Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
This is a guest post collaboration between Squadcast & Threat Stack
It’s common for security professionals to become inundated by alerts, especially as cloud environments continue to scale at a rapid pace. In fact, in a recent SecOps survey, 83 percent of professionals reported struggling with alert fatigue. However, context is king, and with the right tools and integrations, it’s easy to fine-tune your alerts to drive smarter insights that help you make more informed decisions and take action faster.
At Threat Stack, we recognize just how important it is to provide the most meaningful alerts to cybersecurity professionals working to drive down key KPIs like MTTK (mean-time-to-know) and MTTR (mean-time-to-respond). Through partnerships like with Squadcast, an incident response (IR) platform, we’re able to provide Squadcast users with Threat Stack’s industry-leading rules, arming them with powerful insights gleaned from real-time risk and ML-based anomaly detection with enriched context. We also partner with leading public cloud providers like AWS to seamlessly integrate into your cloud environment, removing the hassle of toggling through different platforms.
With these partnerships and integrations between Squadcast and Threat Stack, customers can aggregate their alerts into distinct severity levels to better understand risk within their environment.
Why Full Stack Observability Matters
Anyone familiar with cloud infrastructure will understand the need to monitor their systems to identify and respond to risk closely. Systems are increasingly disparate, complex, and lucrative targets for cybercriminals. Therefore, it is essential to have tools that can help to monitor and quickly identify and remediate issues actively.
For instance, a company with infrastructure on AWS may use native tools like AWS CloudWatch for basic monitoring purposes. However, basic monitoring only goes so far, and security teams must leverage additional dedicated tools that provide observability, i.e., advanced capabilities for monitoring and greater visualization into environments.
Threat Stack enables full stack observability by collecting rich telemetry from cloud workloads, including the infrastructure and application layers, enabling security teams to uncover suspicious activities quickly.
Advanced Monitoring Enables Context Rich Security Alerting
Quickly addressing security and compliance incidents is critical to the success of today’s modern SaaS business. If a website or service is down for even a minute, it can potentially cause significant revenue loss, damage to brand reputation, and distrust among customers.
This is where the combination of modern IR platforms such as Squadcast and the observability from Threat Stack comes into play. In case of an incident, detailed events from Threat Stack can be routed to the respective users via Squadcast.
When Threat Stack detects a security risk and/or anomaly, it acts as the alert source and sends it to Squadcast. Leveraging Site Reliability Engineering (SRE) best practices, Squadcast aggregates, and routes these alerts to the on-call engineer. For the SRE & Security teams, however, they only act after such incidents have been reported.
There can be multiple teams responsible for different components of the infrastructure. And since Squadcast natively integrates with various application performance monitoring (APM)/ logging and error tracking tools, it can notify the appropriate team by intelligently routing alerts and helping them collaborate in real-time to deal with incidents within Squadcast.
Combining the Power of Squadcast and Threat Stack
To fully understand the depth of Squadcast + Threat Stack integration, let’s take the earlier example of a customer whose infrastructure is on AWS. In that scenario, the Threat Stack Cloud Security Platform® observes across the various layers of modern infrastructures to detect a wide variety of behaviors within your environment. Combined with AWS CloudWatch, these solutions enable monitoring infrastructure/application stack and track Service Level Indicators (SLIs) and Service Level Objectives (SLOs). If and when an SLO is breached, alerts are then sent into the Squadcast platform.
Put simply, whenever there is an alert in the Threat Stack platform, the configured Webhook for Squadcast is signaled, and an incident is created. Similarly, if Threat Stack sends more than one alert, the Squadcast platform can organize and group alerts (deduplication), providing full context to users working on resolving the incident. Let’s explore why this is beneficial.
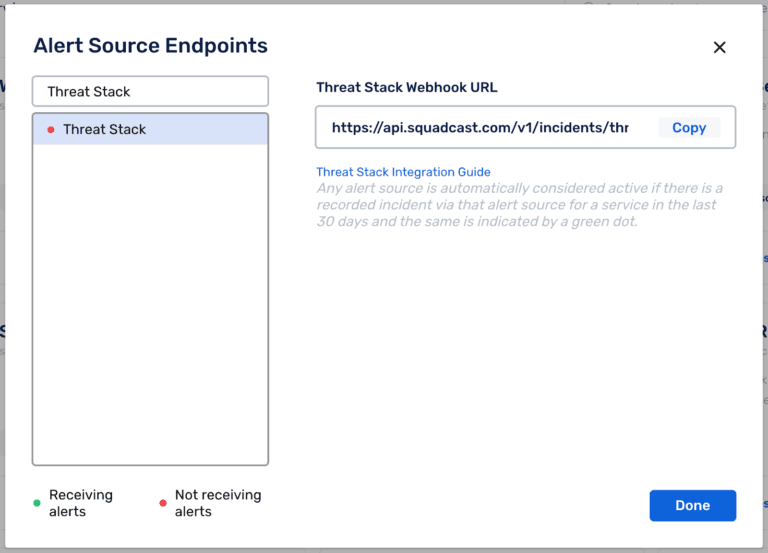
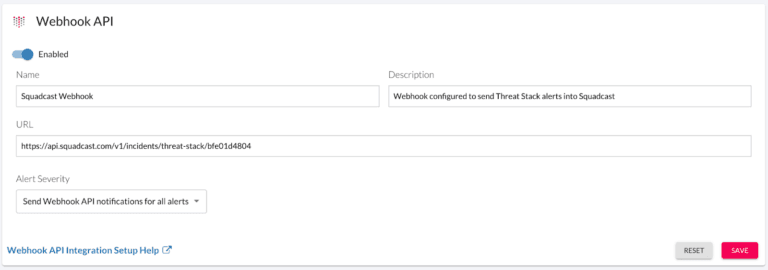
Four Benefits of Integrating Cloud Monitoring and Incident Response Platforms
Faster Recovery Time: The first step towards optimal incident management is adding relevant context to incidents as they are detected. The incident payloads going from Threat Stack into Squadcast can have Tags added to them to make alerts more context-rich. Examples of such tags are incident priority, incident severity, environment name, etc., which provides greater context for the security engineers when they receive an alert, helping to initiate faster incident response and ultimately reducing MTTR.
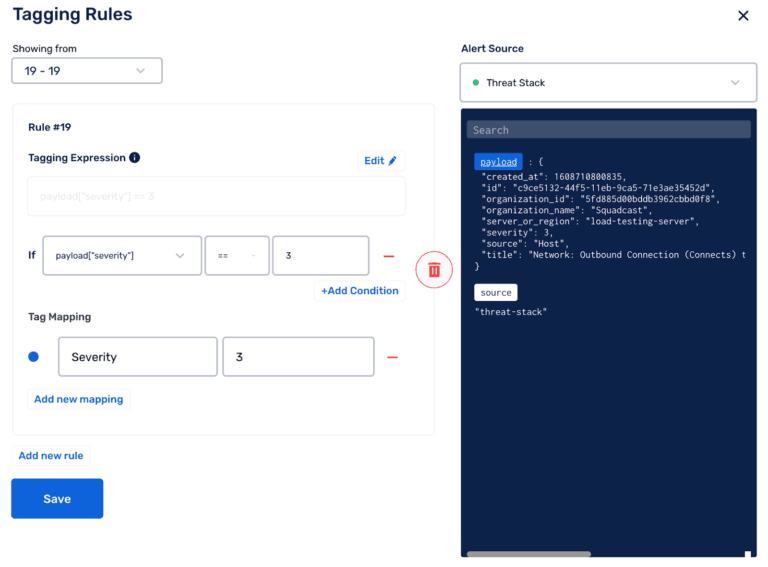
Greater Incident Transparency: As a general rule of thumb, increased transparency not only results in a better incident management and response process but, more importantly, increases trust between team members. This helps them better troubleshoot what went wrong before planning the following steps to resolve the issue.
Together, Threat Stack and Squadcast enable a holistic approach to incident management via full transparency into risk and real-time response capabilities — all of which minimize friction in the incident response lifecycle. Likewise, with better collaboration and transparency, the overall reliability of critical IT systems and services improves significantly.
Blameless Postmortems: Many incidents can be quickly rectified with tools like infrastructure automation, runbooks, feature flags, version control, and continuous delivery to keep your team in the loop with chatops and status pages. Though beneficial to fix the situation at hand, these actions do not provide much value in helping security teams understand what failed and why. But understanding this is a crucial step towards preventing similar occurrences moving forward and ensuring that teams develop a culture around blameless incident postmortem reviews. It should also be noted that empowering them with an easy and automated way to capture incident information and publish the final report with reusable checklists and templates could potentially make incident post mortem meetings less dreadful.
Granular Reliability Insights: Squadcast’s reporting and analytics feature will reveal the team’s performance in acknowledging and resolving alerts and help to identify areas for improvement. It can help teams visualize and analyze the distribution of incidents across services for a specified period of time and each service’s status.
With the growing number of incidents, many patterns will emerge to double down on frequent issues. You can do exploratory data analysis using graphical representations and understand more about the past incidents. This data can also be exported by filtering based on Tags that the incidents carry, such as Severity Tags, Alert Source, Status, Date & Time, etc.
In conclusion, combining the power of Threat Stack and Squadcast will help you quickly detect and respond to security and compliance risk across your cloud workloads, making an enormous contribution to drive down KPIs such as MTTK and MTTR.
If you are interested in unifying these two tools, Squadcast and Threat Stack support teams are available to help you achieve success. If you have other best practices to share or would like assistance with the Threat Stack/Squadcast integration set-up, feel free to drop a line to the Squadcast Support Team.
Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
About the Author
Related Blog Posts
SaaS-first strategies reshape cloud-native application delivery
F5 NGINXaaS empowers cloud and platform architects to unify operations, reduce complexity, and deliver exceptional digital experiences at scale.

F5 ADSP Partner Program streamlines adoption of F5 platform
The new F5 ADSP Partner Program creates a dynamic ecosystem that drives growth and success for our partners and customers.

Accelerate Kubernetes and AI workloads with F5 BIG-IP and AWS EKS
The F5 BIG-IP Next for Kubernetes software will soon be available in AWS Marketplace to accelerate managed Kubernetes performance on AWS EKS.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
F5 Silverline Mitigates Record-Breaking DDoS Attacks
Malicious attacks are increasing in scale and complexity, threatening to overwhelm and breach the internal resources of businesses globally. Often, these attacks combine high-volume traffic with stealthy, low-and-slow, application-targeted attack techniques, powered by either automated botnets or human-driven tools.
Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
David Warburton, author of the F5 Labs 2020 Phishing and Fraud Report, describes how fraudsters are adapting to the pandemic and maps out the trends ahead in this video, with summary comments.