Cybersecurity Trends Impacting Public Sector Agencies
FACED WITH THE GROWING THREAT of malicious attacks, public sector agencies have been diligently working to address their highest risk security challenges. And as cybersecurity technology, frameworks, and standards continue to evolve, they must constantly strengthen their security posture to keep up. So what cybersecurity developments are driving investments in the public sector? Consider the following three trends:
TREND #1
Security, Orchestration, Automation, and Response (SOAR)
WHAT IS IT?
A term coined by Gartner, SOAR encompasses threat and vulnerability management, security operations automation, and security incident response, so organizations can collect threat-related data from a range of sources and systems and respond to low-level threats without human intervention.
WHAT’S THE IMPACT?
Organizations already investing in SOAR are seeing compelling results, as noted in the chart below.
SOAR Benefits

WHAT’S THE CHALLENGE?
An effective SOAR strategy requires a robust security approach that includes collecting threat-related data from a range of sources and systems and responding to that data with little human intervention.
WHAT CAN YOU DO?
Look for security solutions that deliver automated detection, mitigation, and analytics. Machine learning and other AI techniques enable the system to learn from historical or similar traffic patterns and provide insight into exactly what's happening.
TREND #2
Zero Trust: Trust Nobody, Protect Everywhere
WHAT IS IT?
While Zero Trust has been around for a decade, it’s taken on new urgency as more public sector employees work from home during the COVID-19 pandemic. With bad guys constantly plotting new ways to gain access to target networks, “trust, but verify” is giving way to “trust nobody, protect everywhere” (or Zero Trust).
WHAT’S THE IMPACT?
Governments need to rethink the traditional network perimeter to achieve enhanced security. To enable Zero Trust, they must abandon the “trust, but verify” approach and follow these three principles: never trust, always verify, and continuously monitor.
Zero Trust Benefits

NEVER TRUST

ALWAYS VERIFY
CONTINUOUSLY MONITOR

WHAT’S THE CHALLENGE?
The big challenge with Zero Trust security is preventing unauthorized access without making things harder for legitimate users or increasing the IT burden for government agencies.
WHAT CAN YOU DO?
Choose the right access management and authentication technology. For example, a large U.S. federal agency used its existing F5 BIG-IP platforms to enable Zero Trust. Having a large number of F5 devices deployed within its network (2,500 in this case) transformed what can be an arduous process into a seamless one.
TREND #3
Adoption of Government Security Guidelines
WHAT IS IT?
With evolving threats, many agencies are embracing government security guidelines, such as the National Institute of Standards and Technology (NIST) and the Defense Information Systems Agency (DISA) in the U.S. or the Network Information and Security (NIS) 2 Directive in Europe. These powerful cybersecurity standards assist in identifying and implementing the appropriate measures to protect critical systems and data from cyber threats. For example, legislation introduced in U.S. Congress would require federal agencies to begin migrating their IT systems to NIST post-quantum cryptography standards designed to protect sensitive information in the age of quantum computing. Standards can also guide a proper response and recovery from cybersecurity incidents.
WHAT’S THE IMPACT?
Security vulnerabilities associated with new app development and modernization processes can lead to successful attacks and abuses against agencies, resulting in a loss of constituent and employee personally identifiable information (PII), state and military secrets, and money.
Top IT Technology Initiatives
Which of the following technology initiatives is your IT organization prioritizing over the next 12 months?
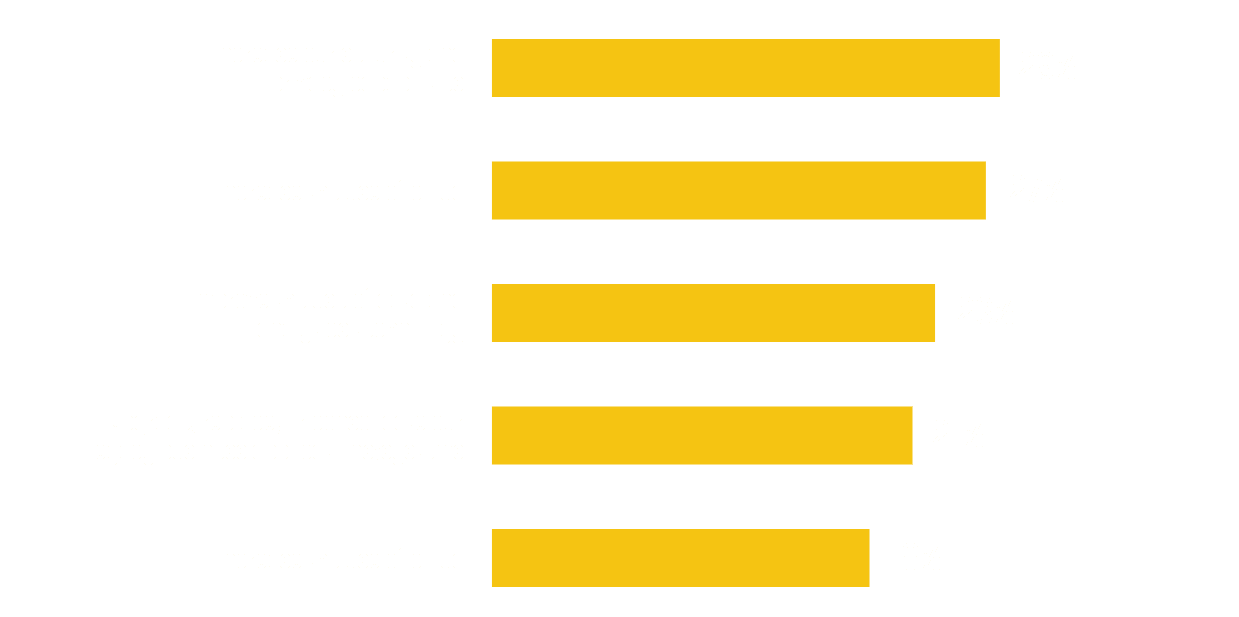
( Forrester Infographic: The State of Digital Transformation in Government 2021 )
WHAT’S THE CHALLENGE?
As highlighted in the above Forrester chart featuring agency respondents, there are many competing IT priorities. Even when increasing security and privacy capabilities is the number one priority, other important initiatives still pull funding and resources away. Balancing these initiatives can be extremely challenging.
WHAT CAN YOU DO?
Look for cybersecurity solutions that simplify the protection of your most valuable assets and comply with the latest government security guidelines.



