I’ve never been a fan of predictive articles. Mostly because I’m not actually prescient and thus like everyone else, I’ve got a 50/50 chance of being right – or wrong. And like most people, I don't like to be wrong. But this year I’ve got responses from over 3000 enterprises across the globe spanning every industry to help me figure it out. That helps, a lot.
Even without that data, a lot of predictions aren’t actually all that hard to make and get right. That’s because they’re either following a predictable technology cycle or there’s a pile of data that pretty much points to the inevitability of the prediction being true.
With that in mind, I decided to actually put down in digital ink what the data and technology cycle is showing will be pretty much a given in 2018.
- More cloud
Come on, it’s been steadily growing for years. You can’t go wrong betting that cloud will continue to gain workloads. Interestingly, though, we are seeing the inevitable slide toward public (IaaS) cloud finally picking up steam. With the bulk of commodity workloads moved to SaaS and private (on-premises) cloud taking on performance and security sensitive corporate apps, enterprises are starting to eye up public (IaaS) cloud with greater enthusiasm. Digital transformation is certainly a factor, and as organizations complete their internal transformation (automation, orchestration, digital enablement for productivity purposes) you can bet they’re going to start consuming public (IaaS) cloud with greater ferocity than in the past.
- More security breaches
It’s not just our own research that shows an increasing frequency of successful breaches. It’s just about everywhere. The number of breaches we saw in 2017 was incredible, and there are no signs it will slow down. The growth in bot traffic alone points to a significant army camped just outside the gates, and it would be foolish to think that there will not be an equal number or more of alarming security breaches in 2018.
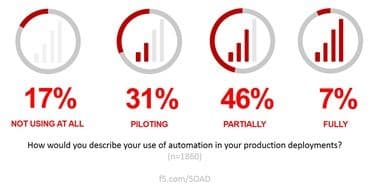
- Because we aren’t done. While we’re seeing more automation and orchestration of IT, we are nowhere near “saturation” yet. Like cloud, if you’re just starting out automation is easy. But for the hundreds of thousands of enterprises who have a whole lot of technical baggage to sort through, automating IT to prepare it to handle the pressure from digital transformation and DevOps isn’t something you do overnight. It’s full steam ahead, though, so expect to see a lot more of it in 2018 as orgs begin to really employ emerging best practices to get IT executing with the same alacrity as startup dev teams.
- More container scalability options
The war for container scalability has already begun, and 2018 will no doubt see it escalate. While the initial answer to scale inside container environments was admirable, it was short term and doomed to be replaced. The good news is that the architectural design of container orchestration environments (COE) is magnificent and well-suited for supporting more mature approaches to scale. The service mesh will replace the default, IP table-based methods included with COE distributions as organizations put these environments into production and expose shortcomings of large-volume scale. And they are putting them into production, not only in the public cloud but in the data center. That’s evident in the rising demand for app services in a container form-factor we see in our latest survey. - More IoT failures
One of the other data points from our State of Application Delivery 2018 (watch for it in January) that was interesting is the appearance of IoT in the “Top Six” strategic trends. It moved up to number six, displacing mobile applications and joining all the clouds. That (and some other data points I can’t share just yet) leads to the inescapable conclusion that there will likely be a lot more IoT being deployed. Sadly, that also likely means more IoT failures. Not just of the devices, themselves, which are often at risk of being conscripted into the growing Death Star-sized botnets, but of the applications that manage, monitor, and often control them. Emberlight was one of the latest proof points in this caveat emptor market, when it closed its doors (and shut down its apps), leaving its customers literally in the dark. Seriously, their smart sockets for light bulbs required a connected app that is no longer available.
So there you have it. Five take-to-the-bank predictions based on years of watching technology cycles wax and wane and the responses from over 3000 folks in the trenches (and some running the show).
With that, I’m signing off for the year, and we’ll catch you on the flip side in 2018. Have a wonderful holiday season, and a very Happy New Year!
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
