The distributed nature of modern applications across hybrid and multi-cloud environments makes ensuring robust security and maintaining compliance a daunting task for organizations. Traditional approaches to security and compliance often fall short in these complex architectures. By providing comprehensive management and visibility, real-time vulnerability assessments, simplified configuration management, and automated certificate handling, F5 NGINX One offers a unified solution that helps organizations implement consistent and robust security and compliance measures across their entire application delivery infrastructure.
Gaining visibility and assessing vulnerabilities
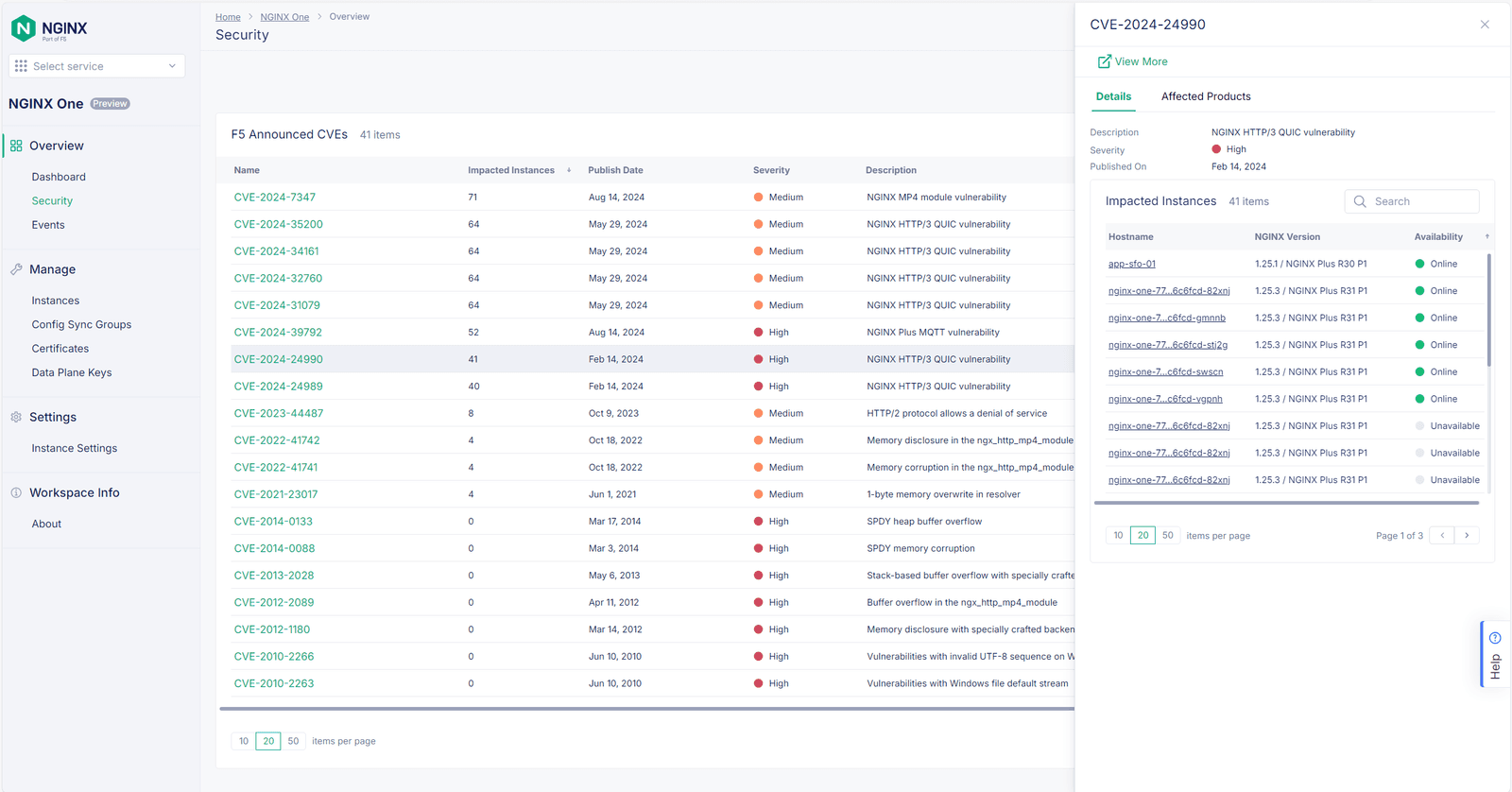
The first step in enhancing security and compliance is understanding what you have and where potential vulnerabilities lie. NGINX One provides comprehensive visibility into all NGINX instances across your environment, including version information and associated security risks.
Without this visibility, assessing vulnerabilities is a time-consuming and complex process, often involving manually emailing teams, waiting for responses, or relying on periodic scans from third-party security scanners. These scans are infrequent, and the results can be months old, making it difficult to maintain an up-to-date view of your security posture.
NGINX One makes vulnerability assessments much easier. The platform continuously monitors your NGINX instances and provides real-time information about potential security risks. This enables you to quickly see which instances are running outdated or unpatched versions and prioritize remediation efforts based on the severity of the vulnerabilities.
Simplifying configuration management
Ensuring secure configurations is just as important as running the latest software versions. Misconfigurations can introduce vulnerabilities, even if the underlying software is up to date. NGINX One simplifies configuration management by providing a centralized platform for staging, testing, and deploying configuration changes.
NGINX One's side-by-side visual difference (diff) view allows you to easily compare current and proposed configurations, ensuring that changes are thoroughly reviewed before being pushed to production. This streamlined process reduces the risk of human error and helps maintain consistent, and secure configurations across your NGINX fleet.
Real-time vulnerability management
NGINX One takes vulnerability management to the next level by providing real-time insights into potential security risks. The platform not only identifies instances with known vulnerabilities based on their version but also analyzes the actual configuration to determine if those vulnerabilities are actively exploitable.
For example, if an NGINX instance is running a version with a known vulnerability related to HTTP/2, NGINX One will check the configuration to see if HTTP/2 is enabled. If it is, that instance will be flagged as a high priority for remediation over other instances on the same version where the vulnerability is not actively exploitable.
This real-time vulnerability management feature helps organizations prioritize their remediation efforts and allocate resources more effectively. It ensures that the most critical security risks are addressed first, reducing the overall exposure of the application delivery infrastructure.
Automating SSL/TLS certificate management
Managing SSL/TLS certificates is a critical aspect of ensuring secure communication between clients and servers. Expired or improperly configured certificates can lead to security vulnerabilities and application downtime. NGINX One automates the certificate management process, making it easier to maintain compliance and reduce risk.
With NGINX One, you can centrally manage and monitor SSL/TLS certificates across your NGINX instances. The platform provides a comprehensive view of certificate statuses, including which ones are valid, expiring soon, or already expired. This centralized visibility eliminates the need for manual tracking and reduces the risk of unexpected certificate expirations.
NGINX One also supports automatic certificate generation and renewal using the ACME protocol, further simplifying the certificate management process and reducing the risk of compliance violations.
By providing real-time visibility, vulnerability assessments, configuration management, and automated certificate handling, NGINX One empowers teams to proactively address security risks and maintain a robust cybersecurity posture. As organizations continue to navigate the complexities of modern application delivery, NGINX One will play a crucial role in helping them build a more resilient, secure, and compliant application delivery infrastructure.
For a deeper dive into the full capabilities of F5 NGINX One, visit these related blogs and resources: Start with an Introduction to NGINX One. Explore how NGINX One optimizes management and observability and boosts availability and performance. And watch these demos on DevCentral to see it in action.
About the Author
Related Blog Posts

Secure Your API Gateway with NGINX App Protect WAF
As monoliths move to microservices, applications are developed faster than ever. Speed is necessary to stay competitive and APIs sit at the front of these rapid modernization efforts. But the popularity of APIs for application modernization has significant implications for app security.
How Do I Choose? API Gateway vs. Ingress Controller vs. Service Mesh
When you need an API gateway in Kubernetes, how do you choose among API gateway vs. Ingress controller vs. service mesh? We guide you through the decision, with sample scenarios for north-south and east-west API traffic, plus use cases where an API gateway is the right tool.
Deploying NGINX as an API Gateway, Part 2: Protecting Backend Services
In the second post in our API gateway series, Liam shows you how to batten down the hatches on your API services. You can use rate limiting, access restrictions, request size limits, and request body validation to frustrate illegitimate or overly burdensome requests.
New Joomla Exploit CVE-2015-8562
Read about the new zero day exploit in Joomla and see the NGINX configuration for how to apply a fix in NGINX or NGINX Plus.
Why Do I See “Welcome to nginx!” on My Favorite Website?
The ‘Welcome to NGINX!’ page is presented when NGINX web server software is installed on a computer but has not finished configuring