The HTTP protocol is, for the most part, running the web. It is the communications protocol that drives most internet traffic. New ways of network optimizing internet communications are emerging, either encrypted, encoded, or clear text over UDP or TCP. Among them is the ability to batch multiple HTTP requests together into a single request. Batching multiple HTTP requests helps limit the payload overhead and the round-trip time (RTT) of a new request – meaning it saves time and cost.
The batching of multiple HTTP requests is primarily used to group various representational state transfer (REST) API calls by multiple protocols and vendors, among them is the Open Data Protocol (OData). An open standard that enables a simple method of creating and using REST APIs that interoperate and can be queried, the OData protocol was developed by Microsoft in 2007 and is used and leveraged in applications from Microsoft, SAP, and other vendors.
As a part of the OData specification, multiple REST API calls over HTTP can be batched into a single HTTP Request, saving precious and expensive network time and allowing the application better utilization of the allocated bandwidth.
When trying to secure applications that are batching HTTP requests, a challenge arises with the application of attack signatures.
There are three different types of attack signatures, depending on the part of the request to which they are relevant:
- Headers Signatures
- URL Signatures
- Payload Signatures
Here is an example of such a request:
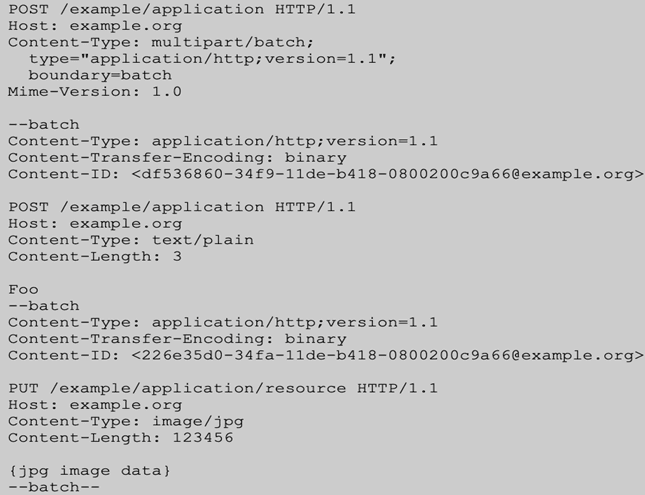
The first request contains other HTTP Requests, including its headers and URLs.
But, when a web application firewall (WAF) processes an HTTP request with multiple batched requests as a part of the payload, it will look at all the batched requests as a single payload. Therefore, it will only use payload-related signatures, which can lead to false positives and undetected attacks.
In F5 Advanced WAF v16.1, F5 has added native parsing and support for HTTP batched requests. This allows Advanced WAF to distinguish between each HTTP request individually – and not collectively in a batch – and therefore run the proper signatures on the right parts of each request.
F5 Advanced WAF protects all OData or other traffic with HTTP Batched Requests without risk of missing attacks or producing many false positives.
SAP leverages the OData protocol to communicate and interoperate with any application, software, or device that is not an SAP offering. As OData is based on HTTPS, any programming language – and for that matter, any developer – can use and communicate with an OData message. This allows any offering that is not an SAP offering to connect with SAP using HTTPS, as the interface to OData is based on XML or JSON.
SAP Fiori delivers tools that empower designers and developers to create and optimize native mobile and Web apps that deliver a consistent, innovative user experience across platforms. SAP Fiori provides a modern user experience to any device and for every user. SAP Fiori delivers users a simple, productive working from anywhere experience. OData enables non-SAP apps to be integrated and interoperable in an SAP Fiori-created environment.
While interoperability and easy communications are essential, so is security, especially for SAP Fiori deployments that are internet-facing and consume analytical applications or that use search over the Internet.
In a blog published by SAP, “Considerations and Recommendations for Internet-facing Fiori apps,” it states that a WAF “should be placed in front of the SAP Web Dispatcher, monitoring and controlling all incoming HTTP requests,” and that a WAF should be deployed “between a trusted internal network and the untrusted Internet.” The blog goes on to point out that, among the security capabilities available in a WAF, it should stop Distributed Denial of Service (DDoS) attacks, particularly “ so they cannot reach your SAP S/4HANA system”.
Support of OData protocol by F5 Advanced WAF enables customers to protect SAP applications with higher efficacy and reduced false positives.
For more information on F5 solutions for SAP Fiori and S/4 HANA, please review the following:
Quick and Secure: SAP Migration to the Cloud (F5.com)
Mitigating Active Cyberattacks on Mission-Critical SAP Applications | DevCentral (f5.com)
For more information on SAP Fiori and the application of a WAF to ensure security and reduce false positives associated with SAP Fiori and its use of OData and HTTP batch requests, you can review the following: Considerations and Recommendations for Internet-facing Fiori apps | SAP Blogs
Deployment in the Intranet or on the Internet | SAP Help Portal
Related Content
OData – Everything that you need to know: Part 1 | SAP Blogs
OData – Everything that you need to know: Part 2 | SAP Blogs
OData – Everything that you need to know: Part 3 | SAP Blogs
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.