We are, I think it’s safe to say, universally delighted by technology. The mundane is transformed into the magical by the mere introduction of technology. The novelty wears off after a time, of course, but by then there’s some other task that has been made controllable via device or phone and the cycle starts again.
The reality is that most people don’t manage their (growing array of) devices like IT manages systems. Not even IT people. Remember that Tripwire survey that found “thirty percent of IT professionals and 46% of workers polled do not even change the default password on their wireless routers”? That’s slightly higher than research discovering that “forty percent of Americans said they were too lazy, found it to be too inconvenient, or they didn’t really care…”5 about following basic security recommendations.
It should be no surprise then, when hounded by security professionals and beaten about in the trade press, that at least consumer-oriented IoT manufacturers seem to be stepping up their game. Automatic updates, patches, and hotfixes can be streamed regularly to connected devices with checkbox simplicity.
Consumers, at least, are ceding control to manufacturers who promise to keep their devices safe from attackers.
Now, that’s the consumer space. Thus far, this kind of behavior seems to be off-limits in the enterprise, even where IoT devices are concerned. Surely enterprises will continue to maintain control over such things for the foreseeable future. After all, the blast radius from an update gone bad is pretty significant inside the data center.
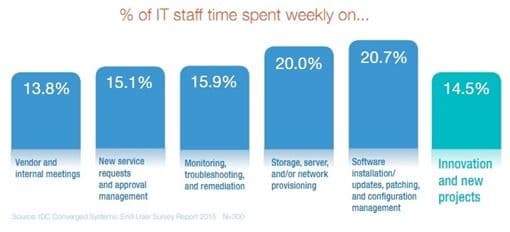
Except that doesn’t scale, and we know full well from our own research and peeking at Shodan.io that a pretty hefty percentage of IoT devices inside organizations are not only exposed to the Internet, but vulnerable.
And if they’re vulnerable, that means there should be (maybe is?) a patch available. Yet if both of those were true, wouldn’t we see fewer devices available for recruitment as a thingbot?
Given an IDC study two years ago that pegged patches, updates, and installs as consuming 20.7% of the week for an average IT staffer, it doesn’t seem possible that they’re going to scale – even with automation – to managing the predicted doubling of devices (from 9259 devices today to 18631) over the next two years.
So what’s the business to do?
The question we have to answer is do we encourage manufacturers to go the distance and auto-update their devices that reside inside the enterprise? Because it’s kind of unfair to blame them without acknowledging that patch fatigue and lack of staff may be preventing those patches from being applied in the first place. As some other interesting research from Tripwire noted, “In 2015, over 6,000 new CVEs were assigned. If only one-tenth of those vulnerabilities affected devices in your area of responsibility, you would have been responsible for resolving 630 vulnerabilities annually or 2.5 vulnerabilities each business day.”
That’s a lotta vulnerabilities to address. A lot, a matching number of patches.
Sadly, just because a patch is issued doesn’t mean it’s applied right away. As noted by the Tripwire survey, “One key component affecting the amount of time needed to deploy patches is testing. Respondents were asked if they tested patches before deployment, and 47 percent said they did for desktops and 55 percent for servers.” When you dig into the details about how long it actually takes to get a security patch into production, you’ll find some alarming data. To wit, 93% of respondents get security patches tested and deployed in less than one month.
Not too shabby, given the number of systems and corresponding vulnerabilities a typical mid to large enterprise is dealing with.
But consider for a moment that when CVE-2017-8225 – affecting a single Chinese manufacturer of IP cameras – was announced, it took less than two months for over 600,000 of the cameras to become infected with Persirai. That’s 10k devices per day. Which means a month is a month too long. And that was only one vulnerability.
As IoT invades the enterprise in the forms of more sensors and monitors and who knows what that are accessible and often vulnerable, how does IT keep up? Can it keep up, even with automation on its side?
So my question really is, would you? Would you cede control over IoT devices if (and I realize that’s a big if, but play along for the sake of discovery) manufacturers stepped up and shouldered more of the responsibility for maintaining the security of their devices?
You can answer that question (and see what your peers think) here. Go ahead, sound off!
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
