The Persian Gate, 330 B.C.
The Pass at Thermopylae, 480 B.C.
The Bridge at Stirling, 1297 A.D.
The Equinix Cloud Exchange Fabric®, 2020 A.D.
Many places are enshrined in history for the strategic role they played in some impactful event. The Pass at Thermopylae is remembered as the place where King Leonidas' famous 300 Spartans held off an advancing Persian army. The Bridge at Stirling is indelibly associated with the Scottish resistance led by William Wallace and a stunning victory over the English army. Lesser known is the Persian Gate, where Ariobarzanes and his army held Alexander the Great at bay for an entire month. The strategic advantages of controlling a single access point to a desired resource is well understood.
The advantages just aren’t about defense; careful control over entry points also results in a multiplicative increase in the efficacy of defenders. It’s no surprise, then, that these principles are often applied in the world of digital security.
For some time now, organizations have been moving applications and workloads to public clouds and enjoying the benefits of digital transformation, including flexibility and economic efficiency. But just like their on-premises counterparts, cloud applications still require advanced services, including security, load balancing, and high availability. Additionally, adding a cloud environment to the data center infrastructure introduces management headaches, compliance risks, and issues related to policy consistency.
Today, the Equinix Cloud Exchange Fabric (ECX Fabric®) is a location organizations should seriously consider to address these challenges. As a digital bridge between the Internet and most major cloud providers, Equinix offers a strategic location at which to control access, secure entry, and protect applications in all the major SaaS, IT service providers, and public clouds.
But the right location is only half the battle. You still need defenders to protect against inevitable attacks. This is a key reason why increasingly diverse distribution of applications and resources poses a challenge to security professionals. Nearly all organizations operate applications across multiple public clouds and consume a healthy portion of SaaS applications.
Consider all the security services you need to defend and protect applications and their infrastructure:
- Single sign-on (SSO) and cloud federation to control access
- Bi-directional web application firewall services to protect consumer and corporate data and defend against abuse
- SSL Orchestration and content inspection to ensure privacy and protect against embedded malicious data
- DDoS protection to keep applications available
Deploying these defenders for each application at every location is going to cause solution sprawl and operator overload. Ensuring the same level of security across them is a task that is constantly repeated due to emerging attacks and newly discovered vulnerabilities. A better approach is, of course, to force the flow of traffic through a single gate at which multiple security services can be deployed and protect all applications across all cloud properties.
Deploying a BIG-IP platform in the ECX Fabric provides a single, strategic location at which you can deploy, operate, and manage the security services you need to protect applications deployed across multiple cloud properties. By guiding all traffic to the same strategic location there are fewer policies to deploy and maintain, fewer services to operate and manage, and fewer entry points to defend.
In addition to reducing the complexity associated with a multi-cloud enterprise, organizations can realize significant cost savings and application performance enhancements while maintaining enterprise-grade security. They also benefit from a single point of entry and exit between the public cloud and the private corporate network—making it easier to retain tight control over network and application security.
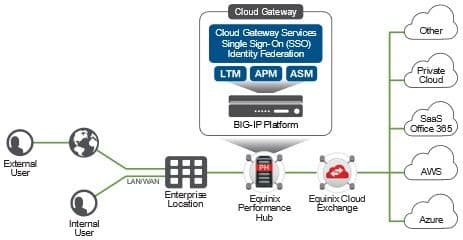
Common F5 application services for this type of deployment include:
- Local and Global Traffic Management
- Access Management
- Identity Federation
- Advanced Web Application Firewall (WAF)
- DDoS Protection
- SSL Inspection and Orchestration
- Telemetry Streaming
Additionally, Equinix offers a service called SmartKey™ which closely interacts with some F5 application services. Equinix SmartKey is a dedicated hardware security module (HSM) offered as-a-Service to provide secure key management and cryptography services that (among other things) F5 uses to optimize its own security services and capabilities.
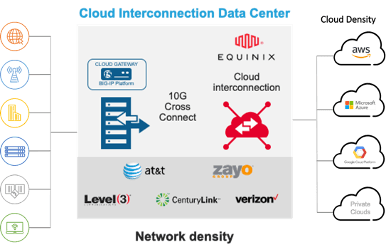
F5 offers a wide range of services that work in conjunction with Equinix to fulfill a variety of use cases and security policies.
The reality of multi-cloud means enterprises will continue to be challenged to protect applications and defend data in many different locations. By pairing the BIG-IP platform with the ECX Fabric, organizations can gain a strategic advantage over attackers while reducing costs and the complexity inherent in managing multi-cloud security.
There are many benefits to employing F5 solutions in the Equinix environment. If you missed them the first time, here are more resources you can check out to learn more:
- Equinix Technology Alliance
- Equinix & F5: Taking Control Of Your Hybrid Cloud Security
- Improving Business Outcomes and Application Experiences with a Cloud Gateway in Equinix
- Improving Security Outcomes with F5 SSLO in Equinix
- Consistently Control Access to Multi-Cloud Applications with F5 Access Manager and Equinix
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
