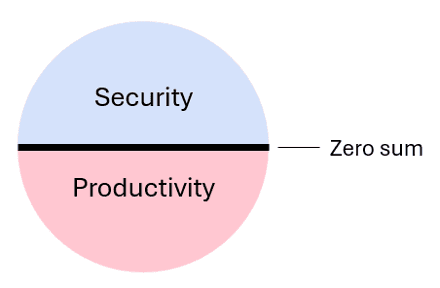
Automation is at odds with data security in the enterprise. Why?
The crux of the issue
Automation increases productivity by harnessing the power of machines. Quite a few servers can be purchased or rented in a cloud for the price of one human information worker. However, accessing enterprise data, particularly with the speed and volumes at which machines work, breaks myriad policies crafted and enforced to reduce the risk of proliferating and exposing said data. I ran across these conflicting forces recently while building an automation.
The automation scrapes some internal web pages containing viewer metrics and inserts them into a set of spreadsheets. Next the spreadsheets are moved to a network folder where a second automation detects the new files and uploads them to a specified location where my colleague notes any activity or trends that need attention. We love it. Then, after several weeks of successful runs, it failed due to an expired security secret. Our data access governance policy requires certain system credentials to expire on a regular basis. Good for security. Expired credentials break automation. Bad for productivity.
Regularly expiring security secrets is a clear best practice, but does it need to break things? The automation saves significant time for my team, but it is merely reading data from one location and reformatting it for easy analysis in another. Does the automation really need to run at the same level of privilege as me, a human? There’s got to be a compromise in there somewhere.
Compromise
Here are two options that come to mind that may serve as a compromise:
Option A
Issue a warning five days ahead of expiration, giving time to renew it before anything breaks.
Option B
Issue service credentials specific to the automation task with the least privilege required.
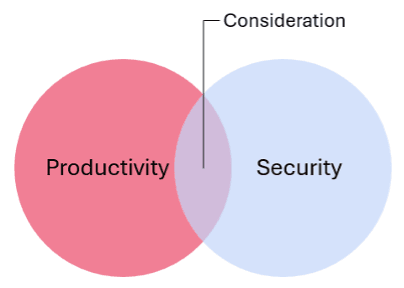
Treat automation as another type of user
Both options respect data security requirements of the organization, and through a tiny bit of increased visibility and communication between the business and security operations (SecOps), a prudent and effective solution is possible. A bit of well-reasoned compromise can ease the tension between data security imperatives and productivity-increasing automations, and, most times, neither side loses, which means the business wins.
Automation introduces a new user into enterprise governance called the machine worker. It brings implementers of security policy and automation together. Organizations who recognize this new user and consider its actual requirements in finer grained detail will escape zero sum tension, establish safer data use practices, and realize the business gains offered by productivity-enhancing technologies.
About the Author
Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.