So, you think you solved your bot problem. But now you are unsure. Or perhaps your contract is up for renewal, and you are doing due diligence to see if you are getting the best ROI from your bot management vendor partnership.
While performance, analytics, and logs look good, something seems off. All your efforts to improve your digital experiences and delight your customers have not borne fruit. Revenue has not followed. Chargebacks are at an all-time high. Customers are calling the help desk and complaining about difficulty transacting on your site and are going to competitors in droves. Your security and risk teams are complaining about an onslaught of false positives that are distracting them from strategic business initiatives.
Perhaps you asked your bot management vendor some of the questions from 10 Questions to Ask a Bot Mitigation Vendor, but you want further validation.
It doesn’t hurt to keep your bot management vendor on their toes—so here are 10 More Questions to Ask a Bot Mitigation Vendor.
1. How does the vendor measure success?
The name of the game is efficacy… Or is it?
Bot mitigation vendors like to mic drop on efficacy, but the attack catch rate is only one part of the equation. A strict security posture may lead to a high catch rate, but it would also lead to false positives that inundate security teams and cause friction that alienates customers, resulting in abandoned sales and stunted business potential.
When you consider factors such as false positives, user friction, opportunities to personalize or improve the customer experience, and maintaining resilience no matter how criminals retool their attacks, we are talking more about effectiveness.

2. Does the service protect apps and APIs across different environments and clouds?
This is an important consideration. Are you able to run your business the way you see fit, leveraging the appropriate business continuity and ecosystems that streamline your operations and give you the highest competitive advantage, or are you required to rearchitect your environment and move your digital footprint into the vendor’s proprietary platform? What if that platform experiences degradation, or even an outage?
Consumers in the new digital economy demand simple and secure experiences, and any hiccup may result in transaction or even brand abandonment. Do you really want to be at the mercy of vendor lock-in, or do you prefer to control your own security destiny?
It is now possible to deploy bot defense anywhere to protect apps and APIs everywhere, with insertion points across clouds and architectures that enable rapid and robust protection—reducing complexity, increasing reliability, and supporting innovation while effectively managing risk.
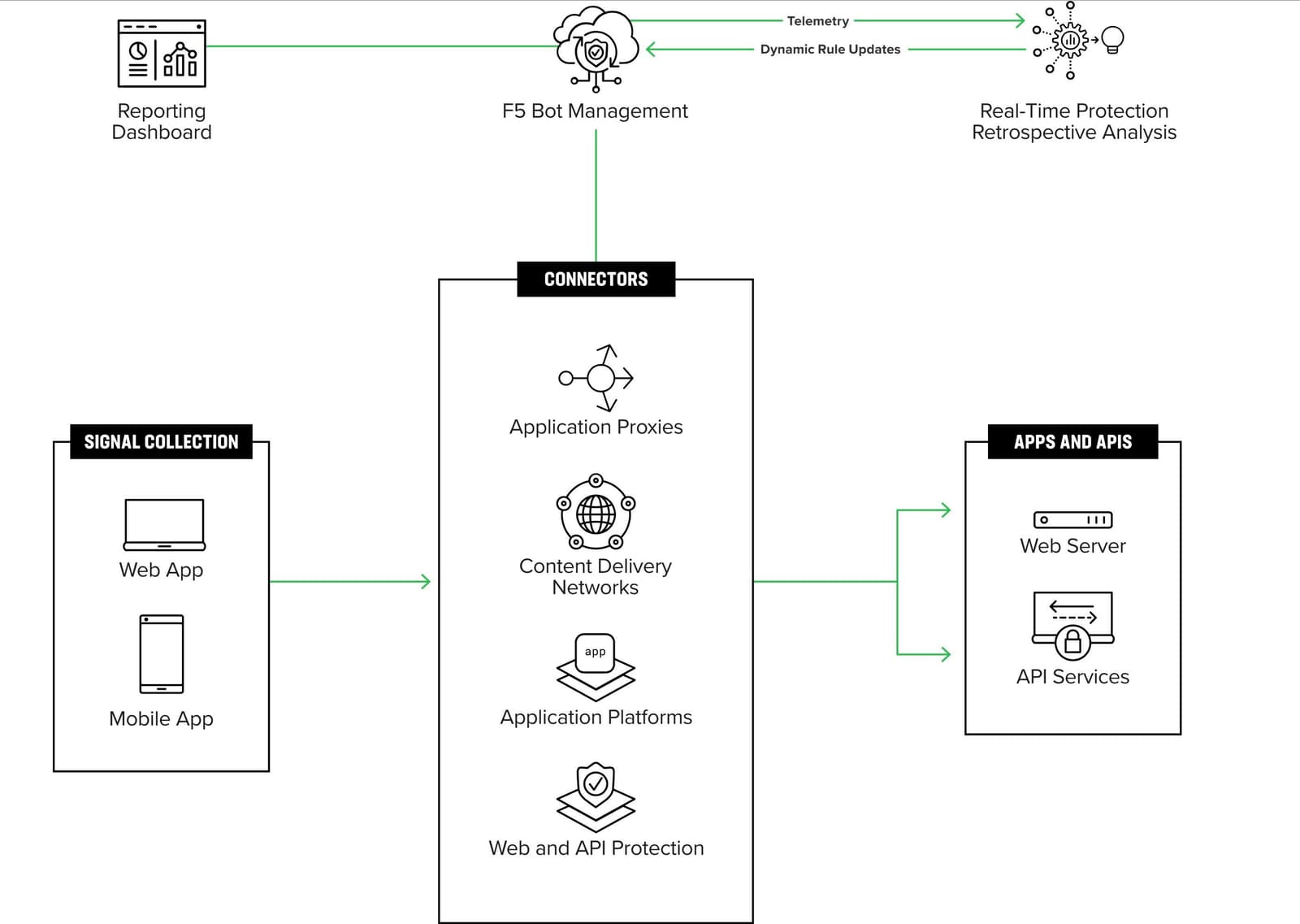
3. Are you able to maximize your existing security investments?
Most security and risk teams have deployed a complex variety of tools in order to run their business and combat ever-evolving threats. For example, web application firewalls, application proxies, and as-a-service application platforms for e-commerce. While consolidation may be attractive, a best-of-breed and defense-in-depth security posture has not gone out of style.
In fact, leveraging existing investments while bolstering defenses against bots and malicious automation provide an ideal choice for practitioners that have limited time to learn the operational side of a new security tool or platform. This also helps align teams that otherwise focus on different parts of the industrialized attack lifecycle—which typically starts with bots and malicious automation, but if left undetected, can result in fraud.
The ideal vendor can maximize existing security investments and minimize the operational burden on security and fraud teams so they can focus on strategic risk management initiatives.
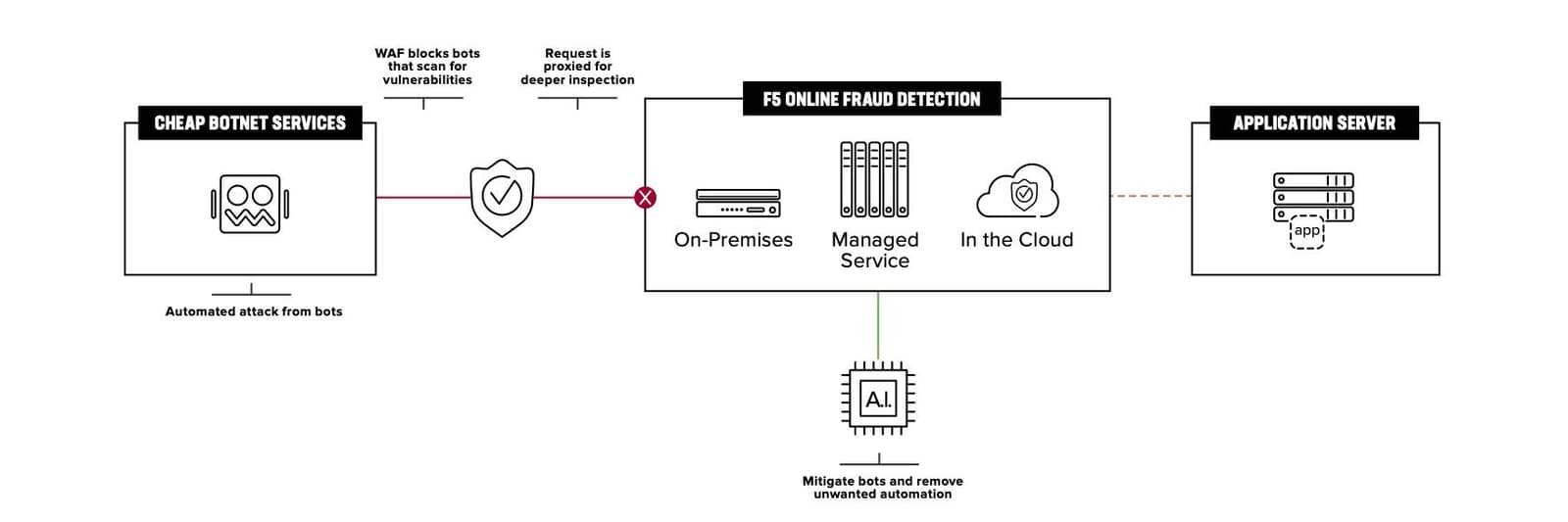
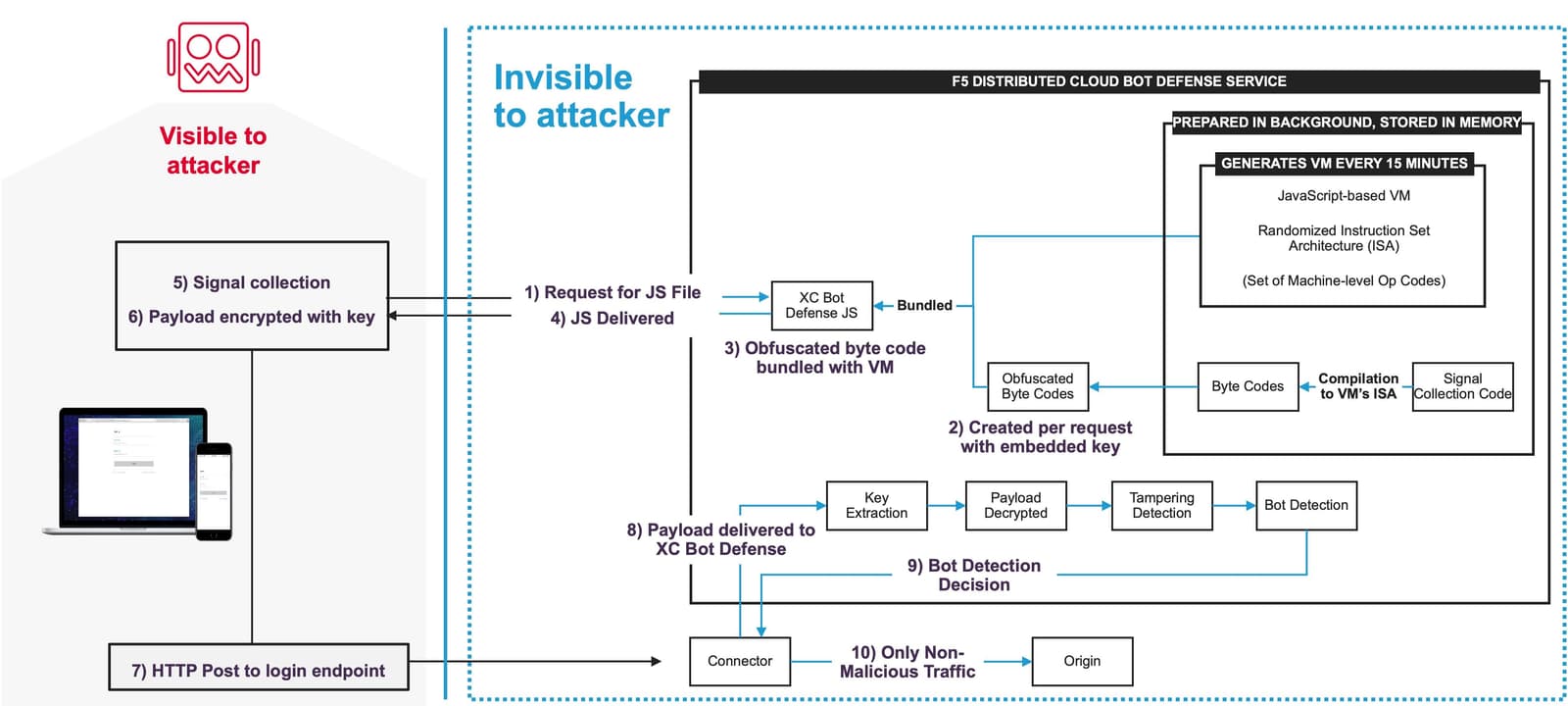
4. What type of controls does the vendor use to prevent tampering and bypass?
Motivated and sophisticated bad actors will leverage reconnaissance and reverse engineering in order to bypass anti-automation defenses and evade detection. Dark web forums are filled with examples of how to evade popular bot management platforms. Darknet fingerprint stores sell stolen customer tokens. Automation frameworks continue to evolve and can emulate or even exhibit human behavior (for example, by integrating with CAPTCHA solving services).
The best defense? Base detection on a variety of advanced network, device, environmental, and behavioral signals using durable and heavily encrypted/obfuscated telemetry that is essentially spoof-proof. F5’s JavaScript leverages bespoke, per-customer implementations, and frequent bytecode randomizations within machine-level opcodes, making it computationally unrealistic to reverse engineer. This technological advantage results in accurate detection and security countermeasures that are resistant to attacker manipulation.
Additionally, AI-based retrospective analysis and continuous monitoring by Security Operations Center (SOC) team members can uncover unusual traffic patterns or tampering.
Disrupt the ROI of cybercrime by making success impossible, or so impractical that it’s unfeasible.
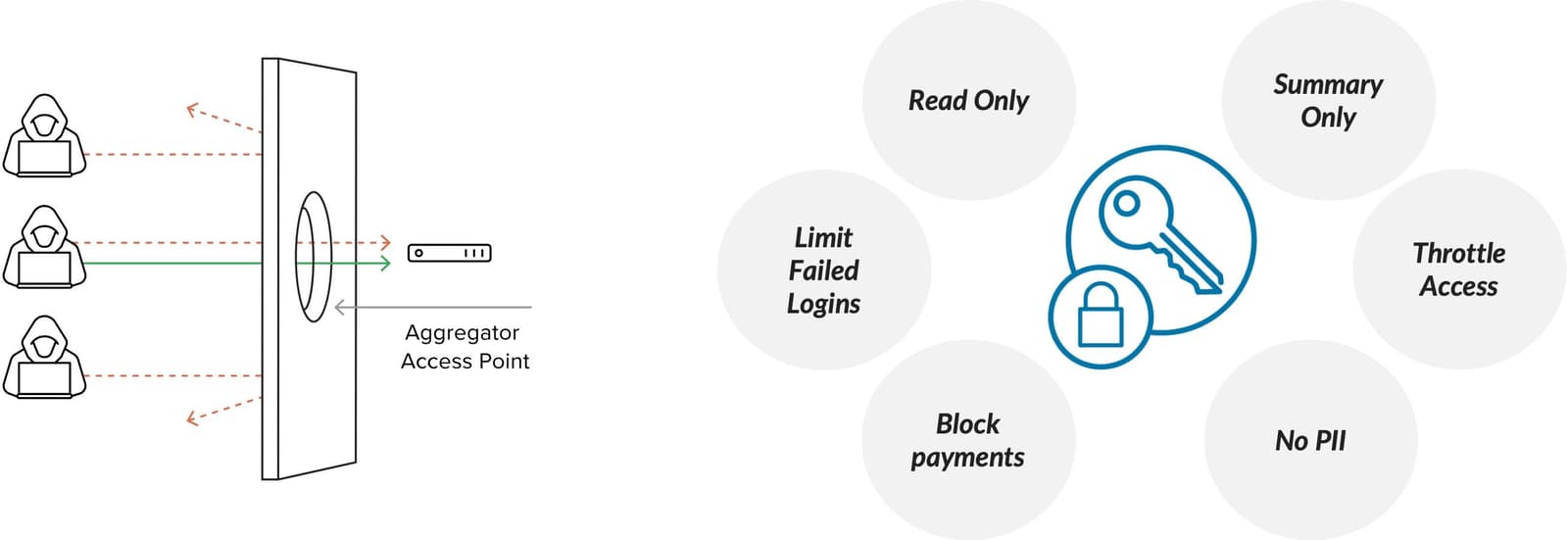
5. Does the service provide controls to prevent attacks through third-party APIs and aggregators?
Your customers demand simplicity and value. Often this means having a consolidated view of accounts or services. But how can you allow third-party integrations without fully understanding the unintended risk of doing so? Well, you better figure it out quick, because if you don’t, your competitors will take advantage.
Bot management needs to support business opportunities enabled through third-party integrations without introducing risk of compromise through such integrations. How? By leveraging policies with fine-grained control of allowed/legitimate aggregators and associated permissions instead of employing a false dichotomy of allowing or disallowing aggregators globally.
6. How many stages of detection does the vendor provide?
Cybercrime, like all crime, comes down to means, motive, and opportunity. For some organizations, particularly in the financial services sector, the perceived value of accounts lends to a perceived attractive ROI, and thus, increases motive. If the motivated bad actor is sophisticated, you better prepare to enter the war room for some good ol’ fashion battle of the bots exercises.
This is why it is imperative to employ multiple stages of detection based on accurate and durable telemetry, highly trained artificial intelligence within a diverse collective defense network, as well as both real-time and retrospective analysis. A two-stage approach that uses AI and “carbon units” (humans) provides optimal protection and agility to deploy countermeasures autonomously and/or deliberately to confuse, and ultimately, deter, motivated adversaries.
7. Is the service able to adapt to your desired security posture and operating model?
Do you want to deploy robust but self-sustaining bot mitigation quickly so as not to worry much about it? Check. Do you want to control your security posture but extend your security and fraud teams’ expertise with a trusted advisor? Check. Are you unsure how to proceed but want to evaluate options and avoid being tied to any particular deployment or operating model? Check.
When agility and security meet, the dance can be quite beautiful. In all cases, a bot mitigation vendor needs to have your back, ready to jump into the war room when necessary to defend your business from compromise and abuse.

8. What types of mitigation does the service perform?
Okay. Time to concede my rookie mistake. I once used the word “block” casually to describe bot mitigation and was taken into time-out and coached by one of our foremost experts. The type of mitigation depends. It depends on the situation. It’s a game of chess.
The appropriate action could mean silently monitoring the attacker’s canary account or it could mean optimizing authentication for a trusted customer.
Perhaps an attacker is allowed to create fake accounts but then isn’t allowed to log into them.
Sometimes it makes sense to block a suspected fraudulent request outright. Sometimes the request should be redirected to a honeypot or responded to with a custom web page.
If malicious intent is suspected, say from a content scraper or compromised aggregator, bot management can transform requests in-transit in order to deceive attackers through misdirection, limit access to specific application functions, throttle traffic, or flag requests for follow-up actions and watchlists.
All in all, security teams should be able to apply granular mitigation controls by traffic type, source, and target, and countermeasures should be dynamic and adaptable in order to respond to the attack at hand.
Remember, effectiveness is more than efficacy. No more writer’s block for me.
9. Can the vendor use security controls to improve business outcomes?
Organizations can improve a number of business outcomes by employing effective bot mitigation to protect critical apps and APIs. It comes down to three important questions: Are you human? Are you who you say you are? What is your intent? By consistently answering these three questions for every interaction in the digital journey, you are well on your way to using security technology to improve business outcomes.
For example:
- Improved conversion, retention, loyalty
- Increased top-line revenue
- Decreased bottom-line losses
- Reduced complexity
- Increased operational efficiencies
- Less fraud, less friction, less effort

10. Is the vendor battle-tested against sophisticated and motivated cybercriminals and nation states?
By partnering with the right bot mitigation vendor, you can protect critical applications, regardless of architecture, cloud, or CDN, with effective, easy-to-use, and battle-tested security.
The name of the game for any solution is to maintain resilience no matter what attackers do, ensuring they get no return on their investment. Eventually they will abandon their efforts and move on.
It makes sense to consider vendors that protect the world’s most valuable brands from the most sophisticated cybercriminals with outcome-based defenses centered on effectiveness.
Learn more at: https://www.f5.com/solutions/application-security/bot-management
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
