Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
As customers evaluate and design new forms of managed container architectures, Threat Stack will be there to provide a detailed view into running systems that can accelerate advanced compliance and threat hunting use-cases. Today, we’re introducing the general availability of Threat Stack Container Security Monitoring for AWS Fargate, expanding our view across the full cloud security stack.
In this article, we’ll describe how Threat Stack’s new Fargate support can augment your existing AWS security controls, and we’ll also quickly look at how alerting and event search work for Fargate metadata within the Threat Stack Cloud Security Platform®.

New Threat Stack Fargate Agent
As a customer, the same basic mechanics of your Threat Stack workflows apply to AWS Fargate metadata for alert generation, rule customization, threat hunting, and more. Simply deploy the Agent, ensure network connectivity, and security data starts flowing into your Threat Stack platform.
Our Fargate Agent runs as a sidecar and is defined as part of your Fargate task definition on Amazon ECS. The Agent monitors two key aspects of your Fargate runtime environment:
- Process activity inside Fargate containers
- Network flow data within, and external to, Fargate tasks
Threat Stack provides further context into Fargate with a full, real-time view into AWS CloudTrail logs. Applications that Fargate tasks are supporting receive additional runtime protection through Threat Stack Application Security Monitoring for Node.js, Python, and Ruby code. While we consolidate your view of this data on Threat Stack’s platform, it is additive to native AWS security controls for your Amazon VPC and AWS IAM permissions.
Fargate Metadata in the Threat Stack Platform
Threat Stack provides default detections for Fargate activities, including:
- Interactive sessions
- SSHD binaries
- Data exfiltration attempts
- Unexpected network connections
These detection rules fire real-time alerts, such as the following for an unexpected inbound network connection:
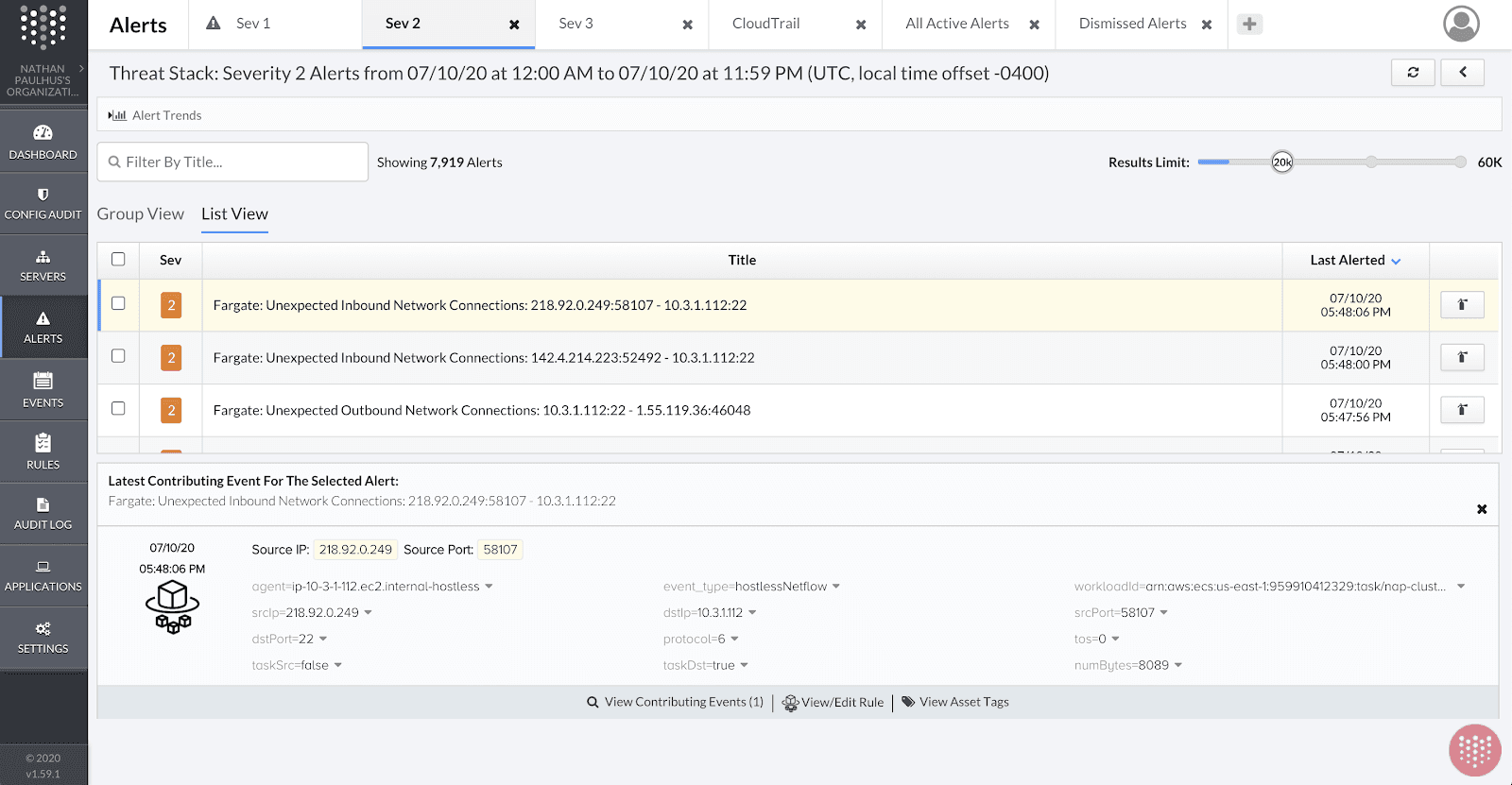
The underlying logic supporting this rule is easily customizable. Here’s a simplified example:
event_type = "hostlessNetflow" and taskDst = "true" and srcIp != "10.0.0.0/8"
Threat Stack also provides a detailed window into all event data to support forensics investigations. For example, customers can easily refine searches to see all process activity for a given task within a defined time period:
event_type = "hostlessProcess" AND agent_id = "7dd63b2d-a41d-11ea-92f9-2741263fc82a" AND event_time <
"1594402575809" AND event_time > "1594402565610"
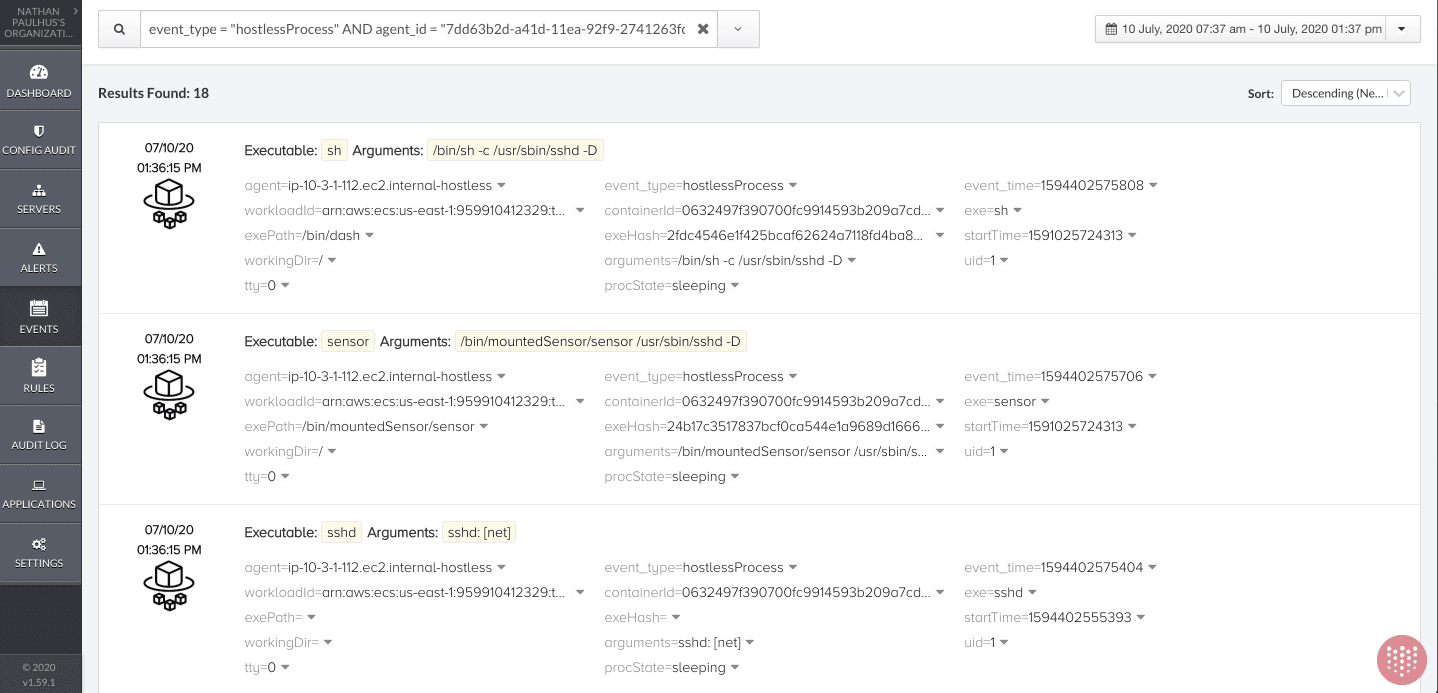
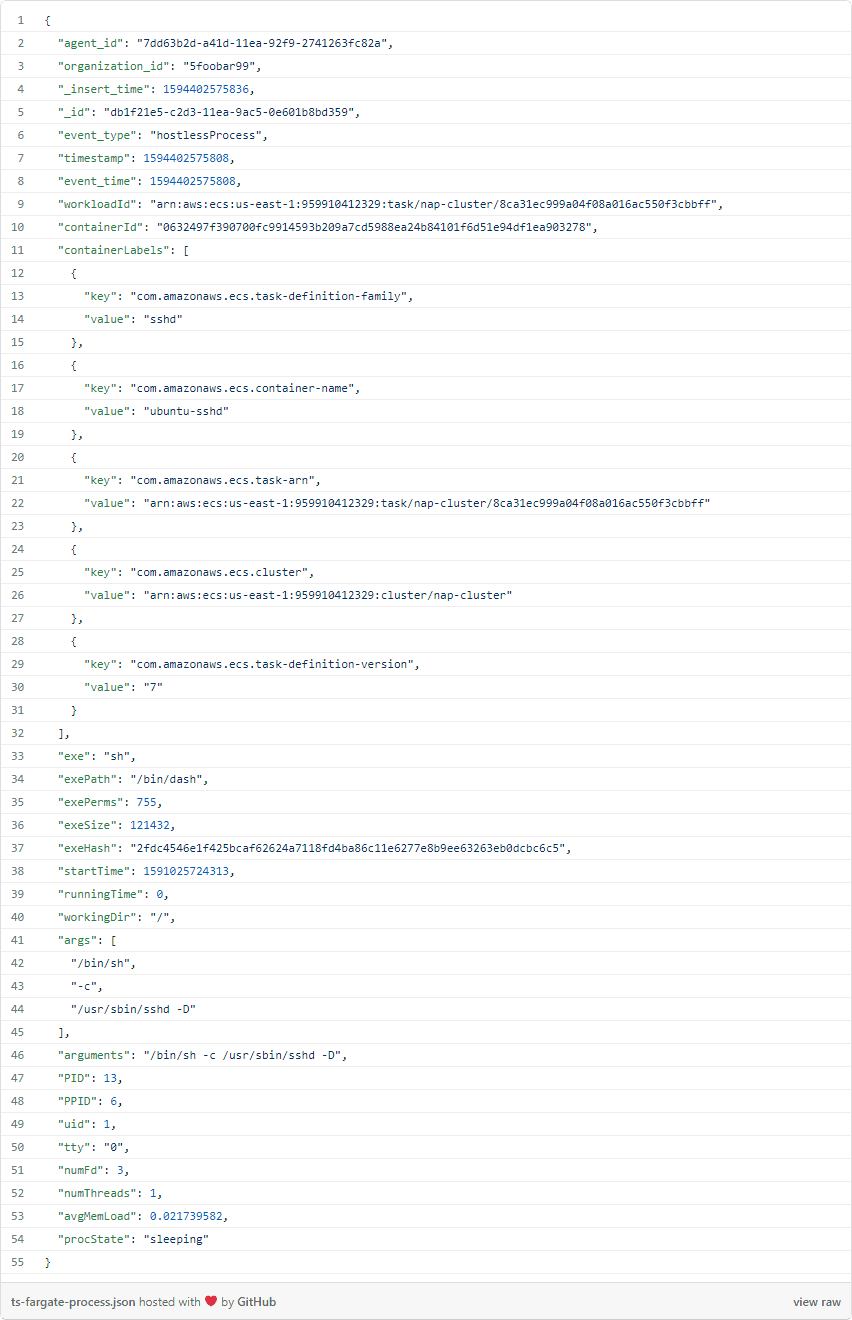
Each event is backed by supporting details, which users can surface in the UI. For example, you can drill into the first event in the image above to see the complete event JSON:
Try It for Yourself
Please contact your Threat Stack customer success manager or sales representative to schedule a demo. Existing customers may also evaluate the Fargate Agent for a limited period by accessing it via https://registry.hub.docker.com/u/threatstack.
Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.