For Information Security/SecOps teams, some mornings can feel a bit like this:
And while enough caffeine can usually get people moving—what’s also likely to get SecOps or BIG-IP admins to feel awake (read: jittery or panicked) is wondering if they’re maintaining a consistent security posture across distributed or multi-environment deployments when they grab that extra coffee. The picture above may not depict the way SecOps dress for work, but it can illustrate their mindset on a day-to-day basis.
Many SecOps teams, like their NetOps counterparts, usually start—and end—their day with a primary goal: ensuring that F5 Security and BIG-IP deployments and the apps running on them remain healthy, secure, available, and performing well. However, achieving true visibility around such metrics has become complicated for organizations as they’ve continued to expand their web applications portfolios. And, of course, it’s difficult to protect what you can’t see.
In a recent blog post, Jay Kelley highlighted that “security enhancements may be necessary to pass a re-audit or to better protect the business and lower the risk of a new breach.”
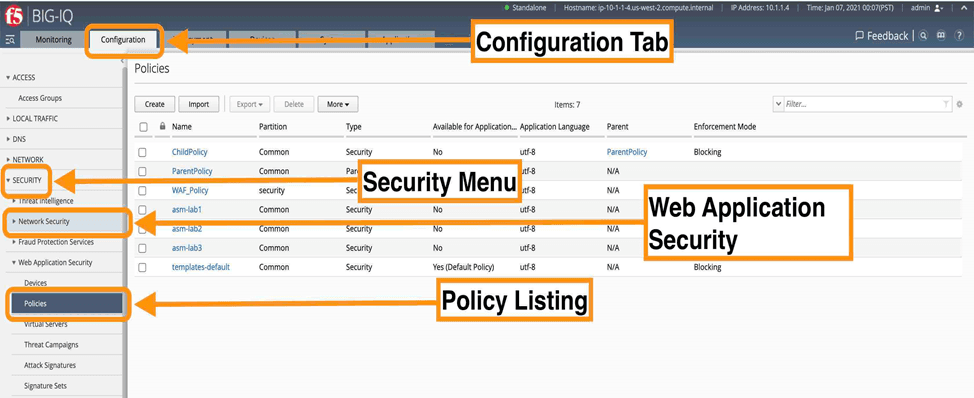
The latest release of BIG-IQ (8.0) does precisely that! BIG-IQ 8.0 introduces several security administration and visibility enhancements that help security pros to not only lower the risk of a new breach but also simplify and streamline day-to-day management tasks.
The latest BIG-IQ release enables better management and visibility of F5 security solutions, improving overall security posture and threat protection. It helps SecOps teams strengthen security enhancements, augment product capabilities, and provide a simplified app-centric user experience.
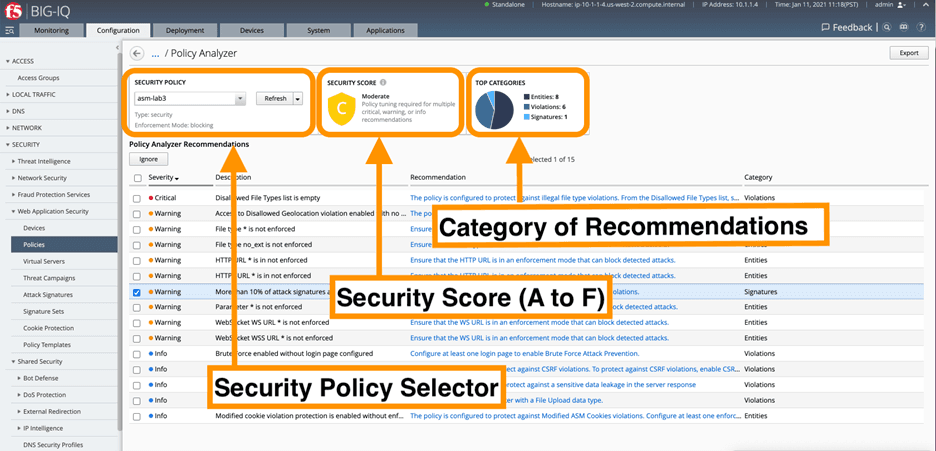
For the security pros who feel like editing web server configuration files requires serious protection, BIG-IQ 8.0 offers an all-new dashboard (Configuration Analyzer) that enables users to audit security policies, detect anomalies and vulnerabilities, understand effectiveness, and use proactive suggestions to improve policies quickly and easily—enabling better application protection.
Another cool feature introduced in 8.0 is policy comparison, allowing SecOps to ensure consistency and compliance across F5 security and application delivery solutions. SecOps teams can easily bring up two web application firewall (WAF) policies and look at them side-by-side in a table format. This view enables them to identify inefficiencies, redundancies, or weaknesses in different policies for compliance more quickly.
Some other noticeable highlights include enhanced bot protection management and extending role-based access controls (RBAC) to additional security workflows and dashboards—helping to foster better collaboration, ensuring deployments are “blessed” by SecOps, and removing operational bottlenecks.
BIG-IQ 8.0 also includes declarative APIs for SAML service providers, unified API support for F5 SSL Orchestrator, and the ability to easily configure zones for BIG-IP Advanced Firewall Manager (AFM)—all helping to enable better management and visibility of F5 security solutions and improving overall security posture and threat protection.
The new security features and capabilities introduced in BIG-IQ Centralized Management 8.0 include:
- Simplified Access Configuration Interface workflows for a SAML service provider
- Policy Configuration Analyzer dashboard
- The ability to compare web app security policies for compliance
- Scheduling and exporting WAF analytics reports
- Office 365 URL fetching for F5 SSL Orchestrator
- Modifying network objects thru iAppLX
- High-Availability (HA) status dashboards and remediation
- Reporting on unused, orphaned objects, Zone-based firewall, and network service mesh (NSM) to unlock items created by network service endpoints (NSE)—helping to ensure data sanitization
- Actionable insights on SSL/TLS compliance reports, SSL certificate expiry days, and incident root cause with new F5 Beacon SaaS integration
For more information about BIG-IQ Centralized Management, click here. Please join us for a BIG-IQ webinar and live demo coming up on Wednesday, March 17 at 10:00 a.m. PT | 1:00 p.m. ET. We look forward to seeing you there!
Stay tuned for the third blog in this series to learn how BIG-IQ 8.0 can further enhance application owners and developers’ day-to-day.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
