Recent years have seen significant increases in the availability of network-enabled devices. Anytime, anywhere access makes it feasible to network all manner of things, from critical health-monitoring devices and autonomous vehicles to thermostats, fitness trackers, and even water bottles. And the rush of new Internet of Things (IoT) devices has only just begun.
Sensors along a gas pipeline. Under-the-skin blood sugar monitors. Security and surveillance systems. Vehicle, cargo, and package tracking. The world of smart devices talking to each other—and to us—is already a reality. The impact of the IoT—and the vertically focused Industrial Internet of Things (IIoT) in manufacturing, healthcare, transportation, and many other industries—is on the rise. However, reaping the business rewards of the IoT and IIoT will depend on our ability to design and build a networking infrastructure, which successfully manages and secures the flood of data that comes with adding ever more things to the IIoT.
Whether you’re a service provider or an enterprise IT department, you’re likely already having to respond to the explosion in connected devices, applications, and data that come with the growth of the IoT and IIoT. Just as “bring your own device” transformed the workplace and enterprise mobility—not to mention subscriber expectations for faster, more reliable access to apps—the IoT will affect almost every aspect of our daily lives.
In some industries, progressive businesses are already using the IIoT to enhance customer service, improve use of field assets, reduce manufacturing and shipping delays, and much more. With IIoT solutions, business operations and manufacturing leaders are becoming reliant on the data generated by things—and acted on by increasingly smart systems, which perform millions of decisions each day. As a result, IIoT enables new business models and a renewed focus on critical factors such as productivity, agility, efficiency, and safety.
However, the growth of the IIoT does come with its own set of challenges, including threats to devices, data, and physical infrastructure; unproven regulations and ill-defined standards; and poorly implemented privacy, encryption, and authentication policies. These and a host of other issues remain largely unaddressed, and we see early signs that the IIoT could become commonplace before robust solutions have been fully established.
These concerns are not so different from the ones that recently surrounded the cloud. In this case, consumer devices are the focus, and service providers must work to find new ways of driving greater operational efficiency and better management of infrastructure—for themselves and their customers. The challenge in harnessing this powerful force isn’t just in managing a distributed infrastructure that mixes physical and virtual entities to produce an enormous volume of data; organizations must also make sense of that data in order to prioritize traffic and optimize the application architecture itself.
The size of the IoT market and the growing number of new devices is likely to surpass anything we’ve seen. The consequences of these devices and their supporting ecosystem failing vary from simple annoyance to significantly disarming, such as a security breach that targets users’ payment information. Accordingly, the underlying network infrastructure that connects, manages, monitors and monetizes these devices and securely transports their data will require considerable attention.
By definition, the Internet of Things refers to the set of devices and systems that connect real-world sensors and actuators via the Internet. But in actuality, this includes many different types of systems, including the following:
Throughout this range of IIoT systems, connections are generally classified as M2M (machine to machine) or M2P (machine to people). And in both cases, these systems connect to the Internet or gateways in the same ways traditional devices communicate, plus more. This includes long-range Wi-Fi/Ethernet using IP protocols (TCP/UDP, including cellular); short-range, low-energy Bluetooth; short-range near-field communication (NFC); and other types of medium-range radio networks, including point-to-point radio links and serial lines.
Across this array of options, some devices connect via standard IP protocols like IPv4/IPv6, while others require more specialized, data-specific protocols built for the IIoT. Some protocols, like Message Queuing Telemetry Transport (MQTT) and Advanced Message Queuing Protocol (AMQP) don’t use HTTP but remain TCP/IP based, while others, like Constrained Application Protocol (CoAP) seek to minimize the impact of HTTP by optimizing a subset specifically for M2M communications.
MQTT is one of the most commonly used protocols and can be found across a range of modern IIoT solutions. Originally developed by IBM, this publish/subscribe messaging protocol was created specifically for lightweight M2M communications and is now an open standard. Under publish/subscribe systems, information providers (publishers) do not link directly to individual consumers of that information (subscribers). Instead, interactions between publishers and subscribers are controlled by a gateway or receiver (called a broker). In this way, a device is able to send a very short message to an MQ broker, and the broker conveys that information to other devices. In this model, clients (e.g., actuators) subscribe to various topics and when a message is published to that topic, they receive a copy of that message (see Figure 1).
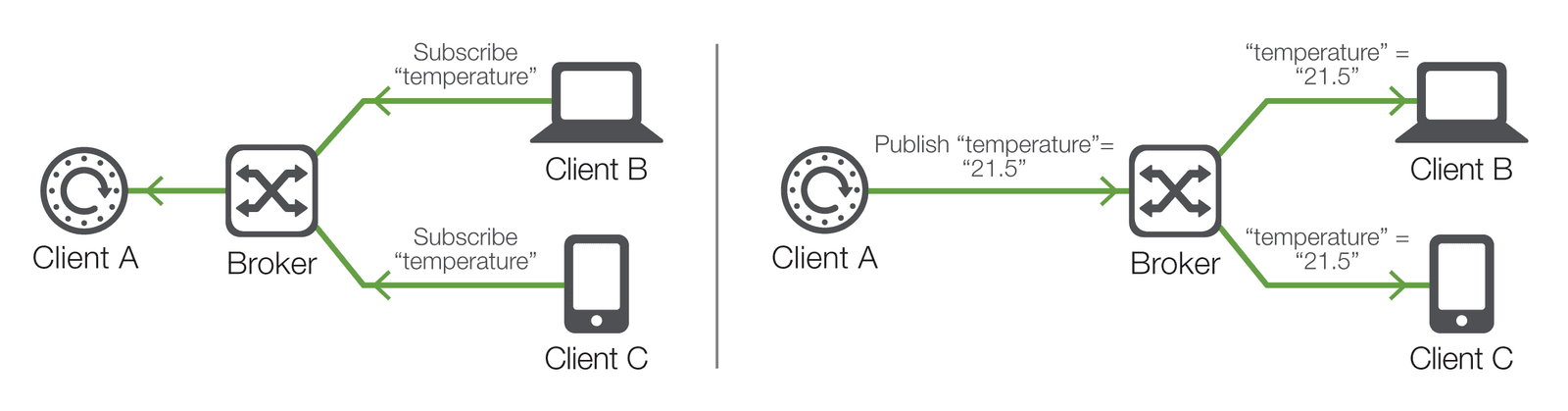
As you can see, this model allows MQTT clients to communicate (via broker) one-to-one, one-to-many, and many-to-one. Naturally, clients can include everything from simple switches to smartphone apps. This is the case with a connected warehouse thermostat, for example, where the site manager communicates with the thermostat via a mobile app (sending instructions and receiving real-time and historical temperature readings) via MQTT over the site’s TCP/IP network. (For a more technical examination of MQTT, please see “F5 BIG-IP MQTT Protocol Support and Use Cases in an IoT Environment.”)
No single architecture addresses all the potential IIoT devices and their requirements, which is why it is critically important for service providers and enterprise IT organizations to deploy scalable architectures that can add or subtract resources in order to support a wide variety of scenarios, now and in the future.
Estimations of the number of connected devices and the quantities of data they’ll transmit vary, but there is no doubt that the numbers will be huge:
As more applications are needed to run all these things, traditional infrastructure concerns such as scale and reliability will become ever more critical. On top of that, additional challenges around identity and access, improving the end-user or subscriber experience, and the need for faster provisioning of services could overwhelm IT departments. It’s clear that the world needs a robust, scalable, and intelligent infrastructure capable of handling the massive traffic growth coming in the near future.
As recent attacks have shown, the IoT has the potential to create vulnerabilities in the entire system, making security more challenging—and also more important—than ever before. In perhaps the most infamous example of IoT security flaws, in 2016 KrebsOnSecurity suffered a then-record 620 gigabit-per-second DDoS attack executed by Mirai, a botnet of thousands of disparate routers, cameras, and other IoT devices. Then, months later, a competing (and far less malicious) botnet known as Hajime infected at least 10,000 devices, issuing commands and updates to infected devices in order to defend them against the likes of Mirai. While these well-documented attacks focused on poorly secured devices such as CCTV cameras and consumer tech, the implications for the IIoT are significant. A similar such attack, even on a smaller scale, could potentially have very severe impacts if it were to gain access to a working IIoT environment. (For more details on developing threats to the IoT, download the full threat analysis report from F5 Labs.)
Unsurprisingly, outpacing attackers and minimizing risk in this threat landscape requires significant resources. Service providers and enterprise IT organizations alike need to continue to harden their own infrastructures and look to cloud services like DDoS mitigation to lessen the effects of attacks. To ensure robust security, intelligent routing, and analytics, multiple networking layers must be fluent in the languages that devices use. Understanding these protocols within the network enables traffic to be secured, prioritized, and routed accordingly (see Figure 2).
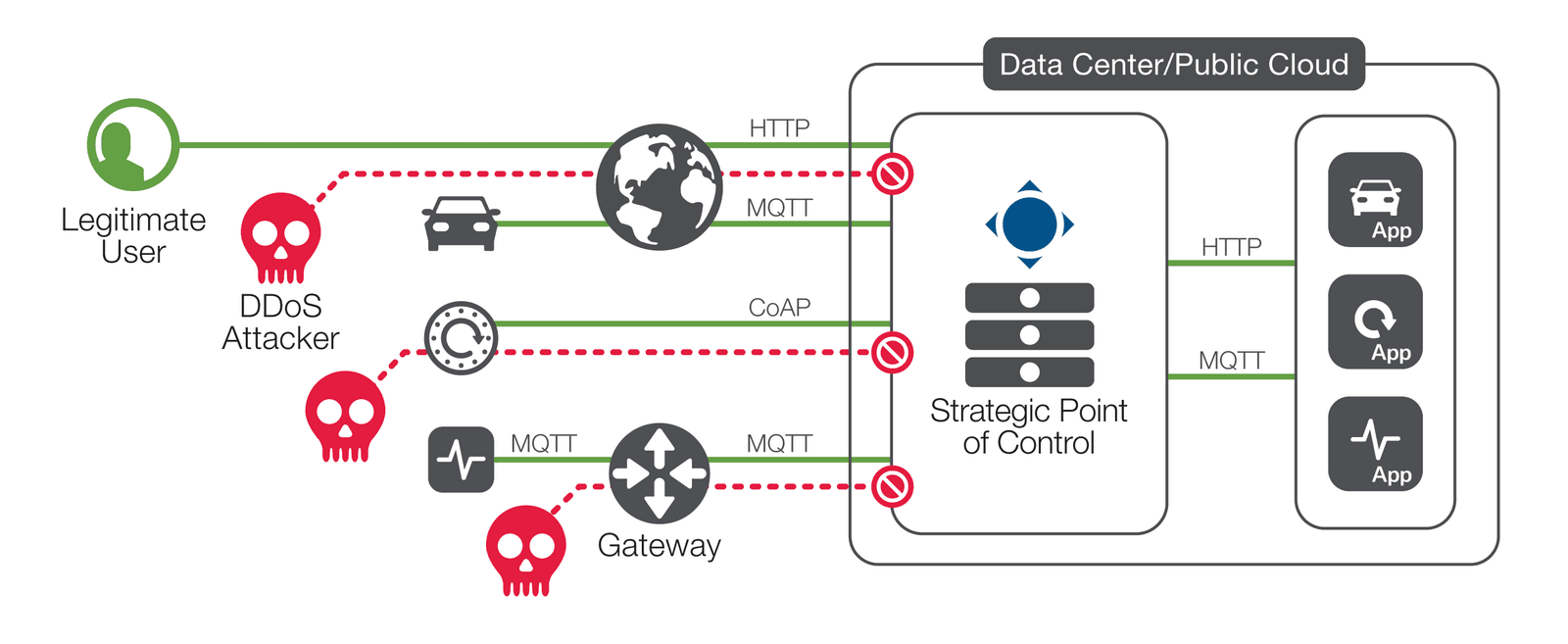
Ultimately, ensuring the high availability of IIoT services relies on robust automation, management, and orchestration capabilities. Good network management must underpin business continuity to mitigate risk and prevent potential losses. From a project-planning standpoint, monitoring capabilities that enable organizations to watch network growth and quickly allocate resources are critical to meeting the ever-increasing demands from IIoT devices.
PUBLISHED JULY 21, 2017