F5's principal threat research evangelist puts on his reporter hat to bring you some insights from one of the oldest hacker conferences there is.

Black Hat is 20 years old now, which sounds old, but it just goes to show you how young our industry is. If Black Hat were a person, it would still be too young to gamble in the city in which the event is held. Before diving into this year's details, let's have a look at a few event numbers to illustrate then vs. now.
| Black Hat Briefings, 1997 | Black Hat, 2017 | |
|---|---|---|
| Attendees | 100 | 15,000+ |
| Sponsors | 3 | 250+ |
| Network | None | 70+ volunteers |
Keynote #1
Jeff Moss (a.k.a. the Dark Tangent), founder of both Black Hat and DEF CON, gave a keynote that was mostly a walk down memory lane. Nothing wrong with that, but there was little vision for the future communicated in his keynote. He did make a call for us “older” cyber vets to mentor the next generation of white hats so that we’d all have people to hire. Totally agree with that sentiment, which makes me want to finish the Hacking 101 class that I’ve been putting together for the little ones...
Keynote #2
Alex Stamos is doing some things right. As the CISO of Facebook, he’s giving away $1,000,000 in prizes for best defensive research presented at USENIX. He’s also sponsoring educational programs[1] to help those younger people get into cyber security and hardening our digital infrastructure with the Internet Bug Bounty project.[2] He spent just a tad too long touting many of the outreach programs that Facebook is involved with, and not enough time addressing what many thought was the elephant in the room—combating the “human abuse” problems that relate to Facebook, such as fake news and cyber bullying.
Where Are the Zero-days, Man?
One common complaint about Black Hat is, “Where are the zero-days, man?” Well, according to Daniel Cuthbert, who presented at the Day Zero evening event, this year had more zero-days than in any Black Hat conference before it.
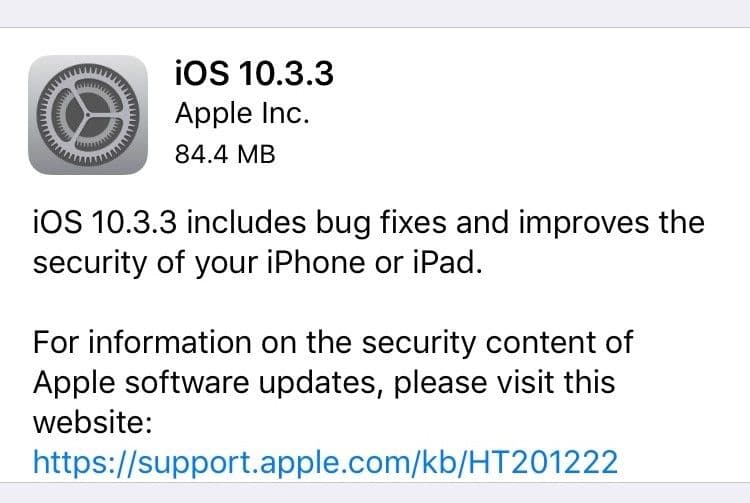
Case in point, when I landed in Las Vegas, my iPhone politely informed me that it wanted to update to latest version: iOS 10.3.3. Updating my computer, or even phone, at a hacker conference is something I think twice about.
But this phone update is the direct result of a zero-day released at Black Hat 2017. The “Broadpwn” vulnerability affects the Broadcom BCM43xx chipset, which is used by both iOS and Android handsets. So, props to you, Black Hat, for getting this, one of the biggest zero-days of the year, at your conference.
General Vibe
If there was an official theme among the briefings at Black Hat 2017, it was surveillance. Or perhaps more accurately, how-to anti-surveillance. Two other Black Hat zero-days were released, and both had to do with breaking mobile networks. The first, “Ghost Telephonist,” exploits a missing authentication in the fallback between LTE and 4G networks, allowing an eavesdropper to intercept calls and even SMS messages.[3]
The second mobile vulnerability allows an attacker (who is using a custom-built $1,500 Stingray-like device as a proxy) to locate and track mobile users by exploiting another missing authentication step in mobile protocols.[4]
My favorite briefing was “Hacking Serverless Runtimes,” where researchers Andrew Krug and Graham Jones showed how to shell out from AWS Lambda functions and run code inside other people’s microservices.[5] Hilarious.
Krug and Jones also joked about the fact that someone has figured out how to embed a docker container inside a lambda function.[6] Why would you do that? That’s ridiculous!

The Pwnie Awards: Rewarding the Security Fails for 2017
Pwnies 2017: The 11th annual “Pwnies” award had some great entries this year. The winner for Best Server-side Bug went to The Equation Group (totally not the NSA, ha ha) for the EternalBlue SMB vulnerability, which was leaked by the Shadow Brokers (totally not Russia, ha ha) and the weaponized by the Lazarus Group (totally not North Korea, ha ha).
The Pwnie for best backdoor went to the M.E. Doc, found by Kaspersky in the Ukrainian tax system. Credit goes to: “Totally not Russia, ha ha.” The Pwnie for best cryptographic attack went to Google, who this year forced the world’s first SHA1 collision. And the SystemD controversy rightly won the “Lamest vendor response” pwnie.
Malcolm Turnbull of the Australian government won Most Epic Fail for demanding that vendors decrypt user data for the government.[7]
The Arsenal
One often overlooked space at Black Hat is the Arsenal. This is where open-source security hobbyists demo their tools for your amusement. Not every tool is compelling but, hey, you get to talk to the actual coder of the tool. My personal favorite this year was Tomer Zait’s Pymultitor tool.[8] It’s a local proxy that uses multiple TOR processes to allow you to bypass IP-based counters for login pages. You know, for research. Not for brute-forcing Facebook accounts.
This year there were over 100 tools presented at the little arsenal workstations. Arsenal is charming enough and community-oriented enough that Black Hat should provide a more prominent space for it rather than stuffing it at the very top, in the very back of the conference.
So...Is Black Hat Still Relevant?
To answer this, let's go back to the founder. During his keynote, Jeff Moss reminisced about assuming that the Black Hat briefings, as a conference, would never last very long. But after 20 years of near constant growth, Black Hat is hitting its stride and settling into becoming a pretty decent security conference for one of its size.
References
[2] https://internetbugbounty.org/
[5] https://www.blackhat.com/docs/us-17/wednesday/us-17-Krug-Hacking-Severless-Runtimes.pdf
[6] https://hackernoon.com/how-did-i-hack-aws-lambda-to-run-docker-containers-7184dc47c09b
[8] https://github.com/realgam3/pymultitor
About the Author
Related Blog Posts
SaaS-first strategies reshape cloud-native application delivery
F5 NGINXaaS empowers cloud and platform architects to unify operations, reduce complexity, and deliver exceptional digital experiences at scale.

F5 ADSP Partner Program streamlines adoption of F5 platform
The new F5 ADSP Partner Program creates a dynamic ecosystem that drives growth and success for our partners and customers.

Accelerate Kubernetes and AI workloads with F5 BIG-IP and AWS EKS
The F5 BIG-IP Next for Kubernetes software will soon be available in AWS Marketplace to accelerate managed Kubernetes performance on AWS EKS.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
F5 Silverline Mitigates Record-Breaking DDoS Attacks
Malicious attacks are increasing in scale and complexity, threatening to overwhelm and breach the internal resources of businesses globally. Often, these attacks combine high-volume traffic with stealthy, low-and-slow, application-targeted attack techniques, powered by either automated botnets or human-driven tools.
Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
David Warburton, author of the F5 Labs 2020 Phishing and Fraud Report, describes how fraudsters are adapting to the pandemic and maps out the trends ahead in this video, with summary comments.