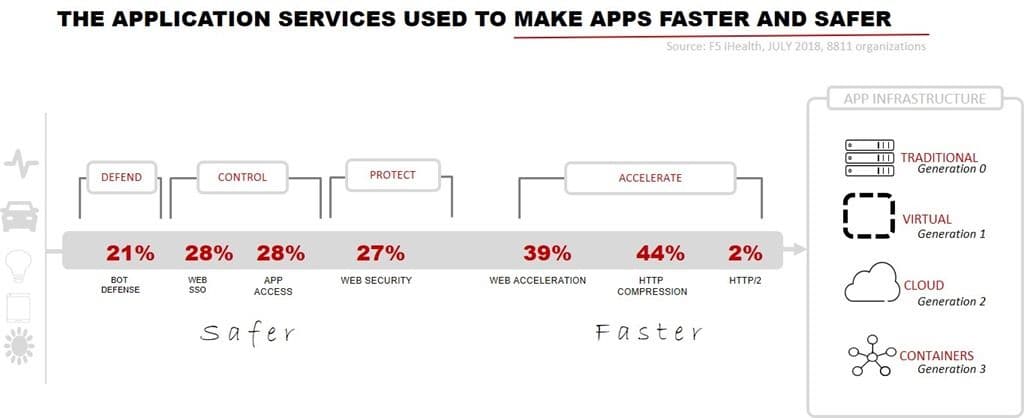
It’s time again to dig into the application services organizations are actually using to make apps faster and safer.
Of note this quarter again is a continuing rise in use of bot defense services. Security and performance application services held firm, showing no losses or gains.
Disturbing is the number of administrative-based ports that remain configured for access. While it’s impossible to determine whether these ports are accessible from the Internet from the data available, the virtual servers configured to support administrative access and protocols is significant, numbering in the thousands. That includes consoles that enable privileged tasks via the web, such as webmin. With incidents involving openly accessible web-consoles increasing, it behooves network operations to regularly audit application services and ensure access is warranted and secured if necessary.
DEFEND
BOT DEFENSE KEEPS RISING
Bot defense gained 2% again over last quarter, growing from 19% to 21% of organizations employing it to defend against malicious non-human traffic.
Research from F5 Labs proposes that half of all Internet traffic originates with bots. Nearly one third (30%) of these are malicious.
CONTROL & PROTECT
SECURITY STANDS FIRM
Use of application access and web single-sign on services were steady quarter over quarter, as was web security usage.
Analysis from F5 Labs revealed that applications and identities were the initial targets in 86% of breaches, making these application services critical.
ACCELERATE
SUSTAINING SPEED
Web acceleration and HTTP compression services each maintained previous gains, staying steady at 39% and 44% respectively.
The use of client-side SSL (82%) remains disproportionate with its server-side implementation (70%), indicating SSL termination in support of speed rather than end-to-end security.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
