
The Internet of Things (IoT) is certainly a topic of much discussion, though for many it remains a consumer-oriented fad that has yet to make a real impact on the enterprise.
Unless, of course, you’re an enterprise that is taking advantage of things as part of your business strategy.
Sometimes we forget that beyond the consumer gadgets that make the headlines, there’s an entire world out there of sensors, appliances, control systems, and even toys that are already a part of the Internet of Things.
And that means there are already issues with security.
One recent issue involves an Internet connected teddy bear from Fisher Price. The security issue? A web application with which the teddy bear communicated apparently contained a vulnerability that left children’s identities exposed. This coming on the heels of the discovery of multiple flaws enabling the internet-connected Hello Barbie doll to be potentially turned into a surveillance device.
Don’t have kids? Try a read through Princeton’s security testing of Belkin WeMo Switch, the Nest Thermostat, an Ubi smart speaker, a Sharx Security Camera, a PixStar digital photo frame, and a SmartThings hub. According to the report, “Ubi used unencrypted communication methods that would reveal sensitive information such as if the user were home or if there were any movements within the house.” Both Sharx and PixStar transferred unencrypted data.
Now maybe we’re focusing on the “thing” side a little too much because it’s new and every new thing that connects to a network winds up with a wealth of new security risks that must be addressed and well, gosh darn it, it’s new and exciting. But the reality is that as you’re looking at incorporating “things” into your business model – whether for operational efficiency or to open up new markets – it behooves us to go back to the basics and ensure we’ve got that side of the equation covered, too.
It’s a simple thing to encrypt traffic. The Internet has more than 15 years of sometimes hard-learned lessons on the importance of proper key and certificate management. And yet millions of devices are reusing certs and sharing keys. And securing web apps? We’ve been pounding on that drum since e-commerce got its “e” and became a thing to be exploited.
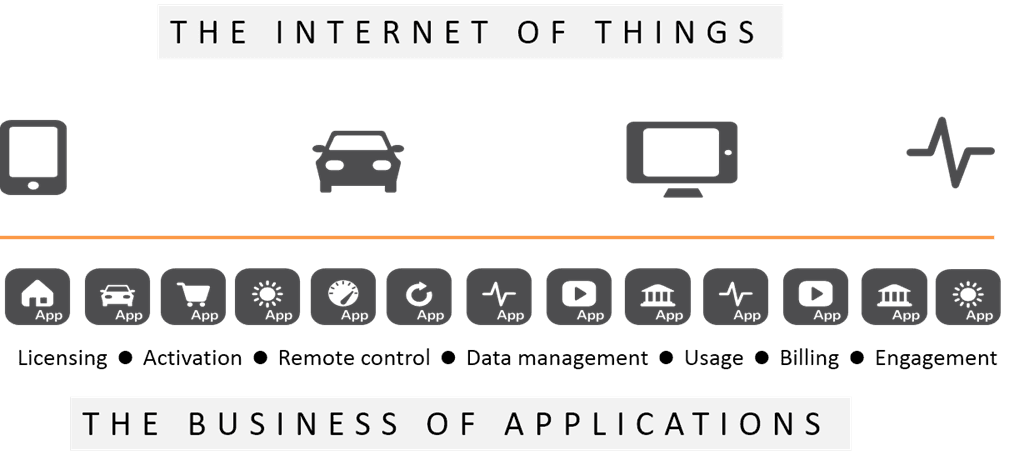
The things are coming, have no doubt about that. Many are already here, and some of them seem, as Douglas Adams might say, “mostly harmless.” But it isn’t just about the things. It’s also about the applications and systems with which those things almost always communicate, whether it’s to register, activate, obtain new content, share data, or to be managed.
Even if the app providing backend functions for your thing isn’t promoted as publicly accessible, it must be, by definition, publicly accessible in order for things out there to access it via the Internet. That means you should insist on security testing for every app that will be accessed by the thing you’ve built. Whether it’s in the cloud or in the data center, it needs testing and protecting.
The Internet of Things is the Business of Applications. And that means that the security of the internet of things is just as much about securing things as it is the securing the application ecosystem that supports them.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
