Today’s enterprises demand a higher level of application awareness and management within the network. Data centers are built to deliver applications and services, but they’re still managed as large networks—and individual networking components are managed as isolated, single-point devices. For example, a traditional router is managed as though it does nothing more than route IP traffic in a void. However, applications are completely dependent on that router to work as expected. Organizational and data center networks are currently viewed by most enterprises as a series of individual objects to be managed by individual groups, but there is no overarching view of how those components relate to each other and the rest of the infrastructure, or how those components all function together to deliver applications to users.
Managing the entire infrastructure as individual components hampers IT, because it requires too many moving parts within different groups to adequately manage and control application delivery to users and to other services in the data center. As a result, IT departments often have complicated spreadsheets detailing which components are doing what at the network level—but no information about how those components are tied to the applications. This convoluted and isolated view of the infrastructure becomes a challenge for data center management, troubleshooting, and agile models such as self-service provisioning, because there is no understanding of how the infrastructure components come together to deliver an application.
While this antiquated view of the data center still influences management in many organizations, applications are evolving, and are taking center stage. This shift has forced enterprise IT departments to start managing with an app-centric view, rather than starting with devices and objects and piecing components together to deliver the application. This shift is largely driven by the push to adopt cloud computing and software as a service (SaaS), where the application becomes the most important component and the infrastructure becomes commoditized.
However, managing applications is much more complex today than it was just five years ago. On the back end, applications can now reside anywhere, whether inside or outside of the enterprise data center. Administrators can deploy apps between different cloud providers, run them as SaaS applications, and even spread them geographically between data centers on different continents. And with virtualization, data centers are moving away from a one-to-one, server-to-application model; resources are shrinking while services are continuing to grow. The applications themselves are also moving to a much more data-rich model, and relying on inter-application communication with APIs, increasing system and network resource requirements. Yet despite this rapid consumerization of enterprise IT, where the app is king, the fundamental infrastructure hasn't adapted. Managing application delivery isn't just about network components—it's also about context, and understanding how users interact with applications in real time.
F5 iApps is a powerful new set of features in the BIG-IP system that provides a better way to architect application delivery in the data center. iApps is rooted in a holistic, app-centric approach to how applications are managed and delivered inside, outside, and beyond the data center. iApps technology provides a framework within the BIG-IP system that provides a contextual view and advanced statistics about the application services supporting the business. With it, application, security, network, systems, and operations personnel can unify, simplify, and more effectively control application delivery services.
iApps abstracts the many individual components required to deliver an application, grouping these resources together in templates associated with specific apps. This alleviates the need for administrators to manage discrete components on the network.
Most enterprise IT departments delegate management responsibilities for various parts of the network to different groups: IP addresses, routing, and DNS are managed by the network team; physical and virtual servers, OS builds, and virus management is owned by the server team; API interaction, application standards, and access rights are owned by the application and security teams. As a result, there is typically no single group within IT that can answer the question, "What components are required to deliver email in your organization and how are each of those components configured?" There are simply too many uncoordinated moving parts.
iApps changes this by managing everything from an application-centered point of view. Nodes, application monitors, pools—with iApps, these application delivery service components can be clustered together and managed as part of an application workflow. This allows application and network administrators to easily define the infrastructure components required to deliver applications successfully by automating key management tasks.
In addition to configuring and managing application delivery services, iApps can define automation tasks, such as deploying additional application delivery resources. iApps relies on many different pieces of the BIG-IP system to manage all parts of application delivery, from applying load balancing rules for the AAA security infrastructure via F5's iRules engine, to exposing application diagnostic and visibility data to iHealth, F5's customer-facing support portal.
With iApps, all application delivery service components are bundled together and treated as extensions of the application. For example, a new SharePoint application will need specific health monitors that check the status of the web front end, search, and database components of SharePoint. Traditionally, those components would need to be individually assigned and managed—leaving room for error, and drastically increasing deployment time. With an iApp for SharePoint, all those pieces become components of the application itself, and can be deployed and managed in one centralized location.
Under the hood, iApps is made up of several discrete components, each responsible for managing a portion of the application delivery infrastructure. Tied together, these components are part of the unified BIG-IP Application Delivery Controller (ADC).
iApps bundles application components together for delivery by creating iApps Application Services that can be applied to any part of the application during delivery. For example, an iApps Application Service for SharePoint could initially be associated with a BIG-IP Local Traffic Manager (LTM) policy and a suite of SSL-related iRules. Later, administrators could associate a BIG-IP Access Policy Manager (APM) access policy with that same iApps Application Service for SharePoint by checking a single iApps box, and then redistribute it throughout the entire network. iApps Application Services reduce operational costs by providing insight into the entire application delivery infrastructure, binding application and network dependencies together in one unified system.
Similar to how object-oriented programming changed the way applications were written, iApps Application Services change the paradigm of how typical application delivery services are placed "in front" of the application. iApps Application Services can be applied to any part of the application delivery chain at any point during delivery, which allows the organization to choose what parts of the application are affected by which service components and at what time—all based on context. iApps policies are not confined to just building load balancing configurations. As part of the entire BIG-IP unified ADC platform, iApps policies can also include configuration settings for advanced BIG-IP system modules and features, such as assigning a user access policy to the application using BIG-IP APM.
Access to templates is one of the most compelling benefits of iApps. Although application templates have been available in BIG-IP LTM since version 10, they were limited to the initial deployment phase of new applications. In addition, they weren't available to modify the running configuration down the road.
iApps Templates are flexible and easy to use for deploying and managing application services—they act as the single-point interface for building, managing, and monitoring applications across all BIG-IP system modules. When an administrator builds a new iApps configuration using an existing template, the resulting configuration is used across all BIG-IP devices in a device service cluster, and provides the necessary information for F5 Analytics.
Beyond BIG-IP system configuration and management, iApps Templates also allow multiple groups within IT to define all the settings required to deliver and manage an application. A cross-functional team of architects can define the application parameters—from the network team providing IP address information, to the application team configuring a caching and compression policy, and the security team defining access polices for users and regions—and roll out procedures in an iApps Template. They can then deliver the template to IT operations for deployment in test or production BIG-IP devices. Once established, iApps Templates can be modified by the applicable group, and reused throughout the organization as business and IT needs evolve.
Another key benefit of iApps is removing the “subject matter expert” barrier to deploying a new app on the ADC, and throughout the infrastructure. Application owners no longer have to think about deploying individual BIG-IP LTM devices for availability or BIG-IP ASM devices for security. With iApps, application owners will simply add those services as part of the iApps application configuration, and the BIG-IP platform will deploy the appropriate service and all of the moving parts associated with that service. Application owners typically spend a great deal of time configuring applications to be delivered through BIG-IP system appliances. With iApps Templates, that up-front work can be reused throughout the organization. Customizable iApps Templates help organizations to save on operating expenses by fine-tuning application policies once, testing them once, and then reusing that work by exporting the configurations and sharing them with additional BIG-IP devices and other IT organizations.
iApps configuration policies are designed to be portable between BIG-IP systems and between users. iApps Templates can be exported on a per-application basis and reused throughout the application network. In addition, they can be exported and shared through the iApps Ecosystem on DevCentral, F5's community site, where BIG-IP system administrators and developers can create, modify, and share their own iApps Templates for other applications or adjust existing iApps Templates.
F5 routinely releases official iApps Templates for new applications through the iApps Ecosystem on DevCentral; this leverages the engineering work for new applications from F5 partners such as Microsoft, IBM, and Oracle, as well as application templates specific to vertical markets such as financial, government, and health care.
The majority of an iApps policy is geared toward configuring the traffic management components required to deliver applications. However, the BIG-IP platform also includes tools for monitoring applications and provides real-time application performance statistics. It also provides diagnostic and troubleshooting information such as application response time, network latency, and connection statistics for the entire application, virtual servers, pools, and nodes.
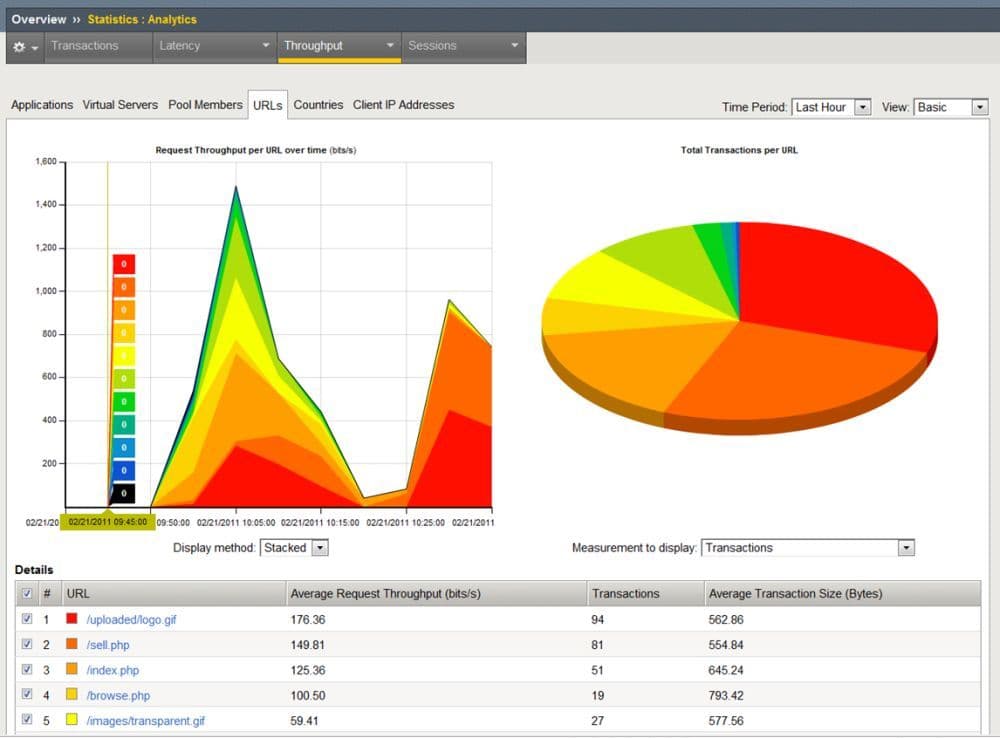
Unlike traditional monitoring tools, F5 Analytics collects performance data at the application level, binding the information to the application itself rather than to individual infrastructure components. Application owners can monitor performance from the application through the application servers, and all the way down to the network. This allows organizations to monitor exactly how the application is performing in real time based on application response, network conditions, and user context.
F5 Analytics leverages statistical and logging data from the BIG-IP system. It takes this data and formats it as a JSON object, which is then exported for consumption by data consumers such as F5 BIG-IQ or applications such as Splunk.
With F5 Analytics, you can configure several categories of data to be exported. For data consumers like Splunk, it lets you configure the network endpoint to which the data is sent.
Data center hardware devices are typically run in redundant pairs, either in Active/Standby (one system manages 100 percent of the duties while another system waits for the first system to go offline before picking up those duties) or Active/Active (both systems distribute the workload between devices). Both redundant configurations are a best practice for any mission-critical hardware deployment, yet they contain one major design flaw: this redundant architecture is based on the entire device failing.
A better approach is to build a fault-tolerant architecture based on what the device is doing at any point during application delivery, rather than whether the entire device is online or down. BIG-IP devices enable a scalable, fault-tolerant architecture at the application level, creating failover protection for application configurations between devices. BIG-IP device service clusters run in two different configuration options: Sync-Only and Sync-Failover modes.
BIG-IP device service clusters Sync-Only mode allows multiple BIG-IP hardware and software appliances to dynamically share application-specific delivery configurations and templates between devices. This eliminates the need for an administrator to manually update full device configurations whenever something changes. Because BIG-IP application policies are separated from the hardware configurations, administrators can sync application and networking information between devices rather than duplicating an entire BIG-IP configuration file. This enables IT to run different BIG-IP devices with different configurations, but still sync unique application configurations and policies between those devices. For example, BIG-IP Application Security Manager (ASM) policies can be synced between BIG-IP devices without affecting other application policies on each device, or requiring the security team to manually install individual BIG-IP ASM policies on each device.
In addition to syncing between devices, application configurations can failover active and live application traffic between devices, taking the Active/Active concept to the application layer. BIG-IP device service clusters Sync-Failover mode extends the 1:1 notion of Active/Active to N:1, where as many active devices as needed can share the application load depending on resource constraints and availability. This is very similar to the idea of RAID 5 striping, where the number of disks can be determined based on need and redundancy.
As more application delivery resources are needed, administrators can add active BIG-IP devices to a device service cluster. The cluster takes on some of the overall application delivery load without adding a second dedicated standby device, just in case the new device goes offline. With BIG-IP device service clusters, every new device in the group takes on some amount of redundancy by being available for the extra application load should one of the devices go offline. The more BIG-IP devices that become part of a device service cluster, the more efficiently the application load can be spread between all available devices.
Two key tenets of iApps are visibility, and control. iApps provides unprecedented levels of each across the entire infrastructure; however, the degree to which it provides visibility and control relies on its placement at a strategic point where all application delivery logic can be applied dynamically to all bi-directional application traffic with a coordinated mediation layer between the users, the applications, and the data. This layer presents a consistent interface and set of services that can be used for all applications and data, regardless of their current location. Using an intelligent understanding of context—who is accessing what from where and why—this layer determines the optimal connection among users, applications, and data. Additionally, it provides a deep understanding of context to inform the underlying application and data elements about the current resource requirements, and to instruct the infrastructure to adapt in real time to ensure optimized application and data access.
This strategic flow of application information becomes part of an iApps configuration. Initial configuration with an iApps Template is based on how the application should be delivered in an ideal architecture; the application is managed throughout the delivery lifecycle through iApps Templates and BIG-IP device service clusters, providing the what and where. F5 Analytics brings the why portion, reporting that information back to IT for analysis. iApps is in strategic points of control—the only place that allows such granular and broad application delivery management.
As organizations have moved to more modular cloud and SaaS models, managing applications has become more important than building infrastructure. Many of the benefits that come from moving to a more agile model are not associated with managing the infrastructure; yet managing application deployments, performance, and availability in cloud and SaaS environments is often difficult because the application is still tied to infrastructure. iApps binds application control, visibility, and management to the infrastructure required to deliver those applications and services beyond the data center.
iApps supports the architecture that transforms a network from a static resource comprising isolated components to a unified, flexible, and resilient pool of resources directly associated with an application or service. This transformation enables rapid network deployment, integration, management, and visibility at the application layer. iApps provides complete control over the entire application delivery infrastructure by adapting the network to the application. The resulting quick deployment and single-point capabilities save operational costs. With F5 iApps, organizations can create a common, and highly reusable, catalogue for security, acceleration, and availability services at a strategic point of control, to dramatically increase the organizational agility and efficiency of F5 BIG-IP devices.
PUBLISHED DECEMBER 14, 2017