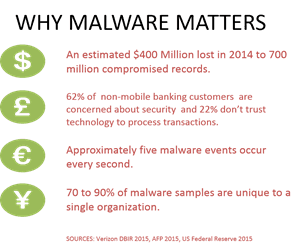
Malware. It’s come to be a significant factor in attacks against both corporate and consumer assets. It continues to result in millions of dollars in fraud while simultaneously chipping away at consumer trust in financial and banking institutions.
Research indicates that preventing and/or detecting malware threats is a top factor driving network security strategy today. Given that Google found just this year that a primary delivery mechanism for malware, phishing, still catches nearly half of its targets that’s no surprise.
It behooves us, then, as leaders and practitioners interested in addressing these issues to be aware of new and rising malware threats that may compromise both our systems and the systems of our consumer-customers.
One such rising dark star is “Slave.” First spotted in March 2015, Slave targets banking web apps with script injections designed to perform a number of functions including credential theft, account access and automatic funds transfers.
In many respects Slave is less sophisticated than some of its cousins, but that makes it no less dangerous. To help you better understand the threat – and defend against it – our security researchers have put together a detailed analysis of this pernicious piece of software and made it available on DevCentral.
Stay safe out there!

###
Editors Note: F5 and DevCentral do not condone the usage of the term ‘slave’ in the context of our technology. In this case the term ‘slave’ is a name, used to specify a particular piece of malware. We believe removing or changing the term, here, would only cause confusion and remove information necessary for effective application security.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
