At the Battle of Thermopylae, so the story goes, Leonidas and his band of three-hundred Spartans were defeated not because of the expected frontal assault. No, it was because the Persians snuck around and out-flanked them thanks to a narrow goat path that gave them a foothold behind Spartan the line defending the Hot Gates*.
It was a strategic error, perhaps, to not protect the less obvious attack route of a goat path. Hindsight is 20/20 and with it we can now see that failing to guard every potential entry point can prove devastating.
So have we learned from history, or are we doomed to repeat it?
Based on the results of our State of Application Delivery 2018 survey, we’re trying our best to repeat it.
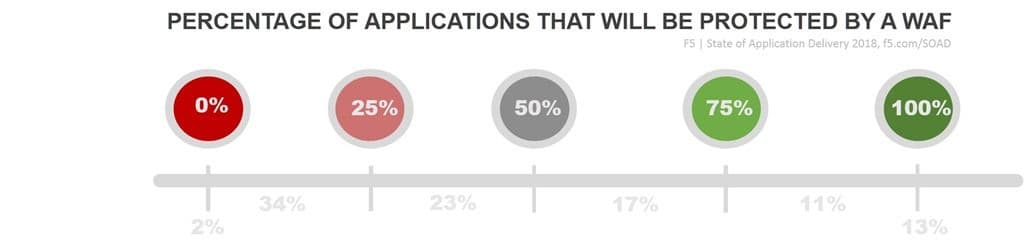
What this chart shows is that 2% of organizations are using a WAF to protect … nothing. None of their applications are protected by the technology. Conversely, 13% of organizations are protecting all of their apps (100%) with a WAF.
Somewhere in between lie the bulk of organizations, with 34% protecting a quarter or less (1-24%) of their applications. Those apps are likely akin to the Hot Gates. They are the most visible, the ones you promote and advertise. They’re the ones that see the most traffic and are, logically, the most likely route of attack.
The rest are goat paths. Narrow, overgrown trails into the data center that are rarely used and least likely to come under attack. Or so you hope.
As an industry we tend to talk in terms of “critical” applications. These are the apps that business needs to operate every minute of every day. That’s your CRM, your SFA, your online store, the APIs your partners use to send you business. These are the ones we talk about with reverence. You need to protect them from attack, scale them to meet demand, and improve their performance so even the most demanding of consumers will be delighted by your attention to the user experience.
We tend to ignore the ‘non-critical’ applications. Sometimes we even shove them off in a public cloud somewhere without regard for setting up the security checkpoints they need to keep data and credentials safe.
Today I’m saying that like that goat path that turned out to be such a critical entry point into the Spartans defenses, so are all those ‘other’ applications. If they connect to the Internet – and by virtue of connecting to a network, they probably do – they are a potential entry point for attackers. If they take advantage of the same platforms and protocols as your ‘critical’ apps – and they probably do – then they are a risk to every application because they share the same vulnerabilities.
All it takes is one, narrow path into the network through any application to put the entire organization (the business) at risk. Gaining a foothold on one application or server opens up a wealth of avenues for attackers to explore. From credentials to connections, a single point of attack inside the data center (whether public cloud or on-premises) is a greater threat than we like to consider.
There is no reason to ignore ‘non-critical’ applications when it comes to security, and in fact there are a hundreds, perhaps thousands, of good reasons to pay attention to them and provide the protection afforded by a WAF. Employee credentials. Personal data. Routes to other, juicier applications and services.
There is no such thing as a non-critical app when it comes to security.
Don’t ignore the goat paths in favor of the Hot Gates.
*Yes, the Persians likely would have won anyway, but now we’ll never know, will we?
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
