Top 3 Public Sector Application Modernization Trends
Balancing Agility with Security
Balancing Agility with Security
Most organizations, including those in the public sector, find their application portfolio weighed down over time by aging legacy apps. Tight budgets, growing cybersecurity concerns, and the challenge of maintaining legacy applications and infrastructures are overloading traditional IT resources in agencies.
Many agencies today are under increasing pressure to keep costs low and serve a growing number of users while managing and protecting a massive amount of data. The good news, whether federal, central, provincial, state, or local, government agencies are increasingly utilizing modern applications to fully support the business requirements of innovation, agility, and efficiency. This article will cover the top three public sector IT modernization trends we’re seeing today.

Many public sector agencies have traditional network architectures that are static, vulnerable to human error, and far too complex.
Managing legacy systems requires significant OpEx and increases TCO, with precious time and resources devoted to maintaining legacy apps that are inefficient and insecure. App dev teams especially are hampered by legacy architecture, inefficient manual processes, and reviews and procedures that don’t integrate well into the app dev lifecycle.
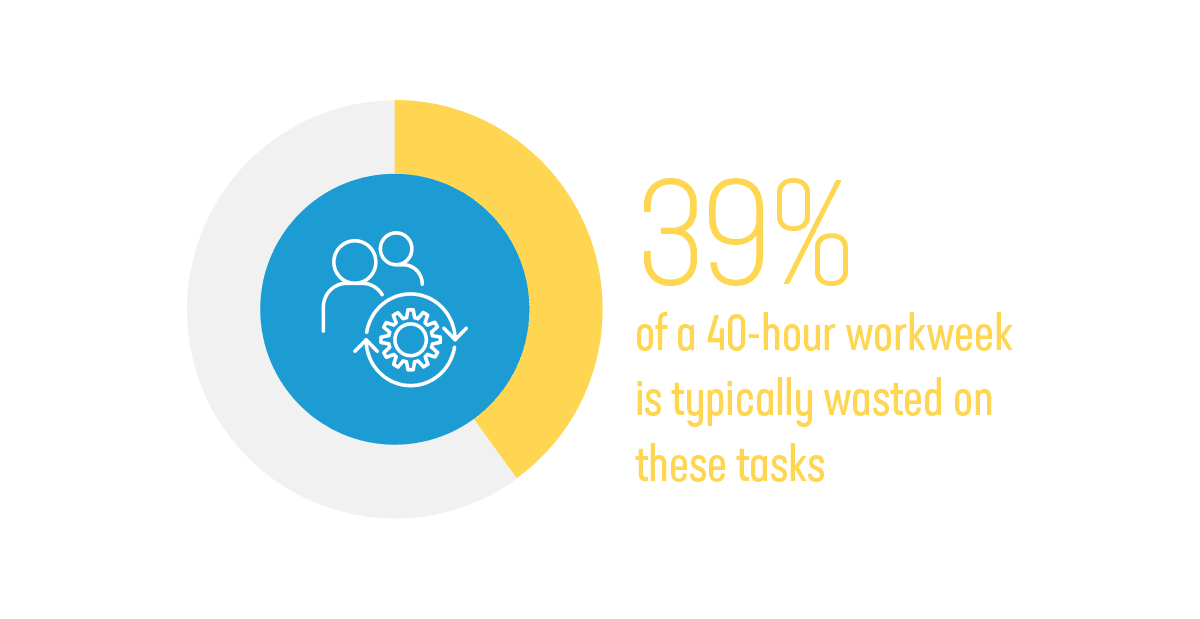
Migrating from legacy applications is only half the battle. A recent survey found that 15 hours a week are being spent by developers in DevOps environments managing tasks such as debugging pipelines and waiting for tests and builds to complete.1 It’s critical to find the right modern app dev solutions that help streamline processes, like ones that help automate repetitive DevOps tasks. 39% of a 40-hour workweek is typically wasted on these tasks.

Dated and complex public sector network architectures and app development and deployment processes make it difficult for agencies to deliver the kind of digital experiences civilians and government employees expect from consumer-grade apps.
BCG recently surveyed 24,500 people across 36 countries on their use of digital channels for government services. 76% of respondents said that government services should be similar to or better than those offered by the best private sector organizations.2 By not keeping up with constituents’ and government employees’ growing demands for positive digital experiences, agencies may not be able to maintain IT effectiveness. Creating digital experiences with customer-centric thinking is not an easy task. Application development teams need the right talent, leadership, and solutions to complete their mission.


Public sector agencies are highly targeted by hackers, cybercriminals, and other governments with malicious intent. In addition, the government’s enormous online presence creates a large attack surface.
Security vulnerabilities associated with evolving app development and modernization processes can lead to successful attacks and abuses against agencies, resulting in a loss of constituent and employee personally identifiable information (PII), state and military secrets, and money. Outside of embracing government security guidelines, like NIST and DISA in the U.S. or the NIS 2 Directive in Europe, many agencies are looking towards adopting DevSecOps and Zero Trust approaches.
2 The Global Trust Imperative , BCG + Salesforce
3 The Promise (And Perils) Of Customer-Focused Government Technology Transformation, Forrester
4 Solving DevSecOps and Microservice Challenges with Zero Trust, F5 Labs