly to changing business needs after deploying F5 BIG-IP.”
Because enterprises are increasingly adopting the cloud as a cost-effective application delivery platform, CIOs need to strike an effective balance between insourcing and outsourcing now more than ever. While cloud adoption offers the ability to scale resources on demand, it also brings challenges around manageability and security.
Data center consolidation has become a necessity as enterprises globalize and are looking to make the most of their IT investments. As virtualization becomes a mainstream technology, enterprises can realize greater savings than ever with consolidation, plus increased capacity, not only in data centers but also in application workloads, network devices, and servers. F5 offers a comprehensive solution that helps organizations get more out of their virtualization investments, offering scale-on-demand capabilities and service resiliency.
F5 enables organizations to get more out of the virtual environment by providing the ability to offload CPU-intensive operations such as SSL termination, caching, and compression from the server to the F5 solution. For example, F5 offloaded 40 percent of the CPU load for Microsoft Exchange. This enabled servers to handle approximately 60 percent more virtual machine capacity on the same physical x86 servers. For SAP infrastructure, F5 achieved a 30 percent decrease in CPU load, which increased the VM density per server by up to 40 percent, producing greater savings and improved ROI.
F5 solutions optimize virtual environments. Use the F5 Optimization Calculator to perform a compression analysis.
While offloading is critical to improving VM density on servers, F5’s unified application delivery solutions that are based on a common platform enable organizations to consolidate network point devices and selective functions such as AAA/SSO into a single device. F5 solutions can consolidate advanced ADC functions such as web acceleration, WAN optimization, global server load balancing, application firewall, and application access control on the same software platform. F5 solutions are built to provide carrier-grade performance, even when all modules are running concurrently, unlike any other similar providers in the market (read the 2010 Application Delivery Controller Performance Report for more detail). With multiple functions available on a common platform, organizations can choose the architecture that best meets their business objectives, be it complete or partial consolidation. This also simplifies the manageability of the entire IT infrastructure.
“88% of IT organizations improved VM density between 10% and 40% on a typical server with F5.”
Source: TechValidate survey of 105 F5 BIG-IP users; TVID: 975-FFD-F8D
IT managers today want to be able to ramp up capacity on demand within the data center, especially in a virtualized environment. F5 solutions working with third-party traffic monitoring applications can automatically spin up and down VMs based on changes in traffic volume. F5’s open API, iControl, can integrate with VMware vCenter and other third-party management software to automate the process of adding and removing nodes from a server pool.
In addition to being able to automate virtual machine capacity in the data center, F5 also offers a true “scale-on-demand” solution via the VIPRION® chassis.
With this scale-on-demand solution, organizations pay a lower up-front cost — only the cost of the capacity that is needed today. Organizations can also scale their application delivery solutions in parallel with capacity by simply adding blades to their existing chassis. This ensures that existing capacity is fully utilized and lowers overall operational costs by cutting down on maintaining over-provisioned gear from day one. Over four years, the F5 solution offers up to 30 percent savings in overall cost of ownership.1
With the F5 scale-on-demand solution, enterprises can take advantage of new technologies as they come on stream, such as 40 Gbps ports, faster CPU, and RAM. Rather than doing a forklift change of an aging solution based on software throughput upgrades, organizations can take a chassis-based approach to scaling and reap the full benefits of the new technology.
“55% of IT organizations reported that the ability to redirect, split, or rate-shape application traffic between multiple data centers is valuable when choosing a cloud provider.”
Source: TechValidate survey of 109 F5 BIG-IP users; TVID: 3D4-C64-27A
Complementing the scale-on-demand approach, F5’s Virtual Clustered Multiprocessing (vCMP®) technology enables the consolidation of physical, purpose-built resources into multiple virtual entities on the same device. Each instance provides total segregation from the others, with exclusively allocated CPU, memory, and disk storage. This enables multiple departments, such as HR, finance, and sales, to implement their own application delivery solutions for their custom applications. Redundancy for each instance is offered across blades or chassis, providing complete availability and isolation for multi-departmental applications. Because the instances are isolated from each other, each department can perform upgrades and configuration changes without affecting the whole organization.
F5 extends data center capacity and resource availability by seamlessly virtualizing all application resources—internal and external—and presenting them as a single resource. The pool of resources that provides the capacity to scale an application can be virtual, physical, local, or remote. F5 can redirect users to additional resources that provide capacity on demand. When demand decreases, the resources are released, helping to reduce costs for customers who have adopted a pay-per-use model. The F5 solution understands the network and application contextually in real time and can determine the best resource to deliver the request, ensuring high availability for applications delivered from the cloud.
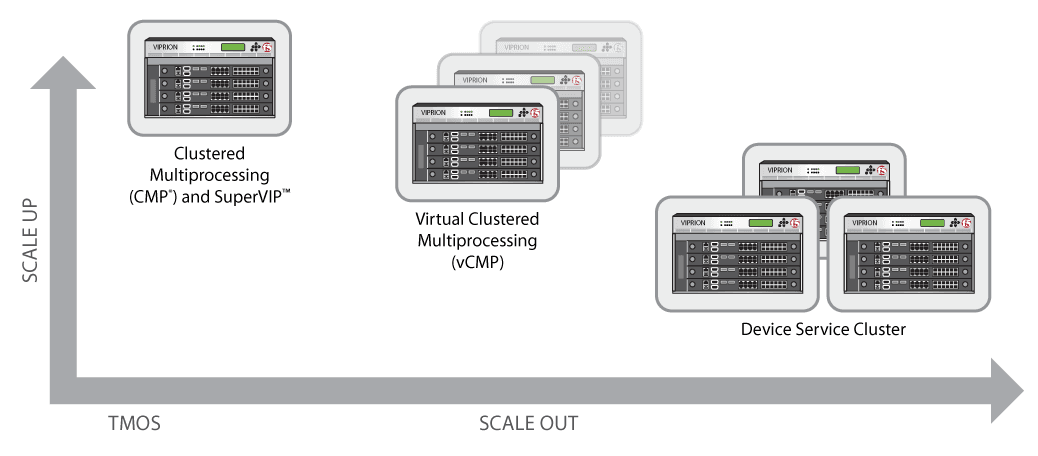
F5’s N+1 clustering solution, ScaleN,™ enables multi-way clustering among devices to create a pool of application delivery services that is both elastic and highly resilient. It allows multiple active devices to look like one solution, and can distribute load across Application Delivery Controllers on an application-by-application basis.
This brings a new level of innovation to the application delivery industry by enabling application services to fail over between physical and virtual ADCs, so organizations can maximize investments while providing maximum availability. ScaleN offers:
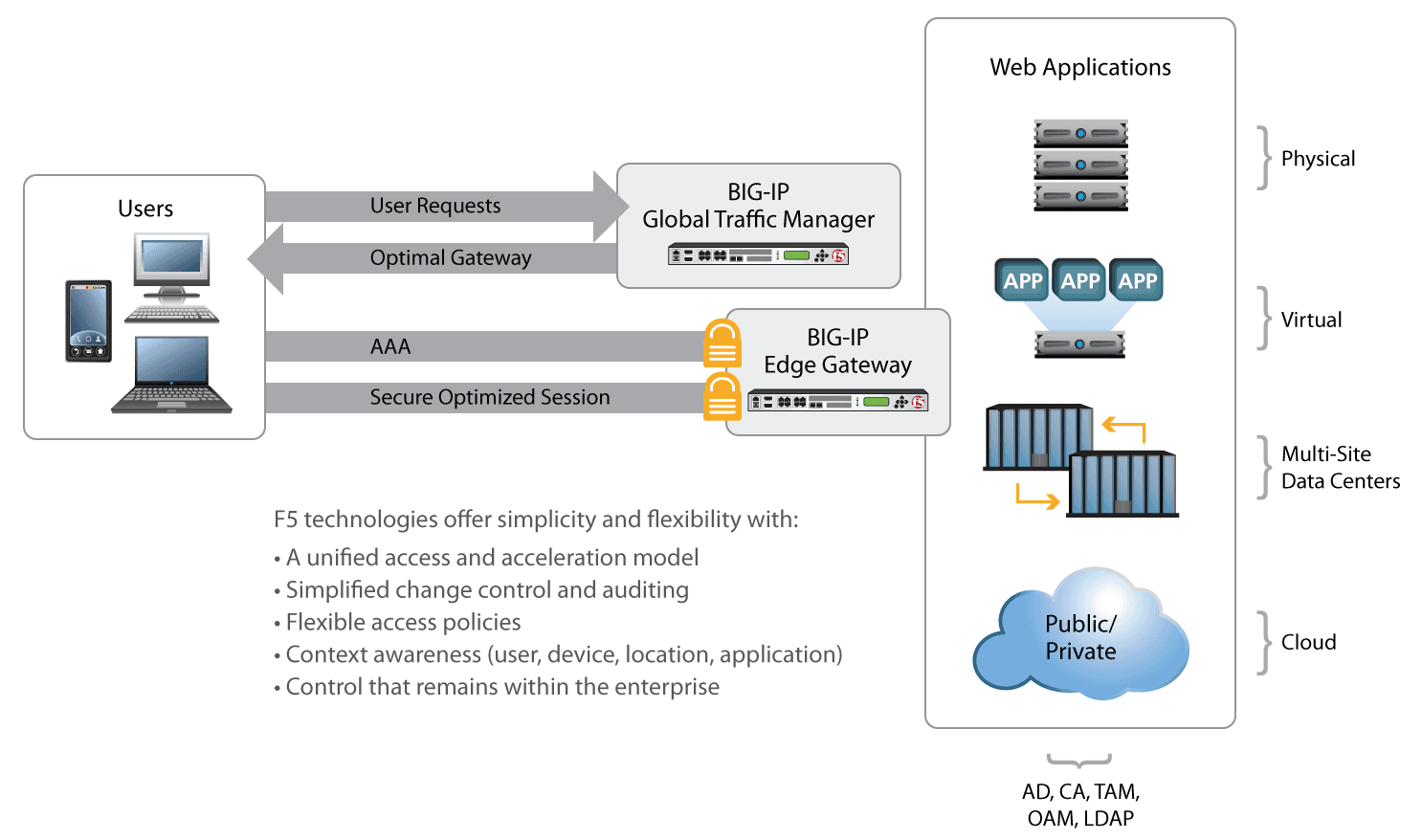
Whether an application is in the enterprise data center or hosted by a cloud service provider, users should be able to access it transparently and securely. F5 secure access solutions provide a single point of control in the enterprise data center from which to manage user access. All user access can be authenticated via the F5 secured gateway within the enterprise; and upon successful authentication, users can be authorized to access any application service either from the data center or the private/public cloud environment. A broad set of authentication services—including Active Directory, LDAP, RADIUS, and native RSA SecurID—ensures strong enforcement of access policies.
F5 solutions provide simplified user access and strong security by federating the authentication at a single location for both enterprise and cloud resources. This eliminates the need to manage multiple point solutions for security and access control, resulting in considerable cost savings and simplified management.
IT managers must be ready for the unexpected, especially when there are so many new industry and government rules concerning data protection and disaster recovery. F5’s comprehensive set of solutions helps organizations achieve business continuity, disaster recovery, and consolidation goals. To provide dynamic data center availability, recovery, and continuity, and to meet SLAs while controlling infrastructure cost, organizations must consider many requirements during the ADN design and deployment phases.
F5 availability and disaster recovery solutions add flexibility, adaptability, and security to the network, so users always have access to applications and data—even if service to the primary data center is interrupted due to natural disasters, system outage, or DNS DDoS attacks. F5 solutions transparently direct users to the closest or best-performing data center available to ensure that users receive the best experience possible when interacting with business applications.
For sites that maintain content in different languages, geographic load balancing ensures that users around the world get the information they need in their own language. With advanced monitoring at the application level, users can be directed to the data center that will optimally deliver the application for each individual.
F5 global traffic management solutions allow organizations to build an active-active data center architecture that maximizes its utilization. F5 solutions provide automated failover to the secondary data center in case the primary data center fails. This solution not only maximizes the use of the usually idle secondary data center, but also eliminates the need for manual failover operations, providing both OpEx and CapEx savings.
Managing risks to the IT infrastructure is part of running any business these days. Regardless of the business, understanding and managing IT risks helps increase network infrastructure and application security, reduce management costs, and achieve greater compliance posture. Failure to identify, assess, and mitigate IT risk sets the business up for serious security breaches and financial losses down the road. Regulations continue to increase, placing additional costs on organizations. In addition, the risk of natural disasters and physical attacks that can bring a data center down for days. When it comes to managing and mitigating IT risk, three major areas need to be considered:
F5 offers a full range of solutions that provide built-in security to help organizations achieve compliance with regulatory requirements such as:
F5 provides a PCI compliance report detailing requirements and recommendations to bring an application environment into compliance. The PCI Compliance Report lists each security measure required to comply with PCI DSS v2.0 and shows, at a glance, how each item in the report compares to the PCI security criteria.
FIPS compliance is also a key feature of F5’s regulatory compliance framework, enabling F5 solutions to be deployed for highly sensitive government environments. F5 provides a range of other solutions that help organizations comply with various regulations and conform to industry standards such as PCI, ICSA, FIPS, and HIPAA. F5 BIG-IP® devices provide a set of pre-built application security policies that enables out-of-the-box protection and compliance. The validated policies require zero configuration time and serve as a starting point for more advanced policy creation.
Ever-evolving cyber threats have led to dramatic change in the security landscape. F5’s comprehensive data center security solutions offer a welcome reprieve by addressing such attacks through combined network, application, and access control for physical, virtual, or cloud environments. There are many benefits that come from designing and deploying an integrated solution that offers network, application, and access control in a consolidated package.
Based on F5’s TMOS® operating system, F5 solutions consolidate all functions necessary to deliver applications to users, such as network infrastructure, DNS, web application access, user-based security policies, and even data center firewall functionality.
F5 makes the only integrated ADC to offer an ICSA Labs certified data center network firewall in a scalable security platform that can support up to 192 million concurrent connections and up to 320 Gbps of throughput on top of the industry’s fastest application firewall solution, exceeding other solutions’ performance by 10x. In addition, F5’s remote user access solution can support up to 60,000 users concurrently on a single platform.
DNS cache poisoning and other DNS attacks can compromise your DNS infrastructure, potentially bringing down corporate web services. F5 takes a holistic approach to DNS security that enables organizations to deploy DNSSEC quickly and easily into existing multi-site environments. The solution is enhanced by combining this with a unique high-speed query capability (>10 million query/sec) that shields primary DNS servers from DNS DDoS attacks. With the upcoming DNS caching technology, F5 provides the industry’s most complete DNS protection for any enterprise wanting to protect their web presence.
F5 delivers comprehensive vulnerability assessment and application protection that can quickly reduce web threats with easy geolocation-based blocking, greatly improving the security posture of an organization’s critical infrastructure. These assessment solutions include integration with IBM Rational AppScan, Cenzic Hailstorm, QualysGuard Web Application Scanning, and WhiteHat Sentinel, building more integrity into the policy lifecycle and making it the most advanced vulnerability assessment and application protection on the market.
F5 security solutions bring the network, applications, data, and users together under a single security strategy that protects against rapidly evolving threats. F5 provides the intelligence and flexibility needed to stay secure in the ever-changing and increasingly threatening landscape.
The strength of the technology and the immediate and long-term benefits of a given solution are significant factors when choosing a technology vendor. But beyond that, it is also important that the vendor has a credible and strong support infrastructure in place.
“74% of F5 BIG-IP customers considered advanced local load balancing methods to be an important feature of virtualized infrastructure.”
Source: TechValidate survey of 277 F5 BIG-IP users; TVID: 4DA-319-804
Global and local support infrastructure, as well as remote technical support from vendors, are crucial for solutions that deliver mission-critical business applications.
F5 has global, comprehensive support infrastructure:
A true testimony to a vendor’s solution awareness and strength is the robustness of the community and the partner ecosystem. The F5 DevCentral community portal boasts more than 100,000 members, including customers and developers, making it the largest in the industry. It also serves as a platform to share iRules, iApps, and deployment and solution guides, as well as to have discussions around F5 solutions. To complement this enormous following in the portal, F5 has a strong ecosystem of technology partners, which includes an array of ISVs such as VMware, Oracle, Microsoft, and SAP, and global SIs like HP, IBM, Dimension Data, and Dell. To support this ecosystem, F5 has established a global network of distributors who act as value-added partners between F5 and its ecosystem of resellers (locate an F5 Partner).
Finally, the ultimate recognition of the acceptance of any vendor is the strength of the installed base and vision that translates to market share and recognition from leading industry analysts. According to Gartner and IDC, F5 is ADC market share vendor leader.
Applications are the heartbeat of any business and therefore it is crucial to ensure that they are fast, secure, and available for an enterprise’s employees and suppliers. To meet such demanding requirements, it is vital to put in place a robust, reliable, and flexible application delivery solution. Designed from the ground up for application delivery with purpose-built hardware and software, F5 application delivery, optimization, and security solutions provide complete application management across any data center, whether on- or off-premises.
When choosing an application delivery vendor that sits in a critical path for production applications, it is important to look beyond the marketing hype and closely examine the ability of the vendor to deliver reliable and innovative solutions that meet business requirements today and into the future. The solutions must be able to address the key pain points and concerns for the infrastructure and support lines of business. Assessing vendors’ capabilities across multiple dimensions such as technology, solutions, support, community, and market leadership evidence is critical to building a complete, scalable application delivery solution.
1 Based on the analysis of comparing F5 VIPRION with the nearest pay-as-you-grow solution from a competitor over a four-year period.
2 F5 is currently in the process of submitting for the EAL4+ certification.
PUBLISHED AUGUST 27, 2012