When asked why he targets banks, bank robber Willie Sutton simply replied, “Because that’s where the money is.”
If the infamous Willie Sutton, who said this in the 1930s, was alive today with a modern take on high-yield crime, we might be asking him: "Why do you launch cyberattacks on healthcare companies?"
The reason why is clear. The average cost of a data breach across all industries is $4.24 million per incident. For healthcare, the cost jumps to $9.23 million per data breach, up from $7.13 million in 2021, giving healthcare the highest data breach costs for any industry, including finance, pharmaceuticals, technology, and energy.
Why is a healthcare data breach more costly? Healthcare companies have the trifecta of information attractive to bad actors: personally identifiable information (PII), protected health information (PHI), and financial information.
The IBM “Cost of a Data Breach Report 2021” says the average cost of lost customer PII is $180 per record. It also states the most popular initial attack vector is compromised credentials, at 20% of all attacks. Combine those numbers with the U.S. Department of Health and Human Services (HHS) report that shows in 2021 a staggering 39,630,191 accounts were breached because of “Hacking/IT Incident.” If we assume 20% of more than 39 million accounts in 2021 were breached because of compromised credentials at $180 per account, the cost is over $1.4 billion.
The Trajectory of Crime for Healthcare Data Breaches
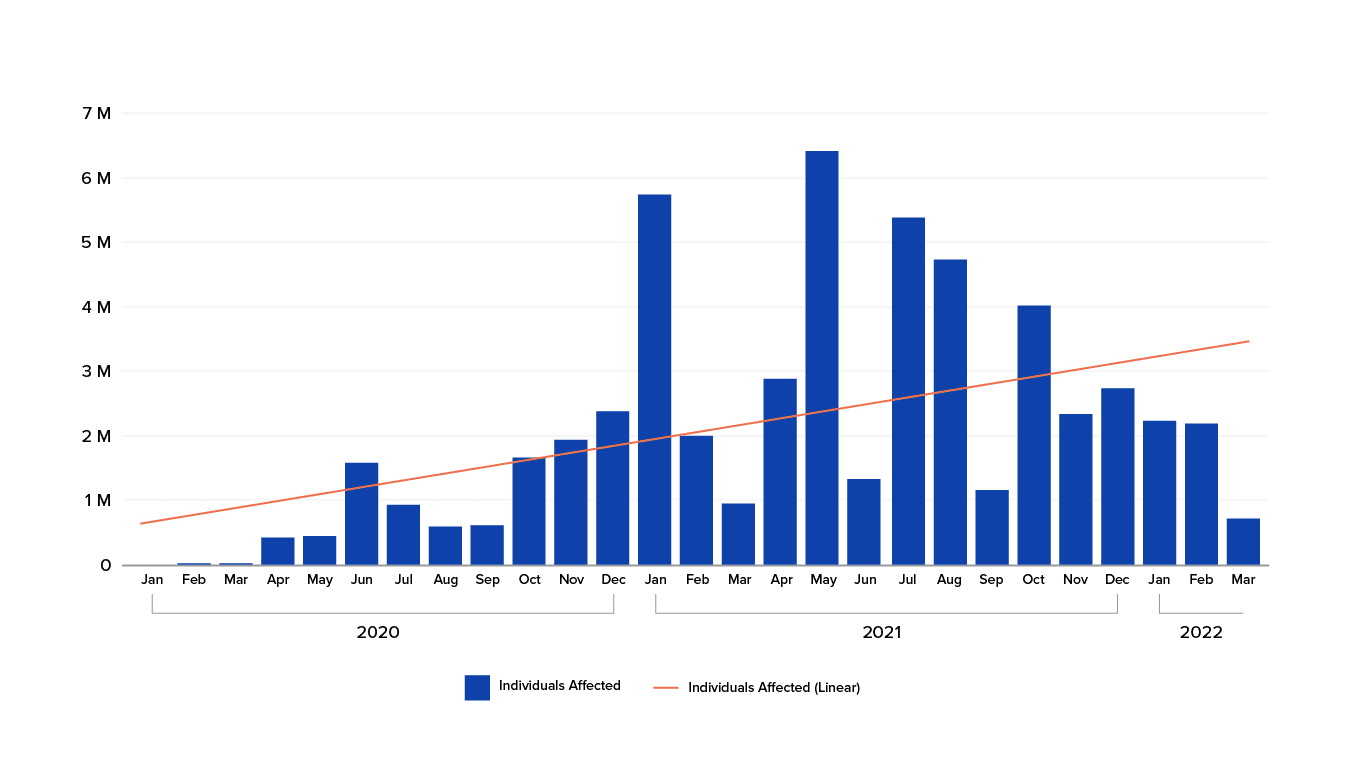
The above chart shows the increase of data breaches reported by the HHS from February 2021 until March 2022.
Once there is a data breach, bad actors will turn to the dark web to purchase these compromised credentials. Bad actors are consolidating data breaches into larger collections, referred to as “combolists,” so attackers can buy a much larger list of compromised credentials. “Collection #I” has been on sale since 2019 and contains 773 million unique email addresses with corresponding passwords.
In a credential stuffing attack, bad actors will buy these collections of compromised credentials and then make repeated attempts to “stuff” the login page across many different web sites. When successful, the attacker takes over the account and uses it for fraudulent purposes. The success rate for a credential stuffing attack is typically 1 to 2 percent. If they are testing 1 million compromised credentials, bad actors can typically access 10,000 to 20,000 accounts. A credential stuffing attack is successful because people tend to reuse and recycle passwords across many accounts, so those available on the dark web are ubiquitous for several apps.
The healthcare industry is also starting to see malicious bots scraping more and more content. Specifically, bots are scraping information on health plans, explanations of benefits (EOB), and lists of physicians within provider networks. Health plan and EOB information can be used by competitors to offer lower prices and competitive intelligence. Physician information can be used for phishing campaigns to collect payments and other PHI from patients.
Getting in Front of Attacks
What is the best way to reduce the risk of data breaches and credential stuffing attacks? There is no single answer, but a good place to start is adopting a zero-trust architecture and identifying bad actors abusing your web applications.
A zero-trust architecture eliminates the idea of a trusted network inside a defined perimeter. In other words, it is a security model that focuses on verifying every user and device, both inside and outside an organization’s perimeters, before granting access. The zero-trust approach is primarily focused on protecting data and services, but it can be expanded to include all enterprise assets.
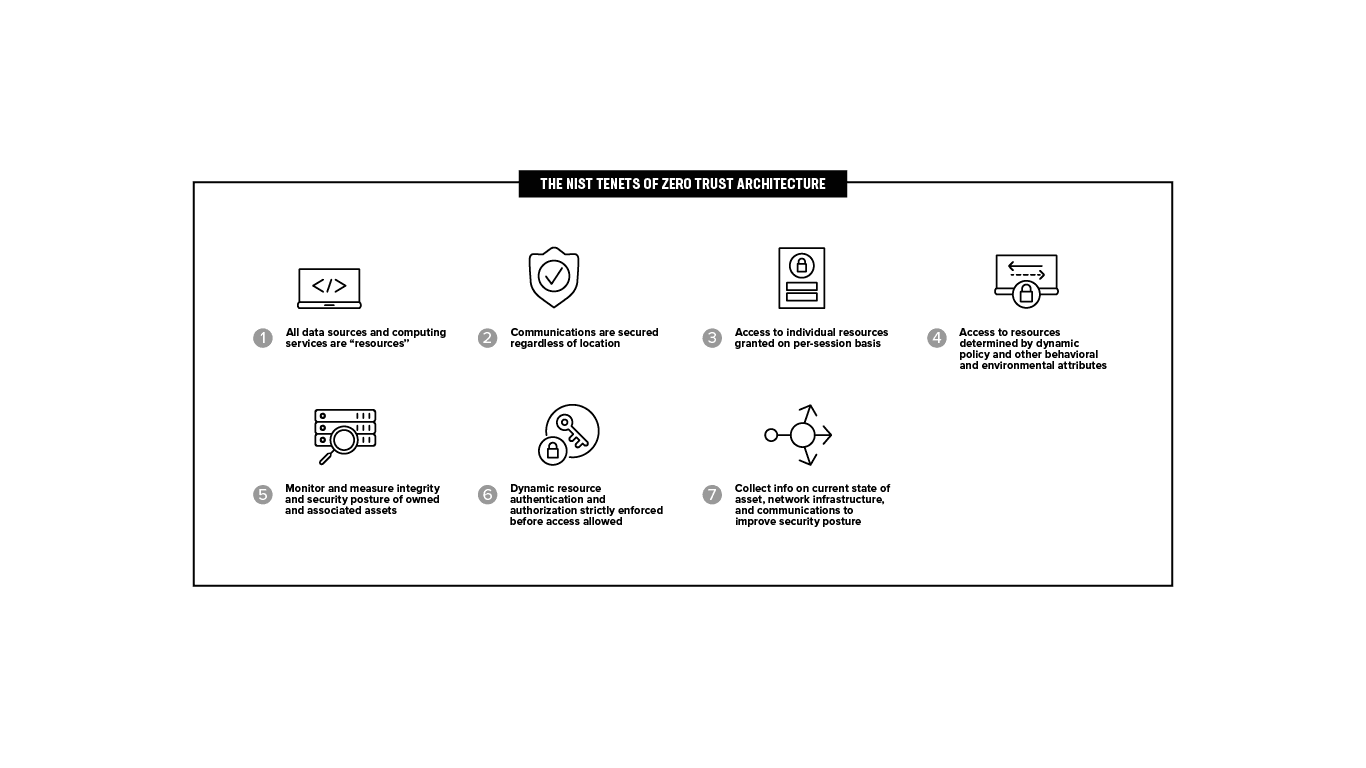
F5 leans heavily on the NIST Special Publication 800-207 Zero Trust Architecture for our efforts around zero trust, because it provides industry-specific general deployment models and use cases where zero trust might improve an enterprise’s overall information technology security posture. The architecture document describes zero trust for enterprise security architects and aids understanding of zero trust for civilian unclassified systems. In addition, it offers a roadmap for migrating and deploying zero trust security concepts to an enterprise environment.
Solutions to Combat Healthcare Cyber Crime
F5 Distributed Cloud Bot Defense and Distributed Cloud Account Protection protect websites from being abused by bad actors. All the credential stuffing attacks we mentioned earlier? They’re all coming from malicious, automated bots. Traditional defenses, such as CAPTCHA and geo-fencing are easily bypassed by today’s bad actors. There are even services for hire that allow bad actors to defeat any type of CAPTCHA. One of these sites, 2captcha.com, provides an API for bad actors to programmatically bypass your protections. 2Captcha will solve normal Captcha, text Captcha, ClickCaptcha, Rotate Captcha, reCAPTCHA V2 & V3, reCAPTCHA Enterprise, FunCaptcha, TikTok Captcha, and more.
Distributed Cloud Bot Defense protects application experiences, web properties, mobile apps and API endpoint transactions from sophisticated bot attacks by intelligently collecting a deep set of JavaScript and HTTP network layer signals and telemetry from each client transaction, without re-routing traffic through a proxy server. The platform identifies malicious bot automation behavior by applying multiple layers of machine learning intelligence. The system monitors, flags, detects, and identifies retooled attacks, and mitigates automated attacks in real time.
Because of the large amount of money flowing throughout the U.S. healthcare industry and on a global scale, bad actors won’t stop at automation. If you can mitigate the automation from bad actors, they will step up to manual attacks. Distributed Cloud Account Protection helps companies identify visitor intent. Distributed Cloud Account Protection evaluates each online transaction across a set of telemetry, environmental, and behavioral biometric data, starting from the first time a visitor arrives at a protected web or mobile application, through to account creation or login, and continuing through all aspects of the user’s journey.
Distributed Cloud Account Protection can even connect context across different browsers and devices operated by the same user, and leverage insights from its global network of organizations to accurately determine user intent. Distributed Cloud Account Protection can be consumed as either a closed-loop model powered by an AI fraud engine that delivers a high-fidelity score to understand visitor intent, or enterprises can ingest account protection data into their own risk engine and combine it with other fraud data points.
The cost of data breaches and credential stuffing attacks is steadily increasing in the healthcare space. Why? Money—and a lot of it. Enterprises can help mitigate this risk by adopting zero trust architectures and stopping credential stuffing attacks using F5 Distributed Cloud Bot Defense and Account Protection.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.