Application architectures have evolved several times since the early days of computing. For some long-lived enterprises, they are on their fifth distinct application architecture. Many are operating and maintaining applications in each one today. To wit, findings from our forthcoming State of Application Services in 2020 indicate this is the reality most orgs operate in:
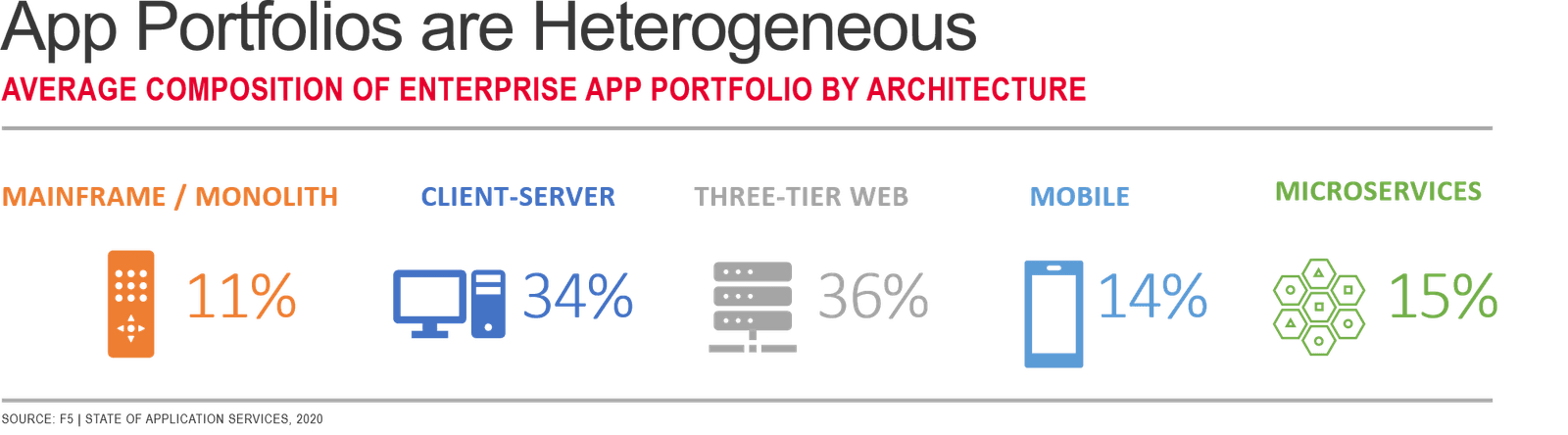
Each app architecture has a dramatic impact on everything "upstream"—networking architectures, technologies, security, and application (delivery) services. At the heart of the latest architectural shift—microservices—is a concept we can refer to as "atomization" or "componentization". Both essentially refer to the process of breaking up an application into smaller, manageable components for the purpose of improving time to market, code quality, and agility.
In previous generations of app architectures, the network remained the most efficient point at which to insert certain types of application services. Until recently, the proxy has been the primary means by which these services were inserted into the data path that stretches from app to client.
But that data path is decomposing along with modern application architectures. It now spans the Internet, cloud properties, and the data center. It increasingly includes the client as a critical component of application functionality.
Thus, it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
Application Service Insertion Points
The notion of 'inserting' application services into a data path gives us a simple way to describe this modern view of deploying application services: insertion points.
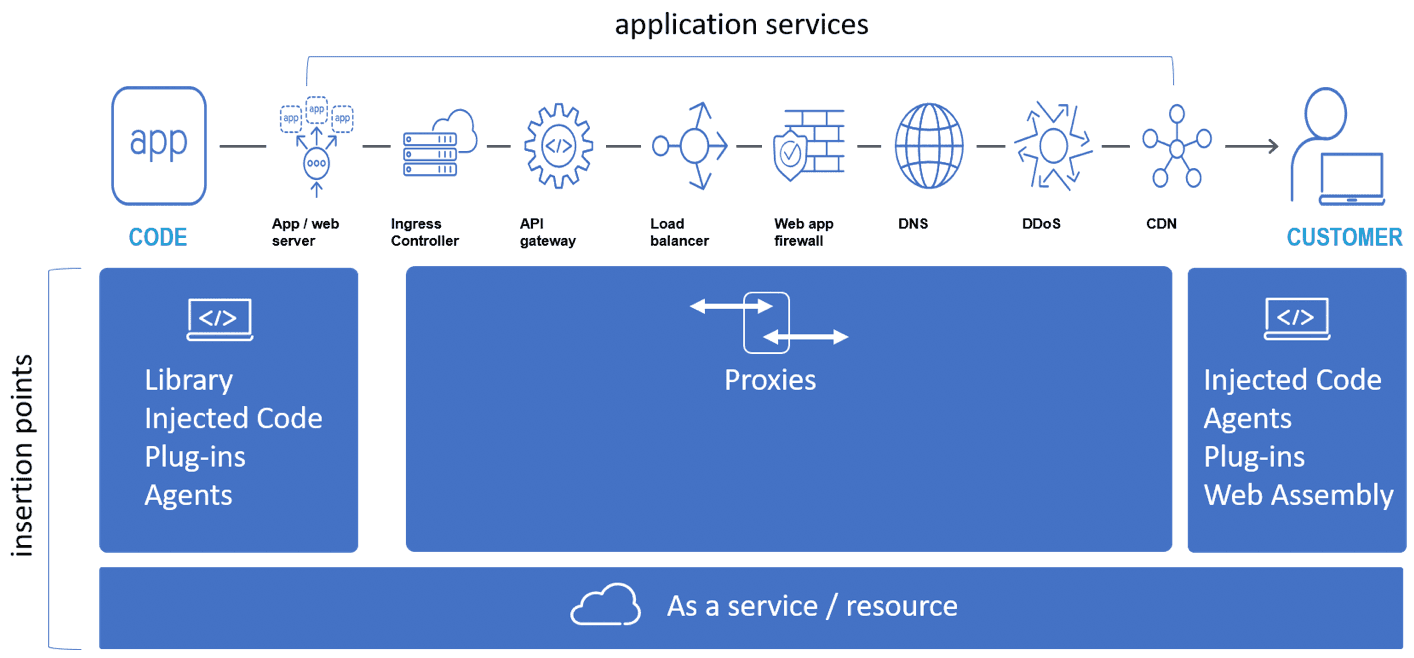
In this model, we distinguish between a traditional insertion point (the proxy) and other locations such as the app/web server and the client device. Each location has multiple forms suitable for application service insertion.
Proxy
In the traditional network insertion point of the network, you'll find proxy-based application services as well as their modern equivalent—the sidecar proxy that forms the foundation of some service mesh solutions. Both are deployed "in the network" and thus require access to that location regardless of form factor (container, software, hardware).
Proxies continue to be an efficient means of inserting application services. The biggest impact from modern app architectures on proxies today is their focus. Where proxies traditionally host application services for many applications, today's architectures demand a more per-app approach. Thus, proxies are being architected into applications and their infrastructure and tend to have a much more granular focus than previous proxy solutions.
Proxyless
Because not all applications and environments offer that access (think SaaS), we look to alternative insertion points where application services might be deployed. We loosely call these alternative points "proxyless" because they do not require or rely on a proxy for deployment and execution. These services may take the form of traditional agents—software deployed as part of the server or application—or they may take a more developer-friendly form of code-based options. Injected code such as JavaScript libraries or web server and browser plug-ins are good examples of insertion points in these alternative locations.
Service
Many of the application services may be delivered "as a service"—that is, hosted as a cloud-based offering. Insertion still requires access to invoke those services; thus, it is rare that such services will be included in an application without some form of insertion via code or configuration artifact.
Given this new landscape shaped by modern application architectures, the answer to where application services fit is, increasingly, everywhere an app—or part of an app—might reside. As app architectures decompose, so will the app services used to scale, secure, and speed up the delivery of application components.
The expansion of insertion points is but one of the evolutionary steps necessary to support future needs for telemetry and smarter automation. As organizations continue to march along the path of digital transformation, app services will continue to expand—and evolve—too.
About the Author

Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.
