The unfolding crises in Ukraine has exposed new facets of nation-state conflicts that have impacts far beyond the immediate geographic region. As a global company, we have tremendous empathy for all who are harmed, displaced, or otherwise negatively impacted by the ongoing attacks, including many of our extended F5 family. Without overlooking the very real, very human aspects of the Russia-Ukraine conflict, we have also been asked by customers to provide guidance on the kinds of cyberattacks that they may see more of in the days to come, in light of recent events. Accordingly, the piece below intends to address those inquiries in a straightforward, respectful, and practical manner.
The role of cyberattacks in nation-states conflicts have given rise to new cybersecurity concerns on a different scale than many organizations have dealt with traditionally, further highlighting the importance of defending against sophisticated attacks through a proactive cybersecurity strategy.
With the evolution of the Internet, global business operations have changed tremendously. Digital transformation is happening at an exponential scale, spurring technology advancements and cyberattack sophistication in equal measure. In parallel, today’s organizations are still dealing with traditional attackers that are motivated financially, but also nation-states and cause-based actors that have broader goals. Of course, with the increase in sophistication of cyberattacks, corresponding protections need to evolve regularly as well. In today’s economy, you are much more likely to encounter nation-state actor that are developing exploits for known (and unknown) vulnerabilities.
In practice this leads to nation-states actors developing exploits that target the Internet (and critical services) infrastructure of other nations on a continuous basis. While the most immediate scenarios that come to mind are geopolitical conflicts between nation-states, many of the same principles must now be broadly applied to traditional enterprise security practices, particularly as nation-states often will attack a combination of government and private-sector Internet resources as a means to destabilization. Accordingly, targeted cyberattacks pose a significant threat both to the integrity of nations and also those attempting to conduct any related business efforts with (or within) a targeted geography. This has led to proactive and continuous cybersecurity as a heightened need for all types of organizations.
Targeted Cyberattacks
Broadly speaking, nation-state adversaries launch targeted cyberattacks to severely diminish the infrastructure of nation-states and disrupt the functionality of their Internet systems, which in turn can impact the financial and military infrastructure. Figure 1 highlights an example of a targeted attack (in this case, phishing) in action.
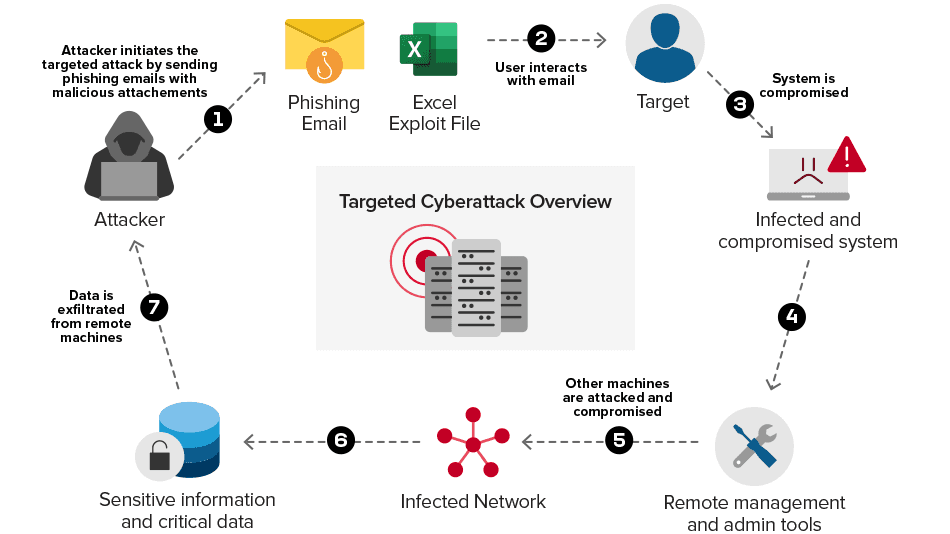
Figure 1: Targeted Phishing Attack in Action
Targeted cyberattacks are executed using malicious code designed to conduct stealthy operations. Some examples of the malicious code are exploits (exploiting vulnerabilities), rootkits (tampering kernel and user mode for unauthorized operations), Remote Administration Toolkits (managing compromising systems), Wipers (destroying Master Boot Records of the system), ransomware (encrypting sensitive data and asking ransom) and many others. While generally referred to as cyberattacks, one can deem these individual tactics as “digital weapons.”
Nation-State Attackers Targeting Infrastructure: Digital Weapons on the Rise
Adversaries conduct a wide variety of attacks during nation-states conflicts, with digital threats posed alongside those of a traditional physical nature. Today's nation-states are well-versed in carrying out multiple sets of cyberattacks, with prominent examples discussed below:
- Launching Distributed Denial-of-Service (DoS) attacks from various geolocations on the Internet to take down critical infrastructure and communication portals is a well-thought operational strategy during nation-states conflicts. For example, adversaries may be determined to affect military-centered websites used for handling internal affairs to disrupt official communications. Financial institutions' web portals are also generally targeted to impact banking and financial operations.
- Triggering data destruction attacks by distributing advanced malicious code via drive-by download attacks. The malicious code is either hosted on the compromised web portals or attached with phished emails (targeted in nature) and using social engineering, the targeted users are forced to interact with the web portal or phishing email to install malicious code on the targeted systems. Once the malicious code is installed, it has the capability to wipe out the complete systems by deleting data and rendering the system useless.
- Stealing Intellectual Property (IP) during a time conflict is also one of the main targets of the nation-state adversaries. The reasoning is usually as follows: If a nation-state infrastructure is compromised already, there may be an opportunity to steal IP that could be used for a variety of purposes later on.
Related, here is a quick breakdown of notable cyberattacks likely to be used as “digital weapons” in nation-state conflicts:
| Cyberattack Type | Malicious Code Name (“Digital Weapon”) | Characteristics |
|---|---|---|
| Distributed Denial-of-Service (DDoS) | Unknown Botnet | Denial-of-Service: Impacting the availability of critical infrastructure such as web portals of financial institutions, military, etc. |
| Malware Distribution | Whisper Gate | Data Destruction and System Bricking: Corrupting the Master Boot Record (MBR) of the compromised systems and encrypting sensitive files |
| Malware Distribution | Hermetic Wiper | Data Destruction and System Bricking: Corrupting and erasing sensitive files on the compromised systems |
Table 1: Malicious code likely to be used in cyberattacks launched during nation-states conflicts
Using the digital weapons listed above, nation-state actors can launch a tremendous set of attacks to severely impact the infrastructure owned by governments and organizations. This is usually part of a larger strategy to upset the ability of the nation-state to communicate freely, and to disrupt the financial and military systems on the fly by circumventing the integrity, availability, and confidentiality of the active systems in the infrastructure.
Again, while this may seem most immediately relevant to nation-states in conflict, there is a broader risk when the tools and exploits used in these attacks make their way into the larger threat landscape. (A historical example of this is the NotPetya bug from 2017.)
Securing Critical Infrastructure
Proactive cybersecurity has become the prevailing necessary approach. While governments are generally responsible for ensuring that critical infrastructure (including military web portals, financial institutions' websites including SCADA infrastructure) should be continuously monitored and protected against cyberattacks, the lines between public- and private-sector security have become much more nuanced. Looking at the overall picture, securing network infrastructure and deployed applications is critical to circumvent network attacks such as DDoS and malicious code distributed over the wire to preserve the integrity of infrastructure resources without impacting the availability. More importantly, protecting the critical applications against HTTP attacks is required as well. The most important part is to ensure communication over the Internet stays undisrupted. For that, organizations need to ensure their infrastructure is embedded with security mechanisms to combat cyberattacks.
The First Steps toward Achieving Proactive Cybersecurity
The accelerated pace of digital transformation has resulted in the adoption of modern applications by governments and organizations to achieve operational efficiency. However, these applications require protection against advanced cyberattacks, which can be targeted or broad-based in nature. It becomes even more relevant during times of nation-states conflict to ensure that critical applications can be kept available. Governments, and all organizations, should remain vigilant with the following key points to consider:
- Web applications and APIs are pervasive in today’s digital landscape. Securing them against abuse and attacks is paramount to maintaining a positive security posture. Services and solutions such as Web App and API Protection (WAAP) not only provide protection against web-based attacks, but include native security features.
- Exploitation and abuse are not the only means of attack. Denial of service attacks can prevent access to critical assets. A proactive cybersecurity strategy should also include the ability to circumvent application-based DoS attacks to ensure critical applications remain available.
- Being proactive also requires the ability to identify signs of a possible attack. Most organizations lack the ability to detect attacks early due to incomplete visibility across all applications, infrastructure, and environments. The health of digital assets is determined by digital signals and is a foundational component for proactive cybersecurity. An observability strategy that enables early detection of potential attacks offers the ability to quickly respond and neutralize an attack.
Building a strong and robust cybersecurity posture should include availability, i.e., one can still use critical applications if they are under attack. Achieving security with resiliency and undisrupted availability are the benchmarks of proactive cybersecurity, with the understanding that threats (and mitigations) will never stop evolving.
About the Author
Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.