State of the APIs
Over the past several years, many organizations have been going through a digital transformation, a process which has accelerated due to the COVID-19 pandemic.
And APIs are playing a significant role in that transformation. As part of their digital transformation, many of those same organizations are now stating that they are an “API-First” organization. An “API-First” organization is one that begins by designing an application by designing APIs first. Then, using the APIs as the foundation, they begin designing the remainder of the application. The intent is that the application will leverage its foundational APIs to communicate with and retrieve information from other applications.
These organizations are usually developing APIs and consuming them to support their partnerships with external organizations, reducing their development time and cost, and enhancing interoperation between internal systems, tools, and teams.
As stated in F5 Labs’ State of Application Strategy Report 2021, APIs are also the cornerstones for application modernization, being leveraged to assist in the adaptation and updating of older, classic applications to support newer, more modular application languages, tools, and platforms. Also, APIs – both good and bad ones – now account for the vast majority of total web traffic.
That’s the first edge of the “double-edged sword” of APIs.
The second edge of the “double-edged” sword regarding APIs is, according to Gartner, API abuses will become the most frequent attack vector by 2022. Attackers realize that APIs can be vulnerable or are even left unprotected by some organizations, as they rely upon an open flow of data and information to be shared between their application and other applications. Other times, its simply an oversight, but one that allows attackers a quick, simple entry point to compromise an application. This situation requires special treatment, such as native support of all API protocols and technologies used by the industry.
GraphQL APIs
One relatively new API technology that has grown quickly in the past few years and is continuing to gain traction is GraphQL. Internally developed by Facebook in 2012, now a part of the Linux Foundation, GraphQL is overcoming significant challenges that exist in REST APIs. Organizations are turning to GraphQL to develop APIs, as opposed to REST or SOAP.
Such challenges include under-fetching and over-fetching of data, faster front-end development without the need for new API endpoints (GraphQL uses one endpoint), great backend analytics using GraphQL queries, and a structured schema and type system.
Last year, GraphQL already attained more than 22% industry adoption1, reaching Innovators, Early Adopters, and the Early Majority of the Innovation Adoption Lifecycle.
GraphQL is expected to become one of the leading standards for APIs in the years to come.
GraphQL Security
However, the meteoric growth and acceptance of GraphQL has also quickly drawn the attention of cyber adversaries, some of whom have already started exploiting vulnerabilities in the GraphQL ecosystem and have begun developing tools to attack them.
Attack techniques on APIs using GraphQL include good old SQL injections, as well as newly formed attacks that are leveraging the GraphQL specification to reveal data about the API and use it to the attacker’s advantage.
In addition, new methods for denial of service (DoS) attacks have been introduced that leverage GraphQL-built APIs and quickly drain server resources.
Starting with Advanced WAF v16.1, F5 now natively supports security for GraphQL APIs.
First and foremost, F5 has developed native parsing of GraphQL traffic to allow Advanced WAF Attack Signatures to be applied.
On one hand, this approach will detect attacks in the right places of the payload (run the signatures on the values); and on the other hand, this approach will stop false positives due to attack signatures running on the wrong parts of GraphQL requests.
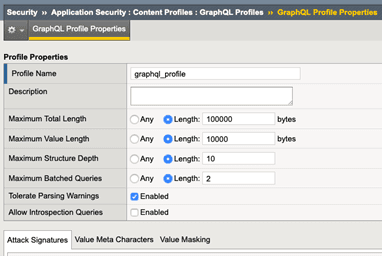
Second, F5 creates the GraphQL policy template and content profile as a part of the Application Security Policy.
In this new content profile, the user can configure the total length and value length of parameters, limiting them according to their policy.
In addition, the user can configure the maximum structure depth eliminating recursive GraphQL queries that can lead to a DoS attack; and the maximum batched queries, limiting the number of different GraphQL queries in one HTTP request.
Introspection queries can also be enforced, which can otherwise aid attackers in their understanding of the API structure and enable them to be more successful breaching an app.
To combat this, F5 has also added support for our declarative policy configuration, the protection of volumetric DoS using our Behavioral DoS feature, and filtration of responses with the DataGuard feature in F5 Advanced WAF.
To summarize, GraphQL provides new ways to create and manage APIs, enhance the modernization of existing classic applications, and support digital transformation. But as always, more threats are coming to exploit openings in any new technology, and you can be caught off guard.
Start protecting your GraphQL APIs with F5 Advanced WAF today!
For more information, please check out our DevCentral post and our Lightboard Lesson on YouTube.
1 2020 State of the API Report, Postman
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.