Our youngest is nine (AND A HALF! DON’T FORGET THE HALF!) and he’s currently enthralled with robots. Not just playing with them, but programming them. With both parents holding advanced degrees in computer science, you can image we’re thrilled and encouraging of this particular trend.
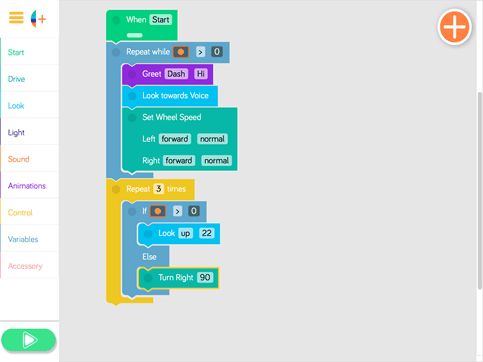
So of course robots that offer easy-to-learn programming models is a thing in our house right now. One of the toys for this summer was from Wonder Workshop, whose robots can be programmed via a “block” like language.
This is the norm for kids today. This child plays with a number of ‘games’ on his various devices, all which use the same “block” like model for constructing programs. Even his Lego Mindstorms Ev3 robot uses a similar mechanism, where programming constructs are blocks you wire together. Variables and conditions are set by selecting them, and there’s no actual “code” displayed on the screen.
But you know it’s there.
Back in the day when I was evaluating BPM (Business Process Management) solutions, they used a similar paradigm to enable business stakeholders to define processes. Its interface reflected the nature of processes, which is to say you built a flowchart using a drag-n-drop model, but much of the construction of the orchestration was accomplished via an easier-to-learn interface. Like those my youngest uses today, only more Visio like. A lot more Visio like now that I think about it.
Forget the kids. This is the direction IT automation needs to go. There is no reason for the complexity inherent in IT automation today other than no one has yet to recognize that if we want to encourage more of it – and by folks who aren’t naturally coders – we need to find a better way to construct the workflows that represent the IT processes used to deploy, manage, and configure IT infrastructure.

The first thing we need to agree on is that programmatic doesn’t necessarily mean “you can do anything you want cause, code.” That’s true, in the most liberal sense of the word, but it also means the ability to change or define behavior programmatically. There are a limited set of actions required to execute a workflow in IT, and most are enabled today by the (other) API economy. By providing an interface that encapsulates those limited set of actions and provides clear and easy to understand logic constructs (if/then, while, iterative functions), we could ostensibly eliminate the tendency toward the unstructured scripting mechanisms that introduce far more technical debt into IT operations than most software developed in enterprises in the past. This level of constrained abstraction would also enable non-native coders (network and storage engineers and architects) to produce well-constructed workflows that are highly maintainable (a significant driver of standardization). When coupled with a serverless backbone to execute workflows, this model reduces the investment required to create, maintain, and execute workflows appropriate to IT operations.
That’s important, because as we need to approach IT automation with an eye toward sustainability. A script today works great, but can it scale along with people and processes in the future?
Now, maybe we don’t need a solution quite this simple (or colorful) but the premise on which the interface is designed is important, I think, to adapt as we look toward the future of IT automation and how we build (and maintain) the code that will eventually make IT go. Sadly, we tend to transfer the complexity in the underlying systems to the design of systems (and thus interfaces) that interact and control them. We want to expose every knob and button possible. At a minimum, an API broker that provides a way to aggregate the natural complexity of CLIs turned APIs into more comprehensible operational tasks would be a boon for those tasked with automating IT networks and app services. Logging in can be a complex process comprising multiple steps that are repeated every time. Composing them into a single “service” makes them repeatable and infinitely more auditable in addition to consistent. Combine that with a (more) intuitive interface and we’ve got ourselves an IT automation winner.
The interfaces for kids “coding” apps today proves that you can do that without making their users feel like they’re staring at an ENIAC with no manual to guide them. We can do better, and if we’re going to scale internal digital transformation to keep up with the business, we need to.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
